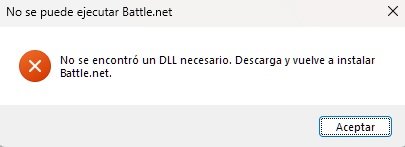
If one asks security experts about Applocker, then many of them know that Applocker can work via GPO on Windows Enterprise, Education, or Server editions. Here is the info from Microsoft (related to Windows 10 and 11):

But, as we can see from the above info, Applocker can work on Windows 10 and 11 without GPO, when managed by MDM. It is interesting because currently there are issues with Software Restriction Policies on Windows 11 ver 22H2. After some research, I found an interesting article about this possibility, written by Sandy Zeng:
:

 msendpointmgr.com
msendpointmgr.com
Sandy is skilled in Microsoft Endpoint Manager (ConfigMgr and Intune), Windows 10 and security. She applied Applocker policies for EXE files via MDM WMI Bridge. I tested this successfully also on Windows Home.
After some trial and error work, I managed to create some PowerShell scripts, similar to those used in the article. These scripts can create/add/remove Applocker policies also for DLLs, scripts, MSI Installer, and packaged apps.
Some interesting resources:

 4sysops.com
4sysops.com
 call4cloud.nl
call4cloud.nl

 github.com
github.com
Edit.
Warning!!!
I strongly recommend making a System Restore Point before applying the Applocker rules.
You can use the AppLocker CSP to configure AppLocker policies on any edition of Windows 10 and Windows 11 supported by Mobile Device Management (MDM). You can only manage AppLocker with Group Policy on devices running Windows 10 and Windows 11 Enterprise, Windows 10 and Windows 11 Education, and Windows Server 2016.

Requirements to use AppLocker
This article for the IT professional lists software requirements to use AppLocker on the supported Windows operating systems.
learn.microsoft.com
But, as we can see from the above info, Applocker can work on Windows 10 and 11 without GPO, when managed by MDM. It is interesting because currently there are issues with Software Restriction Policies on Windows 11 ver 22H2. After some research, I found an interesting article about this possibility, written by Sandy Zeng:
:

Does AppLocker work in Windows 10 Pro? Yes, it does! - MSEndpointMgr
MSEndpointMgr Does AppLocker work in Windows 10 Pro? Yes, it does! In this post, I will show you how to maange AppLocker rules for Windows 10 Pro, by using PowerShell.
Sandy is skilled in Microsoft Endpoint Manager (ConfigMgr and Intune), Windows 10 and security. She applied Applocker policies for EXE files via MDM WMI Bridge. I tested this successfully also on Windows Home.
After some trial and error work, I managed to create some PowerShell scripts, similar to those used in the article. These scripts can create/add/remove Applocker policies also for DLLs, scripts, MSI Installer, and packaged apps.
Some interesting resources:

Enable AppLocker on Windows 10 Pro and Windows 11 Pro with PowerShell – 4sysops
In the past, AppLocker was available only for Windows Enterprise and Education subscribers. In this post, I will show you a way to use AppLocker on Windows 10 P

Applocker | Windows Pro | WMI Bridge | Deploy without Intune
Windows Pro | Deploy Applocker Without Intune | rootcimv2mdmdmmap | WBEMTest | WMI Bridge |
 call4cloud.nl
call4cloud.nl
MSIntune/Intune-PowerShell/AppLocker at master · sandytsang/MSIntune
Contribute to sandytsang/MSIntune development by creating an account on GitHub.
Edit.
Warning!!!
I strongly recommend making a System Restore Point before applying the Applocker rules.
Last edited: