Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,142
Windows Hybrid Hardening. (updated in October 2023)
https://github.com/AndyFul/Hard_Con...dowsHybridHardening/WHHLight_Package_1004.exe
The link to the WHHLight website:
https://github.com/AndyFul/Hard_Configurator/tree/master/WindowsHybridHardening
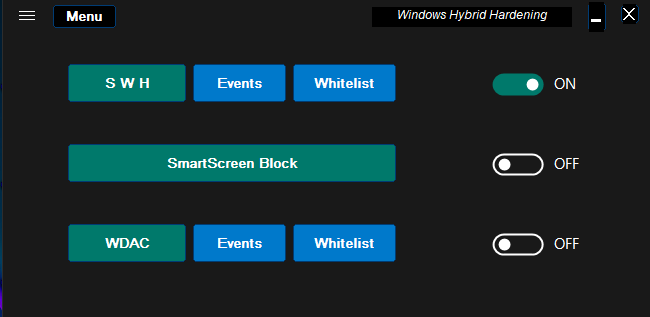
WindowsHybridHardening Light (WHHLight) works on Windows 10/11 (Home and Pro editions). It is a successor of SimpleWindowsHardening.
WHHLight is a simplified configurator of Windows built-in application control features: SmartScreen, Software Restriction Policies (SRP), and Windows Defender Application Control (WDAC). After initial configuration, it can be closed, and all protection comes from the Windows built-in features.
WHHLight can work with any antivirus - Microsoft Defender is not required but can be recommended with the ConfigureDefender tool.
WHHLight is adjusted to the home environment. SRP is still the best Windows built-in solution at home to prevent fileless attack vectors via scripts, shortcuts, and other non-PE files with active content. WDAC is the best prevention against malicious PE files (EXE, DLL, etc.) and MSI packages.
The hybrid of SRP and WDAC simplifies proper whitelisting. The folder whitelisted in WDAC allows only EXE, DLL, and MSI files but not scripts and other file types.
Some important post-exploitation mitigations of vulnerable applications (MS Office, Adobe Acrobat Reader, etc.) can be configured via DocumentsAntiExploit, FirewallHardening, and ConfigureDefender (tools included in the WHHLight installation package). The ConfigureDefender tool can be used only when Microsoft Defender real-time protection is enabled.
https://github.com/AndyFul/Hard_Con...dowsHybridHardening/WHHLight_Package_1004.exe
The link to the WHHLight website:
https://github.com/AndyFul/Hard_Configurator/tree/master/WindowsHybridHardening
WindowsHybridHardening Light (WHHLight) works on Windows 10/11 (Home and Pro editions). It is a successor of SimpleWindowsHardening.
WHHLight is a simplified configurator of Windows built-in application control features: SmartScreen, Software Restriction Policies (SRP), and Windows Defender Application Control (WDAC). After initial configuration, it can be closed, and all protection comes from the Windows built-in features.
WHHLight can work with any antivirus - Microsoft Defender is not required but can be recommended with the ConfigureDefender tool.
WHHLight is adjusted to the home environment. SRP is still the best Windows built-in solution at home to prevent fileless attack vectors via scripts, shortcuts, and other non-PE files with active content. WDAC is the best prevention against malicious PE files (EXE, DLL, etc.) and MSI packages.
The hybrid of SRP and WDAC simplifies proper whitelisting. The folder whitelisted in WDAC allows only EXE, DLL, and MSI files but not scripts and other file types.
Some important post-exploitation mitigations of vulnerable applications (MS Office, Adobe Acrobat Reader, etc.) can be configured via DocumentsAntiExploit, FirewallHardening, and ConfigureDefender (tools included in the WHHLight installation package). The ConfigureDefender tool can be used only when Microsoft Defender real-time protection is enabled.
Last edited:

