If your web browser is constantly being redirected to the Threatdetect.org site, then it is possible that you have adware installed on your computer.
What is Threatdetect.org?
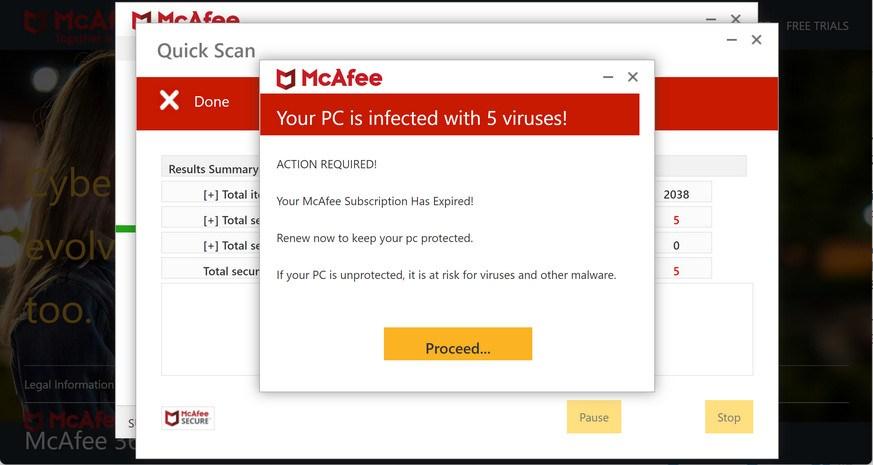
Threatdetect.org is a browser-based scam that tries to trick you into thinking that an antivirus (McAfee or Norton) quick scan has detected 5 viruses and you need to renew your antivirus subscription to remove them. It does this to scare you into buying an antivirus license so that the scammers can earn a commission from the sale.
When the Threatdetect.org scam is displayed in your browser it will show this message:
McAfee
Your PC is infected with 5 viruses!
ACTION REQUIRED!
Your Norton Subscription Has Expired!
Renew now to keep your pc protected.
If your PC is unprotected, it is at risk for viruses and other malware.
As you can imagine, the Threatdetect.org alerts are nothing more than fake error messages and anything it states is just a scam. If you have been redirected to the Threatdetect.org site, we recommend closing this page and do not enter any personal information.
Why am I seeing the Threatdetect.org pop-up ads?
You are seeing the Threatdetect.org pop-up ads because your device is infected with malware, malicious push notifications, or a site you have visited has redirected your browser.
Less than reputable sites can display malicious ads that redirect your browser to the Threatdetect.org pop-up ads to generate advertising revenue. If this happens, you can close the page and install an ad blocker like AdGuard to block the malicious ads. However, if you are continuously seeing pop-ups like the Threatdetect.org pop-up ads, then your computer might be infected with a malicious program and you need to scan your device for adware and remove it.
Here are a few typical signs that you have a malicious program installed on your computer:
- Advertisements appear in places they shouldn’t be.
- Your web browser’s homepage has mysteriously changed without your permission.
- Web pages that you typically visit are not displaying properly.
- Website links redirect to sites different from what you expected.
- Browser popups appear which recommend fake updates or other software.
- Other unwanted programs might get installed without your knowledge.
To check your computer for the Threatdetect.org pop-up ads and remove them for free, please use the guide below.
Remove Threatdetect.org pop-up ads (Virus Removal Guide)
This malware removal guide may appear overwhelming due to the number of steps and numerous programs that are being used. We have only written it this way to provide clear, detailed, and easy-to-understand instructions that anyone can use to remove malware for free.
Please perform all the steps in the correct order. If you have any questions or doubts at any point, stop and ask for our assistance.
The Threatdetect.org browser redirect can happen on Windows, Mac, or Android, so we’ve covered below all these operating systems. Depending on which operating system is installed on the device you’re seeing the Threatdetect.org pop-up ads, follow the removal guide.
 Remove Threatdetect.org from Windows
Remove Threatdetect.org from Windows-
 Remove Threatdetect.org from Mac
Remove Threatdetect.org from Mac  Remove Threatdetect.org from Android
Remove Threatdetect.org from Android
- STEP 1: Use Malwarebytes to remove Threatdetect.org browser hijacker
- STEP 2: Use HitmanPro to scan your computer for Threatdetect.org and other malware
- STEP 3: Use AdwCleaner to remove malicious browser policies
- STEP 4: Remove malicious browser extensions
STEP 1: Use Malwarebytes to remove Threatdetect.org browser hijacker
In this first step, we will install Malwarebytes to scan and remove the Threatdetect.org malicious files and registry key from your computer.
Malwarebytes is one of the most popular and most used anti-malware software for Windows, and for good reasons. It is able to destroy many types of malware that other software tends to miss, without costing you absolutely nothing. When it comes to cleaning up an infected device, Malwarebytes has always been free and we recommend it as an essential tool in the fight against malware.
Download Malwarebytes for Windows.
You can download Malwarebytes by clicking the link below.
 MALWAREBYTES FOR WINDOWS DOWNLOAD LINK
MALWAREBYTES FOR WINDOWS DOWNLOAD LINK
(The above link will open a new page from where you can download Malwarebytes)Double-click on the Malwarebytes setup file.
When Malwarebytes has finished downloading, double-click on the MBSetup file to install Malwarebytes on your computer. In most cases, downloaded files are saved to the Downloads folder.
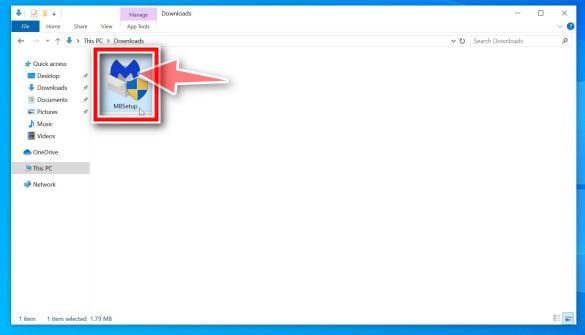
You may be presented with an User Account Control pop-up asking if you want to allow Malwarebytes to make changes to your device. If this happens, you should click “Yes” to continue with the Malwarebytes installation.
Follow the on-screen prompts to install Malwarebytes.
When the Malwarebytes installation begins, you will see the Malwarebytes setup wizard which will guide you through the installation process. The Malwarebytes installer will first ask you on what type of computer are you installing this program, click either Personal Computer or Work Computer.
On the next screen, click “Install” to install Malwarebytes on your computer.
When your Malwarebytes installation completes, the program opens to the Welcome to Malwarebytes screen. Click the “Get started” button.
Click on “Scan”.
To scan your computer with Malwarebytes, click on the “Scan” button. Malwarebytes will automatically update the antivirus database and start scanning your computer for Threatdetect.org browser hijacker and other malicious programs.
Wait for the Malwarebytes scan to complete.
Malwarebytes will scan your computer for Threatdetect.org browser hijacker and other malicious programs. This process can take a few minutes, so we suggest you do something else and periodically check on the status of the scan to see when it is finished.
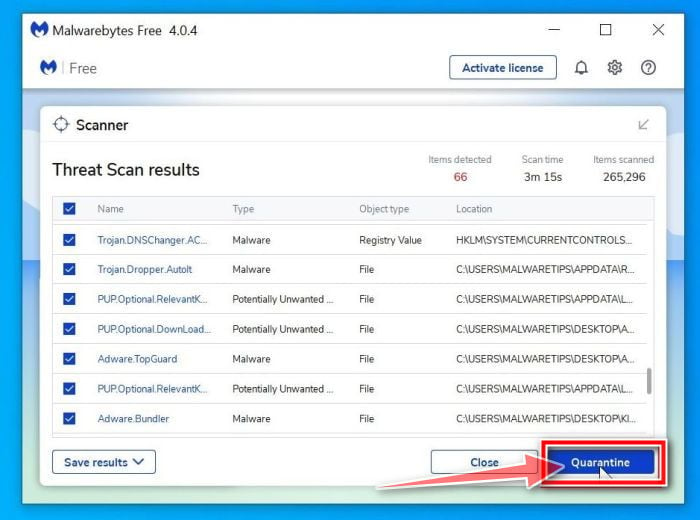
Click on “Quarantine”.
When the scan has completed, you will be presented with a screen showing the malware infections that Malwarebytes has detected. To remove the Threatdetect.org extension and other malicious programs that Malwarebytes has found, click on the “Quarantine” button.
Restart computer.
Malwarebytes will now remove all the malicious files and registry keys that it has found. To complete the malware removal process, Malwarebytes may ask you to restart your computer.
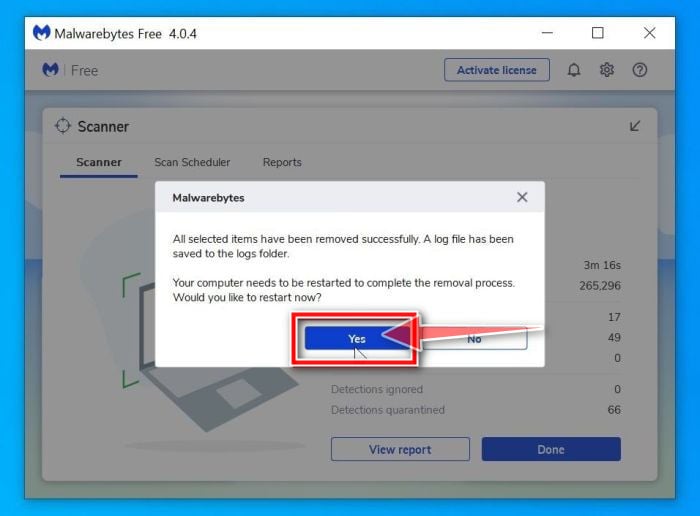
When the malware removal process is complete, you can close Malwarebytes and continue with the rest of the instructions.
STEP 2: Use HitmanPro to scan your computer for Threatdetect.org and other malware
In this next step, we will scan the computer with HitmanPro to ensure that no other malicious programs are installed on your device.
HitmanPro is a second opinion scanner that takes a unique cloud-based approach to malware scanning. HitmanPro scans the behavior of active files and also files in locations where malware normally resides for suspicious activity. If it finds a suspicious file that’s not already known, HitmanPro sends it to its clouds to be scanned by two of the best antivirus engines today, which are Bitdefender and Kaspersky.
Although HitmanPro is shareware and costs $24.95 for 1 year on 1 PC, there is actually no limit in scanning. The limitation only kicks in when there is a need to remove or quarantine detected malware by HitmanPro on your system and by then, you can activate the one time 30-days trial to enable the cleanup.
Download HitmanPro.
You can download HitmanPro by clicking the link below.
 HITMANPRO DOWNLOAD LINK
HITMANPRO DOWNLOAD LINK
(The above link will open a new web page from where you can download HitmanPro)Install HitmanPro.
When HitmanPro has finished downloading, double-click on “hitmanpro.exe” (for 32-bit versions of Windows) or “hitmanpro_x64.exe” (for 64-bit versions of Windows) to install this program on your PC. In most cases, downloaded files are saved to the Downloads folder.
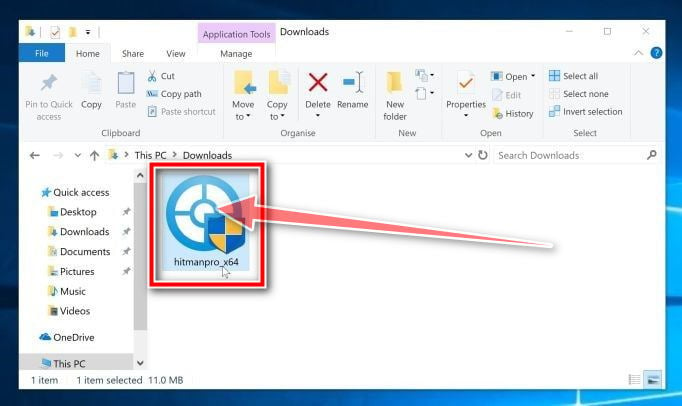
You may be presented with an User Account Control pop-up asking if you want to allow HitmanPro to make changes to your device. If this happens, you should click “Yes” to continue with the installation.
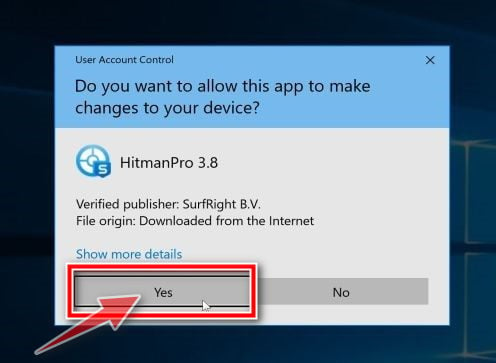
Follow the on-screen prompts.
When HitmanPro starts you will be presented with the start screen as shown below. Click on the “Next” button to perform a system scan.
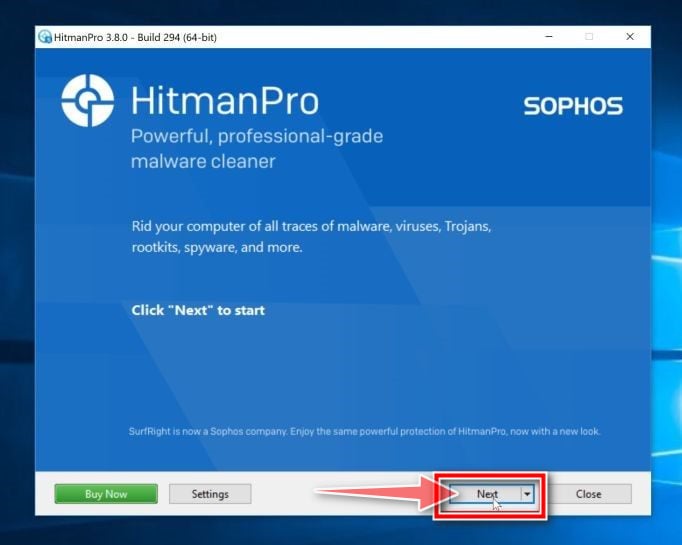
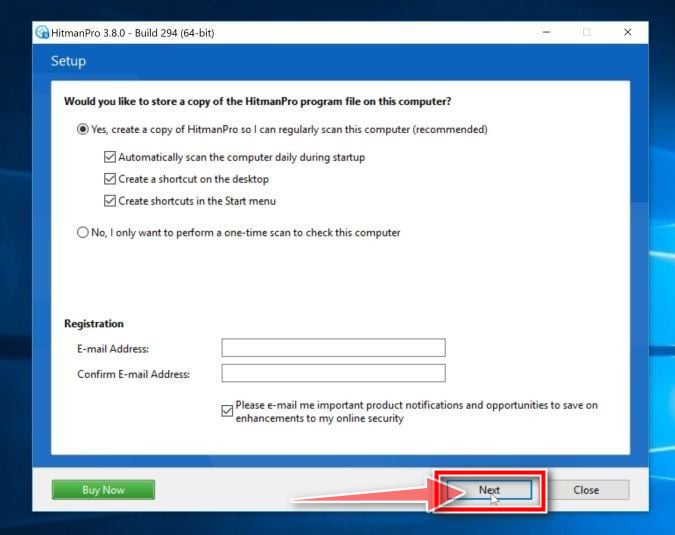
Wait for the HitmanPro scan to complete.
HitmanPro will now begin to scan your computer for Threatdetect.org browser hijacker and other malicious programs.
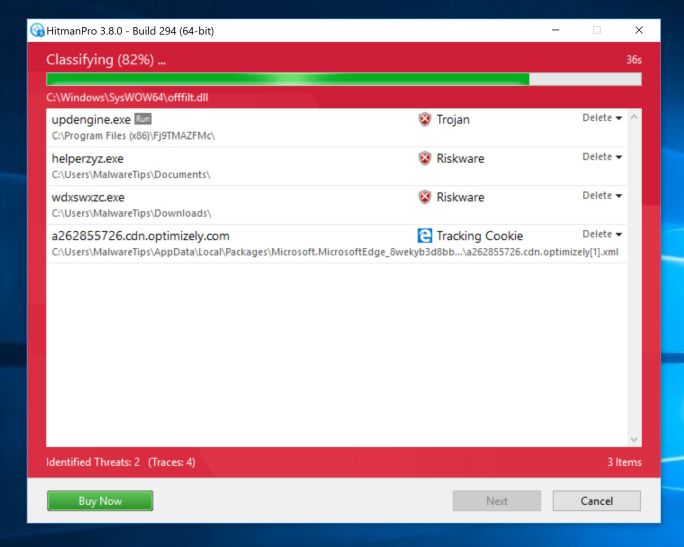
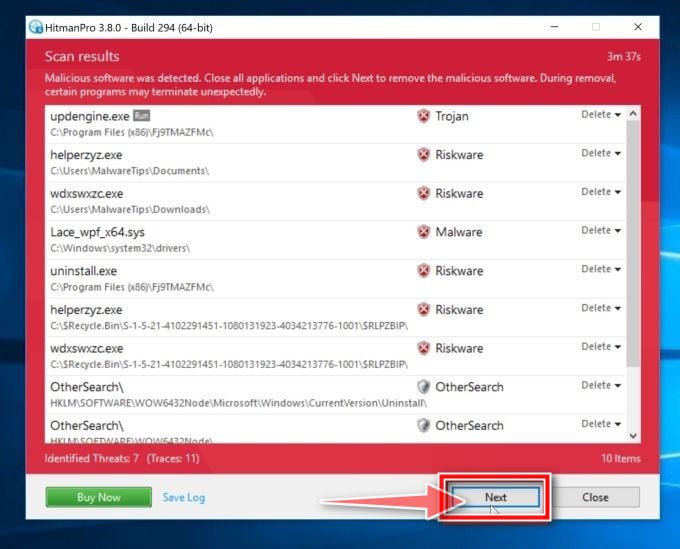
Click on “Next”.
When HitmanPro has finished the scan, it will display a list of all the malware that the program has found. Click on the “Next” button to remove Threatdetect.org adware and other malicious programs.
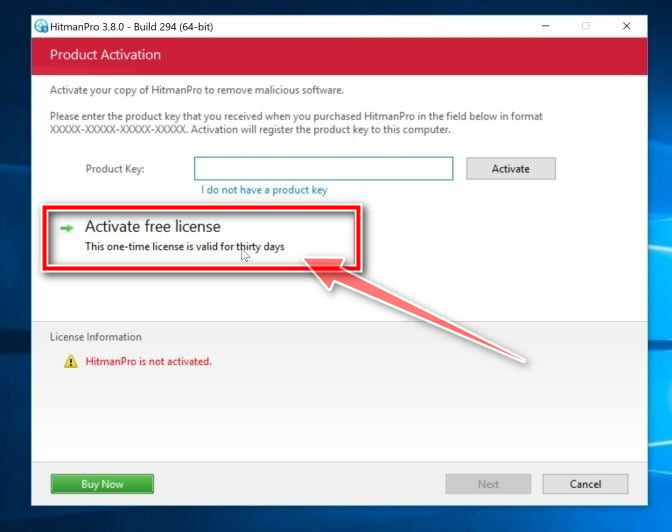
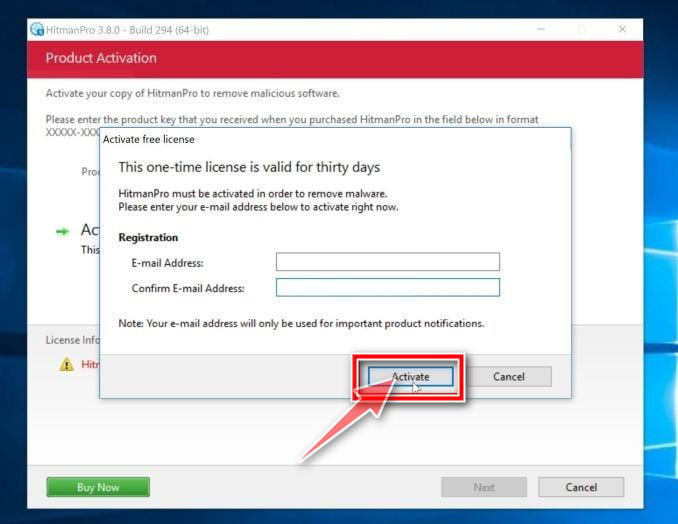
Click on “Activate free license”.
Click on the “Activate free license” button to begin the free 30 days trial and remove all the malicious files from your PC.
STEP 3: Use AdwCleaner to remove malicious browser policies
In this third step, we will use AdwCleaner to remove the malicious browser policies that were set by browser hijackers on your computer and delete malicious browser extensions.
AdwCleaner is a free popular on-demand scanner that can detect and remove malware that even the most well-known anti-virus and anti-malware applications fail to find. This on-demand scanner includes a lot of tools that can be used to fix the side effects of browser hijackers.
Download AdwCleaner.
You can download AdwCleaner by clicking the link below.
 ADWCLEANER DOWNLOAD LINK
ADWCLEANER DOWNLOAD LINK
(The above link will open a new web page from where you can download AdwCleaner)Double-click on the setup file.
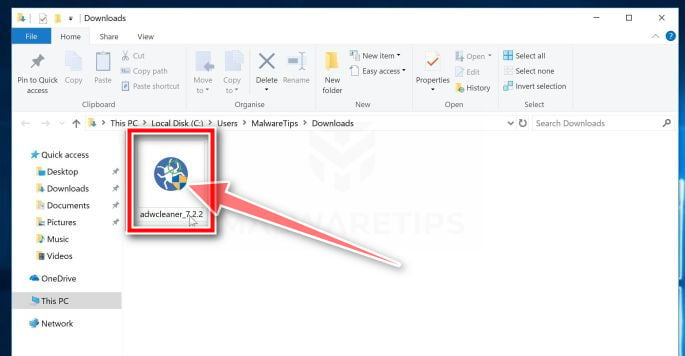
Double-click on the file named “adwcleaner_x.x.x.exe” to start AdwCleaner. In most cases, downloaded files are saved to the Downloads folder.
You may be presented with a User Account Control dialog asking you if you want to run this file. If this happens, you should click “Yes” to continue with the installation.
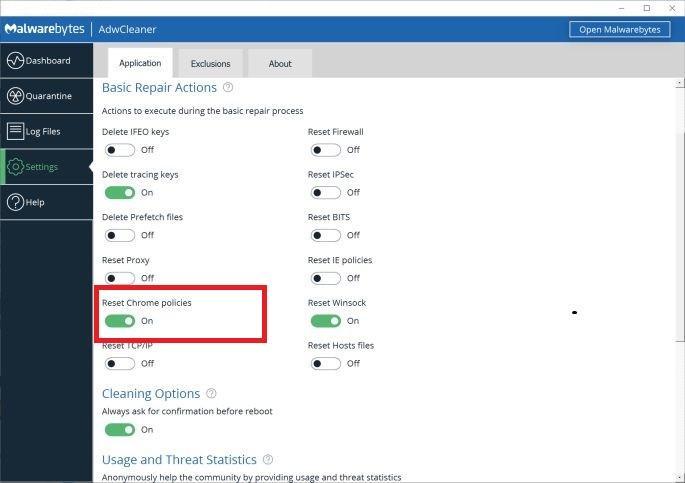
Enable “Reset Chrome policies” to remove Threatdetect.org browser policies.
When AdwCleaner starts, on the left side of the window, click on “Settings” and then enable “Reset Chrome policies“.
Click on “Scan Now”.
On the left side of the window, click on “Dashboard” and then click “Scan Now” to perform a system scan.
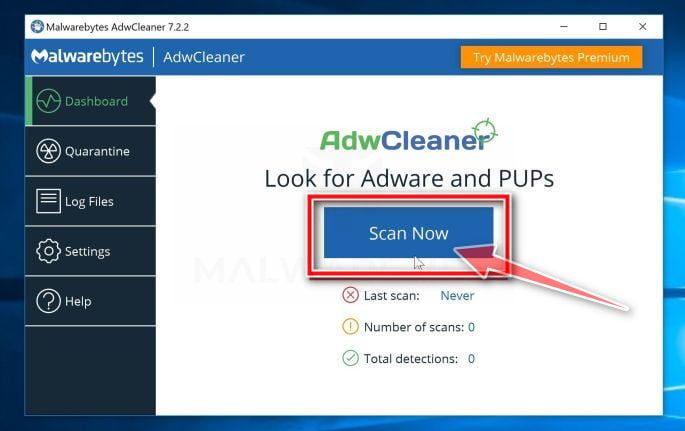
Wait for the AdwCleaner scan to complete.
AdwCleaner will now scan your computer for the Threatdetect.org browser hijacker and other malicious programs. This process can take a few minutes.
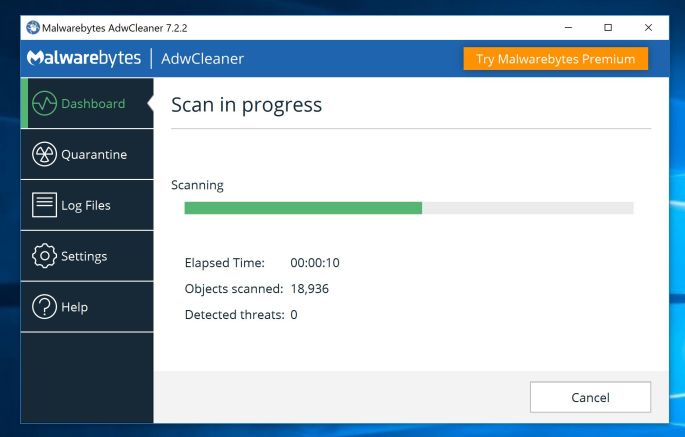
Click on “Clean & Repair”.
When AdwCleaner has finished it will display a list of all the malware that the program found. Click on the “Clean & Repair” button to remove the Threatdetect.org browser hijacker and other malicious programs from your computer.
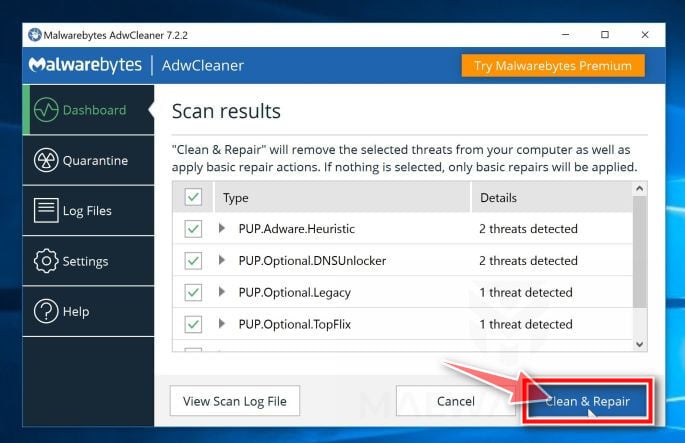
Click on “Clean & Restart Now”
When the malware removal process is complete, AdwCleaner may need to restart your device. Click on the “Clean & Restart Now” button to finish the removal process.
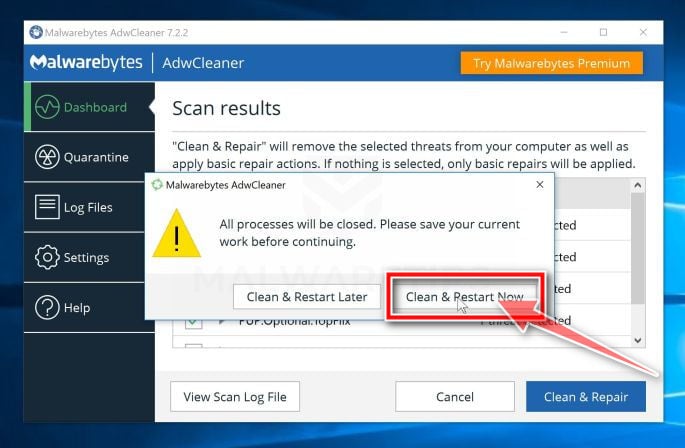
When the malware removal process is complete, you can close AdwCleaner and continue with the rest of the next step from this guide.
STEP 4: Remove malicious browser extension
In this final step, we will remove any malicious extensions from your browser and change to default any settings that might have been changed by malware.
Remove Threatdetect.org browser hijacker from Google Chrome
To remove Threatdetect.org from Google Chrome, we will remove the browser extension and then check the settings.
Remove malicious browser extension.
In the top right corner, click on Chrome’s main menu button, represented by three vertical dots. When the drop-down menu appears, click on “More tools“, then click on “Extensions“.
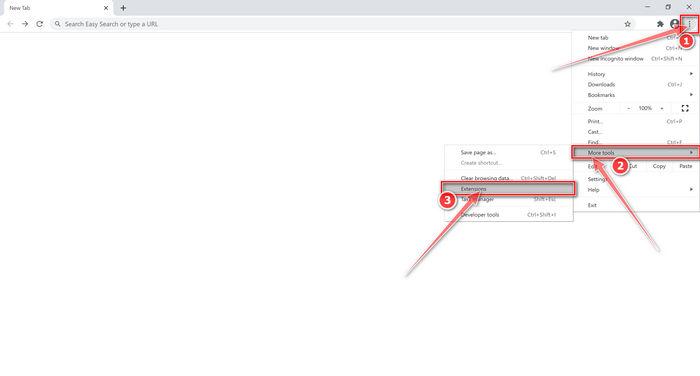
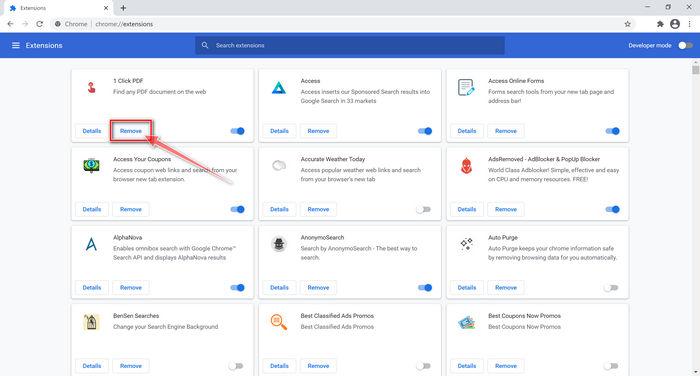
The “Extensions” screen will be displayed with a list of all the extensions installed on Chrome. Scroll through the list and search for unknown browser extensions, and then click on “Remove” to remove them.
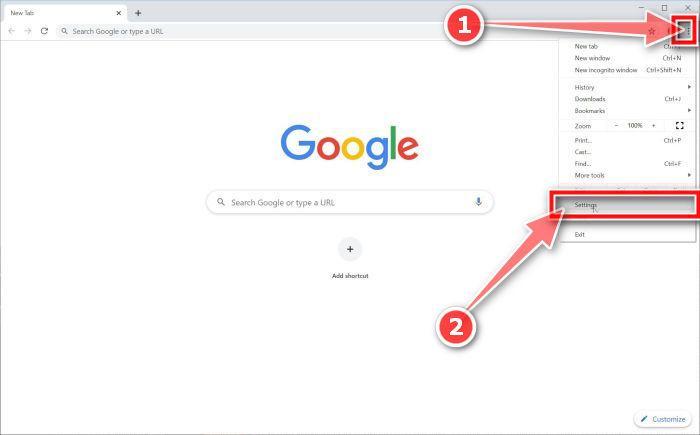
Change the search engine to Google.
In the top right corner, click on Chrome’s main menu button, represented by three vertical dots. When the drop-down menu appears, click on “Settings“.
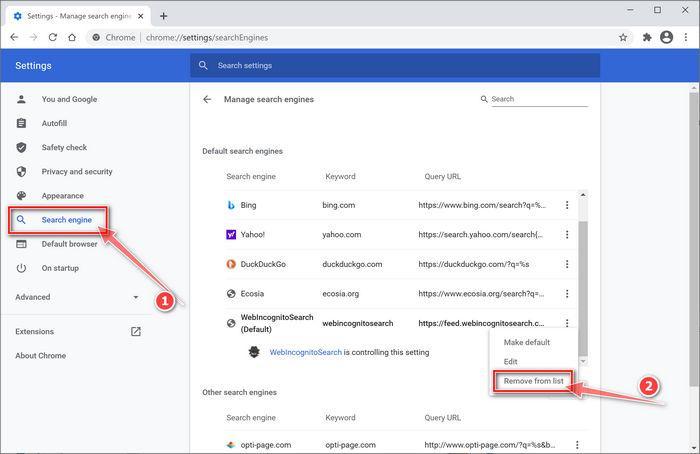
On the left side of the window, click on “Search engine“, then click “Manage search engines…“. In the opened list, find Google Search, click the three vertical dots and select “Make default“.”.
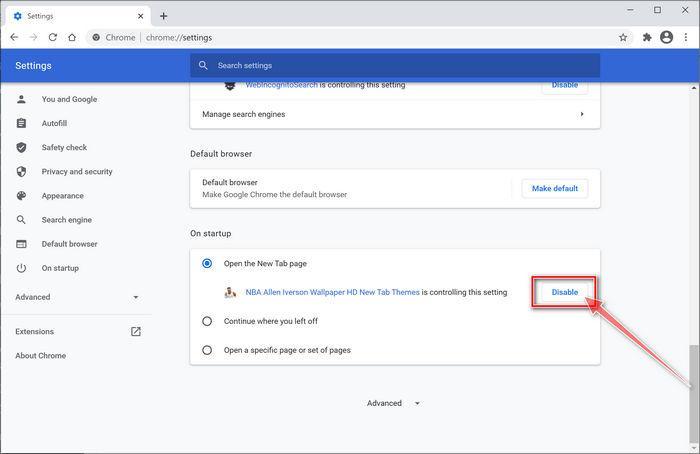
Check the homepage and new tab settings.
In the top right corner, click on Chrome’s main menu button, represented by three vertical dots. When the drop-down menu appears, click on “Settings“.

In the “On startup” section, disable any unkwnon extension, then select “Open the New Tab page” as your preferred setting.
Remove Threatdetect.org browser hijacker from Firefox
To remove the Threatdetect.org redirect from Firefox we will reset the browser settings to its default. The reset feature fixes many issues by restoring Firefox to its factory default state while saving your essential information like bookmarks, passwords, web form auto-fill information, browsing history, and open tabs.
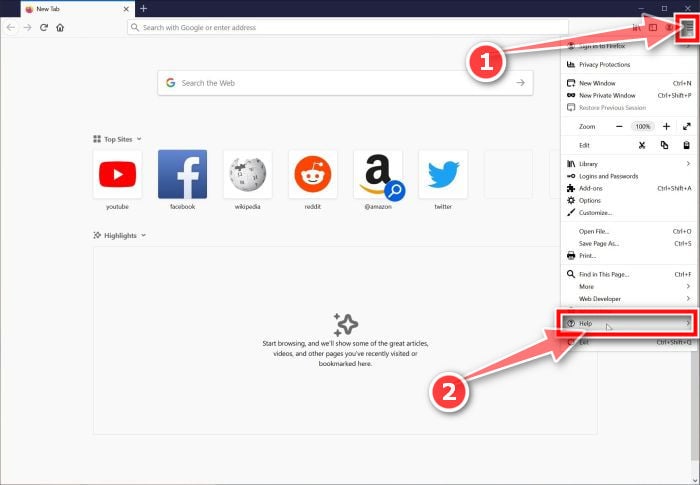
Click the menu icon, then click on “Help”.
Click on Firefox’s main menu button, represented by three horizontal lines. When the drop-down menu appears, select the option labeled “Help“.
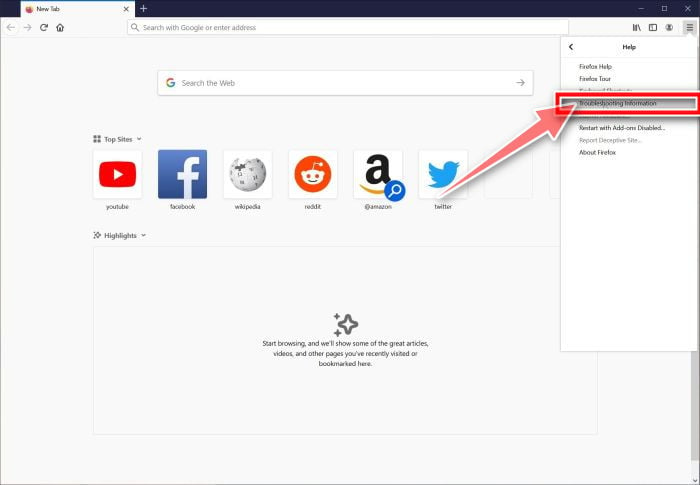
Click “Troubleshooting Information”.
From the Help menu, click on “Troubleshooting Information“.
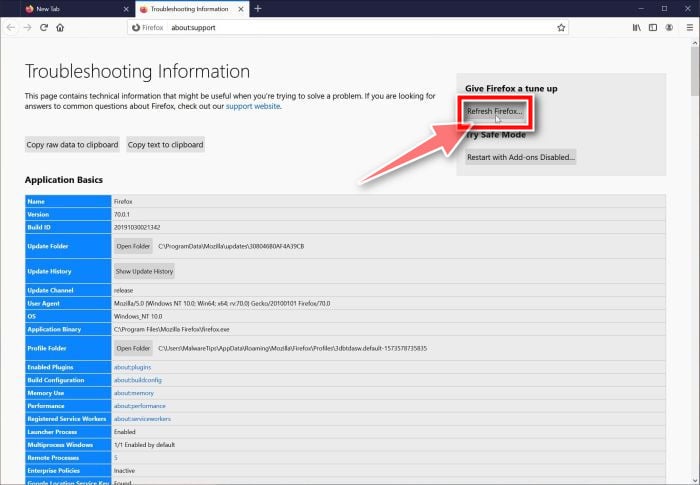
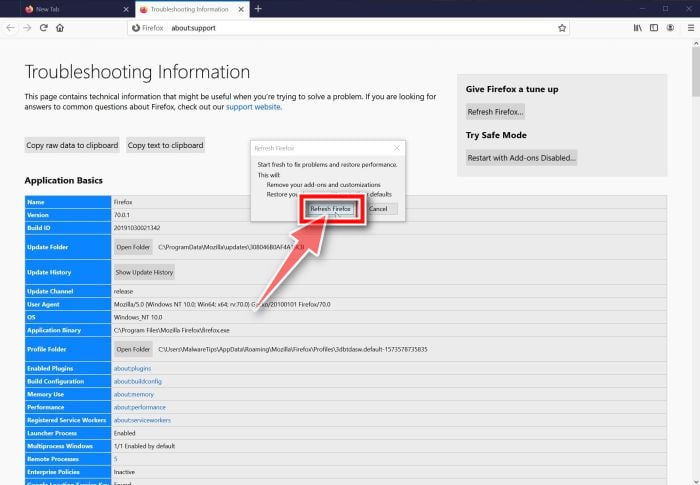
Click on “Refresh Firefox”
Click the “Refresh Firefox” button in the upper-right corner of the “Troubleshooting Information” page.
Confirm.
To continue, click on the “Refresh Firefox” button in the new confirmation window that opens.
Click “Finish”.
Firefox will close itself and will revert to its default settings. When it’s done, a window will list the information that was imported. Click on “Finish“.
Your old Firefox profile will be placed on your desktop in a folder named “Old Firefox Data“. If the reset didn’t fix your problem you can restore some of the information not saved by copying files to the new profile that was created. If you don’t need this folder any longer, you should delete it as it contains sensitive information.
Remove Threatdetect.org browser hijacker from Microsoft Edge
To remove the Threatdetect.org redirect from Microsoft Edge we will reset the browser settings to its default. This will reset your startup page, new tab page, search engine, and pinned tabs. It will also disable all extensions and clear temporary data like cookies. Your favorites, history and saved passwords will not be cleared.
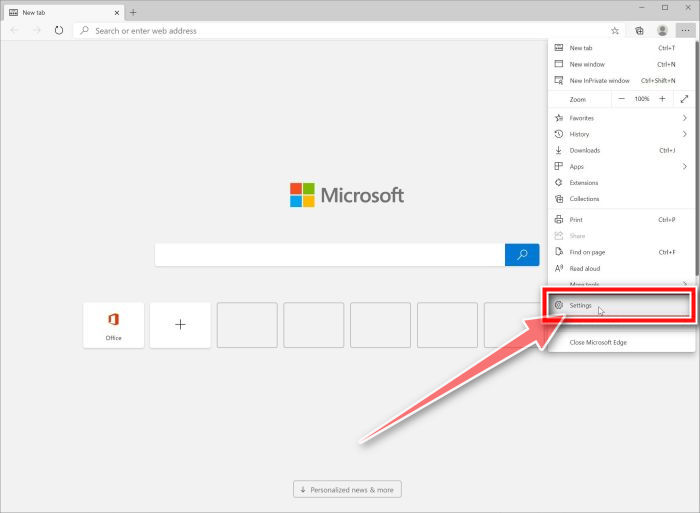
Open the “Settings” menu.
In the top right corner, click on Microsoft Edge’s main menu button, represented by three horizontal dots. When the drop-down menu appears, click on “Settings“.”.
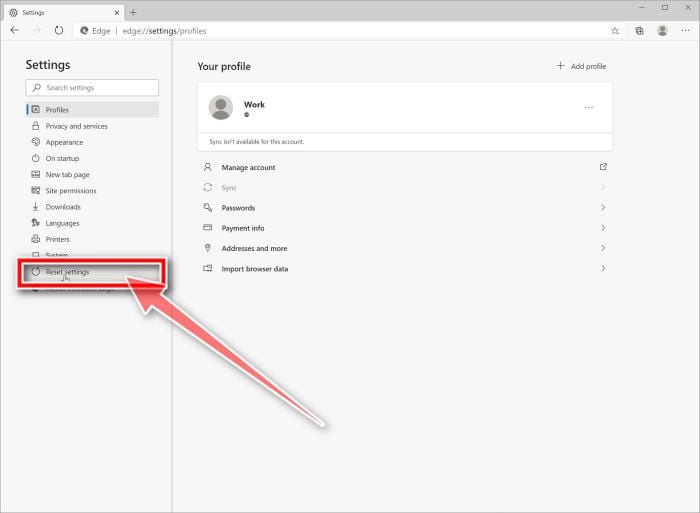
Click on “Reset Settings”.
On the left side of the window, click on “Reset Settings”.
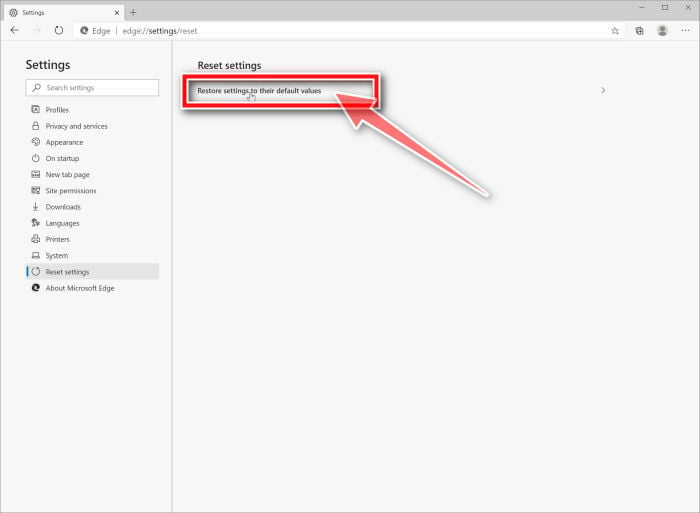
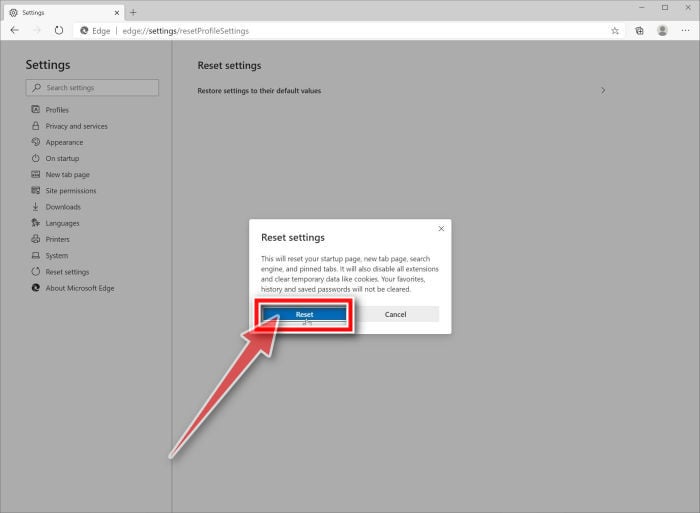
Click on “Restore settings to their default values”.
In the main window, click on “Restore settings to their default values”.
Click “Reset”.
A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue on with the reset process. To complete the restoration process, click on the “Reset” button.
Remove Threatdetect.org browser hijacker from Internet Explorer
To remove the Threatdetect.org redirect from Internet Explorer we will reset the browser settings to its default. You can reset Internet Explorer settings to return them to the state they were in when Internet Explorer was first installed on your computer.
Go to “Internet Options”.
Open Internet Explorer, click on the gear icon in the upper right part of your browser, then select “Internet Options“.
Select the “Advanced” tab, then click “Reset”
In the “Internet Options” dialog box, select the “Advanced” tab, then click on the “Reset” button.
Click on “Reset”.
In the “Reset Internet Explorer settings” section, select the “Delete personal settings” checkbox, then click on the “Reset” button.
Click on “Close”.
When Internet Explorer has completed its task, click on the “Close” button in the confirmation dialogue box.
Close your browser and then you can open Internet Explorer again.
Your computer should now be free of the Threatdetect.org browser hijacker. If your current antivirus allowed this malicious program on your computer, you may want to consider purchasing Malwarebytes Premium to protect against these types of threats in the future.
If you are still having problems with your computer after completing these instructions, then please follow one of the steps:
- Run a computer scan with ESET Online Scanner
- Ask for help in our Windows Malware Removal Help & Support forum.
- STEP 1: Remove malicious Profiles from your Mac
- STEP 2: Remove the malicious programs from Mac
- STEP 3: Use Malwarebytes for Mac to remove Threatdetect.org browser hijacker
- STEP 4: Remove Threatdetect.org redirect from Safari, Chrome, or Firefox
STEP 1: Remove malicious Profiles from your Mac
Profiles are used by IT admins in businesses to control the behavior of their Macs. These profiles can configure a Mac to do many different things, some of which are not otherwise possible.
When it comes to home users, adware and browser hijackers are using the configuration profile to prevent users from removing malicious programs from the computer. This also prevents the user from changing that behavior in the browser’s settings.
In this first step, we will check your computer to see if any configuration profiles are installed. To do this, follow the below steps:
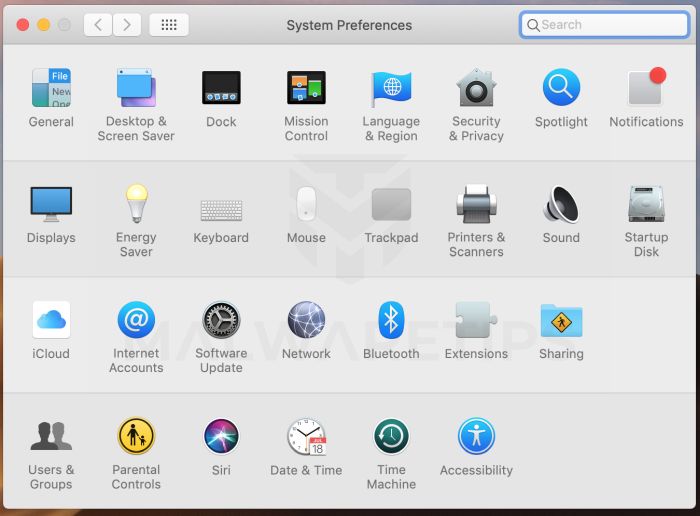
Open “System Preferences”
From the Apple menu, select System Preferences.
Search for “Profiles”
When the System Preferences window opens, search for the Profiles icon.
 If there isn’t a Profiles icon, you don’t have any profiles installed, which is normal and you can continue with the next steps.
If there isn’t a Profiles icon, you don’t have any profiles installed, which is normal and you can continue with the next steps.Remove the malicious profiles
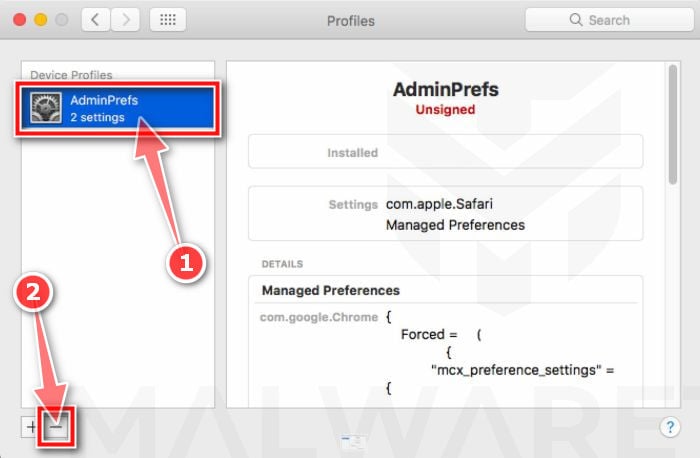
If there’s a Profile icon, click on it and select any suspicious profile that you want to remove, and then press the – (minus) button. Click Remove to remove the profile.
STEP 2: Remove the malicious programs from Mac
In this second step, we will try to identify and remove any malicious apps and files that might be installed on your computer. Sometimes redirects or adware programs can have usable Uninstall entries that can be used to remove these programs.
Quit the malicious programs
On the Apple menu bar, in the top-right corner, if you see any unknown or suspicious icon, click on it and then select Quit.
Open “Finder”
Click the Finder application on your dock.
Click on “Applications”
In the Finder left pane, click on “Applications“.
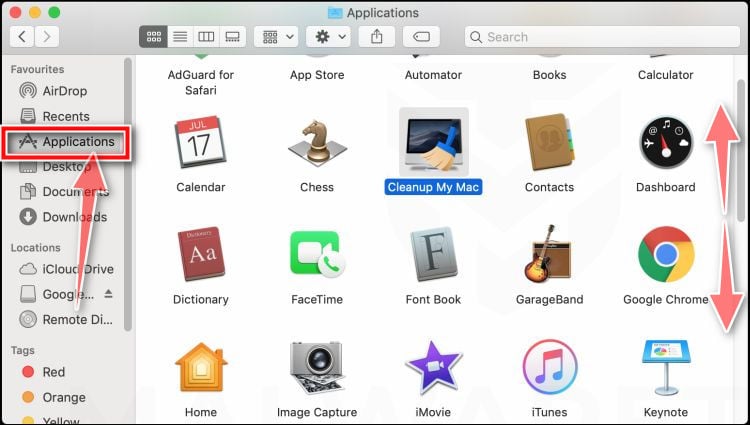
Find and remove the malicious app.
The “Applications” screen will be displayed with a list of all the apps installed on your device. Scroll through the list until you find the malicious app, right-click it, and then click “Move to Trash”.
Look out for any suspicious program that could be behind all the drama – anything you don’t remember downloading or that doesn’t sound like a genuine program. Here are some known malicious programs: SearchMine, TakeFresh, TopResults, FeedBack, ApplicationEvents, GeneralOpen, PowerLog, MessengerNow, ImagePrime, GeneralNetSearch, Reading Cursors, GlobalTechSearch, PDFOnline-express, See Scenic Elf, MatchKnowledge, Easy Speedtest, or WebDiscover.
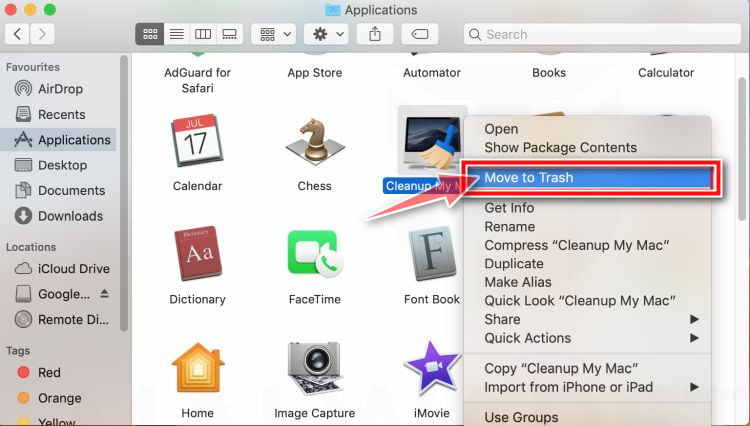
Click “Empty Trash”
On the dock, right-click on the trash icon and select “Empty Trash”. Doing so deletes the Trash’s contents, including the program that you just sent to the Trash.
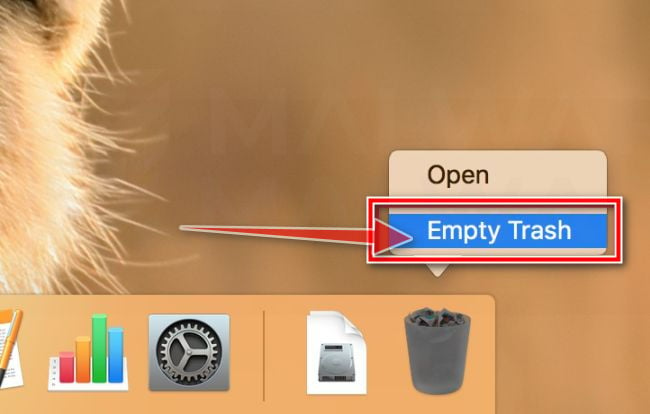
Find and remove the malicious files
- Click the desktop to make sure you’re in the Finder, choose “Go” then click on “Go to Folder“.
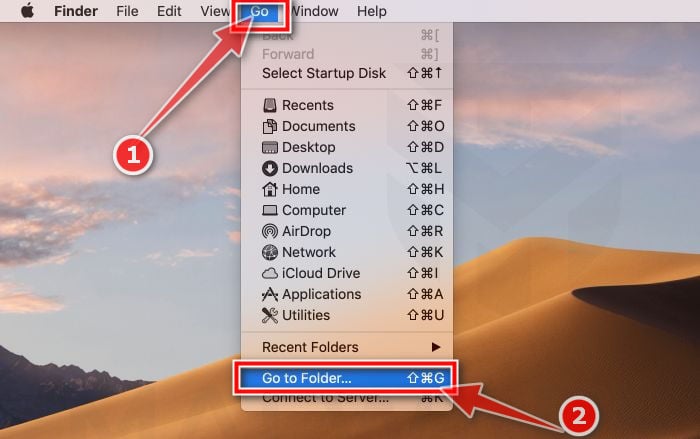
- Type or copy/paste each of the below paths into the window that opens, then click Go.
- /Library/LaunchAgents
- ~/Library/LaunchAgents
- /Library/Application Support
- /Library/LaunchDaemons
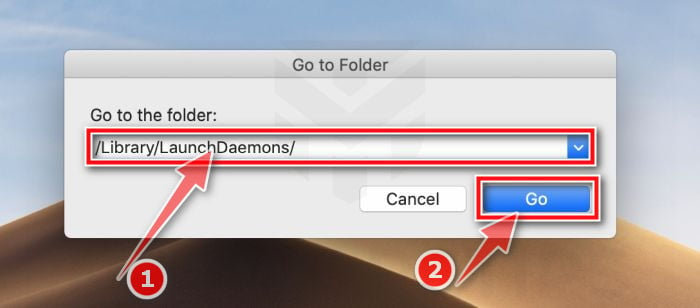
- Look out for any suspicious files that could be behind all the drama – anything you don’t remember downloading or that doesn’t sound like a genuine program. Here are some known malicious files: Here are some known malicious files: “com.adobe.fpsaud.plist” “installmac.AppRemoval.plist”, “myppes.download.plist”, “mykotlerino.ltvbit.plist”, or “com.myppes.net-preferences.plist”. When you find a malicious file move it to the Trash.
- Click the desktop to make sure you’re in the Finder, choose “Go” then click on “Go to Folder“.
STEP 3: Use Malwarebytes for Mac to remove Threatdetect.org browser hijacker
In this third step, we will scan the computer with Malwarebytes for Mac to find and remove any malicious programs that might be installed on your Mac.
Malwarebytes for Mac is an on-demand scanner that can destroy many types of malware that other software tends to miss without costing you absolutely nothing. When it comes to cleaning up an infected device, Malwarebytes has always been free, and we recommend it as an essential tool in the fight against malware.
Download Malwarebytes for Mac.
You can download Malwarebytes for Mac by clicking the link below.
 MALWAREBYTES FOR MAC DOWNLOAD LINK
MALWAREBYTES FOR MAC DOWNLOAD LINK
(The above link will open a new page from where you can download Malwarebytes for Mac)Double-click on the Malwarebytes setup file.
When Malwarebytes has finished downloading, double-click on the setup file to install Malwarebytes on your computer. In most cases, downloaded files are saved to the Downloads folder.
Follow the on-screen prompts to install Malwarebytes.
When the Malwarebytes installation begins, you will see the Malwarebytes for Mac Installer which will guide you through the installation process. Click “Continue“, then keep following the prompts in order to continue with the installation process.
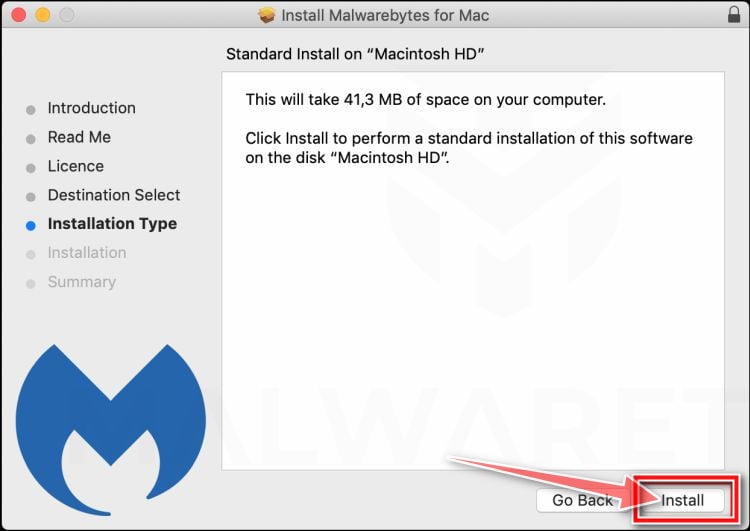
When your Malwarebytes installation completes, the program opens to the Welcome to Malwarebytes screen. Click the “Get started” button.
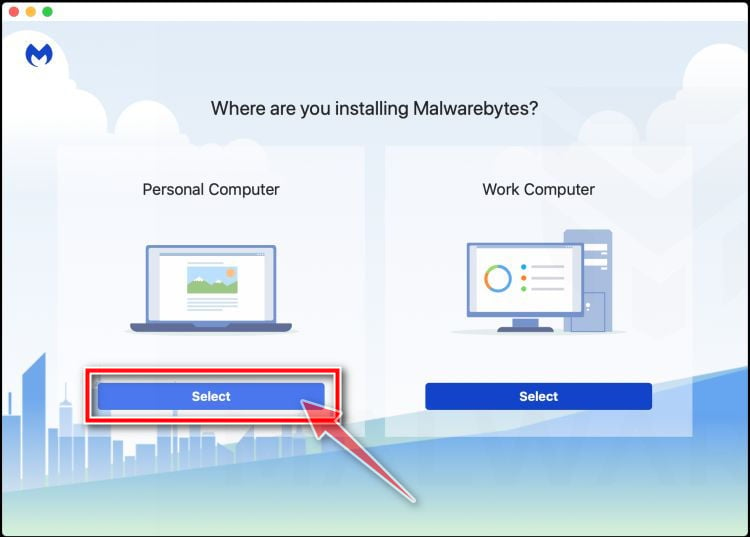
Select “Personal Computer” or “Work Computer”.
The Malwarebytes Welcome screen will first ask you on what type of computer are you installing this program, click either Personal Computer or Work Computer.
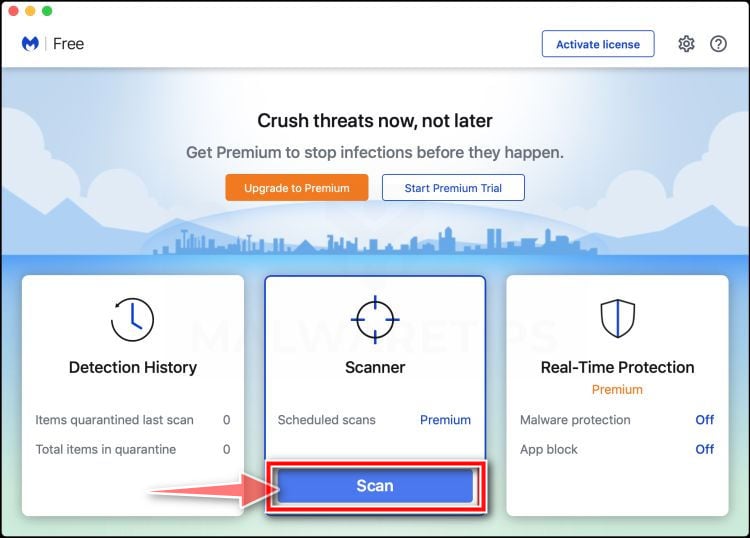
Click on “Scan”.
To scan your computer with Malwarebytes, click on the “Scan” button. Malwarebytes for Mac will automatically update the antivirus database and start scanning your computer for Threatdetect.org malware.
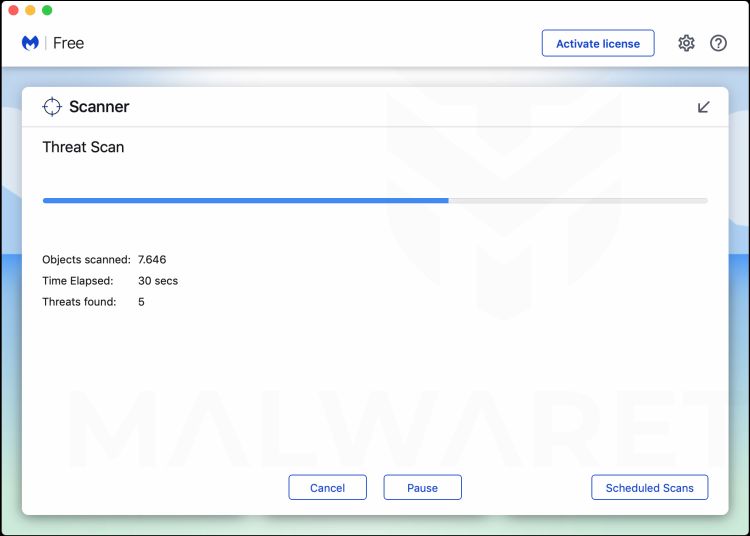
Wait for the Malwarebytes scan to complete.
Malwarebytes will scan your computer for the Threatdetect.org browser hijacker and other malicious programs. This process can take a few minutes, so we suggest you do something else and periodically check on the status of the scan to see when it is finished.
Click on “Quarantine”.
When the scan has completed, you will be presented with a screen showing the malware infections that Malwarebytes has detected. To remove the Threatdetect.org malware that Malwarebytes has found, click on the “Quarantine” button.
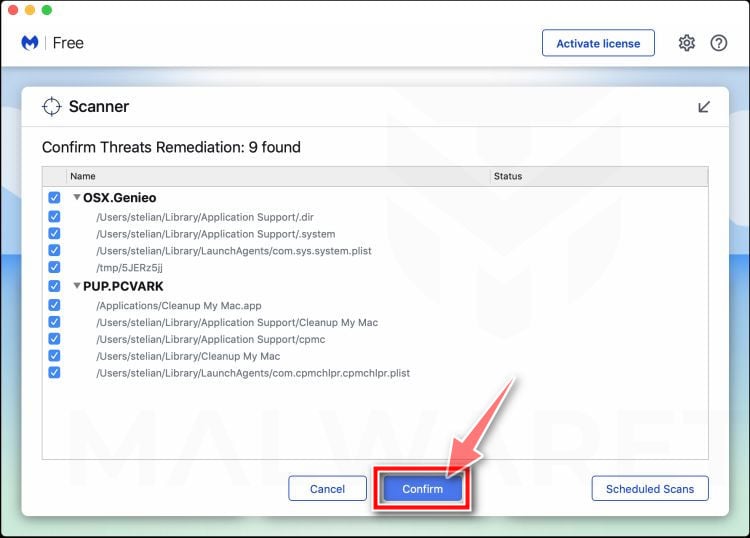
Restart computer.
Malwarebytes will now remove all the malicious files that it has found. To complete the malware removal process, Malwarebytes may ask you to restart your computer.
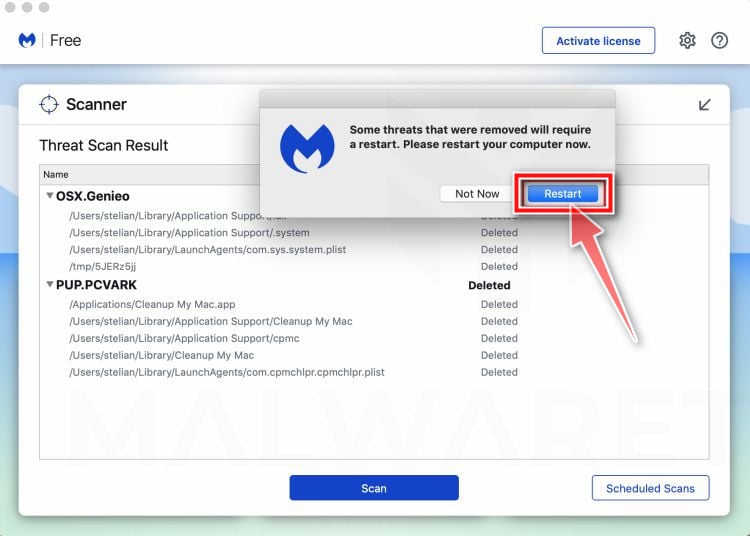
When the malware removal process is complete, you can close Malwarebytes and continue with the rest of the instructions.
STEP 4: Remove Threatdetect.org from Safari, Chrome, or Firefox
If you are still having problems with the Threatdetect.org adware browser extension, then you should also reset your browsers back to their default configuration
For each browser that you have installed on your computer, please click on the tab below and follow the displayed steps to reset that browser.
Remove Threatdetect.org browser hijacker from Safari
To remove Threatdetect.org browser hijacker from Safari we will check if there are any malicious extensions installed on your browser and what settings have been changed by this malicious program.
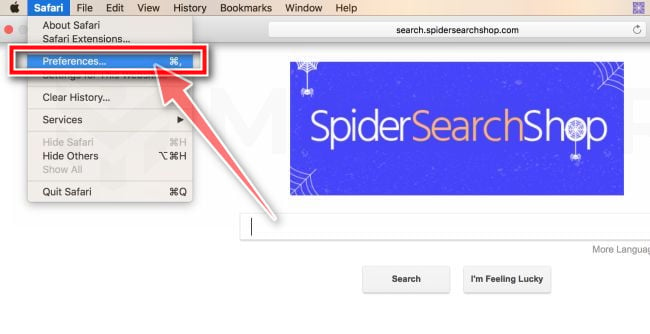
Go to Safari’s “Preferences”.
On the menu bar, click the “Safari” menu and select “Preferences”.
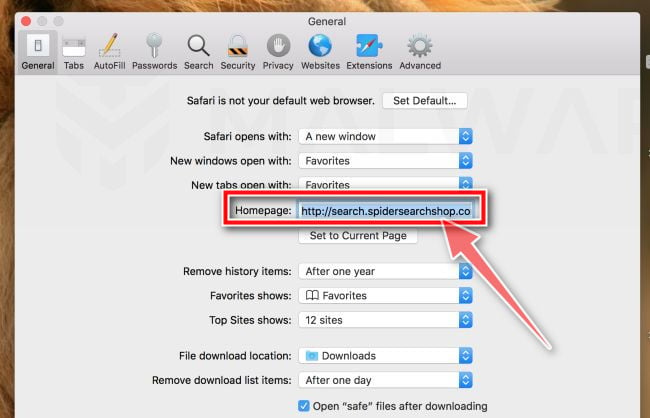
Check Homepage.
This will open a new window with your Safari preferences, opened to the “General” tab. Some browser hijackers may change your default homepage, so in the Homepage field make sure it’s a web page you want to use as your start-up page.
Click “Extensions”
Next, click on the “Extensions” tab.
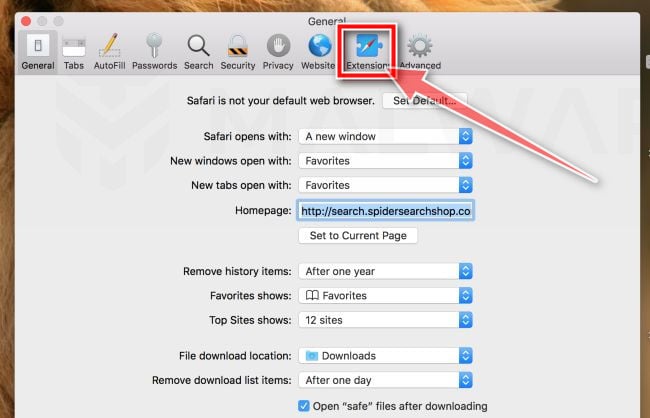
Find and uninstall Threatdetect.org.
The “Extensions” screen will be displayed with a list of all the extensions installed on Safari. Scroll through the list until you find an unknown or suspicious extension, and then click on “Uninstall” to remove it.
Look out for any suspicious browser extension that could be behind all the drama – anything you don’t remember downloading or that doesn’t sound like a genuine extension. By default, there are no extensions installed on Safari so it’s safe to remove any extension.
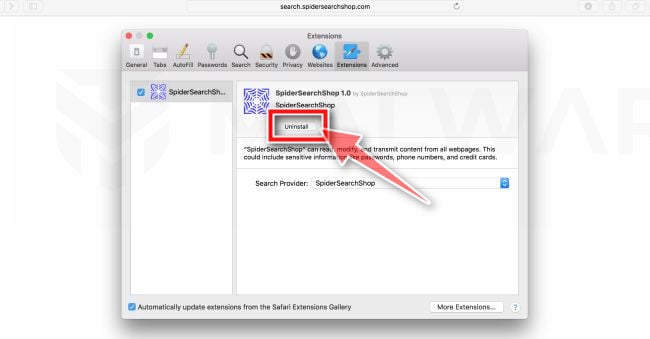 The malicious extension may have a different name on your computer.
The malicious extension may have a different name on your computer.
If the above steps didn’t help you remove the Threatdetect.org browser hijacker from Safari, you can follow the below steps:
Workaround for greyed out Safari’s homepage
In some cases, after being changed by browser hijackers or malware, Safari’s home page can become stuck (greyed out). You will be able to edit the Homepage field in Safari’s preferences, but the change will not stick. This appears to be a bug, and there is an odd workaround. Try this:
- In Safari, choose Preferences from the Safari menu.
- In the window that opens, click the General icon (if necessary)
- Enter your desired home page in the “Homepage” field, but DO NOT press return!
- At the top of the window, click any of the other icons (eg, Tabs, AutoFill, etc).
- You may see a prompt asking for confirmation for changing the home page. If so, confirm.
- Switch back to the General page and check to make sure the home page has been changed.
Delete Safari’s preferences file to remove malicious changes
Some malicious programs are known to install managed preferences to set the homepage and search engine settings in Safari. If the above options didn’t help you remove the malicious redirects, we’ll need to delete Safari’s preferences. To do this, follow the below steps:
- Quit Safari
- Click the desktop to make sure you’re in the Finder, choose “Go” then click on “Go to Folder“.

- Type or copy/paste the following path into the window that opens, then click Go: ~/Library/Preferences/com.apple.Safari.plist
- If the file is found, delete it, then re-open Safari
Remove Threatdetect.org browser hijacker from Chrome for Mac
To remove Threatdetect.org browser hijacker from Chrome for Mac we will reset the browser settings to its default. Resetting your browser settings will reset the unwanted changes caused by installing other programs. However, your saved bookmarks and passwords will not be cleared or changed.
Click on the three dots at the top right and click “Settings”.
Click on Chrome’s main menu button, represented by three dots at the top right corner. Now click on the menu option labeled Settings as shown by the arrow in the picture below, which will open the basic settings screen.
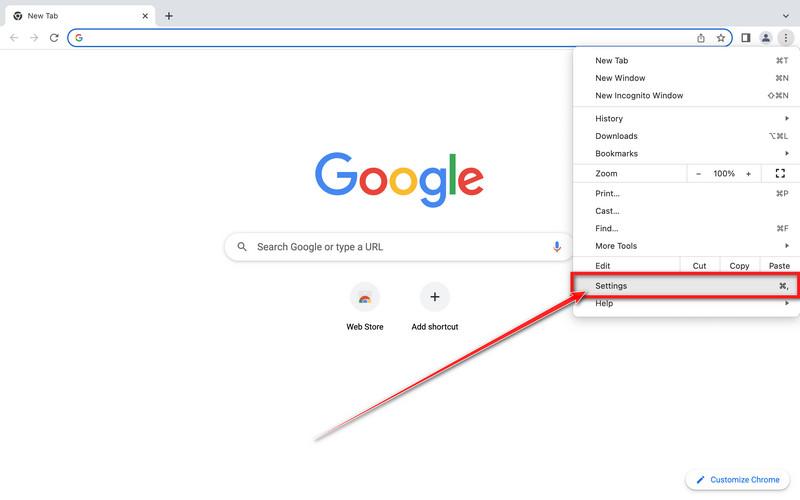
At the bottom, click “Advanced”.
Chrome’s “Settings” should now be displayed in a new tab or window, depending on your configuration. Next, scroll to the bottom of the page and click on the “Advanced” link (as seen in the below example).
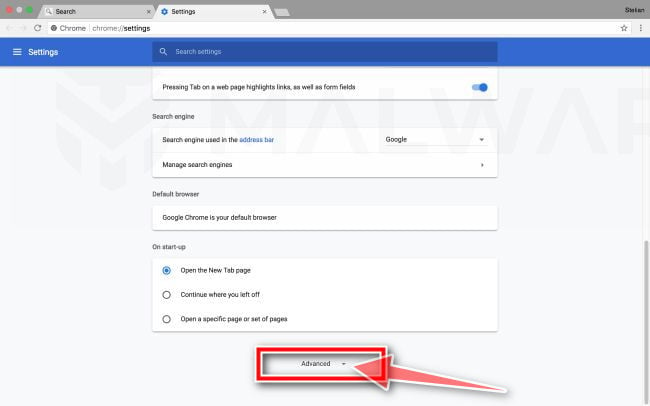
Under the section “Reset,” click “Reset”.
Chrome’s advanced settings should now be displayed. Scroll down until the “Reset and clean up” section is visible, as shown in the example below. Next, click on the “Reset settings to their original defaults” button.
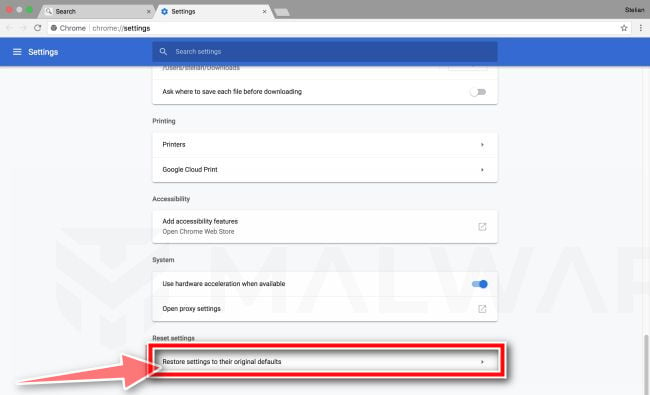
Confirm by clicking “Reset”.
A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue on with the reset process. To complete the restoration process, click on the “Reset Settings” button.
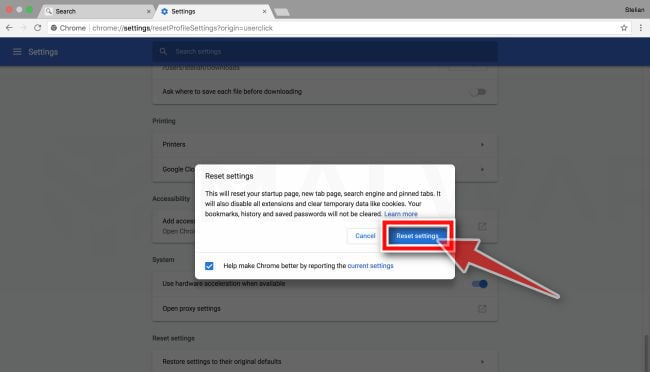
If the above steps didn’t help you remove the Threatdetect.org browser hijacker from Chrome, you can follow the below steps:
Remove the unwanted policies created by malware from Chrome
In many cases, changes to Chrome may not be fixed with a simple browser reset. In such a case, a malicious program may have created unwanted policies on your browser. You can check if any unwanted policies are loaded into the browser by typing chrome://policy into the URL bar.
To reset these policies, follow these steps:- Open a new Terminal window. To do this, go to Finder > Go > Utilities > Terminal
- Enter the following commands, pressing enter after each line:
- defaults write com.google.Chrome HomepageIsNewTabPage -bool false
- defaults write com.google.Chrome NewTabPageLocation -string “https://www.google.com/”
- defaults write com.google.Chrome HomepageLocation -string “https://www.google.com/”
- defaults delete com.google.Chrome DefaultSearchProviderSearchURL
- defaults delete com.google.Chrome DefaultSearchProviderNewTabURL
- defaults delete com.google.Chrome DefaultSearchProviderName
- defaults delete com.google.Chrome ExtensionInstallSources
- After running these commands, quit Chrome if you haven’t already done so, then launch it again and check chrome://policy to see if the same keys are still present (you may need to click the “Reload policies” button for changes to show up). If they’re gone, you should be able to change your search engine and home page back to your preferred defaults in Chrome’s settings.
Remove the “Managed by your organization” policy from Chrome
Some malicious programs are known to install managed preferences to set the home page and search engine settings in Chrome. To check for these, do the following:
- Quit Chrome
- Click the desktop to make sure you’re in the Finder, choose “Go” then click on “Go to Folder“.

- Type or copy/paste the following path into the window that opens, then click Go: /Library/Managed Preferences/
- Paste the below path into the window that opens, then click Go:
Look for the following files, where [username] is your username:- com.google.Chrome.plist
- [username]/com.google.Chrome.plist
- [username]/complete.plist
These may be legitimate, so open these files with TextEdit and see if they have links to the troublesome site in them. If they do, delete them and restart Chrome.
Uninstall Google Chrome from your computer
If the above options didn’t help you remove the malicious redirects, it is easier to completely remove Chrome and all data, then reinstall the browser. To do this, click the Finder icon, from the menu bar. Choose Go, and click Go to Folder, then paste one of the below paths into the window that opens.
You will need to delete all of the below items, but before doing this be aware that this will delete all data for all Google apps you have installed, such as your bookmarks, so you will need to export them before doing this.- /Applications/Chrome.app
- /Library/Application Support/Google/
- /Library/Google/
- ~/Library/Application Support/Google/
- ~/Library/Google/
- ~/Library/Preferences/com.google.Chrome.plist
Note: The “~” indicates that it’s the current user’s Library which is often invisible in recent versions of macOS. To get to it you must hold down the Option (sometimes labeled Alt) key down and select Library from the Finder’s Go menu.
After deleting all of the above files, restart your device. You can now download and re-install Google Chrome on your device. You will need to import any exported bookmarks or other data and may need to reinstall any other Google apps that you use.
Remove Threatdetect.org browser hijacker from Firefox for Mac
To remove Threatdetect.org browser hijacker from Firefox for Mac we will reset the browser settings to its default. The reset feature fixes many issues by restoring Firefox to its factory default state while saving your essential information like bookmarks, passwords, web form auto-fill information, browsing history, and open tabs.
Go to the “Help” menu.
Click on Firefox’s main menu button, represented by three horizontal lines. When the drop-down menu appears, select the option labeled “Help“.
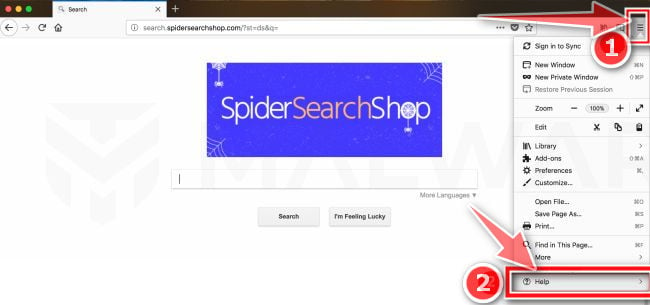
Click “Troubleshooting Information”.
From the Help menu, click on “Troubleshooting Information“.
If you’re unable to access the “Help” menu, type about:support in your address bar to bring up the Troubleshooting information page.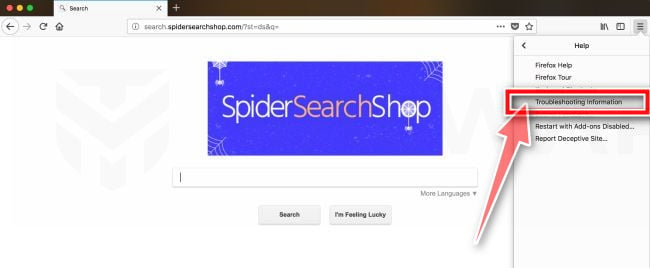
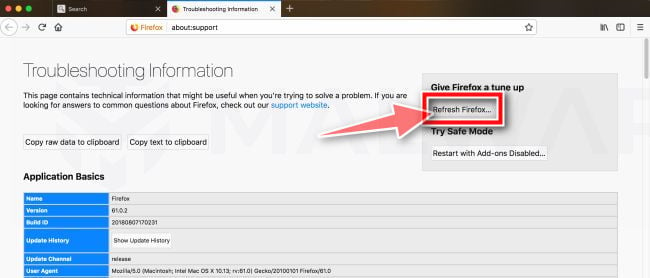
Click on “Refresh Firefox”
Click the “Refresh Firefox” button in the upper-right corner of the “Troubleshooting Information” page.
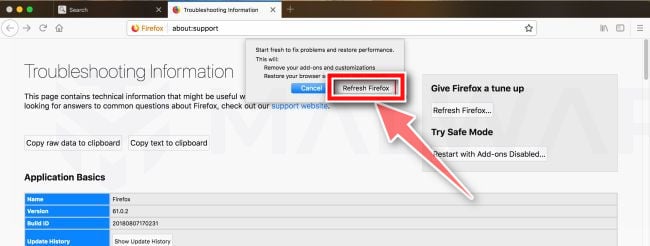
Confirm.
To continue, click on the “Refresh Firefox” button in the new confirmation window that opens.
Click on “Finish”.
Firefox will close itself and will revert to its default settings. When it’s done, a window will list the information that was imported. Click on the “Finish“.
Your computer should now be free of the Threatdetect.org browser hijacker. If your current antivirus allowed a malicious program on your computer, you might want to consider purchasing the full-featured version of Malwarebytes Anti-Malware to protect against these types of threats in the future.
If you are still experiencing problems while trying to a malicious program from your computer, please ask for help in our Mac Malware Removal Help & Support forum.
- STEP 1: Uninstall the malicious apps from your Android phone
- STEP 2: Use Malwarebytes for Android to remove Threatdetect.org adware
- STEP 3: Reset your browser settings to remove Threatdetect.org pop-up ads
STEP 1: Uninstall the malicious apps from your Android phone
In this first step, we will check if any malicious apps are installed on your phone. Sometimes browser hijackers or adware apps can have usable Uninstall entries that can be used to remove these apps.
Open the “Settings” menu.
Tap on the “Settings” app from your phone menu or home screen.
Tap on “Apps”.
When the “Settings” menu opens, tap on “Apps” (or “App Manager”) to see all the installed applications on your phone.
Find the malicious app.
The “Apps” screen will be displayed with a list of all the applications that are installed on your phone. Scroll through the list until you find the unknown or malicious app. Look out for any suspicious app that could be behind all the drama – anything you don’t remember downloading or that doesn’t sound like a genuine program.
Most often, cybercriminals hide malware inside the video or photo editing apps, weather apps, and camera apps.Here are some known malicious apps: ES File Explorer, Xender, Amber Weather Widget, GO Weather Forecast & Widgets, Kitty Play, Touchpal, Z Camera. If you cannot find the malicious app, we advise you to uninstall all the recently installed applications.
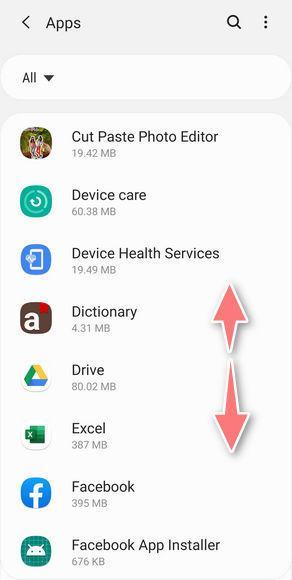
Uninstall the malicious app
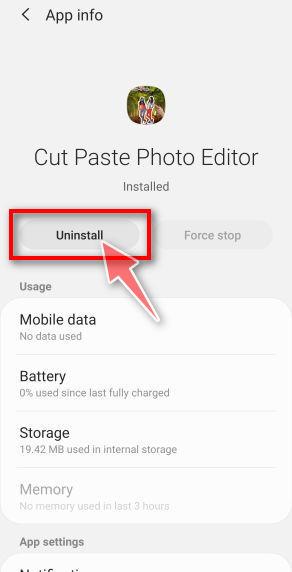
When you find a suspicious or malicious app, tap on it to uninstall it. This won’t start the app but will open up the app details screen. If the app is currently running press the “Force stop” button, then tap on “Uninstall”.
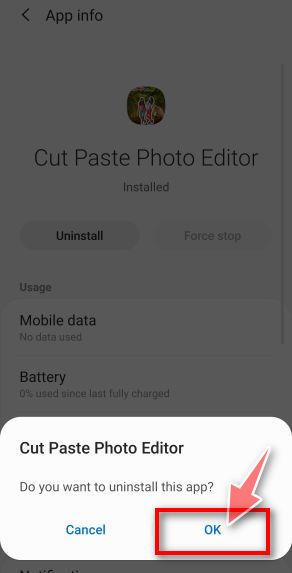
A confirmation dialog should be displayed to confirm you want to uninstall the app, tap on “OK” to remove the malicious app from your phone.
STEP 2: Use Malwarebytes for Android to remove Threatdetect.org adware
In this next step, we will install Malwarebytes for Android to scan and remove malicious apps from your phone.
Malwarebytes for Android Free is an on-demand scanner that searches all files and apps quickly and effectively for malware or potentially unwanted programs such as screen lockers or adware, freeing your phone from bloatware.
Download Malwarebytes for Android.
You can download Malwarebytes for Android by clicking the link below.
 MALWAREBYTES FOR ANDROID DOWNLOAD LINK
MALWAREBYTES FOR ANDROID DOWNLOAD LINK
(The above link will open a new page from where you can download Malwarebytes for Android)Install Malwarebytes for Android on your phone.
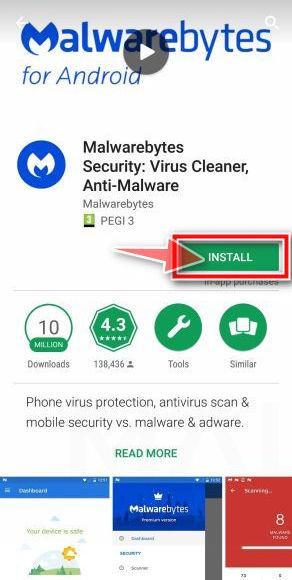
In the Google Play Store, tap “Install” to install Malwarebytes for Android on your device.
When the installation process has finished, tap “Open” to begin using Malwarebytes for Android. You can also open Malwarebytes by tapping on its icon in your phone menu or home screen.
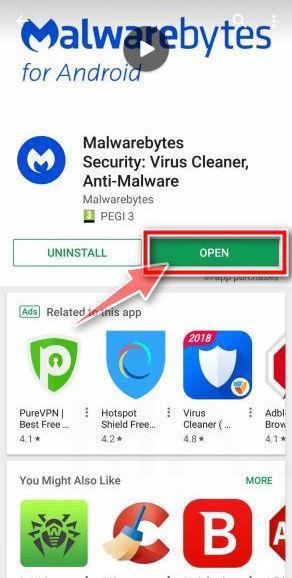
Follow the on-screen prompts to complete the setup process
When the Malwarebytes will open, you will see the Malwarebytes Setup Wizard which will guide you through a series of permissions and other setup options.
This is the first of two screens which explain the difference between the Premium and Free version. Swipe this screen to continue.
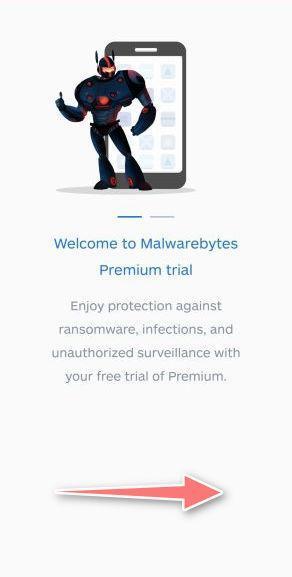
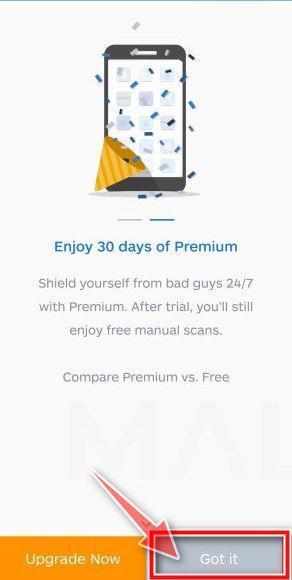
Tap on “Got it” to proceed to the next step.
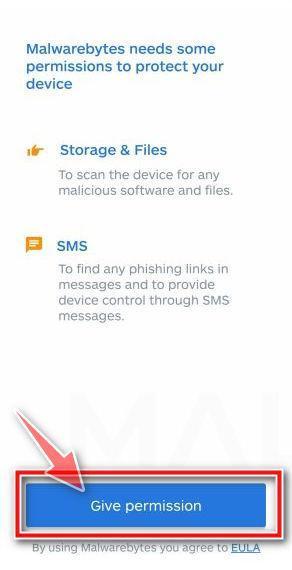
Malwarebytes for Android will now ask for a set of permissions that are required to scan your device and protect it from malware. Tap on “Give permission” to continue.
Tap on “Allow” to give permission to Malwarebytes to access the files on your phone.
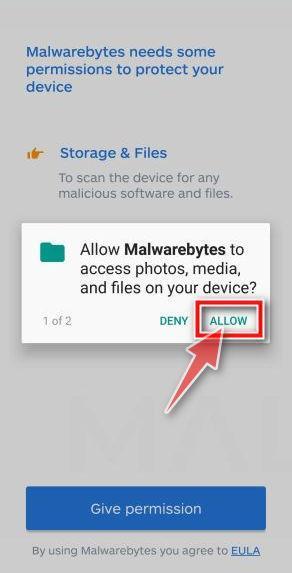
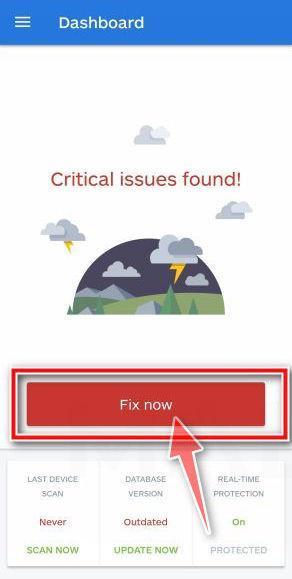
Update database and run a scan with Malwarebytes for Android
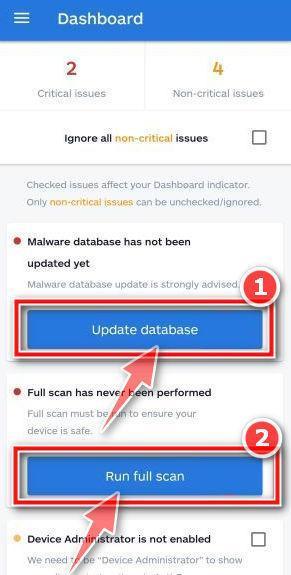
You will now be prompted to update the Malwarebytes for Android database and run a full system scan.
Click on “Update database” to update the Malwarebytes for Android definitions to the latest version, then click on “Run full scan” to perform a system scan.
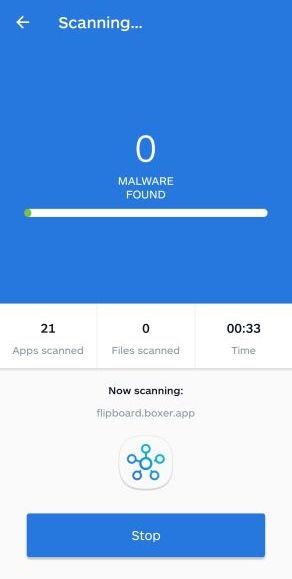
Wait for the Malwarebytes scan to complete.
Malwarebytes will now start scanning your phone for adware and other malicious apps. This process can take a few minutes, so we suggest you do something else and periodically check on the status of the scan to see when it is finished.
Click on “Remove Selected”.
When the scan has completed, you will be presented with a screen showing the malware infections that Malwarebytes for Android has detected. To remove the malicious apps that Malwarebytes has found, tap on the “Remove Selected” button.
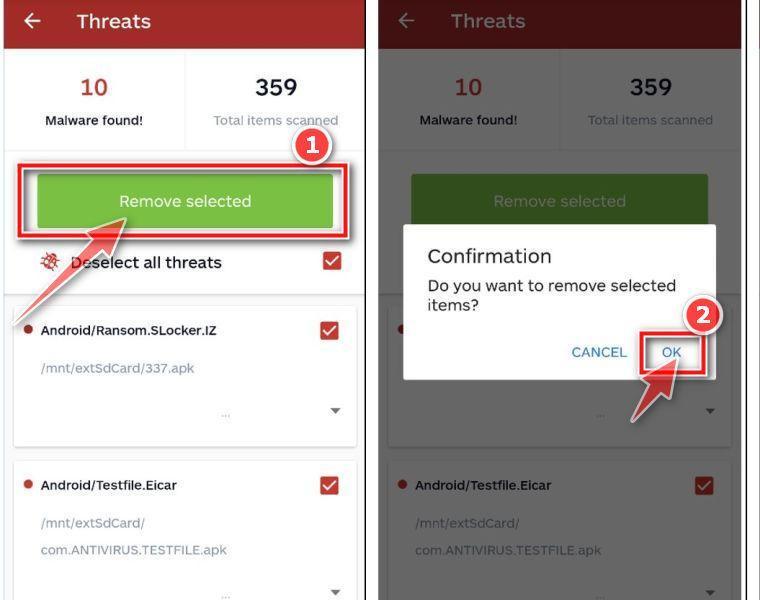
Restart your phone.
Malwarebytes for Android will now remove all the malicious apps that it has found. To complete the malware removal process, Malwarebytes may ask you to restart your device.
STEP 3: Reset your browser settings to remove Threatdetect.org pop-ups
In this final step, if your phone is still redirected to the Threatdetect.org ads, we will need to reset the web browser settings to their original defaults. This step should be performed only if the issues have not been solved by the previous steps.
Resetting the browser settings to their default it’s an easy task on Windows or Mac computers; however, when it comes to Android, this can’t be done directly because it’s not an option built-in into the browser settings. Restoring the browser settings on Android can be done by clearing the application data. This will remove all the cookies, cache, and other site settings that may have been saved. So let’s see how we can restore your browser to its factory settings.
Remove Threatdetect.org pop-up ads from Chrome for Android
To reset Chrome for Android to its default settings, follow the below steps:
Open the “Settings” menu.
Tap on the “Settings” app from your phone menu or home screen.

Tap on “Apps”.
When the “Settings” menu opens, tap on “Apps” (or “App Manager”) to see all the installed applications on your phone.

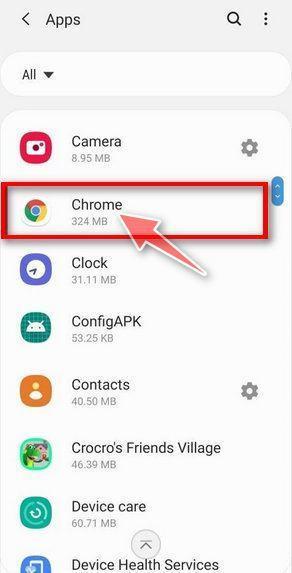
Find and tap on Chrome.
The “Apps” screen will be displayed with a list of all the apps installed on your phone. Scroll through the list until you find the Chrome app, then tap on it to open the apps details.
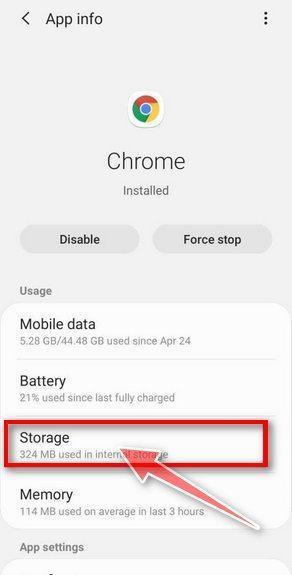
Tap “Storage”.
When the Chrome’s app info menu is displayed, tap on “Storage“.
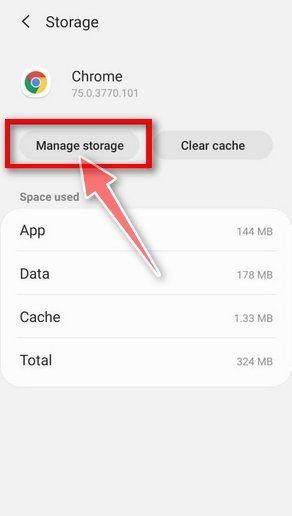
Tap “Manage Space”.
Under the storage settings, you will get two options — Manage Space and Clear Cache. Tap on “Manage Space“.
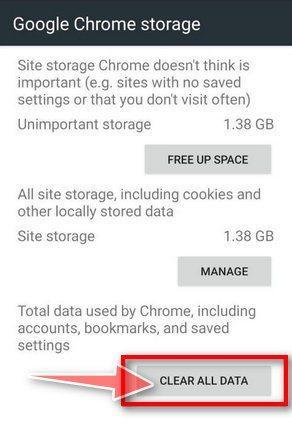
Tap “Clear all data”.
Tap “Clear all data” to delete all Chrome’s data including accounts, bookmarks and your settings in order to reset the default settings.
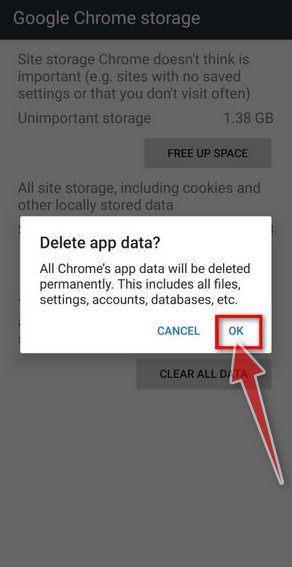
Confirm by tapping “Ok”.
A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue on with the reset process. To complete the restoration process, tap “Ok“.
Remove Threatdetect.org pop-up ads from Firefox for Android
To reset Firefox for Android to its default settings, follow the below steps:
Open the “Settings” menu.
Tap on the “Settings” app from your phone menu or home screen.

Tap on “Apps”.
When the “Settings” menu opens, tap on “Apps” (or “App Manager”) to see all the installed applications on your phone.

Find and tap on Firefox.
The “Apps” screen will be displayed with a list of all the apps installed on your phone. Scroll through the list until you find the Firefox app, then tap on it to open the apps details.

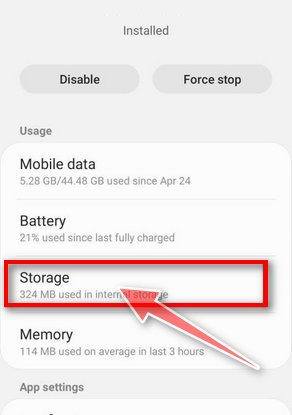
Tap “Storage”.
When the Firefox’s app info menu is displayed, tap on “Storage“.
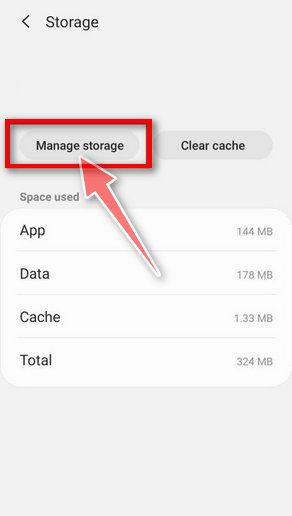
Tap “Manage Space”.
Under the storage settings, you will get two options — Manage Space and Clear Cache. Tap on “Manage Space“.
Tap “Clear all data”.
Tap “Clear all data” to delete all Firefox’s data including accounts, bookmarks and your settings in order to reset the default settings.

Confirm by tapping “Ok”.
A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue on with the reset process. To complete the restoration process, tap “Ok“.
Remove Threatdetect.org from Opera browser
To reset the Opera browser to its default settings, follow the below steps:
Open the “Settings” menu.
Tap on the “Settings” app from your phone menu or home screen.

Tap on “Apps”.
When the “Settings” menu opens, tap on “Apps” (or “App Manager”) to see all the installed applications on your phone.

Find and tap on Opera.
The “Apps” screen will be displayed with a list of all the apps installed on your phone. Scroll through the list until you find the Opera app, then tap on it to open the apps details.

Tap “Storage”.
When the Opera’s app info menu is displayed, tap on “Storage“.

Tap “Manage Space”.
Under the storage settings, you will get two options — Manage Space and Clear Cache. Tap on “Manage Space“.

Tap “Clear all data”.
Tap “Clear all data” to delete all Opera’s data including accounts, bookmarks and your settings in order to reset the default settings.

Confirm by tapping “Ok”.
A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue on with the reset process. To complete the restoration process, tap “Ok“.
Remove Threatdetect.org from Samsung Internet Browser
To reset the Samsung Internet Browser to its default settings, follow the below steps:
Open the “Settings” menu.
Tap on the “Settings” app from your phone menu or home screen.

Tap on “Apps”.
When the “Settings” menu opens, tap on “Apps” (or “App Manager”) to see all the installed applications on your phone.

Find and tap on Samsung Internet Browser.
The “Apps” screen will be displayed with a list of all the apps installed on your phone. Scroll through the list until you find the Samsung Internet Browser app, then tap on it to open the apps details.

Tap “Storage”.
When the Samsung Internet Browser’s app info menu is displayed, tap on “Storage“.

Tap “Manage Space”.
Under the storage settings, you will get two options — Manage Space and Clear Cache. Tap on “Manage Space“.

Tap “Clear all data”.
Tap “Clear all data” to delete all Samsung Internet Browser’s data including accounts, bookmarks, and your settings in order to reset the default settings.

Confirm by tapping “Ok”.
A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue on with the reset process. To complete the restoration process, tap “Ok“.
Remove Threatdetect.org from Microsoft Edge for Android
To reset the Microsoft Edge for Android to its default settings, follow the below steps:
Open the “Settings” menu.
Tap on the “Settings” app from your phone menu or home screen.

Tap on “Apps”.
When the “Settings” menu opens, tap on “Apps” (or “App Manager”) to see all the installed applications on your phone.

Find and tap on Microsoft Edge.
The “Apps” screen will be displayed with a list of all the apps installed on your phone. Scroll through the list until you find the Microsoft Edge app, then tap on it to open the apps details.

Tap “Storage”.
When the Microsoft Edge’s app info menu is displayed, tap on “Storage“.

Tap “Manage Space”.
Under the storage settings, you will get two options — Manage Space and Clear Cache. Tap on “Manage Space“.

Tap “Clear all data”.
Tap “Clear all data” to delete all Microsoft Edge’s data including accounts, bookmarks, and your settings in order to reset the default settings.

Confirm by tapping “Ok”.
A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue on with the reset process. To complete the restoration process, tap “Ok“.
Your phone should now be free of the Threatdetect.org pop-up ads. If your current antivirus allowed a malicious app on your phone, you may want to consider purchasing the full-featured version of Malwarebytes to protect against these types of threats in the future.
If you are still having problems with your phone after completing these instructions, then please follow one of the steps:
- Restore your phone to factory settings by going to Settings > General management > Reset > Factory data reset.
- Ask for help in our Mobile Malware Removal Help & Support forum.

