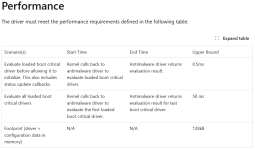
How would you prevent the termination of this one-by-one backup creation when Windows on shutdown forcibly kills it?
Furthermore it could be the case that all rules are deleted first and than all rules are rewritten when only one new rule needs to added.
When one manually adds e new HIPS rule in CIS and the HIPS rules list is (very) long it takes pretty much time before the new rule is added before the HIPS rules window closes.
Yeah, they likely at the first step delete all rules in preparation for non-atomic write and this can be easily verified, add a rule, before that open regedit at the hips rules location. Once the Comodo loading commences, start refreshing in regedit repeatedly. Observe whether rules will disappear.
Observe whether they will reappear one by one or as a single dump. You can also use tools like procmon.
If all rules disappear and reappear, it all comes down to forceful termination, Windows will not wait forever for Comodo to rewrite its rules. Specially in paranoid mode, they will quickly become far too many.
They can also be performing some rule maintenance operations that take so long.
The fix as I suggested at the start is in first, optimising the writer to support few operations: edit, delete, add.
Instead of always overwriting, you pass what you want it to do, new rule, old rule (or empty string) and whatever else you want it to write. Then your shutdown routines is fixed. This writer is called in multiple places of the GUI (and not only) so the calls need to be updated.
Any maintenance operations will need to be removed from this function, they belong in an executable called as a scheduled task.
Last edited: