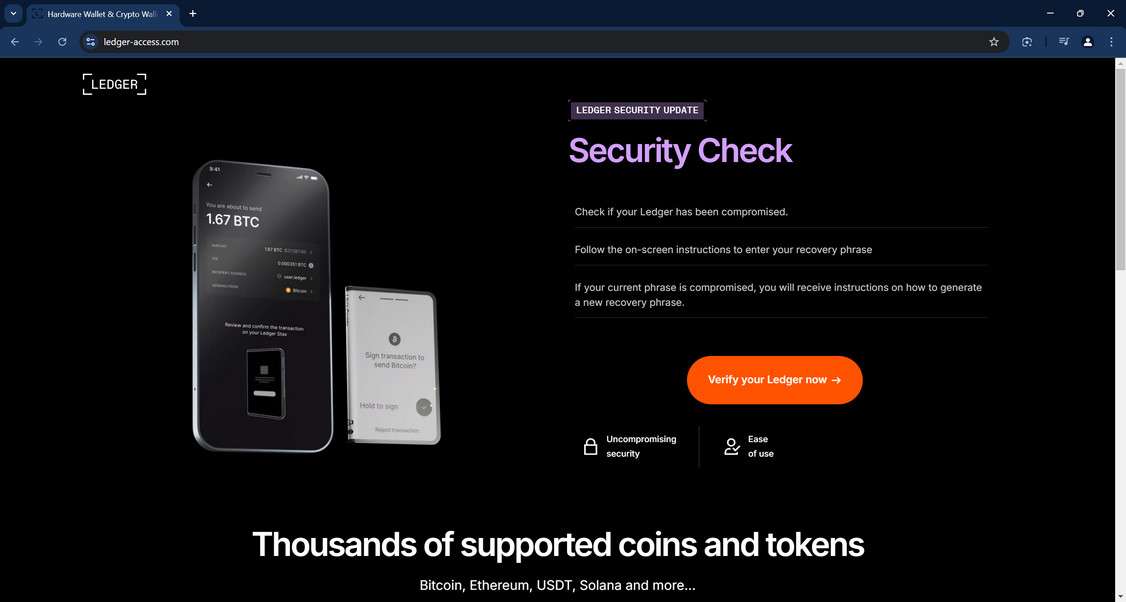
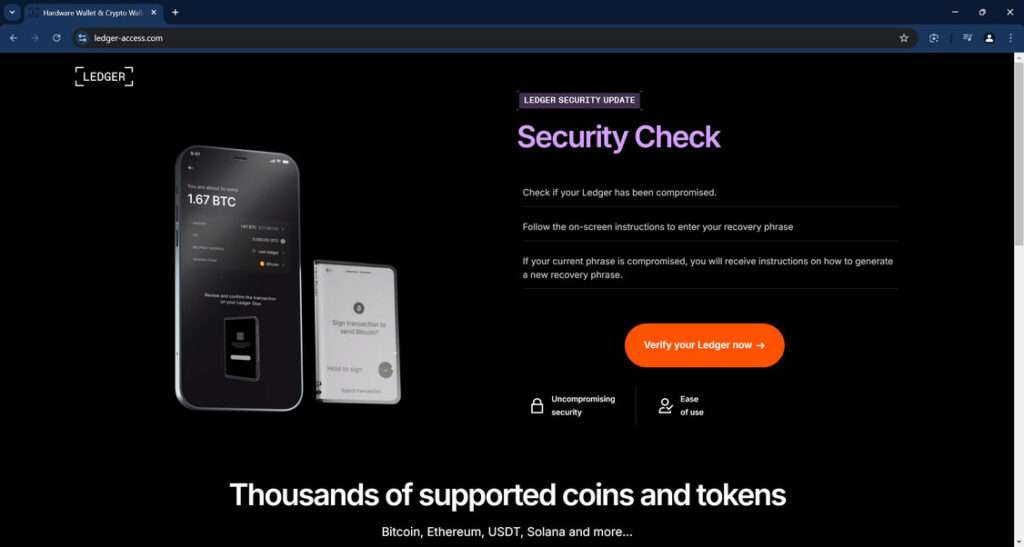
Picture this: You’re going about your day when suddenly an urgent email from Ledger pops up in your inbox. It claims there’s been a data breach and urges you to verify your recovery phrase immediately to keep your crypto assets safe. Your heart races as you click the link, worried about the security of your funds. But hold on, don’t enter anything just yet. This is a sneaky phishing scam designed to trick you into handing over your sensitive information to cybercriminals.
In this article, we’ll dive deep into the Ledger Recovery Phrase Verification email scam, exposing how it works and what you can do to protect yourself.
Scam Overview
The Ledger Recovery Phrase Verification email scam is a highly deceptive phishing attack that targets cryptocurrency users. The scammers send out an email that appears to come from Ledger, a well-known manufacturer of hardware wallets for securely storing cryptocurrencies. The email claims that there has been a data breach affecting Ledger’s service, and that certain recovery phrases (also known as “seed phrases”) may have been exposed. Recovery phrases are a crucial backup mechanism for cryptocurrency wallets. They consist of a series of words that can be used to restore access to the wallet and its associated funds if the device is lost, stolen, or damaged.
In the email, the scammers create a sense of urgency by emphasizing the need to verify the security of the user’s recovery phrase. They provide a link to a supposed “official verification page” where users are instructed to enter their recovery phrase. The email may also include a button labeled “Verify My Recovery Phrase” to make the process seem more legitimate. However, the link in the email does not lead to Ledger’s actual website. Instead, it directs users to a fake phishing site designed to look like Ledger’s official platform. The phishing site, often hosted on a domain that closely resembles Ledger’s legitimate domain (e.g., ledger-access.com), is set up to steal the user’s recovery phrase.
By creating a sense of urgency and leveraging the trust that users have in Ledger, the scammers aim to trick individuals into revealing their sensitive recovery phrases. Once the scammers obtain the recovery phrase, they gain full control over the associated cryptocurrency wallets and can steal the funds stored within them. This scam is particularly dangerous because it exploits the fear and concern that users have about the security of their crypto assets. By posing as a legitimate company and creating a convincing narrative about a data breach, the scammers manipulate users into taking action without properly verifying the authenticity of the email or the linked website.
It’s crucial for cryptocurrency users to be aware of this scam and to exercise caution when receiving unsolicited emails claiming to be from Ledger or any other crypto-related service. Legitimate companies will never ask users to share their recovery phrases via email or through a linked website. Recovery phrases should always be kept confidential and never shared with anyone. In the following sections, we will delve into the step-by-step process of how this scam works and provide guidance on what to do if you have fallen victim to it.
How The Scam Works
The Ledger Recovery Phrase Verification email scam is a carefully orchestrated phishing attack that follows a step-by-step process to deceive cryptocurrency users. Let’s break down how this scam unfolds:
Step 1: Crafting the Phishing Email
The scammers begin by creating an email that closely resembles an official communication from Ledger. They use Ledger’s branding, logo, and a convincing email template to make the message appear legitimate. The email typically has a subject line that implies urgency, such as “Action Required: Ledger Data Breach – Check Your Recovery Phrase.”
Step 2: Claiming a Data Breach
In the body of the email, the scammers fabricate a story about a recent data breach affecting Ledger’s service. They state that while the Ledger wallets themselves remain secure, certain recovery phrases may have been exposed. This claim is designed to create a sense of urgency and concern among recipients, as the recovery phrase is a critical component of wallet security.
Here is how the email scam might look:
Subject Action Required: Ledger Data Breach – Check Your Recovery Phrase
LEDGER
Verify the Security of Your Recovery Phrase
Hello,
We want to inform you of a recent data breach affecting our service. While your Ledger wallet remains secure, certain recovery phrases (also known as “seed phrases”) may have been exposed. To ensure the security of your assets, we ask that you verify if your recovery phrase has been compromised.
Steps to Verify Your Recovery Phrase Security:
Visit our official verification page.
Enter your recovery phrase following the on-screen instructions.
If your current phrase is compromised, you will receive instructions on how to generate a new recovery phrase.
If you have any questions or need assistance, our support team is here to help. Click the button below to go directly to the verification
page:
Verify My Recovery Phrase
Step 3: Urging Recovery Phrase Verification
The email emphasizes the importance of verifying the security of the user’s recovery phrase to ensure the safety of their assets. It provides a set of instructions, urging the user to visit an “official verification page” by clicking on a provided link or button. The scammers often use language that implies the verification process is mandatory and time-sensitive.
Step 4: Directing to a Fake Website
When the user clicks on the link or button provided in the email, they are redirected to a fake website that closely mimics Ledger’s official platform. The phishing site is usually hosted on a domain that resembles Ledger’s legitimate domain, such as “ledger-access.com.” This adds to the convincing nature of the scam, as users may not immediately notice the subtle difference in the URL.
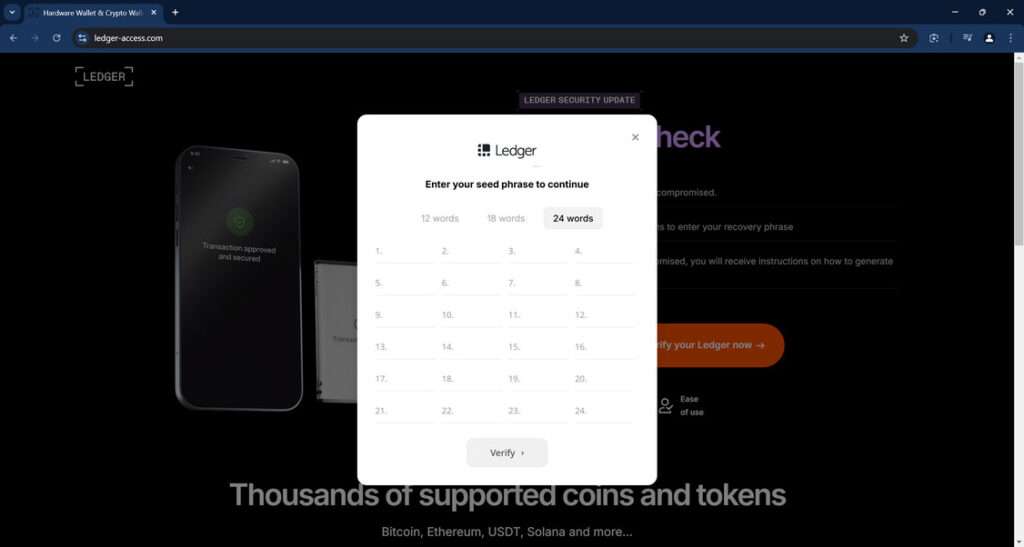
Step 5: Requesting Recovery Phrase Input
On the fake website, the user is presented with a form or input field where they are instructed to enter their recovery phrase. The website may claim that this step is necessary to check if the user’s current recovery phrase has been compromised. The scammers often provide reassurances that if the phrase is found to be compromised, the user will receive instructions on how to generate a new one.
Step 6: Stealing the Recovery Phrase
Once the user enters their recovery phrase on the fake website, the scammers capture this sensitive information. With the recovery phrase in hand, the scammers have complete access to the user’s associated cryptocurrency wallets. They can then proceed to steal the funds stored within those wallets, transferring the cryptocurrencies to their own addresses.
Step 7: Leaving No Trace
After successfully stealing the user’s recovery phrase and funds, the scammers typically take down the fake website to avoid detection. They may also delete or abandon the email account used to send the phishing emails, making it difficult for authorities to trace their activities.
Throughout this process, the scammers rely on social engineering techniques to exploit the trust and concern of cryptocurrency users. By crafting a convincing narrative and creating a sense of urgency, they manipulate individuals into taking action without thoroughly verifying the legitimacy of the email or website.
It’s important to note that legitimate companies like Ledger will never ask users to share their recovery phrases via email or through a linked website. Recovery phrases should always be kept confidential and securely stored offline. In the next section, we will discuss what steps to take if you have fallen victim to this scam.
What to Do if You Have Fallen Victim to This Scam
If you have fallen victim to the Ledger Recovery Phrase Verification email scam and have entered your recovery phrase on the fake website, it’s crucial to take immediate action to minimize the potential damage. Here are the steps you should follow:
- Contact Ledger Support: Reach out to Ledger’s official support team through their website or official communication channels. Inform them about the scam email you received and that you have inadvertently shared your recovery phrase. They can provide guidance on the next steps to take.
- Change Your Recovery Phrase: If you have entered your recovery phrase on the fake website, consider it compromised. Generate a new recovery phrase for your Ledger wallet immediately. Follow the official instructions provided by Ledger to reset your device and create a new recovery phrase. Make sure to store the new recovery phrase securely and never share it with anyone.
- Transfer Your Funds: If you still have access to your cryptocurrency wallets, transfer your funds to a new wallet with a different recovery phrase as soon as possible. This step is crucial to prevent the scammers from stealing your assets. Use a reputable and secure wallet provider to create a new wallet and ensure that you follow best practices for wallet security.
- Report the Scam: Report the phishing email and fake website to the relevant authorities, such as your local law enforcement or cybercrime units. Provide them with as much information as possible, including the phishing email, the fake website URL, and any other relevant details. This can help prevent others from falling victim to the same scam.
- Strengthen Your Security Measures: Review and strengthen your overall security measures to protect yourself from future phishing attempts. Enable two-factor authentication (2FA) on your accounts whenever possible, use strong and unique passwords, and be cautious when clicking on links or downloading attachments from unsolicited emails.
- Educate Yourself: Take the time to educate yourself about phishing scams, social engineering techniques, and best practices for cryptocurrency security. Stay informed about the latest scams targeting the crypto community and be vigilant when receiving any communication claiming to be from crypto-related services.
- Spread Awareness: Share your experience with others in the cryptocurrency community to raise awareness about this scam. By alerting others, you can help prevent them from falling victim to similar phishing attempts in the future.
Remember, prevention is key when it comes to protecting yourself from phishing scams. Always be cautious when receiving unsolicited emails, double-check the legitimacy of the sender and any linked websites, and never share your recovery phrase or other sensitive information unless you are absolutely certain you are dealing with a legitimate source.
If you have suffered financial losses due to this scam, it’s important to document the incident thoroughly and consider seeking legal advice to explore potential avenues for recovery. While it may be difficult to retrieve stolen funds, reporting the scam and cooperating with authorities can help combat these fraudulent activities and protect others from falling victim.
Frequently Asked Questions About the Ledger Recovery Phrase Verification Email Scam
Q1: What is the Ledger Recovery Phrase Verification email scam?
A1: The Ledger Recovery Phrase Verification email scam is a phishing attack that targets cryptocurrency users. Scammers send an email claiming to be from Ledger, stating that there has been a data breach and urging users to verify their recovery phrase (also known as a seed phrase) by clicking on a provided link. However, the link leads to a fake website designed to steal the user’s recovery phrase, allowing the scammers to access and steal the funds stored in the associated cryptocurrency wallets.
Q2: How can I identify a Ledger Recovery Phrase Verification scam email?
A2: To identify a Ledger Recovery Phrase Verification scam email, look for the following red flags:
- The email creates a sense of urgency about a supposed data breach and the need to verify your recovery phrase immediately.
- The email includes a link or button to a “verification page” that is not the official Ledger website.
- The email asks you to enter your recovery phrase on a website or share it via email.
Remember, legitimate companies like Ledger will never ask you to share your recovery phrase through an email or a linked website.
Q3: What should I do if I receive a Ledger Recovery Phrase Verification scam email?
A3: If you receive a Ledger Recovery Phrase Verification scam email, do not click on any links or buttons provided in the email. Do not enter your recovery phrase or any other sensitive information on any website linked from the email. Instead, report the email as spam or phishing to your email provider and delete it from your inbox. If you are unsure about the legitimacy of an email claiming to be from Ledger, contact Ledger’s official support directly through their website.
Q4: What steps should I take if I have fallen victim to the Ledger Recovery Phrase Verification scam?
A4: If you have entered your recovery phrase on a fake website linked from a Ledger Recovery Phrase Verification scam email, take the following steps immediately:
- Contact Ledger support and inform them about the incident.
- Generate a new recovery phrase for your Ledger wallet and reset your device.
- Transfer any remaining funds to a new wallet with a different recovery phrase.
- Report the scam to the relevant authorities, such as local law enforcement or cybercrime units.
- Strengthen your overall security measures, such as enabling 2FA and using strong passwords.
Q5: How can I protect myself from falling victim to the Ledger Recovery Phrase Verification scam?
A5: To protect yourself from the Ledger Recovery Phrase Verification scam and similar phishing attempts, follow these best practices:
- Never share your recovery phrase or private keys with anyone, including through emails or linked websites.
- Always double-check the legitimacy of any email claiming to be from Ledger or other crypto-related services.
- Verify the authenticity of any linked website by carefully examining the URL and ensuring it is the official Ledger website.
- Enable two-factor authentication (2FA) on your accounts whenever possible.
- Keep your recovery phrase securely stored offline and never save it digitally.
- Stay informed about the latest scams targeting the cryptocurrency community and educate yourself on phishing techniques.
Q6: Will Ledger ever ask me to share my recovery phrase via email?
A6: No, Ledger will never ask you to share your recovery phrase via email or through a linked website. Your recovery phrase is a sensitive piece of information that grants access to your cryptocurrency wallets. Legitimate companies, including Ledger, understand the importance of keeping your recovery phrase confidential and will never request it through unsecured channels like email. If you receive an email asking for your recovery phrase, it is almost certainly a scam.
Q7: What should I do if I’m unsure about the legitimacy of an email claiming to be from Ledger?
A7: If you are unsure about the legitimacy of an email claiming to be from Ledger, do not click on any links or download any attachments provided in the email. Instead, go directly to Ledger’s official website by typing the URL into your browser’s address bar. From there, you can navigate to the support section and contact Ledger’s official support team. They will be able to verify the authenticity of the email and provide guidance on how to proceed.
Q8: Can I recover my funds if I have fallen victim to the Ledger Recovery Phrase Verification scam?
A8: If you have shared your recovery phrase with scammers through the Ledger Recovery Phrase Verification scam, it may be difficult to recover your stolen funds. Cryptocurrency transactions are generally irreversible, and once the scammers have access to your wallets, they can quickly transfer the funds to their own addresses. However, it is still important to report the incident to Ledger support and the relevant authorities. In some cases, law enforcement may be able to trace the stolen funds and take action against the scammers. Additionally, reporting the scam can help prevent others from falling victim to similar phishing attempts in the future.
Q9: What are some common red flags to look out for in phishing emails?
A9: Some common red flags to look out for in phishing emails include:
- A sense of urgency or pressure to take immediate action
- Poor grammar, spelling errors, or unusual phrasing
- Suspicious or unfamiliar email addresses or domain names
- Requests for sensitive information, such as recovery phrases, private keys, or login credentials
- Links or attachments that seem suspicious or unfamiliar
- Threats or warnings of negative consequences if you don’t comply with the email’s instructions
If you notice any of these red flags in an email, be cautious and verify the legitimacy of the sender through official channels before taking any action.
Q10: How can I report a Ledger Recovery Phrase Verification scam email?
A10: If you receive a Ledger Recovery Phrase Verification scam email, you can report it through the following channels:
- Forward the email to Ledger’s official support team at support@ledger.com to notify them of the scam attempt.
- Report the email as spam or phishing to your email provider. This helps improve their filters and protects other users from receiving similar scam emails.
- Report the scam to your local law enforcement or cybercrime units. Provide them with as much information as possible, including the email, any linked websites, and details of any financial losses incurred.
- Notify the cryptocurrency community through forums, social media, or other channels to raise awareness and prevent others from falling victim to the scam.
By reporting Ledger Recovery Phrase Verification scam emails, you can help combat these fraudulent activities and protect yourself and others from financial losses and privacy breaches.
The Bottom Line
The Ledger Recovery Phrase Verification email scam is a stark reminder of the importance of vigilance and caution in the world of cryptocurrencies. Scammers are constantly evolving their tactics to deceive users and steal their valuable assets. By understanding how this scam works and taking proactive measures to protect yourself, you can significantly reduce the risk of falling victim to such phishing attempts.
Remember, legitimate companies like Ledger will never ask you to share your recovery phrase via email or through a linked website. Always be skeptical of unsolicited communications, double-check the authenticity of the sender and any provided links, and prioritize the security of your recovery phrase and private keys.
If you do fall victim to this scam, swift action is crucial. Contact Ledger support, change your recovery phrase, transfer your funds to a new wallet, and report the incident to the relevant authorities. By staying informed, educating yourself about potential scams, and adopting best practices for cryptocurrency security, you can navigate the crypto landscape with greater confidence and protect your assets from malicious actors.
Stay safe out there, and always remember: when it comes to your recovery phrase, keep it secret, keep it safe.