This thread is about a different method of applying the AppLocker policies on Windows Home. The first method was discussed in the thread:
https://malwaretips.com/threads/applocker-on-windows-home.118614/
It was based on MDM WMI Bridge implemented in PowerShell.
In this thread, I am going to use the GPO policies.
Yes, the GPO Applocker policies can work well on Windows 10 Home without GPO!!!
How to do it.
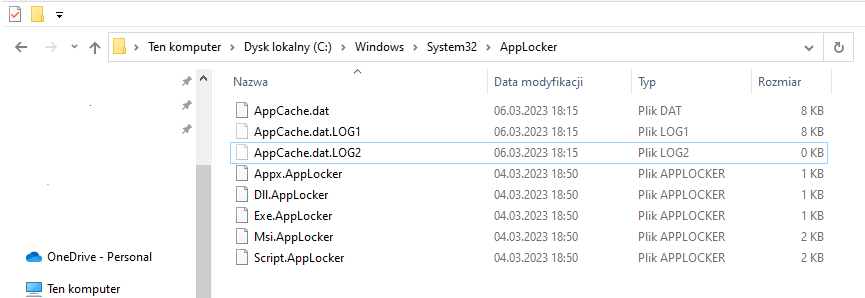
One has to use the binary policies made on the computer with Windows Pro (Appx.AppLocker, Dll.AppLocker, Exe.AppLocker, Msi.AppLocker, Script.AppLocker). They are located in the directory:
%WinDir%\System32\Applocker
The AppLocker protection can be turned OFF/ON by changing the registry value:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Srp\Gp]
"RuleCount"=dword:00000002
If it is equal to 0 then AppLocker is turned OFF. If it is equal to 2, then AppLocker is turned ON.
WARNING:
The method presented in this thread is new, so please test it first in the Virtual Machine.
https://malwaretips.com/threads/applocker-on-windows-home.118614/
It was based on MDM WMI Bridge implemented in PowerShell.
In this thread, I am going to use the GPO policies.
Yes, the GPO Applocker policies can work well on Windows 10 Home without GPO!!!
How to do it.
One has to use the binary policies made on the computer with Windows Pro (Appx.AppLocker, Dll.AppLocker, Exe.AppLocker, Msi.AppLocker, Script.AppLocker). They are located in the directory:
%WinDir%\System32\Applocker
- Copy these 5 policies to the computer with Windows 10 Home (into %WinDir%\System32\Applocker).
- Open the PowerShell console with Administrator rights and set the AppIDSvc service to automatic:
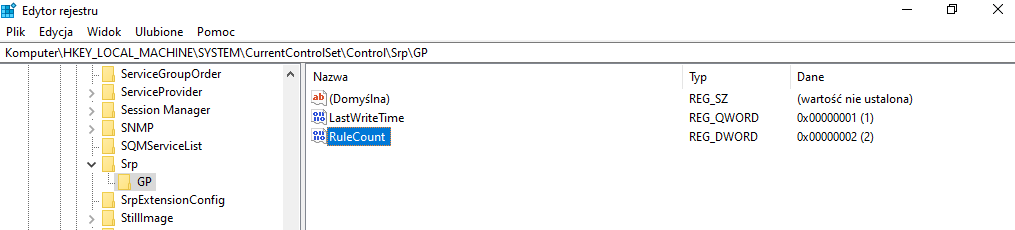
sc.exe config appidsvc start= auto - Add the registry keys (the second key is QWORD):
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Srp\Gp]
"RuleCount"=dword:00000002
"LastWriteTime"=hex(b):01,00,00,00,00,00,00,00 - Restart the computer.
The AppLocker protection can be turned OFF/ON by changing the registry value:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Srp\Gp]
"RuleCount"=dword:00000002
If it is equal to 0 then AppLocker is turned OFF. If it is equal to 2, then AppLocker is turned ON.
WARNING:
- When AppLocker is turned ON, the SRP automatically turns itself OFF. So, the restrictions made by SimpleWindowsHardening or Hard_Configurator will not work with AppLocker.
- This method is incompatible with AppLocker introduced via MDM WMI Bridge (MDM policies should be removed from the AppLocker directory).
The method presented in this thread is new, so please test it first in the Virtual Machine.
Last edited:

