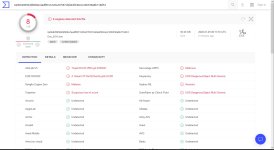
Today I received a suspicious letter with an attachment came to the work mailbox. I decided to check it in a virtual machine on the defender. What was my disappointment, the Windows defender did not react at all to the new virus. Although updated and defender settings are set to high using ConfigureDefende.