Windows Defender Disappointment
- Thread starter Mercenary
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Mark Of The Web, right mouse click any downloaded file and select properties
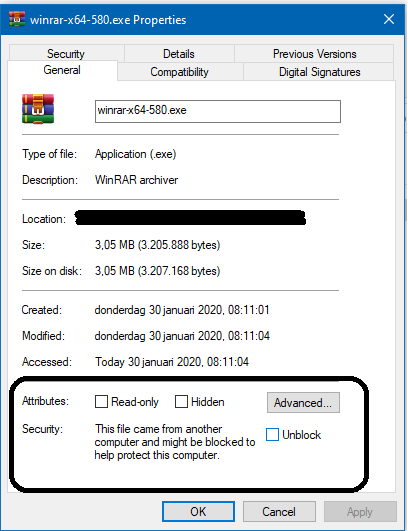
The Windows built-in compression feature is OK (preserves MOTW), but it works only for ZIP files. So, many users install 3rd party archivers - most of them do not preserve MOTW.Thanks for the info
I thought that the default Windows Explorer uncompression of ZIP files, skipped EXE files when the ZIP-file had MOTW?
Last edited:
What's MOTW?

Downloads and the Mark-of-the-Web
Last update: October 28, 2025 Background To help protect the user and their device, Windows and its applications will often treat files originating from the Internet more cautiously than files gene…
Simply it is information added to the file downloaded from the Internet when using popular web browsers, OneDrive, and some other online services. MOTW can be added to the file only on the NTFS drive (so it is lost on most flash drives, and also on CD/DVD drives, CD/DVD images, Memory Cards). File downloaders, application auto-updates, malware, etc. usually download files without MOTW. Most archivers (but not Windows built-in and Bandizip) do not preserve MOTW.
Some security solutions like SmartScreen integrated with Explorer and CyberCapture feature in Avast, require MOTW to work properly. The documents with MOTW trigger the Protected View feature in MS Office and Adobe Acrobat Reader.
Adding the MOTW before file execution (like in Hard_Configurator and RunBySmartScreen) can force the SmartScreen check also for files stored on flash drives, CD/DVD drives, CD/DVD images, Memory Cards, etc.
Last edited:
Today I received exactly the same letter as yesterday, only the sender is different, the name of the files is the same, but the hash the sum of the files is different)If your EXE file was in the archive, then you probably uncompressed it without MOTW. If so, then the file was executed without SmartScreen and "Block At First Sight" protection. If you propose WD to your clients, then install the Bandizip archiver that preserves MOTW while uncompressing executables from archives.
Anyway, after some hours this sample was detected by most AVs (including WD), so it is not a good example for disappointment about AV detection. It should be also blocked as 0-day malware by the WD ASR rule "Block executable files from running unless they meet a prevalence, age, or trusted list criteria", which is included only in ConfigureDefender MAX Protection Level (too many false positives).
The malware is classified as a kind of hack tool, so it is a prelude to further infection via payloads. That is why most AVs did not detect it as 0-hour malware (low level of suspicious actions). That is normal.
Almost all such infections can be avoided by simply waiting one day before opening attachments from not trusted emails. Of course, it is even better to not opening them at all.
The virus that arrived yesterday is already identified by 36 antivirus engines, a new file of 15 antiviruses. Although antiviruses detect it with the same name.
WD already defines himThanks for sharing. COuld you give it another try with ConfigureDefender set to MAX?
Your IT admin should not allow exe attachments to be received by email. That is leaving the door wide open to attacks. If it is a small business, and you are the admin, either switch to a more secure email provider, such as Outlook.com or Gmail, or figure out how to block suspicious file attachments with the service you have.Today I received exactly the same letter as yesterday, only the sender is different, the name of the files is the same, but the hash the sum of the files is different)
The virus that arrived yesterday is already identified by 36 antivirus engines, a new file of 15 antiviruses. Although antiviruses detect it with the same name.
View attachment 233038View attachment 233039
Our mail is located on Gmail, we use G Suite and Gmail did not send them to spam. The virus was archived in .lzh format and it was not attached to the letter, there was a link to google drive.Your IT admin should not allow exe attachments to be received by email. That is leaving the door wide open to attacks. If it is a small business, and you are the admin, either switch to a more secure email provider, such as Outlook.com or Gmail, or figure out how to block suspicious file attachments with the service you have.
Ah, thanks for the update. That makes sense. Links will always be a problem. @Andy Ful's suggestion to use BandiZip is a good one. The more recent versions of Windows will be able to apply SmartScreen filtering to it, since the MarkOfTheWeb will still be present.Our mail is located on Gmail, we use G Suite and Gmail did not send them to spam. The virus was archived in .lzh format and it was not attached to the letter, there was a link to google drive.
AV detection on email-delivered malware will always be hit-and-miss, because email tends to deliver zero-days. But SmartScreen is not easily fooled by zero-days. On the contrary, it is very suspicious of new samples, unless they bear a high-quality digital signature. That latter case is pretty rare, barring cases of high-level targeted attacks.
How about configuring the specific ASR rule "block executable content from email client and webmail?" According to MS Docs, exclusions can be made. Not sure if gmail would be included, though, as I don't have a virtual machine at the moment. Someone else know for sure? Regardless, I would not place 100% faith in just one mitigation, for anything.


Use attack surface reduction rules to prevent malware infection - Microsoft Defender for Endpoint
Attack surface reduction rules can help prevent exploits from using apps and scripts to infect devices with malware.
docs.microsoft.com
Then you are delusional. Nothing is invincible.
You may call it delusional, I call it "have thrown enough ##### at it for years" to know it's not a delusion but real world experience with it. Basically ever since they introduced behavior PDM module and cloud system it's been basically bullet proof. Something I can't really say for any other antivirus. Maybe Comodo Internet Security, but it's plagued by so many problems, usability issues and stagnating development that I can't really recommend it to anyone coz of that. But these two are actually the only ones I'd trust them to such extent.
Over the last few months, Kaspersky has not always been getting 100% in the commercial testing.You may call it delusional, I call it "have thrown enough **** at it for years" to know it's not a delusion but real world experience with it. Basically ever since they introduced behavior PDM module and cloud system it's been basically bullet proof. Something I can't really say for any other antivirus. Maybe Comodo Internet Security, but it's plagued by so many problems, usability issues and stagnating development that I can't really recommend it to anyone coz of that. But these two are actually the only ones I'd trust them to such extent.
90% is still way better 20%Over the last few months, Kaspersky has not always been getting 100% in the commercial testing.
This will work only for Outlook.How about configuring the specific ASR rule "block executable content from email client and webmail?" According to MS Docs, exclusions can be made. Not sure if gmail would be included, though, as I don't have a virtual machine at the moment. Someone else know for sure? Regardless, I would not place 100% faith in just one mitigation, for anything.

Use attack surface reduction rules to prevent malware infection - Microsoft Defender for Endpoint
Attack surface reduction rules can help prevent exploits from using apps and scripts to infect devices with malware.docs.microsoft.com
If you meant WD (20%), then If I correctly recall most of the exploit methods were tested on Windows 7. Anyway, the WD free features protection (no ATP) in businesses, cannot be good because many computers in local networks are not connected to the Internet. So, the main WD free protection is useless because it highly depends on the cloud backend (Cloud delivered protection, BAFS, SmartScreen). The computers can be infected remotely from a single compromised machine connected to the local network.90% is still way better 20%
"Kaspersky has not always been getting 100%"If you meant WD (20%), then If correctly recall most of the exploit methods were tested on Windows 7. Anyway, the WD free features protection (no ATP) in businesses, cannot be good because many computers in local networks are not connected to the Internet. So, the main WD free protection is useless because it highly depends on the cloud backend (Cloud delivered protection, BAFS, SmartScreen).
Which is fine as long as the percentage is high enough and there's some consistency among various testing organizations
defender is a minivan. if you want better performance you'll have to get a Ferrari 
I agree, I was just responding to @RejZoR's comment that Kaspersky gets it right every time. This may well be true in his personal testing, but the commercial testers didn't have exactly the same findings."Kaspersky has not always been getting 100%"
Which is fine as long as the percentage is high enough and there's some consistency among various testing organizations
F
ForgottenSeer 823865
If people knew that MS is partnered with AV vendors, and those vendors contribute in some extent to WD, all this debate wont be so long lol.
Basically WD is indirectly powered by AV vendors using WD ATP in their infrastructure . Example Bit Defender.
Basically WD is indirectly powered by AV vendors using WD ATP in their infrastructure . Example Bit Defender.
@Andy Ful But I've seen smartscreen.exe triggering even for files without MOTW. I use IDM and 7zip so MOTW is not present for anything I download but smartscreen does make dns queries after executing an exe files. How effective is this?
You may also like...
-
App Review Microsoft Defender Antivirus feat AI Defender
- Started by Shadowra
- Replies: 13
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Question Is GenP (An Adobe activitier) a virus?
- Started by Lintianyun Luo
- Replies: 16
-
New Update Defender Hardening Console (part of Hawk Eye Analysis Platform)
- Started by Trident
- Replies: 62
-
Question Kaspersky showed 52 disinfected objects after a full scan, but there's nothing in the quarantine folder.
- Started by nonamebob567
- Replies: 13
