If your computer is locked, and you are seeing a “Your PC is blocked” notification from the International Cyber Security Protection Alliance (ICSPA), then your computer is infected with a piece of malware known as Trojan Reveton.
This threat is distributed through several means. Malicious websites, or legitimate websites that have been compromised, may drop the threat onto a compromised computer. This drive-by-download often happens surreptitiously. Another method used to propagate this type of malware is spam email containing infected attachments or links to malicious websites. The threat may also be downloaded manually by tricking the user into thinking they are installing a useful piece of software. Ransomware is also prevalent on peer-to-peer file sharing websites and is often packaged with pirated or illegally acquired software.
Once installed on your computer, the ICSPA virus will display a bogus notification, that pretends to be from the official law enforcement agency (FBI, Europol or another law enforcement agency) and states that your computer has been blocked due to it being involved with the distribution of pornographic material, SPAM and copyrighted content.
The International Cyber Security Protection Alliance (ICSPA) virus will lock you out of your computer and applications, so whenever you’ll try to log on into your Windows operating system or Safe Mode with Networking, it will display instead a lock screen asking you to pay a non-existing fine in the form of a MoneyPak, Ukash or PaySafeCard code.
Furthermore, to make its alert seem more authentic, this virus also has the ability to access your installed webcam, so that the bogus ICSPA notification shows what is happening in the room.
The ICSPA notification is used by cyber criminals alongside the name of known international law enforcement agencies like Federal Bureau of Investigation (FBI),Europol and Central Intelligence Agency (CIA), or local law enforcement agencies: Royal Canadian Mounted Police, United Kingdom Police or Australian Federal Police.
Here is an example of how the bogus ICSPA notification:
FBI CYBERCRIME DIVISION
International Cyber Security Protection Alliance
ATTENTION! Your PC is blocked due at least one of the reasons specified below.
You have been violating Copyright and Related Rights Law. (Video, Music, Software) and illegally using or distributing copyrighted content, thus infringing Article 1, Section 2, Clause 8, also known as the Copyright of the Criminal Code of United States of America.
Article 1, Section 2, Clause 8 of the Criminal Code provides for a fine of 200 to 500 minimal wages or a deprivation of liberty for 2 to 8 years.
You have been viewing or distributing prohibited Pornographic content (Child Porn/Zoophilia and etc). Thus violating Article 2, Section 1, Clause 2 of the Criminal Code of United States of America.
Article 2, Section I, Clause 2 of the Criminal Code provides for a deprivation of liberty for 4 to 12 years.
Illegal access to computer data has been initiated from your PC, or you have been…
Article 2, Section 1, Clause 8 of the Criminal Code provides for a fine of up to 5200,000 and/or a deprivation of liberty for 4 to 9 years.
Illegal access has been initiated from your PC without your knowledge or consent, your PC may be infected by malware, thus you are violating the law On Neglectful Use of Personal Computer.
Article 2, Section 1, Clause 1 of the Criminal Code provides for a fine of up to 5200,000 and/or deprivation of liberty for 4 to 9 years.
Spam distribution or other unlawful advertising has been effected from your PC as a profit-seeking activity or without your knowledge, your PC may be infected by malware.
Article 2, Section 1, Clause 2 of the Criminal Code provides for a fine of up to 5500,000 and a deprivation of liberty of up to 6 years. In case this activity has been effected without your knowledge, you fall under the above mentioned Article 2, Section 1, Clause 1 of the Criminal Code of United States of America.
Your personality and address are currently being identified, a criminal case is going to be initiated against you under one or more articles specified above within the next 72 hours.
Pursuant to the amendment to the Criminal Code of United States of America of February 05, 2013, this law infringement (if it is not repeated – first time) may be considered as conditional in case you pay the fine to the State.
Fines may only be paid within 72 hours after the infringement. As soon as 72 hours elapse, the possibility to pay the fine expires, and a criminal case is initiated against you automatically within the next 72 hours! To unblock the computer you must pay the fine through MoneyPak of $300. When you pay the fine, your PC will get unlocked in 1 to 72 hours after the money is put into the State’s account.
Since your PC is unlocked, you will be given 7 days to correct all violations.
In case all violations are not corrected after 7 working days, your PC will be blocked again, and a criminal case will be initiated against you automatically under one or more articles specified above.
The ICSPA notification is a scam, and you should ignore any alert that this malicious software might generate.
Under no circumstance should you send any money via Ukash to these cyber criminals, as this could lead to identity theft,and if you have, you can request a refund from Ukash stating that the payment was due to a scam and a computer virus.
ICSPA – Virus Removal Instructions
STEP 1: Remove ICSPA lock screen from your computer
ICSPA Ukash Ransom has modified your Windows registry and added its malicious files to run at start-up, so whenever you’re trying to boot your computer it will launch instead its bogus notification.To remove these malicious changes, we can use any of the below methods :
Method 1: Start your computer in Safe Mode with Networking and scan for malware
Some variants of ICSPA virus will allow the users to start the infected computer in Safe Mode with Networking without displaying the bogus lock screen. In this first method, we will try to start the computer in Safe Mode with Networking and then scan for malware to remove the malicious files.
- Remove all floppy disks, CDs, and DVDs from your computer, and then restart your computer.
- Press and hold the F8 key as your computer restarts.Please keep in mind that you need to press the F8 key before the Windows start-up logo appears.
Note: With some computers, if you press and hold a key as the computer is booting you will get a stuck key message. If this occurs, instead of pressing and holding the “F8 key”, tap the “F8 key” continuously until you get the Advanced Boot Options screen. - On the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.
![Remove ICSPA lock-screen virus (Removal Guide) 5 [Image: Safe Mode with Networking]](//malwaretips.com/blogs/wp-content/uploads/2013/01/safemode.jpg)
- If your computer has started in Safe Mode with Networking, you’ll need to perform a system scan (as seen on STEP 2) with Malwarebytes Anti-Malware and HitmanPro to remove the malicious files from your machine.
IF the ICSPA virus didn’t allow you to start the computer in Safe Mode with Networking,you’ll need to follow Method 2 to get rid of its lock screen.
Method 2: Restore Windows to a previous state using System Restore
System Restore can return your computer system files and programs to a time when everything was working fine, so we will try to use this Windows feature to get rid of ICSPA lock screen.
- Restart your computer, and then press and hold F8 during the initial startup to start your computer in safe mode with a Command prompt.
Note: With some computers, if you press and hold a key as the computer is booting you will get a stuck key message. If this occurs, instead of pressing and holding the “F8 key”, tap the “F8 key” continuously until you get the Advanced Boot Options screen. - Use the arrow keys to select the Safe mode with a Command prompt option.
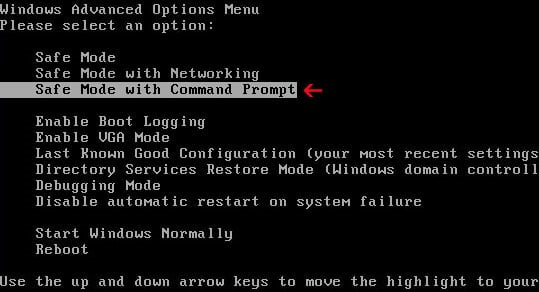
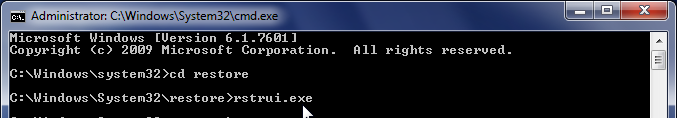
- At the command prompt, type cd restore, and then press ENTER.
Next,we will type rstrui.exe , and then press ENTER.
Alternatively, Windows Vista, 7 and 8 users, can just type : C:\windows\system32\rstrui.exe.
If you are using Windows XP, you will need to type C:\windows\system32\restore\rstrui.exe, and then press ENTER.
- The System Restore window will start and you’ll need to select a restore point previous to this infection.
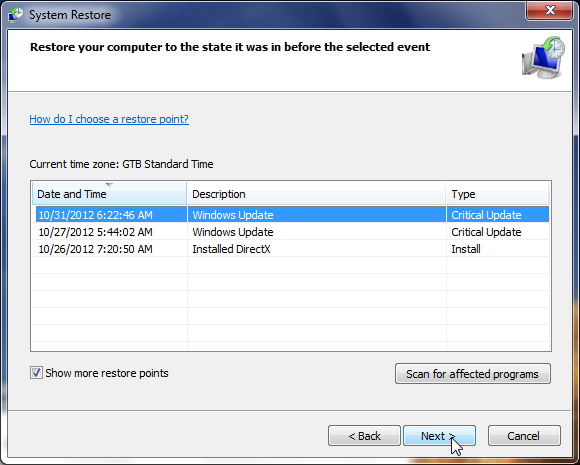
- After System Restore has completed its task,you should be able to boot in Windows normal mode,from there you’ll need to perform a system scan (as seen on STEP 2) with Malwarebytes Anti-Malware and HitmanPro to remove the malicious files from your machine.
IF the ICSPA virus didn’t allow you to start the computer in Safe Mode with Command Prompt you’ll need to follow Method 3, to get rid of its screen lock.
Method 3: Remove ICSPA virus with HitmanPro Kickstart
IF you couldn’t boot into Safe Mode with Command Prompt or didn’t have a System Restore point on your machine, we can use HitmanPro Kickstart to bypass this infection and access your computer to scan it for malware.
- We will need to create a HitmanPro Kickstart USB flash drive,so while you are using a “clean” (non-infected) computer, download HitmanPro from the below link.
HITMANPRO DOWNLOAD LINK (This link will open a download page in a new window from where you can download HitmanPro) - Insert your USB flash drive into your computer and follow the instructions from the below video:
- After you have create the HitmanPro Kickstart USB flash drive, you can insert this USB drive into the infected machine and start your computer.
- Once the computer starts, repeatedly tap the F11 key (on some machines its F10 or F2),which should bring up the Boot Menu, from there you can select to boot from your USB.
Next,you’ll need to perform a system scan with HitmanPro as see in the below video:
- After HitmanPro Kickstart has completed its task,you should be able to boot in Windows normal mode,from there you’ll need to perform a system scan (as seen on STEP 2) with Malwarebytes Anti-Malware and HitmanPro to remove the malicious files from your machine.
STEP 2: Remove ICSPA malicious files from your computer
No matter what method you have used to get rid of ICSPA lock screen, we will need to remove its malicious files from your computer.
Please download and run a scan with the following scan to completely remove ICSPA virus from your computer.
Run a computer scan with Malwarebytes Anti-Malware Free
- You can download Malwarebytes Anti-Malware Free from the below link,then double click on it to install this program.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK(This link will open a download page in a new window from where you can download Malwarebytes Anti-Malware Free) - When the installation begins, keep following the prompts in order to continue with the setup process.
DO NOT make any changes to default settings and when the program has finished installing, make sure you leave both the Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware checked,then click on the Finish button.
![Malwarebytes Anti-Malware final installation screen [Image: Malwarebytes Anti-Malware final installation screen]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
- On the Scanner tab,select Perform quick scan and then click on the Scan button to start scanning your computer.
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)
- Malwarebytes’ Anti-Malware will now start scanning your computer for ICSPA virus as shown below.
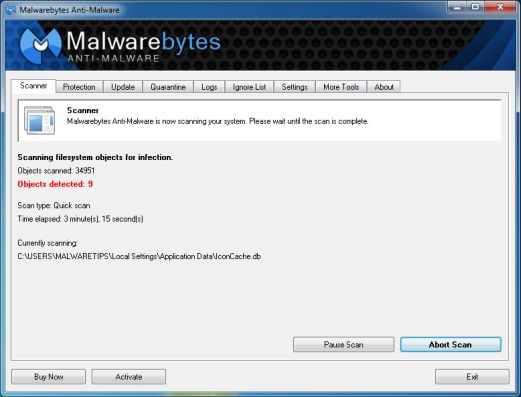
- When the Malwarebytes scan will be completed,click on Show Result.
![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
- You will now be presented with a screen showing you the malware infections that Malwarebytes’ Anti-Malware has detected.Please note that the infections found may be different than what is shown in the image.Make sure that everything is Checked (ticked) and click on the Remove Selected button.
![Click on Remove Selected to get rid of Your computer has been locked virus [Image:Malwarebytes removing virus]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)
- After your computer will restart in Normal mode, open Malwarebytes Anti-Malware and perform a Full System scan to verify that there are no remaining threats
Run a computer scan with HitmanPro
- Download HitmanPro from the below link,then double click on it to start this program.
HITMANPRO DOWNLOAD LINK (This link will open a new web page from where you can download HitmanPro)
IF you are experiencing problems while trying to start HitmanPro, you can use the Force Breach mode.To start HitmanPro in Force Breach mode, hold down the left CTRL-key when you start HitmanPro and all non-essential processes are terminated, including the malware process. (How to start HitmanPro in Force Breach mode – Video) - HitmanPro will start and you’ll need to follow the prompts (by clicking on the Next button) to start a system scan with this program.
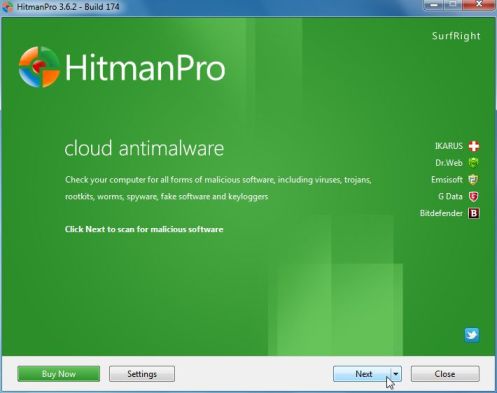
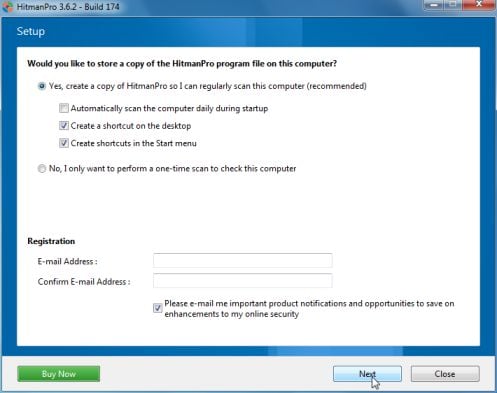
- HitmanPro will start scanning your computer for ICSPA malicious files as seen in the image below.
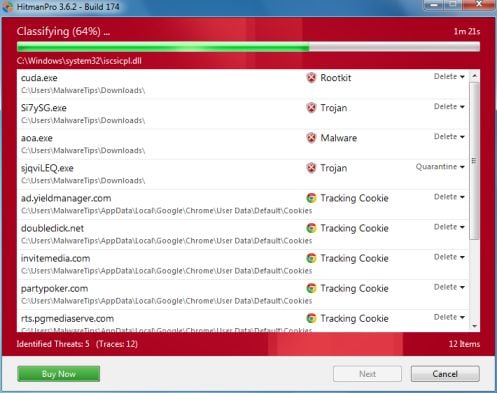
- Once the scan is complete,you’ll see a screen which will display all the infected files that this utility has detected, and you’ll need to click on Next to remove these malicious files.
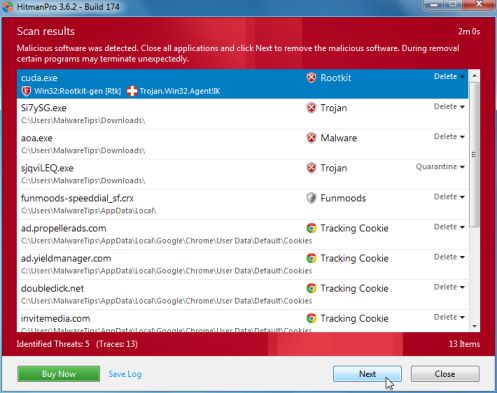
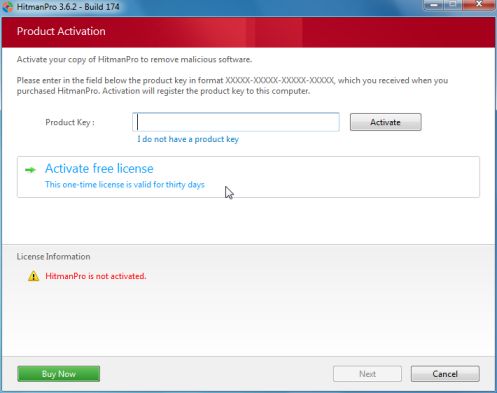
- Click Activate free license to start the free 30 days trial and remove all the malicious files from your computer.

![Remove ICSPA lock-screen virus (Removal Guide) 1 [Image: International Cyber Security Protection Alliance virus]](https://malwaretips.com/blogs/wp-content/uploads/2013/02/International-Cyber-Security-Protection-Alliance-virus.png)
![Remove ICSPA lock-screen virus (Removal Guide) 2 [Image: International Cyber Security Protection Alliance virus]](https://malwaretips.com/blogs/wp-content/uploads/2013/02/International-Cyber-Security-Protection-Alliance-virus-290x290.png)
![Remove ICSPA lock-screen virus (Removal Guide) 3 [Image: ICSPA virus]](https://malwaretips.com/blogs/wp-content/uploads/2013/02/ICSPA-virus-290x290.jpg)
![Remove ICSPA lock-screen virus (Removal Guide) 4 [Image: ICSPA Ukash virus]](https://malwaretips.com/blogs/wp-content/uploads/2013/02/ICPSA-Ukash-virus-290x290.jpg)
![Remove ICSPA lock-screen virus (Removal Guide) 5 [Image: Safe Mode with Networking]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/safemode.jpg)



![Malwarebytes Anti-Malware final installation screen [Image: Malwarebytes Anti-Malware final installation screen]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)

![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
![Click on Remove Selected to get rid of Your computer has been locked virus [Image:Malwarebytes removing virus]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)








