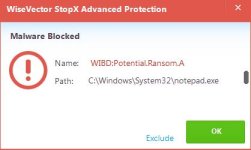
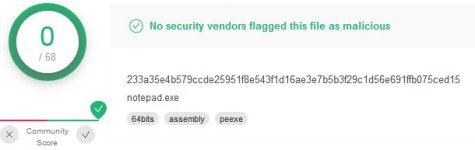
Excellent initiative and result speaks volumes to such combo. Very persuasive and formidable. Helpful challenges and appreciate the results and opinions.I have found no issues with the dumb detection routines as for in the wild malware there were samples caught by one and allowed by others but overall leading to additive protection. But the AI component of WV still impresses, and along with Comodo's auto-sandbox true zero day malware really don't have much of a chance. Last week I coded up a ransomware file loosely based on Ryuk (true zero-day) and although undetected by the dumb components, the WV AI after less than a minutes "thought" came back with a detection (potential.ransomware.A), detected and cleaned up my ransomware nor and some trivia dropped in AppData/Local). Poor malware didn't even make it to the sandbox.
(and regarding WF- seems not to matter if it is enabled or disabled as it neither helps nor detracts)
Unmaintained WiseVector Free AI Driven Security
- Thread starter Thirio
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
For myself no need for another firewall.Wisevector works well with all its components .
Is there any way to make WiseVector to run on boot from startup folder or adding run reg key?
- Aug 17, 2014
- 12,729
- 123,838
- 8,399
Is there any way to make WiseVector to run on boot from startup folder or adding run reg key?
Here WiseVector starts automatically on Windows 10 admin-accounts, but doesn't work on SUA (standard user account).
On admin account I try to add WiseVector.exe shortcut to startup folder WiseVector did not start and adding run reg keys did not work.
Hi @WiseVector
It's great your new version comes with FW and HIPS
Any comment on Kaspersky FW in KIS? Is yours better in any way? I already have KIS so should I disable one FW
Can attach some screenshots of WV's FW and HIPS settings pages?
Thanks
We heard there is no conflict between WVSX and KIS, so you can enable both FW.
But if you feel any lag, such as slow website loading, you can try to turn off KIS's firewall.
If you are not so familiar with computer knowledge you can just keep the default settings of WVSX.
On admin account I try to add WiseVector.exe shortcut to startup folder WiseVector did not start and adding run reg keys did not work.
WVSX relies on scheduled tasks to start with Windows. Windows + R-> Run, and then type taskschd. msc.
Then you can check if the WVSX's items exist in Task Scheduler. If not, open WV->settings->disable->re-enable "Automatically launch at system startup".
Please do not use notepad to modify the files in the ransomware trap folder of WVSX. To see all ransomware trap folders, open WV->Settings->Advanced->Anti-Ransomware settings->Enable deception-based ransomware detection->Set up.
Also for ransomware, uploading to VT doesn't make sense. Legitimate programs can be used by ransomware to bypass AV.
For example, Netwalker->explorer.exe, Sodinokibi->Windows Defender's binaries.
Is there any way to auto start WVSX on boot without Task Scheduler?WVSX relies on scheduled tasks to start with Windows. Windows + R-> Run, and then type taskschd. msc.
Then you can check if the WVSX's items exist in Task Scheduler. If not, open WV->settings->disable->re-enable "Automatically launch at system startup".
Is there any way to auto start WVSX on boot without Task Scheduler?
Currently WVSX can only be started by Task Scheduler on boot, can you tell me why you need to start WV without Task Scheduler?
We can change this according to user's needs.
MSITC WiseVector StopX AI based detection and prevention of HiveNightmare aka SeriousSAM
This video shows how WiseVector StopX uses artificial intelligence to detect an exploit for a security vulnerability, initially with real-time protection activated and real-time protection deactivated. HiveNightmare is the name of a proof of concept, i.e. a functioning code with which vulnerabilities in operating systems can be exploited.
Malware loves task scheduler to do its dirty work. Can you add optional alternative boot option disabled by default.Currently WVSX can only be started by Task Scheduler on boot, can you tell me why you need to start WV without Task Scheduler?
We can change this according to user's needs.
Malware loves task scheduler to do its dirty work. Can you add optional alternative boot option disabled by default.
We are working on this issue. If users have disabled the task scheduler service, we will try another way to start WVSX automatically.
Thank you very muchWe are working on this issue. If users have disabled the task scheduler service, we will try another way to start WVSX automatically.
hxxps://www.youtube.com/watch?v=csHGxDqf_wQ
Intermission - WiseVector StopX 2.73 Test vs Fresh Malware Samples Part 2
League of Antivirus
hxxps://www.youtube.com/watch?v=vTnZSu51-G0&t=0s
Intermission - WiseVector StopX 2.73 Test vs Fresh Malware Samples Part 1
Intermission - WiseVector StopX 2.73 Test vs Fresh Malware Samples Part 2
League of Antivirus
hxxps://www.youtube.com/watch?v=vTnZSu51-G0&t=0s
Intermission - WiseVector StopX 2.73 Test vs Fresh Malware Samples Part 1
Last edited:
Thanks the author for the testing, any testing of WVSX will help us to improve.hxxps://www.youtube.com/watch?v=csHGxDqf_wQ
Intermission - WiseVector StopX 2.73 Test vs Fresh Malware Samples Part 2
League of Antivirus
hxxps://www.youtube.com/watch?v=vTnZSu51-G0&t=0s
Intermission - WiseVector StopX 2.73 Test vs Fresh Malware Samples Part 1
First of all, I don't think these are fresh malware samples, as I understand fresh malware samples should appear at least within one month, preferably not present in Virustotal or at least less than 30 detections, or less than 20 in VT. According to the video we can tell that these samples probably come from Virussign or Virusshare, because Virussign often has many normal files that are infected with Floxif virus, Virusshare are full of PUPs. Samples from Virussign are definitely not fresh samples.
In the end of the video, most of the infected files are files infected by Floxif virus and PUPs, with a few worms we think they are the same file and one Quasar malware.
1. We are confident that our behavior detection is able to block Floxif virus. In the author's test WVSX has blocked one, please see screenshot below. We have tested several files infected by Floxif virus by ourselves and we can sure WVSX is able to block them all. If there are testers willing to test Floxif samples with WVSX, we would appreciate it. If WVSX failed to block any Floxif sample, please post it here. Testers can disconnect from the network to prove we haven't updated anything。
2. We observed that WVSX's own files are also infected by Floxif virus, which should not be possible because our kernel drivers prevent other programs from writing to WVSX's installation folder. This should be result in running a large number of Floxif virus at the same time.
3. For PUPs, if we do not observe any advertising or spying behavior in our environment, we will not add the detection. For example, there are several mail.ru PUPs in the vlogger's test, we have analyzed many samples developed by mail.ru and didn't observe advertising behavior in our environment. Also, as far as we know, mail.ru has a large number of users in Russia, so we would be quite cautious to flag these files.
4. For older malware samples like Quasar, they may not exhibit malicious behavior if their CC server is dead.
We think that the reason for these infections may be due to running a large number of samples at the same time, and WVSX have some problems when faced stress test. We will do more stress tests ourselves in the future, but you should know that it is impossible for a normal user to run a large number of malicious programs at once.
Hi anyone know if these tests on max settings would be the same or is the test yet to be done.? Just curiuos.
I have no doubt that this would have played a significant part. Running a great deal of potentially malicious files simultaneously is as far from real-world as one can get. Although perhaps a test like this has some use when tested against a solely signature based (dumb) security application, it can have little value against a product that operates on a different level (HIPS, Sandbox, AI).We think that the reason for these infections may be due to running a large number of samples at the same time
Personally I coded various types of malware, ensuring true zero day status, and have notes that WV will take time (sometimes up to 30 seconds) before a detection will occur. What would happen if 5 of these were gang-banged on the system was something that I felt would be of no interest as it would be hardly a true and accurate scenario.
So although a video such as this could be mesmerizing to watch with all the flashing stuff on the screen, one would not be wrong to question its validity (but that's just the opinion of lonely girl in an increasingly confusing universe).
Seems like a plausible approach to wreak havoc. Much like a "MIRV" --- multiple independently targetable reentry vector that defeats the "iron dome".if 5 of these were gang-banged on the system
You may also like...
-
Security News ESET Warns AI-driven Malware Attack and Rapidly Growing Ransomware Economy
- Started by Brownie2019
- Replies: 7
-
Malware News AI-Driven Obfuscated Malicious Apps Bypassing Antivirus Detection to Deliver Malicious Payloads
- Started by Brownie2019
- Replies: 2
-
Security News Hackers Launch Over 91,000 Attacks on AI Systems Using Fake Ollama Servers
- Started by Brownie2019
- Replies: 2
-
Expired Ashampoo HDR #10 [with AI] lifetime free
- Started by Brownie2019
- Replies: 0
-
Technology ‘Worst in Show’ CES products include AI refrigerators, AI companions and AI doorbells
- Started by Gandalf_The_Grey
- Replies: 6