I am slowly learning to configure Windows Firewall to block all outbound connections, except needed apps and vital Windows services. I could use some help about the processes needed for Windows Update and other essentials. I've been researching this with limited success.  Thanks in advance for any replies.
Thanks in advance for any replies.
Advice Request Windows Firewall: What outbound rules to enable vital Windows processes/services?
- Thread starter oldschool
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
Its better to use 3rd party GUI for Win firewall otherwise its really tough to configure. I use Firewall control from sphinxsoft. You can give Binisoft a try or FW made by Henry(I can't remember the name)
@Vasudev - I don't wish to use a 3rd party GUI or a separate WFP-based app like Simplewall. Too many bugs, popups, etc. Making Windows Firewall rules is not complex, but it is difficult to find information about needed processes, e.g. Windows Update - what I need to enable it.
By default, OS essential services aren't blocked unless you used Telemetry block rules for windows firewall as ps1 script.@Vasudev - I don't wish to use a 3rd party GUI or a separate WFP-based app like Simplewall. Too many bugs, popups, etc. Making Windows Firewall rules is not complex, but it is difficult to find information about needed processes, e.g. Windows Update - what I need to enable it.
By default, OS essential services aren't blocked unless you used Telemetry block rules for windows firewall as ps1 script.
OK, that helps. DUH, I think I'm good now.
That depends whats considered essential? Best to use privacy apps like shutup if ur concerned and bavne y already done so
That depends whats considered essential? Best to use privacy apps like shutup if ur concerned and bavne y already done so
I'm not concerned with privacy. I just want to block all outbound and allow only what apps I want and to keep Windows working properly.
Cool. Cuz maybe not everything essential is essential...or maybe it is..
True, I haven't seen a good tutorial for configuring Windows Firewall.I've been researching this with limited success.
Doing it without 3-rd party software will be painful for you. Furthermore, that can be effective for the users' privacy and against simple malware. The more complex malware will simply inject into one of the system processes (like svchost.exe) or use the process hollowing method to hide.I am slowly learning to configure Windows Firewall to block all outbound connections, except needed apps and vital Windows services. I could use some help about the processes needed for Windows Update and other essentials. I've been researching this with limited success.Thanks in advance for any replies.
The user can set firewall to 'Outbound Connections that do not match a rule are blocked.'
Use 'Advanced settings' >> 'Windows Firewall Properties', choose your active profile and set 'Outbound connections' from 'Allow (default)' to 'Block'
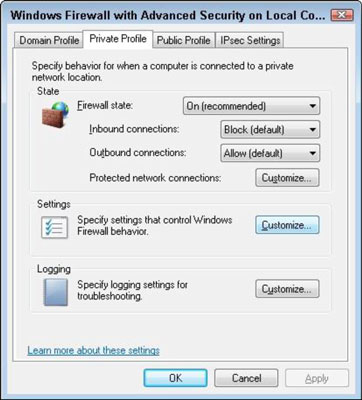
This will block by default outbound connections for the chosen firewall profile, except the green rules, which can be seen under the Outbound connections tab. So, the system processes, web browser, MS Store, will be allowed, but most applications will be blocked.
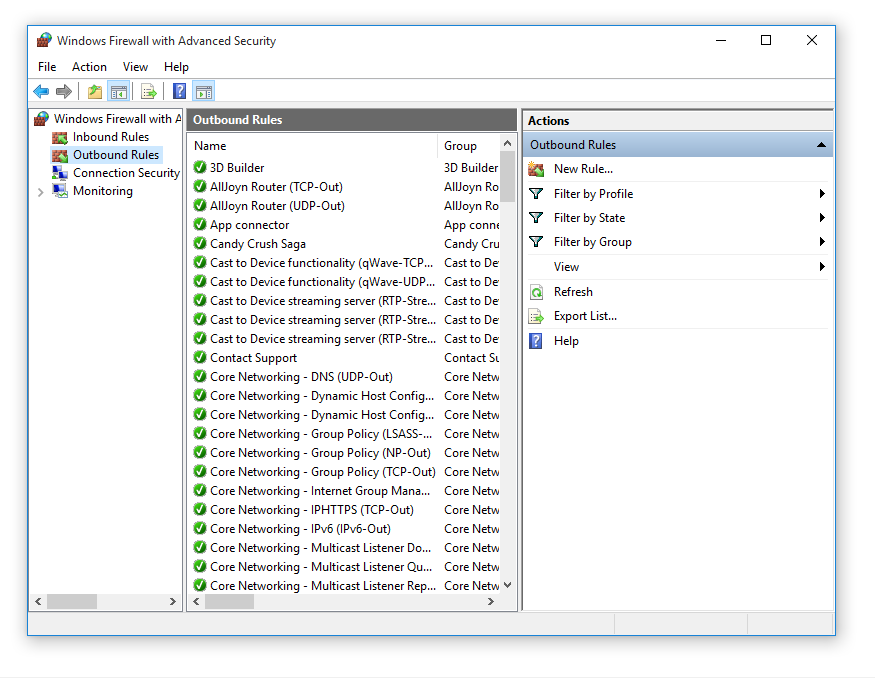
Use 'Advanced settings' >> 'Windows Firewall Properties', choose your active profile and set 'Outbound connections' from 'Allow (default)' to 'Block'
This will block by default outbound connections for the chosen firewall profile, except the green rules, which can be seen under the Outbound connections tab. So, the system processes, web browser, MS Store, will be allowed, but most applications will be blocked.
Last edited:
I agree with @Andy Ful.
@oldschool I suggest you NVT Connections Viewer. Great tool and which is not a real-time software.
https://www.novirusthanks.org/products/connections-viewer/

@oldschool I suggest you NVT Connections Viewer. Great tool and which is not a real-time software.
https://www.novirusthanks.org/products/connections-viewer/

The user can set firewall to 'Outbound Connections that do not match a rule are blocked.'
Use 'Advanced settings' >> 'Windows Firewall Properties', choose your active profile and set 'Outbound connections' from 'Allow (default)' to 'Block'
View attachment 208748
This will block by default outbound connections for the chosen firewall profile, except the green rules, which can be seen under the Outbound connections tab. So, the system processes, web browser, MS Store, will be allowed, but most applications will be blocked.
View attachment 208749
I have already done this, which is the easy part. Windows seems to work this way EXCEPT for Windows Update. I'm scratching my head trying to understand the required process(s) to make it functional.
Edit: I have already enabled Edge and SmartScreen.
Last edited:
As far as I know, WU requires only svchost, but lately I allow all outbound, so maybe I have missed something.Windows seems to work this way EXCEPT for Windows Update.
Code:
netsh advfirewall firewall add rule name="Svchost DNS" dir=out action=allow protocol=UDP remoteport=53 program="%WINDIR%\System32\svchost.exe"
netsh advfirewall firewall add rule name="Svchost TCP" dir=out action=allow protocol=TCP remoteport=80,443 program="%WINDIR%\System32\svchost.exe"I use LiveTcpUdpWatch to find out network traffic, since it logs traffic. Like, I could not figure out, how to get Update Time v1.2 working, because it makes the connection so fast, that it only blinks in network monitors like currports. Then I found this little gem from nirsoft.
People, who tried it, ended in a psychiatric ward. Just setting up loopback can be changeling and do not even get me started on LAN network. :emoji_expressionless:True, I haven't seen a good tutorial for configuring Windows Firewall.
I tested the setup from my previous post. It seems that it partially restricts the connections of system processes. For example, without any rule for svchost.exe, the firewall blocked downloading files via bitsadmin.exe and also via PowerShell with BitsTransfer cmdlet (both use BITS). The same effect was when I allowed svchost.exe with a safe option: Allow the connection if it is authenticated and integrity-protected. But, if svchost.exe was fully allowed by the firewall rule, then the download was allowed.
The similar is probably true for Windows Updates.
The similar is probably true for Windows Updates.
After applying the above rules, the Firewall can be bypassed again by the downloaders which uses bitsadmin.exe and PowerShell with BitsTransfer cmdlet.As far as I know, WU requires only svchost, but lately I allow all outbound, so maybe I have missed something.
...Code:netsh advfirewall firewall add rule name="Svchost DNS" dir=out action=allow protocol=UDP remoteport=53 program="%WINDIR%\System32\svchost.exe" netsh advfirewall firewall add rule name="Svchost TCP" dir=out action=allow protocol=TCP remoteport=80,443 program="%WINDIR%\System32\svchost.exe"
I tested the setup from my previous post. It seems that it partially restricts the connections of system processes. For example, without any rule for svchost.exe, the firewall blocked downloading files via bitsadmin.exe and also via PowerShell with BitsTransfer cmdlet (both use BITS). The same effect was when I allowed svchost.exe with a safe option: Allow the connection if it is authenticated and integrity-protected. But, if svchost.exe was fully allowed by the firewall rule, then the download was allowed.
The similar is probably true for Windows Updates.
I was taking this route, but got this warning message which I did not fully understand:
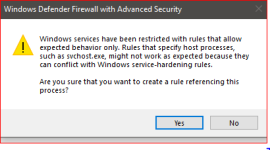
…
People, who tried it, ended in a psychiatric ward. Just setting up loopback can be changeling and do not even get me started on LAN network. :emoji_expressionless:
Yes, the men with the white coats are at my door now!
So I guess, not allowing any Windows processes is a good choice then, while allowing them only temporarily, when updating and such.After applying the above rules, the Firewall can be bypassed again by the downloaders which uses bitsadmin.exe and PowerShell with BitsTransfer cmdlet.
So I guess, not allowing any Windows processes is a good choice then, while allowing them only temporarily, when updating and such.
Yes, that is what I believe now. Without any testing, I got the funny feeling that enabling some Windows processes was not a good idea. I have Edge, Brave Beta, AV and VodooShield working. I guess that's all I need. So it's not rocket science after all, if one takes the approach you suggest. Making the rules is definitely not the problem.
You may also like...
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
Serious Discussion Simple Steps to Secure Your Windows 11 PC
- Started by Divergent
- Replies: 0
-
App Review Evorim Free Firewall
- Started by Dreams&Visions
- Replies: 3
-
