Ransomware Prevention
- BEST Ransomware Prevention
Blaze's Security Blog: bartblaze.blogspot.fr: Blaze's Security Blog: Ransomware Prevention
Ransomware doesn't need any introduction anymore: we've all come to know (and unfortunately in some cases, experience) what it does and how it works. In short: this specific malware will encrypt your (personal) files and requires you to pay a certain monetary amount (hence the name 'ransom'ware) to regain access to your files. Nowadays, most ransomware will ask you to pay in Bitcoin.
Other names: CryptoLocker, cryptoware, encrypting ransomware.
This blog post is split up in two parts: 1 for users, 1 for companies/businesses. Most tips however are interchangeable and can be applied on most environments (we're talking Windows here).
Finally, some tools are proposed as well as additional resources.
Translations are available in Dutch, French and Korean. If you'd like to translate in your own language, contact me.
Users
Companies
In companies, the same tips as mentioned above are applicable as well. Most of those tips can be applied without too much hassle using Group Policies (GPO).
Additionally:
Tools
Browser:
Avoid using Internet Explorer or Edge - other browser are more 'customizable', which means you can have some extra protection with an add-on or extension. (however, don't forget to keep these up-to-date as well)
Activate click-to-play for plugins (such as Flash or Silverlight)
uBlock Origin (Chrome)
uBlock Origin (Firefox)
NoScript
Block the execution of scripts:
Remediate VBS Worm (option D)
Script Defender
CryptoPrevent Malware Prevention:
CryptoPrevent Malware Prevention
Java:
Why should I uninstall older versions of Java from my system?
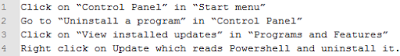
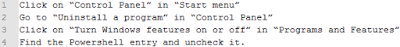
Disable PowerShell:
Resources
Backups:
Back up and restore: frequently asked questions
Office:
Enable or disable ActiveX controls in Office documents
Block or unblock external content in Office documents
Enable or disable macros in Office files
Using GPO:
2007 Office system (SP2) Administrative Template files (ADM, ADMX, ADML) and Office Customization Tool
Office 2010 Administrative Template files (ADM, ADMX/ADML) and Office Customization Tool download
Office 2013 Administrative Template files (ADMX/ADML) and Office Customization Tool
Office 2016 Administrative Template files (ADMX/ADML) and Office Customization Tool
Identify ransomware:
ID Ransomware
List of ransomware, both known & unknown:
Ransomware Overview
No More Ransom project (decrypters etc.):
The No More Ransom Project
Ransomware extra information:
Ransomware: a Q&A
Windows File Sharing:
Understanding Windows Server 2008 File and Folder Ownership and Permissions
Windows Script Host (WSH):
Disabling Windows Script Host
WMI permissions and restrictions:
Managing WMI security

Email ThisBlogThis!Share to TwitterShare to FacebookShare to Pinterest
- BEST Ransomware Prevention
Blaze's Security Blog: bartblaze.blogspot.fr: Blaze's Security Blog: Ransomware Prevention
Ransomware doesn't need any introduction anymore: we've all come to know (and unfortunately in some cases, experience) what it does and how it works. In short: this specific malware will encrypt your (personal) files and requires you to pay a certain monetary amount (hence the name 'ransom'ware) to regain access to your files. Nowadays, most ransomware will ask you to pay in Bitcoin.
Other names: CryptoLocker, cryptoware, encrypting ransomware.
This blog post is split up in two parts: 1 for users, 1 for companies/businesses. Most tips however are interchangeable and can be applied on most environments (we're talking Windows here).
Finally, some tools are proposed as well as additional resources.
Translations are available in Dutch, French and Korean. If you'd like to translate in your own language, contact me.
Users
- Use, depending on the mailclient, a robust anti-spam filter. In all online services (Outlook.com, Gmail, ...) an anti-spam filter is offered by default.
- Never open attachments from an unknown sender.
- Disable the execution of macros in Office.
- Disable Windows Script Host. You can use option D in my tool for example.
- Disable Powershell. You can do this via Control Panel > Programs > Turn Windows features on or off.
- Use a robust antivirus/antimalware and firewall solution and keep it up-to-date and running.
- Always install all relevant Windows updates.
- Remove all outdated Java versions, or remove Java completely if possible.
- Remove SilverLight if possible.
- Remove Flash if possible. If not:
Activate click-to-play for Flash in your browser. This depends on your browser.
(see Resources section) - Install an adblocker in your browser, for example uBlock Origin.
- A freeware program called CryptoPrevent is available as well. This will automatically improve protection for ransomware by, for example, monitoring known locations where ransomware will execute from.
Last but not least, the two most important rules are: - Always think twice before clicking on a link or opening an attachment.
- Create backups on a regular basis! Don't forget to disconnect your external hard drive afterwards. A word of warning: be careful when backing up to the cloud - once you notice you are infected, immediately terminate the network/internet connection or shut down the machine to prevent further encryption of your files.
Also test if your backup is functional by restoring some (test)files. A backup is always the best option for restoring your files, but you have to know the backup has succeeded and as such is functional.
Companies
In companies, the same tips as mentioned above are applicable as well. Most of those tips can be applied without too much hassle using Group Policies (GPO).
Additionally:
- Always use strong passwords for your servers (regardless if it's a domain controller, fileserver, etc...).
- Always install all relevant Windows updates.
- If possible, disable RDP. If not possible, use a robust firewall solution (hardware) which has VPN. Use strong passwords/authentication for those as well.
- Disable administrator-rights for normal users. Most of users with a company laptop shouldn't be able to install programs anyway (at least in theory).
- Disable, via GPO, the use of macro's in Office if possible. If not possible, only allow digitally signed macro's. Disable Windows Script Host and make the use of antivirus mandatory.
- Install antivirus on all machines in the network and especially for those users with a company laptop which they can/may take home as well.
- If present, activate the option to also scan archives (ZIP, RAR, ...) by the antivirus.
- Install a robust anti-spam solution and prohibit the use of attachments with dangerous extensions such as .exe, .scr, .... However, also block scriptlets, such as JavaScript files (.js).
- Verify the file sharing permissions of your users. Try to be as efficient as possible - a user belonging to group X is not related to group Y or its share at all? Prohibit or restrict access - use ACLs for example.
- Inform users about the dangers of opening attachments from unknown senders, or clicking on links randomly everywhere. Education is important as well. Also, have a plan of action ready (procedures) when a malware-infection (ransomware or otherwise) would happen.
- Consider changing the default action of potentially malicious scripts and their associated extensions, to notepad for example. This is rather trivial to implement with GPO. More information on changing a default action is here and here.
Example of extensions to change are:
.js, .jse, .wsc, .wsh, .wsf, .sct, .vbe, .cmd and .hta.
You may additionally add: .ps1, .vbs and .bat, granted you don't use these scriptlets.
Always test on one or several machine first, before deploying on your whole network. - Use policies to prohibit executable files running from specific locations. See here.
- Consider restricting the use of WMI. See here.
Last but not least, the two most important rules are: - 'Failing to prepare is preparing for failure':
Prevention is more important than removal/disinfection. - Create backups on a regular basis! Don't forget to disconnect your external hard drive afterwards. A word of warning: be careful when backing up to the cloud - once you notice you are infected, immediately terminate the network/internet connection or shut down the machine to prevent further encryption of your files.
Also test if your backup is functional by restoring some (test)files. A backup is always the best option for restoring your files, but you have to know the backup has succeeded and as such is functional.
Tools
Browser:
Avoid using Internet Explorer or Edge - other browser are more 'customizable', which means you can have some extra protection with an add-on or extension. (however, don't forget to keep these up-to-date as well)
Activate click-to-play for plugins (such as Flash or Silverlight)
uBlock Origin (Chrome)
uBlock Origin (Firefox)
NoScript
Block the execution of scripts:
Remediate VBS Worm (option D)
Script Defender
CryptoPrevent Malware Prevention:
CryptoPrevent Malware Prevention
Java:
Why should I uninstall older versions of Java from my system?
Disable PowerShell:
Resources
Backups:
Back up and restore: frequently asked questions
Office:
Enable or disable ActiveX controls in Office documents
Block or unblock external content in Office documents
Enable or disable macros in Office files
Using GPO:
2007 Office system (SP2) Administrative Template files (ADM, ADMX, ADML) and Office Customization Tool
Office 2010 Administrative Template files (ADM, ADMX/ADML) and Office Customization Tool download
Office 2013 Administrative Template files (ADMX/ADML) and Office Customization Tool
Office 2016 Administrative Template files (ADMX/ADML) and Office Customization Tool
Identify ransomware:
ID Ransomware
List of ransomware, both known & unknown:
Ransomware Overview
No More Ransom project (decrypters etc.):
The No More Ransom Project
Ransomware extra information:
Ransomware: a Q&A
Windows File Sharing:
Understanding Windows Server 2008 File and Folder Ownership and Permissions
Windows Script Host (WSH):
Disabling Windows Script Host
WMI permissions and restrictions:
Managing WMI security
Email ThisBlogThis!Share to TwitterShare to FacebookShare to Pinterest
Last edited: