Good advice. Was just making sure the person who I was talking to covered the basicsRemember that if the vault is stolen, there is no 2FA that can holds. The only thing that protects the vault is the master password.
~LDogg
Good advice. Was just making sure the person who I was talking to covered the basicsRemember that if the vault is stolen, there is no 2FA that can holds. The only thing that protects the vault is the master password.
Making sure you have a strong master password is most likely the best thing you can do right now.Is it safe to just stay with Bitwarden or should i switch to Dashlane/1Password?
BTW i set my KDF Iteration from 100.000 to 700.000, but is that enough at all?
If on devices you find Bitwarden to be slow, you should decrease it slightly, as some devices may not cope with that much of iterations.
Yes, I’d say so. In my blog post I recommend setting a strong master password however. Note that the “strong” indicator on Bitwarden’s account creation page doesn’t necessarily indicate a strong password. I recommend using a randomly generated passphrase (using diceware for example).Is it safe to just stay with Bitwarden or should i switch to Dashlane/1Password?
If you have financial availability to pay, need a simple service with nothing management and need integration with various devices, yes, 1P is probably the most appropriate choice.Is it safe to just stay with Bitwarden or should i switch to Dashlane/1Password?
BTW i set my KDF Iteration from 100.000 to 700.000, but is that enough at all?
Done the same, but increased the iterations to 600k as the new, new default:Some take backs about this as I can sense some are a little scared. (Makes sense)
1. Make a stronger master password
2. Enable 2FA
3. Increase iterations from the base you have to 350k as recommended via this forum & OWASP.
~LDogg

 malwaretips.com
malwaretips.com
There's no word on whether this is for new users only or on their back end for all users. Even so, I'll edit my original comment as the consensus is surely at 600k. Thanks again for your words of wisdom, sometimes we all learn from each other and that's what I love about this forum.Done the same, but increased the iterations to 600k as the new, new default:

Hot Take - Bitwarden Design Flaw : Server side iterations
The Master Password is stored on the server, the Secret Key is stored locally. Got it, thanks. It's worth using both. But Bitwarden only has the Master Password.malwaretips.com
dittoDone the same, but increased the iterations to 600k as the new, new default:

Hot Take - Bitwarden Design Flaw : Server side iterations
The Master Password is stored on the server, the Secret Key is stored locally. Got it, thanks. It's worth using both. But Bitwarden only has the Master Password.malwaretips.com

The LastPass data breach caused uproar amongst its users and the tech community, but there are several good things that happened in the aftermath of the incident. It actually taught users a lesson in security, don't take things for granted.
It was a wake-up call for many, a rude one, yes, but it has made people think twice about their password storage methods, alternatives they can migrate to, and also to learn more about the settings that they can tweak to improve their password manager's security.
One component which gained a lot of attention was the password iterations count. Amongst other weak points in the attack, LastPass was found to have set the iterations to a low count, which is considered an insecure practice. More recently, Bitwarden users raised their voices asking the company to not make the same mistake as its rival. Bitwarden responded to their requests and has decided to increase the iterations to 600,000, as recommended by OWASP. You can set the value manually by referring to this article.
Let's dig a little deeper about password iterations. There are many types of Key Derivation Functions (KDFs), the most commonly used cryptographic algorithm is PBKDF2, which is the one that's recommended by the National Institute of Standards and Technology (NIST). Bcrypt is used by many websites. PBKDF2 uses SHA256 (and SHA512) for hashing and salting the passwords. The higher the number of iterations, the slower it is to run password guesses and breach a vault.
While it can be a good layer of safety, it is actually the weakest version of the KDF versions. It's not necessarily bad, but there are better ones such as Scrypt, Bcrypt, and Argon2. Argon2 is resistant to ASIC and GPU based attacks, and is considered the best of the lot.
PBKDF2 AES iterations relies on a high number of iterations to hash the passwords in an effort to deliberately slow the attacks. With 600,000 it will take a long time to brute-force a vault, and can be taxing on the CPU. Argon2 not only slows down this threat, but also consumes memory for running passes, and it also has a degree of parallelism that is determined by the number of CPU cores/threads. Let's just say it's a lot more expensive for a hacker both in terms of time and resources to attack an Argon2 encrypted database.
You may read more about it at its GitHub page, and on OWASP. This isn't a new request, Bitwarden users have been asking for Argon2 support since 2017 (and 2018), but the idea has only come to fruition now. Quexten, the developer who contributed the code for Argon2 support, agreed to another user's suggestion that Bitwarden would not have expedited the process now if it had not been for the recent LastPass data breach. Here is the pull request for the feature.
There are three types/versions of Argon2: Argon2d, Argon2i and Argon2id. The first one, Argon2d, is resistant to GPU based cracking attacks, but is vulnerable to side-channel attacks. Argon2i is the opposite, its strong against side-channel threats, but is prone to GPU attacks. Argon2id is a hybrid of the two, and as a result offers the best of both worlds.
Bitwarden's implementation will use Argon2id. With PBKDF users have just one parameter that they can control, to set the number of iterations. Argon2 will offer more options, you will be able to set the number of iterations, the amount of memory to use, for example 64MB, and Parallelism lets you define the number of parallel threads to be used.
According to comments posted by Quexten at Bitwarden's community forums, the company has a 5-week release cycle, so we could expect Argon2 support to be added next month on all platforms if the tests are successful. The feature will be opt-in, and should be available on the same page as the password iteration settings in Bitwarden's web vault.
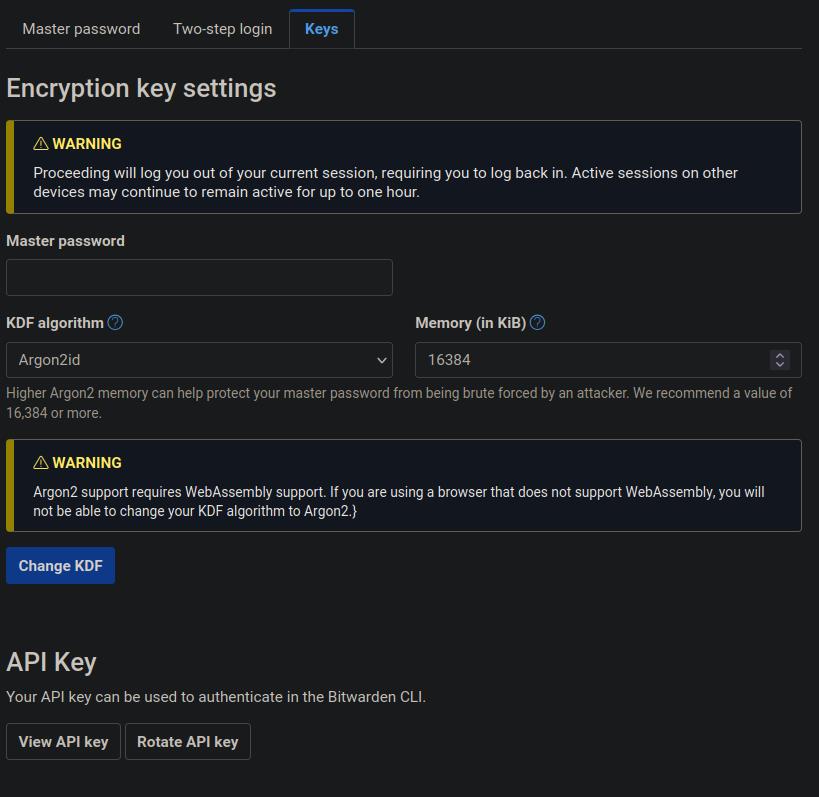
In that case do I have to increase the KDF interactions to 600000? Mine is already 100000.Bitwarden to increase its server-side iterations to 600,000; here's how to set it manually:

How to change the KDF iterations count in Bitwarden Password Manager - gHacks Tech News
PSA: Here's how to change the server side iterations count in Bitwarden Password Manager to protect your account.www.ghacks.net
It would be more safe if you.In that case do I have to increase the KDF interactions to 600000? Mine is already 100000.
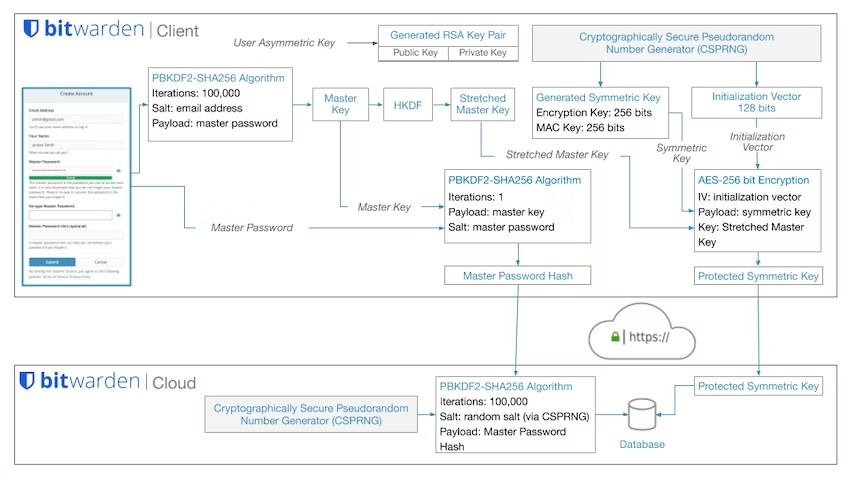
So what happens if some malicious actor happens to get a copy of the data, like it happened with LastPass? They will need to decrypt it. And for that, they will have to guess the master password. PBKDF2 is meant to slow down verifying whether a guess is correct.
Testing the guesses against the master password hash would be fairly slow: 200,001 PBKDF2 iterations here. But the attackers wouldn’t waste time doing that of course. Instead, for each guess they would derive an encryption key (100,000 PBKDF2 iterations) and check whether this one can decrypt the data.
This simple tweak removes all the protection granted by the server-side iterations and speeds up master password guessing considerably. Only the client-side iterations really matter as protection.
While I have set it to 600K I think it's better if you depended on a strong(er) password than just KDF iteration values. Argon2d (Dashlane uses it) will be an excellent change over..I dare say even an upgrade. I was experimenting with Keepass and its Argon2d KDF settings. I just can't help but be curious.In that case do I have to increase the KDF interactions to 600000? Mine is already 100000.
Yes, the master password used in all my PMs, are strong enough, even exaggerated enough, that it is boring when I type them, so I won't worry about KDF iteration values changing in Bitwarden. Waiting for the upgrade to Argon2d in Bitwarden. Yes, I also tested Argon2d in keepass, and it worked perfectly. Let's wait.While I have set it to 600K I think it's better if you depended on a strong(er) password than just KDF iteration values. Argon2d (Dashlane uses it) will be an excellent change over..I dare say even an upgrade. I was experimenting with Keepass and its Argon2d KDF settings. I just can't help but be curious.