Post updated in September 2024.
SWH works with Windows 10 and 11 (all versions including 24H2)
Windows 11 ver. 22H2 (fresh installation) turns off by default Software Restriction Policies. So, SimpleWindowsHardening ver. 2.0.0.1 (and prior) cannot use the SWH options related to SRP. This issue is corrected in version 2.1.1.1. It can also work with enabled Smart App Control.
Microsoft documentation for Software Restriction Policies (July 2021):
 This documentation was made for Windows Server (2012-2022), but SRP works the same on Windows 7, 8, 8.1, 10, and 11. From Windows 11, one has to pay attention to AppLocker policies.
This documentation was made for Windows Server (2012-2022), but SRP works the same on Windows 7, 8, 8.1, 10, and 11. From Windows 11, one has to pay attention to AppLocker policies.
Overview
Simple Windows Hardening (SWH) works on Windows Home and Pro editions. It is a portable application that allows configuring Windows built-in features to support antivirus and prevent fileless malware. SWH is adjusted to the home environment. After the initial configuration, it can be closed and all protection comes from the Windows built-in features.
SWH is based on Software Restriction Policies (SRP) and some useful Windows Policies. Users on Windows 11 should bear in mind that Microsoft stopped the development of SRP a few years ago. One cannot exclude the possibility that some problems related to SRP may arise in the future on Windows 11. It is also possible that Microsoft will remove SRP on Windows 12. SWH is tested via the Windows Insider program, so any possible problem is recognized in advance and reported on the Dev. Website.
The security setup is adjusted to keep usability and prevent fileless malware in the home environment. So, the EXE and MSI files are not restricted in SWH, except when executed from archives and email clients. But non-executable files like scripts, shortcuts, and other files with unsafe extensions are restricted. Such a setup can be very efficient because nowadays, many initial vectors of attack are performed via non-executable files.
The more sophisticated attack, the fewer chances that AV can detect it, but the greater chances that SWH can prevent it.
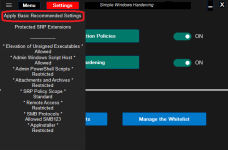
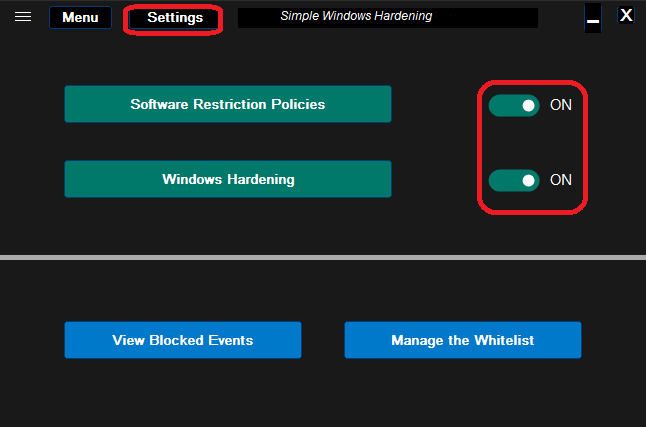
The restrictions made by SWH can be switched OFF/ON by using two switches on the right of the green buttons: <Software Restriction Policies> and <Windows Hardening>. In the OFF position, the restrictions are remembered and next removed - Windows default settings are applied for previously restricted features. When switching ON, the remembered settings are restored. Furthermore, in the ON position, the configurable settings can be changed by the user from the Settings menu.
# THE EXE / MSI 0-DAY MALWARE
The SWH application does not apply restrictions to EXE and MSI files, because these files are often used to install/update applications. Nowadays, many antivirus solutions have very good detection of such files, as compared to the detection of scripts. But still, the antivirus proactive features can have a problem with 0-day malware. In the home environment, the main delivery vectors of 0-day malware are spam emails and flash drives (USB drives).
The user has to be very careful when running EXE/MSI files originating from:
RunBySmartscreen is available as a part of Hard_Confugurator Hardening Tools (together with ConfigureDefender and FirewallHardening): ConfigureDefender/H_C_HardeningTools at master · AndyFul/ConfigureDefender
# QUICK CONFIGURATION
# RECOMMENDED SETTINGS
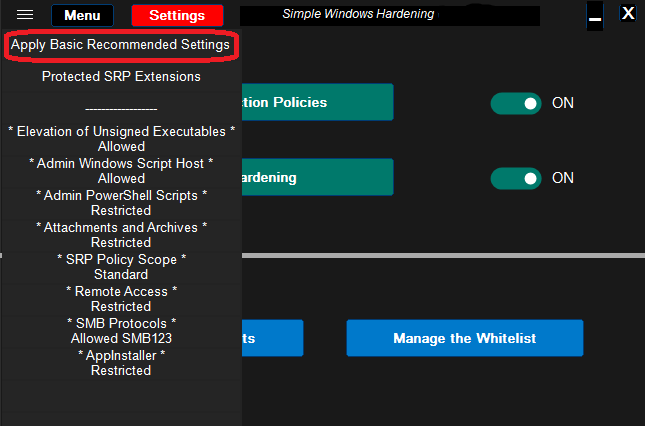
The above settings are installed by default. They are recommended if MS Office and Adobe Acrobat Reader are not installed.
If MS Office and Adobe Acrobat Reader DC are installed then additional hardening is recommended via the DocumentsAntiExploit tool.
# SOFTWARE INCOMPATIBILITIES
SWH vs. ATTACKS IN THE WILD (examples of how SWH works):
In most cases, SWH blocks the attacks at the delivery stage, before the final payload could be dropped/executed.
Nobelium: Q&A - Simple Windows Hardening
Zloader: Q&A - Simple Windows Hardening
Log4Shell: Q&A - Simple Windows Hardening
GootLoader: Q&A - Simple Windows Hardening
Emotet: Q&A - Simple Windows Hardening
Warzone and AgentTesla: Q&A - Simple Windows Hardening
AsyncRAT: Q&A - Simple Windows Hardening
Shuckworm RATS: Q&A - Simple Windows Hardening
Muddywater: Q&A - Simple Windows Hardening
SolarMarker: Q&A - Simple Windows Hardening
BazarLoader: Q&A - Simple Windows Hardening
PPAM attack: Q&A - Simple Windows Hardening
HTML ---> ISO ---> scripts: Q&A - Simple Windows Hardening
Hermetic Wiper: Q&A - Simple Windows Hardening
Asylum Ambuscade spear-phishing: Q&A - Simple Windows Hardening
Quakbot: Q&A - Simple Windows Hardening
Vidar infostealer: Q&A - Simple Windows Hardening (RunBySmartscreen)
Emotet: Q&A - Simple Windows Hardening
IceID (Cobalt Strike, Quantum ransomware): Q&A - Simple Windows Hardening
Fileless RAT (CHM file): Q&A - Simple Windows Hardening
SocGholish: Q&A - Simple Windows Hardening
TA551 phishing campaigns: Q&A - Simple Windows Hardening
GuLoader: Q&A - Simple Windows Hardening (RunBySmartscreen)
Follina exploit: Q&A - Simple Windows Hardening
AstraLocker 2.0: Q&A - Simple Windows Hardening
Raspberry Robin worm: Q&A - Simple Windows Hardening
Magniber (CPL variant): Q&A - Simple Windows Hardening
Batloader (MSI PowerShellScriptInline custom action): Question - Simple Windows Hardening
SWH works with Windows 10 and 11 (all versions including 24H2)
SWH ver. 2.1.1.1 - July 2023 (added support for Windows 11 ver. 22H2)
SWH ver. 2.0.0.1 - August 2022 (no support for Windows 11 ver. 22H2)
https://github.com/AndyFul/Hard_Configurator/raw/master/Simple Windows Hardening/SimpleWindowsHardening_2001.zipWindows 11 ver. 22H2 (fresh installation) turns off by default Software Restriction Policies. So, SimpleWindowsHardening ver. 2.0.0.1 (and prior) cannot use the SWH options related to SRP. This issue is corrected in version 2.1.1.1. It can also work with enabled Smart App Control.
Microsoft documentation for Software Restriction Policies (July 2021):

Software Restriction Policies Technical Overview
Learn about software restriction policies, when and how to use the feature, and what changes have been implemented in past releases.
learn.microsoft.com
Overview
Simple Windows Hardening (SWH) works on Windows Home and Pro editions. It is a portable application that allows configuring Windows built-in features to support antivirus and prevent fileless malware. SWH is adjusted to the home environment. After the initial configuration, it can be closed and all protection comes from the Windows built-in features.
SWH is based on Software Restriction Policies (SRP) and some useful Windows Policies. Users on Windows 11 should bear in mind that Microsoft stopped the development of SRP a few years ago. One cannot exclude the possibility that some problems related to SRP may arise in the future on Windows 11. It is also possible that Microsoft will remove SRP on Windows 12. SWH is tested via the Windows Insider program, so any possible problem is recognized in advance and reported on the Dev. Website.
The security setup is adjusted to keep usability and prevent fileless malware in the home environment. So, the EXE and MSI files are not restricted in SWH, except when executed from archives and email clients. But non-executable files like scripts, shortcuts, and other files with unsafe extensions are restricted. Such a setup can be very efficient because nowadays, many initial vectors of attack are performed via non-executable files.
The more sophisticated attack, the fewer chances that AV can detect it, but the greater chances that SWH can prevent it.
The restrictions made by SWH can be switched OFF/ON by using two switches on the right of the green buttons: <Software Restriction Policies> and <Windows Hardening>. In the OFF position, the restrictions are remembered and next removed - Windows default settings are applied for previously restricted features. When switching ON, the remembered settings are restored. Furthermore, in the ON position, the configurable settings can be changed by the user from the Settings menu.
# THE EXE / MSI 0-DAY MALWARE
The SWH application does not apply restrictions to EXE and MSI files, because these files are often used to install/update applications. Nowadays, many antivirus solutions have very good detection of such files, as compared to the detection of scripts. But still, the antivirus proactive features can have a problem with 0-day malware. In the home environment, the main delivery vectors of 0-day malware are spam emails and flash drives (USB drives).
The user has to be very careful when running EXE/MSI files originating from:
- Internet web links embedded in the emails.
- Attachments embedded in the emails.
- Flash drives (USB drives) shared with other people.
RunBySmartscreen is available as a part of Hard_Confugurator Hardening Tools (together with ConfigureDefender and FirewallHardening): ConfigureDefender/H_C_HardeningTools at master · AndyFul/ConfigureDefender
# QUICK CONFIGURATION
- Run SWH - the restrictions are automatically configured.
- Log OFF the account or reboot is required, depending on what restrictions were applied in SWH.
- If MS Office (or Adobe Acrobat Reader) is installed, then it is recommended to apply additional hardening by using the DocumentsAntiExploit tool. More info can be found in the "DocumentsAntiExploit tool - Manual".
# RECOMMENDED SETTINGS
The above settings are installed by default. They are recommended if MS Office and Adobe Acrobat Reader are not installed.
If MS Office and Adobe Acrobat Reader DC are installed then additional hardening is recommended via the DocumentsAntiExploit tool.
- Recommended settings for Microsoft Defender with ConfigureDefender HIGH Protection Level:
- Otherwise:
# SOFTWARE INCOMPATIBILITIES
- Software Restriction Policies (SRP) used in SWH may conflict with SRP introduced via Group Policy Object (GPO), available in Windows Pro, Education, and Enterprise editions. Before using SWH, the SRP has to be removed from GPO.
- Caution is required when applying policies via GPO on Windows 11 - this can turn OFF the SRP. So, after each GPO session, it is necessary to run and close SWH, which will automatically turn ON the SRP again (Windows restart is required).
- SWH can also conflict with any software that uses SRP, but such applications are rare (CryptoPrevent, SBGuard, AskAdmin). Before using SWH, the conflicting application should be uninstalled.
- It is not recommended to use SWH alongside WindowsHybridHardening and Hard_Configurator. These applications share several settings, which can lead to misconfigurations.
- Windows built-in Software Restriction Policies (SRP) are incompatible with AppLocker. Any active AppLocker rule introduced via GPO or MDM WMI Bridge, turns off SRP. When running SWH, it checks for active AppLocker rules and alerts about the issue.
- The Child Account activated via Microsoft Family Safety also uses AppLocker (via MDM), so SRP cannot work with it. This issue is persistent even after removing the Child Account because (due to a bug) the AppLocker rules are not removed. To recover SRP functionality, one must remove the AppLocker rules manually from the directory %Windir%\System32\AppLocker.
SWH vs. ATTACKS IN THE WILD (examples of how SWH works):
In most cases, SWH blocks the attacks at the delivery stage, before the final payload could be dropped/executed.
Nobelium: Q&A - Simple Windows Hardening
Zloader: Q&A - Simple Windows Hardening
Log4Shell: Q&A - Simple Windows Hardening
GootLoader: Q&A - Simple Windows Hardening
Emotet: Q&A - Simple Windows Hardening
Warzone and AgentTesla: Q&A - Simple Windows Hardening
AsyncRAT: Q&A - Simple Windows Hardening
Shuckworm RATS: Q&A - Simple Windows Hardening
Muddywater: Q&A - Simple Windows Hardening
SolarMarker: Q&A - Simple Windows Hardening
BazarLoader: Q&A - Simple Windows Hardening
PPAM attack: Q&A - Simple Windows Hardening
HTML ---> ISO ---> scripts: Q&A - Simple Windows Hardening
Hermetic Wiper: Q&A - Simple Windows Hardening
Asylum Ambuscade spear-phishing: Q&A - Simple Windows Hardening
Quakbot: Q&A - Simple Windows Hardening
Vidar infostealer: Q&A - Simple Windows Hardening (RunBySmartscreen)
Emotet: Q&A - Simple Windows Hardening
IceID (Cobalt Strike, Quantum ransomware): Q&A - Simple Windows Hardening
Fileless RAT (CHM file): Q&A - Simple Windows Hardening
SocGholish: Q&A - Simple Windows Hardening
TA551 phishing campaigns: Q&A - Simple Windows Hardening
GuLoader: Q&A - Simple Windows Hardening (RunBySmartscreen)
Follina exploit: Q&A - Simple Windows Hardening
AstraLocker 2.0: Q&A - Simple Windows Hardening
Raspberry Robin worm: Q&A - Simple Windows Hardening
Magniber (CPL variant): Q&A - Simple Windows Hardening
Batloader (MSI PowerShellScriptInline custom action): Question - Simple Windows Hardening
Attachments
Last edited: