- Jun 24, 2016
- 2,502
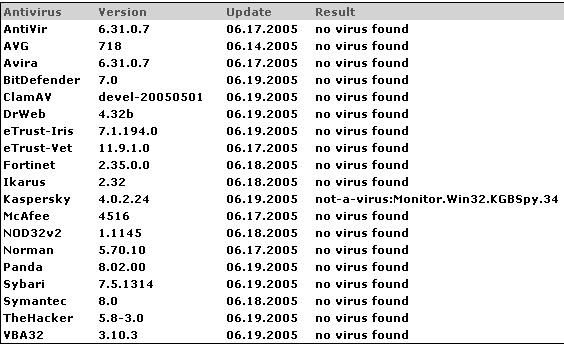
You're right here. Nevertheless, my comment pointed to legit signed malware, meaning a legit file, issued by a Trusted Vendor, corrupted by malware (a.k.a CCleaner case). If such case occurs, and no programming errors are found (like the infinite callbacks home from CCleaner malware), the chances of signatures detecting it are minimum, tending to zero. Here's where the importance of backups gain popularity.Many AVs may have a problem with detecting never-seen & signed malware. But usually, the signed malware which can hit home users will be detected by signatures. That is why the AV alongside CF is welcome. The user can also throw out most entries from CF Trusted Vendor LIst and keep only those entries which are required for system/software updates.