Thanks Andy.Interesting. Is the block present if you open Microsoft Store and do nothing?
Please, wait - I have noticed the same now on my computer. I will try to investigate what it means.
New Update Simple Windows Hardening
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
F
ForgottenSeer 95367
SWHThank you. I guess this happens when I go to the Microsoft store and update my apps.
I made some research. The block is for WindowsPackageManagerServer.exe. It can be important for developers who are going to submit their applications to Microsoft Store. When opening, the Microsoft Store tries to access it.Yes.
This block can be ignored by home users. The updates and installations of UWP apps are not impacted.
Anyway, it would be good to get rid of it.
F
ForgottenSeer 95367
SWH thenDon't use HC.
Somehow a wildcard rule is getting "set" in SWH for the WindowsApps folder.
Since nothing was ever broken, the blocks events were moot from the beginning.
Last edited by a moderator:
True. Everything in the Microsoft Store can be updated manually or automatically as usual. No issues on my computer.I made some research. The block is for WindowsPackageManagerServer.exe. It can be important for developers who are going to submit their applications to Microsoft Store. When opening, the Microsoft Store tries to access it.
This block can be ignored for home users. The updates and installations of UWP apps are not impacted.
F
ForgottenSeer 77194
I have a feature request for SWH.
Add an option or button in SWH to check for updates or to auto update(Delete previous version and download new one.)
Add an option or button in SWH to check for updates or to auto update(Delete previous version and download new one.)
Agreed. Quite a pain to manually check for updates for every single hardening tool like SWH, ConfigureDefender, Firewall Hardening etc.I have a feature request for SWH.
Add an option or button in SWH to check for updates or to auto update(Delete previous version and download new one.)
Thats great. Looking forward to it.I have this in my plans.
This will require some important changes with my repositories on GitHub and MT threads, so I am not sure when it will happen. I am thinking about adding FirewallHardening and RunBySmartScreen to the SWH repository. So, there will be two main repositories: ConfigureDefender and SWH (with DocumentsAntiExploit, FirewallHardening, and RunBySmartscreen).
Nice.This will require some important changes with my repositories on GitHub and MT threads, so I am not sure when it will happen. I am thinking about adding FirewallHardening and RunBySmartScreen to the SWH repository. So, there will be two main repositories: ConfigureDefender and SWH (with DocumentsAntiExploit, FirewallHardening, and RunBySmartscreen).
Seems like a good plan to me.This will require some important changes with my repositories on GitHub and MT threads, so I am not sure when it will happen. I am thinking about adding FirewallHardening and RunBySmartScreen to the SWH repository. So, there will be two main repositories: ConfigureDefender and SWH (with DocumentsAntiExploit, FirewallHardening, and RunBySmartscreen).
Or H_C and standalone (everything else!) tools repositories.This will require some important changes with my repositories on GitHub and MT threads, so I am not sure when it will happen. I am thinking about adding FirewallHardening and RunBySmartScreen to the SWH repository. So, there will be two main repositories: ConfigureDefender and SWH (with DocumentsAntiExploit, FirewallHardening, and RunBySmartscreen).
Maybe H_C could get big buttons that would do the stuff SWH could do (with or without DocumentsAntiExploit, FirewallHardening, and RunBySmartscreen) and the normal (like they are now option) H_C option/settings would just be accessible with a small "advanced user I know the risks" button.
So there would be only H_C which could be used by novice users and advanced. Just take it as a random thought of a none coder who got no clue about the amount of work it would require
Thanks for all your time and work to keep H_C running
Tldr H_C would start with "novice" interface that would onlyallow to do stuff like SWH, while more "dangerous" option would be still there but "hidden" with an "advanced" button.
So there would be only H_C which could be used by novice users and advanced. Just take it as a random thought of a none coder who got no clue about the amount of work it would require
Thanks for all your time and work to keep H_C running
Tldr H_C would start with "novice" interface that would onlyallow to do stuff like SWH, while more "dangerous" option would be still there but "hidden" with an "advanced" button.
It is not possible. The H_C must be installed (not a portable application) and the standalone tools like ConfigureDefender, SWH, etc. are portable applications.Maybe H_C could get big buttons that would do the stuff SWH could do (with or without DocumentsAntiExploit, FirewallHardening, and RunBySmartscreen) and the normal (like they are now option) H_C option/settings would just be accessible with a small "advanced user I know the risks" button.
I could do what you have proposed, but only for the H_C. I am not sure that this is necessary when the standalone tools can do just the same.
SWH vs. AstraLocker attack

 malwaretips.com
malwaretips.com

 blog.reversinglabs.com
blog.reversinglabs.com
The attack is very primitive and well known. I doubt if such malware could infect the users under the protection of any popular AV. Anyway, it shows the method used a few years ago quite often.
The malware uses the well known method to weaponize MS Word documents via embedding the malicious executable directly into the document (OLE method). This method is uncommon in the wild nowadays, because the user must click on the icon in the document and next allow to run the file:
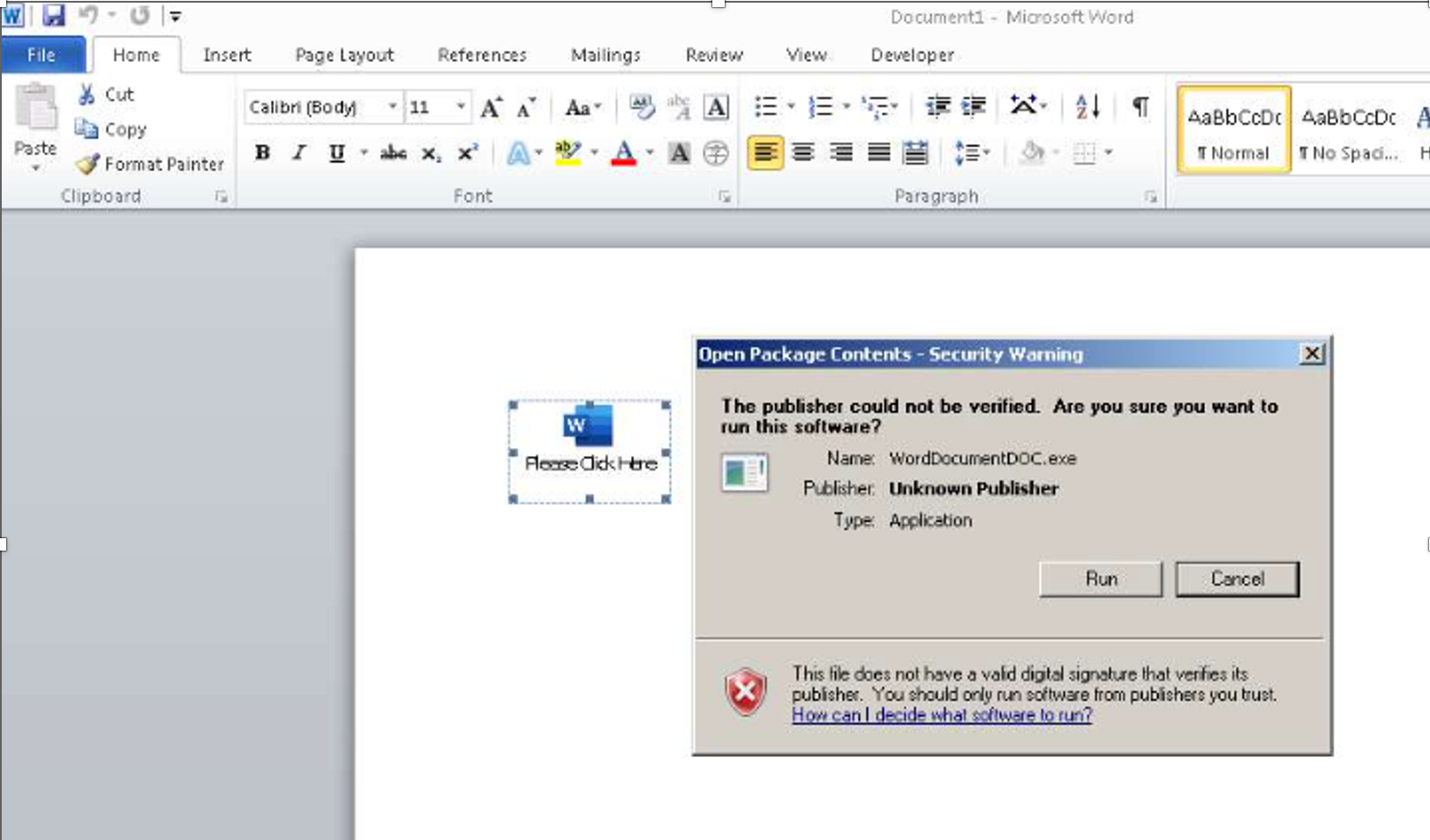
The infection chain:
Email attachment (Word document) ----> user opens the document and clicks the icon (OLE) -----> user presses Run button ---> malware is executed
The malware is blocked by SWH 2.0.0.0 recommended settings:

AstraLocker 2.0 infects users directly from Word attachments
A lesser-known ransomware strain called AstraLocker has recently released its second major version, and according to threat analysts, its operators engage in rapid attacks that drop its payload directly from email attachments. This approach is quite unusual as all the intermediate steps that...
 malwaretips.com
malwaretips.com

RL Blog | ReversingLabs | ReversingLabs
RL Blog: AppSec & Supply Chain Security, Dev & DevSecOps, Threat Research, and Security Operations (SecOps)
The attack is very primitive and well known. I doubt if such malware could infect the users under the protection of any popular AV. Anyway, it shows the method used a few years ago quite often.
The malware uses the well known method to weaponize MS Word documents via embedding the malicious executable directly into the document (OLE method). This method is uncommon in the wild nowadays, because the user must click on the icon in the document and next allow to run the file:
The infection chain:
Email attachment (Word document) ----> user opens the document and clicks the icon (OLE) -----> user presses Run button ---> malware is executed
The malware is blocked by SWH 2.0.0.0 recommended settings:
- No ConfigureDefender HIGH Protection Level: malware blocked after MS Office hardening via DocumentsAntiExploit tool.
- Defender + ConfigureDefender HIGH Protection Level: malware blocked by ASR rule.
Last edited:
SWH vs. Raspberry Robin worm

 www.cybereason.com
www.cybereason.com

 malwaretips.com
malwaretips.com

 www.bleepingcomputer.com
www.bleepingcomputer.com

 www.bleepingcomputer.com
www.bleepingcomputer.com
It is a typical attack via an infected USB drive that contains a malicious shortcut (.lnk file) masquerading as a legitimate folder on a USB device. Opening the fake folder starts the infection chain.

SWH can block such attacks by default due to the special SRP restrictions for shortcuts. The shortcuts are rarely restricted in the business environment even for USB drives. Furthermore, the Applocker and Microsoft Application Control cannot block shortcuts and most administrators do not know how to effectively manage the shortcuts via SRP.
Edit.
This thread can be also blocked by FirewallHardening tool - the LOLBin msiexec.exe will be prevented from downloading the malicious DLL from the URL.

THREAT ALERT: Raspberry Robin Worm Abuses Windows Installer and QNAP Devices
Raspberry Robin involves a worm that spreads over USB devices or shared folders, leveraging compromised QNAP (Network Attached Storage or NAS) devices as stagers and an old but still effective method of using “LNK” shortcut files to lure its victims...

Microsoft finds Raspberry Robin worm in hundreds of Windows networks
Microsoft says that a recently spotted Windows worm has been found on the networks of hundreds of organizations from various industry sectors. The malware, dubbed Raspberry Robin, spreads via infected USB devices, and it was first spotted in September 2021 by Red Canary intelligence analysts...
 malwaretips.com
malwaretips.com

Microsoft finds Raspberry Robin worm in hundreds of Windows networks
Microsoft says that a recently spotted Windows worm has been found on the networks of hundreds of organizations from various industry sectors.

New Raspberry Robin worm uses Windows Installer to drop malware
Red Canary intelligence analysts have discovered a new Windows malware with worm capabilities that spreads using external USB drives.
It is a typical attack via an infected USB drive that contains a malicious shortcut (.lnk file) masquerading as a legitimate folder on a USB device. Opening the fake folder starts the infection chain.
SWH can block such attacks by default due to the special SRP restrictions for shortcuts. The shortcuts are rarely restricted in the business environment even for USB drives. Furthermore, the Applocker and Microsoft Application Control cannot block shortcuts and most administrators do not know how to effectively manage the shortcuts via SRP.
Edit.
This thread can be also blocked by FirewallHardening tool - the LOLBin msiexec.exe will be prevented from downloading the malicious DLL from the URL.
Last edited:
SWH can block such attacks by default due to the special SRP restrictions for shortcuts. The shortcuts are rarely restricted in the business environment even for USB drives. Furthermore, the Applocker and Microsoft Application Control cannot block shortcuts and most administrators do not know how to effectively manage the shortcuts via SRP.
Thanks Andy. I guess no need to block additional Sponsors such as msiexec.exe or odbcconf.exe?
EDIT
Oops
Last edited:
Thanks Andy. I guess no need to block additional Sponsors such as msiexec.exe or odbcconf.exe?
EDIT
Oopsthis is the SWH thread. I was thinking of H_C which I use, so I'm not even sure if my question can also apply to SWH.
Yes. SWH cannot block LOLBins because it generally allows EXE files. But, as you can see by reading the examples in this thread, it can efficiently prevent running LOLBins in fileless attacks.
If SWH can block the attack, then also H_C can do it even with Basic_Recommended_Settings.
You may also like...
-
New Update Defender Hardening Console (part of Hawk Eye Analysis Platform)
- Started by Trident
- Replies: 62
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
-
