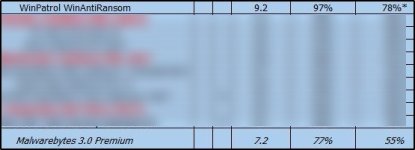
H
hjlbx
Thread author
But more seriously... this is why I opt for SRP default-deny.
I don't have to guess
I dont' have to flip a coin
However, even though that is all good and dandy, network security remains a huge security risk with its many vulnerabilities along the whole transmission chain.
- I clean install OS (system is clean)
- I install wanted softs (system is still clean)
- I install SRP and lock down system (system is locked into clean state)
- I do not introduce unknown\untrusted stuff to system
- Everything that isn't allowed, is denied - with no reliance upon AV signatures, Authenticode, file reputation, HIPS, behavior blocker, Ai, etc, etc
- What is allowed, but vulnerable, is restricted to Standard User access rights
I don't have to guess
I dont' have to flip a coin
However, even though that is all good and dandy, network security remains a huge security risk with its many vulnerabilities along the whole transmission chain.