Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
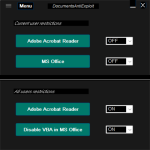
I know, but the many suppliers I work with still sent files in the old format probably for compatibility reasons or maybe because they use an alternative to MS Office.Gandalf_The_Grey,
What is the source of .xls documents? This is a legacy format from the era before MS Office 2007.
The last part I don't know.