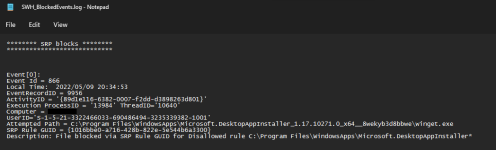
Does SWH works with O&O ShutUp 10, WPD etc?
I was looking at the readme file of WPD a while ago and saw the below (a snapshot)
### List of buttons ###
* **Local Group Policy**
* CEIPEnable - Windows Customer Experience Improvement Program
* DisableCustomerImprovementProgram - Internet Explorer Customer Experience Improvement Program
* CEIP - Windows Messenger Customer Experience Improvement Program
* AllowCortana - Allow Cortana
* AllowSearchToUseLocation - Allow search and Cortana to use location
* WindowsErrorReporting - Windows Error Reporting
* DisableUAR - Steps Recorder
* DisableInventory - Inventory Collector
* AllowTelemetry - Telemetry
* RestrictImplicitCollection - Handwriting automatic learning
* AllowInputPersonalization - Input personalization / Allow users to enable online speech recognition services
* AllowLinguisticDataCollection - Improve inking and typing recognition
* ScenarioExecutionEnabled - PerfTrack
* DisableQueryRemoteServer - Microsoft Support Diagnostic Tool
* AdvertisingInfo - Advertising ID
* DisableContentFileUpdates - Search Companion
* DisableWindowsConsumerFeatures - Microsoft consumer experiences
*
* **MS Office Local Group Policy**
* qmenable - Customer Experience Improvement Program
* sendtelemetry - Send Telemetry
* sendcustomerdata - Send personal information
*
* **Microsoft Edge (Chromium) Local Group Policy**
* AddressBarMicrosoftSearchInBingProviderEnabled - Enable Microsoft Search in Bing suggestions in the address bar
* AlternateErrorPagesEnabled - Suggest similar pages when a webpage can't be found
* AutofillAddressEnabled - Enable AutoFill for addresses
* AutofillCreditCardEnabled - Enable AutoFill for credit cards
* NetworkPredictionOptions - Enable network prediction
* PersonalizationReportingEnabled - Allow personalization of ads, search and news by sending browsing history to Microsoft
I believe those are Local Group Policy settings. I assume O&O ShutUp 10 and similar privacy tools also work alike.
So, am I right to say SWH will have problems working with these softwares since SWH works on SRP? Or such privacy tools are doing part of SWH is doing so not needed?
Thanks
I was looking at the readme file of WPD a while ago and saw the below (a snapshot)
### List of buttons ###
* **Local Group Policy**
* CEIPEnable - Windows Customer Experience Improvement Program
* DisableCustomerImprovementProgram - Internet Explorer Customer Experience Improvement Program
* CEIP - Windows Messenger Customer Experience Improvement Program
* AllowCortana - Allow Cortana
* AllowSearchToUseLocation - Allow search and Cortana to use location
* WindowsErrorReporting - Windows Error Reporting
* DisableUAR - Steps Recorder
* DisableInventory - Inventory Collector
* AllowTelemetry - Telemetry
* RestrictImplicitCollection - Handwriting automatic learning
* AllowInputPersonalization - Input personalization / Allow users to enable online speech recognition services
* AllowLinguisticDataCollection - Improve inking and typing recognition
* ScenarioExecutionEnabled - PerfTrack
* DisableQueryRemoteServer - Microsoft Support Diagnostic Tool
* AdvertisingInfo - Advertising ID
* DisableContentFileUpdates - Search Companion
* DisableWindowsConsumerFeatures - Microsoft consumer experiences
*
* **MS Office Local Group Policy**
* qmenable - Customer Experience Improvement Program
* sendtelemetry - Send Telemetry
* sendcustomerdata - Send personal information
*
* **Microsoft Edge (Chromium) Local Group Policy**
* AddressBarMicrosoftSearchInBingProviderEnabled - Enable Microsoft Search in Bing suggestions in the address bar
* AlternateErrorPagesEnabled - Suggest similar pages when a webpage can't be found
* AutofillAddressEnabled - Enable AutoFill for addresses
* AutofillCreditCardEnabled - Enable AutoFill for credit cards
* NetworkPredictionOptions - Enable network prediction
* PersonalizationReportingEnabled - Allow personalization of ads, search and news by sending browsing history to Microsoft
I believe those are Local Group Policy settings. I assume O&O ShutUp 10 and similar privacy tools also work alike.
So, am I right to say SWH will have problems working with these softwares since SWH works on SRP? Or such privacy tools are doing part of SWH is doing so not needed?
Thanks
Last edited: