E
Eddie Morra
Thread author
Hiya
I've decided to come back to testing Windows Defender's Attack Surface Reduction (ASR) feature - which is part of the Exploit Guard component - and I've created this thread to share my testing results for various rules as and when I have time to prepare and run a test for them. I'll test as many of them as I can because the documentation is extremely bland in terms of explaining how they actually work, and reverse-engineering how the internals of the different rule implementations work to conduct a proper and reliable test can be very time-consuming and tricky when they aren't all grouped together under the same components.
Please do note that this is not based on insider knowledge. I do not have any insider knowledge from Microsoft (e.g. Windows Defender Team) to help me conduct these tests. The testing is based on personal and manual research/trial and error. Due to this, you should take everything with a grain of salt, because it is very easy for a mistake to be made. Do not assume that any information presented to you under this thread by me is 100% accurate because there's no guarantee that this is the case. It is vital that you remember that the implementations of ASR rules internally are subject to change at any time through Windows/Office updates (as has been the case numerous times in the past - I've seen rules completely change over time with my own eyes), so always bear that in mind.
Before jumping into the tests, I will mention the specifications of my testing environment and how I am enabling these ASR rules, because this information may be important to other people (or help them replicate if they are capable of doing so).
I'm using Office 365 (based on the 2016 version) as a subscribed Business customer.
I am enabling the rules through the Group Policy Editor (type in "gpedit.msc" without "" in the Windows Run box (Windows Key + R) to open it). You will not have access to the Group Policy Editor by default if you're a Windows 10 Home user, however there is a way to install it... This won't be covered here for obvious reasons though.
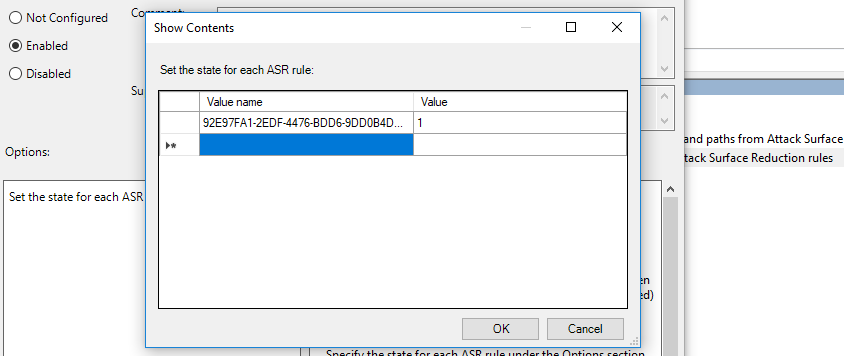
Group Policy Editor -> Computer Configuration -> Administrative Templates -> Windows Components -> Windows Defender Antivirus -> Windows Defender Exploit Guard -> Attack Surface Reduction -> Configure Attack Surface Reduction rules. All rules which are configured have the value of "1" to block.
This test is undoubtedly going to be one of the simplest but at the same time, it is one of the most important. 9 times out of 10, an Office VBA macro which is genuine and is not up to no good, is not going to need to be dependent on the Win32 API - this figure isn't from statistics, it is completely opinionated, so bear this in mind. The fact of the matter is, it isn't uncommon for malicious macro's to be dependent on the Win32 API... it is prevalent for malicious macro's. The reason for this is simple: the Win32 API provides the ability for a malicious macro to do a number of things from general process, file-system, registry and even networking management, among more. It's a no-brainer for malware authors who are relying on an Office VBA macro.
If we take a look at a recent blog post from the Windows Defender Team, we can actually see that a malicious macro they are using for analysis is using the Win32 API (as a demonstration of what I'm talking about).

Source:
Office VBA + AMSI: Parting the veil on malicious macros - Microsoft Secure %
The NtAllocateVirtualMemory routine which is being imported is from NTDLL and is part of the "Native API" (NTAPI). However, the WriteProcessMemory and EnumSystemCodePagesW routines are part of the "Win32 API".
In the past when I've tested this ASR rule, it was dynamic-based as opposed to static-based. This means that it was blocking the Win32 API calls as they were attempted whilst the Office VBA Macro script was being executed by the interpreter... but this is not the result of the test I've just conducted. It would appear that in the recent months, this ASR rule has been modified internally. I cannot get this ASR rule to block Win32 API calls dynamically at all anymore, I can only get it to block access to the Microsoft Office document containing the macro script which imports Win32 API routines.
The test for this ASR rule is incredibly simple and I will outline the testing process in bullet-point form to make it easy for readers to follow.
If you want an example of code you can put into a macro script to test this, you can copy-paste the below.
You do not need to actually call the imported routine, the import just has to be present.
Screenshots:
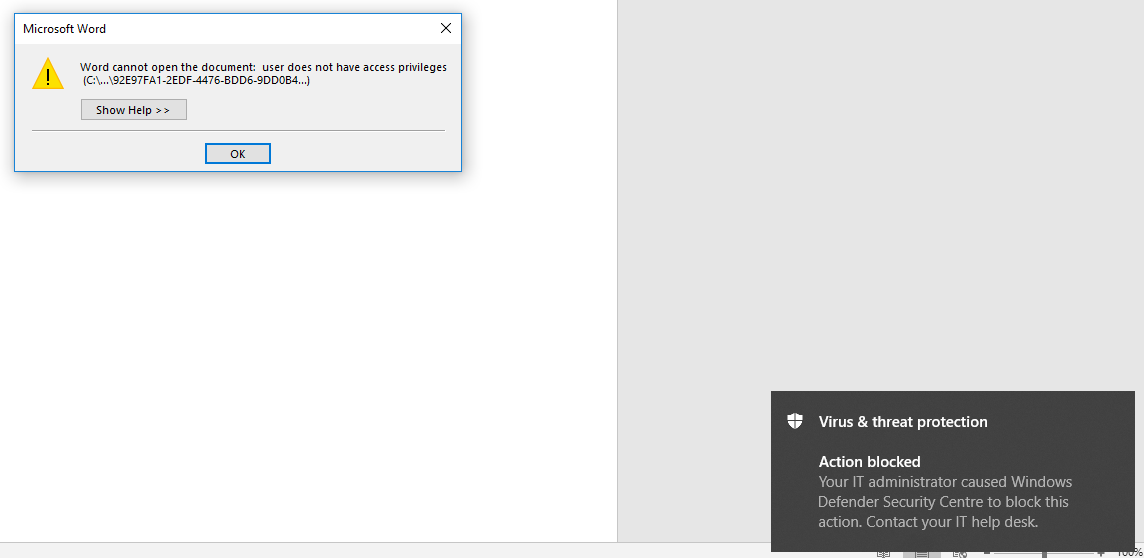
I think it is safe to conclude after this test that this ASR rule relies on a static macro script scanner as opposed to functioning dynamically now - in the past I recall it blocking the Win32 API calls instead of just throwing no access to the document. Beforehand, I was testing dynamically by injecting code into winword.exe which would do various things with the Win32 API, and I also tried enabling ASR and then creating a new document which would use the Win32 API from within a macro script, but it won't block the activity dynamically anymore. As of right now, I can only get it to block the entire document on open/saving when a macro is included which supports the Win32 API usage.
Test 2: Discuss - Windows Defender's Attack Surface Reduction (ASR) Rule Tests
I'm sure other members will have things to add in the comment discussion here about their own testing because I'm not the only person here who has tested/is testing ASR rules - please feel free to share and discuss ASR in the comments whether it be about testing or in general. For when I add new tests, I'll just post it as a new post on the thread.
Cya
I've decided to come back to testing Windows Defender's Attack Surface Reduction (ASR) feature - which is part of the Exploit Guard component - and I've created this thread to share my testing results for various rules as and when I have time to prepare and run a test for them. I'll test as many of them as I can because the documentation is extremely bland in terms of explaining how they actually work, and reverse-engineering how the internals of the different rule implementations work to conduct a proper and reliable test can be very time-consuming and tricky when they aren't all grouped together under the same components.
Please do note that this is not based on insider knowledge. I do not have any insider knowledge from Microsoft (e.g. Windows Defender Team) to help me conduct these tests. The testing is based on personal and manual research/trial and error. Due to this, you should take everything with a grain of salt, because it is very easy for a mistake to be made. Do not assume that any information presented to you under this thread by me is 100% accurate because there's no guarantee that this is the case. It is vital that you remember that the implementations of ASR rules internally are subject to change at any time through Windows/Office updates (as has been the case numerous times in the past - I've seen rules completely change over time with my own eyes), so always bear that in mind.
Before jumping into the tests, I will mention the specifications of my testing environment and how I am enabling these ASR rules, because this information may be important to other people (or help them replicate if they are capable of doing so).
Prerequisite information
Testing environment: Windows 10 Professional (version 1803) with no third-party security software installed. Windows Defender is enabled for real-time protection and has not had any configuration changes except for the ASR rules. I will re-test on Windows 10 Professional (version 1809) in a few weeks time and notify if any changes to the tests I am conducting now are present.
I'm using Office 365 (based on the 2016 version) as a subscribed Business customer.
I am enabling the rules through the Group Policy Editor (type in "gpedit.msc" without "" in the Windows Run box (Windows Key + R) to open it). You will not have access to the Group Policy Editor by default if you're a Windows 10 Home user, however there is a way to install it... This won't be covered here for obvious reasons though.
Group Policy Editor -> Computer Configuration -> Administrative Templates -> Windows Components -> Windows Defender Antivirus -> Windows Defender Exploit Guard -> Attack Surface Reduction -> Configure Attack Surface Reduction rules. All rules which are configured have the value of "1" to block.
Test 1
"Block Win32 API calls from Office macro"
The GUID for this ASR rule is 92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B."Block Win32 API calls from Office macro"
This test is undoubtedly going to be one of the simplest but at the same time, it is one of the most important. 9 times out of 10, an Office VBA macro which is genuine and is not up to no good, is not going to need to be dependent on the Win32 API - this figure isn't from statistics, it is completely opinionated, so bear this in mind. The fact of the matter is, it isn't uncommon for malicious macro's to be dependent on the Win32 API... it is prevalent for malicious macro's. The reason for this is simple: the Win32 API provides the ability for a malicious macro to do a number of things from general process, file-system, registry and even networking management, among more. It's a no-brainer for malware authors who are relying on an Office VBA macro.
If we take a look at a recent blog post from the Windows Defender Team, we can actually see that a malicious macro they are using for analysis is using the Win32 API (as a demonstration of what I'm talking about).

Source:
Office VBA + AMSI: Parting the veil on malicious macros - Microsoft Secure %
The NtAllocateVirtualMemory routine which is being imported is from NTDLL and is part of the "Native API" (NTAPI). However, the WriteProcessMemory and EnumSystemCodePagesW routines are part of the "Win32 API".
In the past when I've tested this ASR rule, it was dynamic-based as opposed to static-based. This means that it was blocking the Win32 API calls as they were attempted whilst the Office VBA Macro script was being executed by the interpreter... but this is not the result of the test I've just conducted. It would appear that in the recent months, this ASR rule has been modified internally. I cannot get this ASR rule to block Win32 API calls dynamically at all anymore, I can only get it to block access to the Microsoft Office document containing the macro script which imports Win32 API routines.
The test for this ASR rule is incredibly simple and I will outline the testing process in bullet-point form to make it easy for readers to follow.
- Create a new Microsoft Office document (I am using Microsoft Word for this test).
- After the new document has been created, press the Alt key + F11 at the same time to open Microsoft Visual Basic for Microsoft Office.
- At the top of the window -> Insert -> User Form.
- Double-click on the form to move into the code-view and you'll automatically have a private subroutine named "<FormName>_Click" generated for you. You can ignore this because it isn't required for the test.
- Outside of the private subroutine, import a Win32 API routine from a module like kernel32.dll or kernelbase.dll.
- Save and close down the Visual Basic window.
- Save the Microsoft Office document with the extension of *.docm.
- Close down the Microsoft Office application you're using for the test.
If you want an example of code you can put into a macro script to test this, you can copy-paste the below.
Code:
Private Declare PtrSafe Function OpenProcess Lib "kernel32" (ByVal DesiredAccess As Long, ByVal InheritHandle As Long, ByVal ProcessId As Long) As LongYou do not need to actually call the imported routine, the import just has to be present.
Screenshots:
Bear in mind, kernelbase.dll was introduced starting Windows 8, and was a replacement for holding some of the kernel32 API routines (among newer ones). For compatibility reasons, kernel32.dll routines which are now implemented under kernelbase.dll are just wrappers for calling the kernelbase.dll versions.
I think it is safe to conclude after this test that this ASR rule relies on a static macro script scanner as opposed to functioning dynamically now - in the past I recall it blocking the Win32 API calls instead of just throwing no access to the document. Beforehand, I was testing dynamically by injecting code into winword.exe which would do various things with the Win32 API, and I also tried enabling ASR and then creating a new document which would use the Win32 API from within a macro script, but it won't block the activity dynamically anymore. As of right now, I can only get it to block the entire document on open/saving when a macro is included which supports the Win32 API usage.
Thread post ending
Test 2: Discuss - Windows Defender's Attack Surface Reduction (ASR) Rule Tests
I'm sure other members will have things to add in the comment discussion here about their own testing because I'm not the only person here who has tested/is testing ASR rules - please feel free to share and discuss ASR in the comments whether it be about testing or in general. For when I add new tests, I'll just post it as a new post on the thread.
Cya
Last edited by a moderator: