Assuming I would need to do this within the browser extension correct?This is what I did:
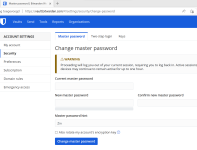
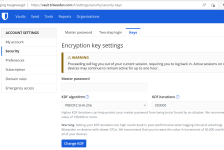
Changed the KDF iterations setting from the default 100,000 to the new default of 350,000.
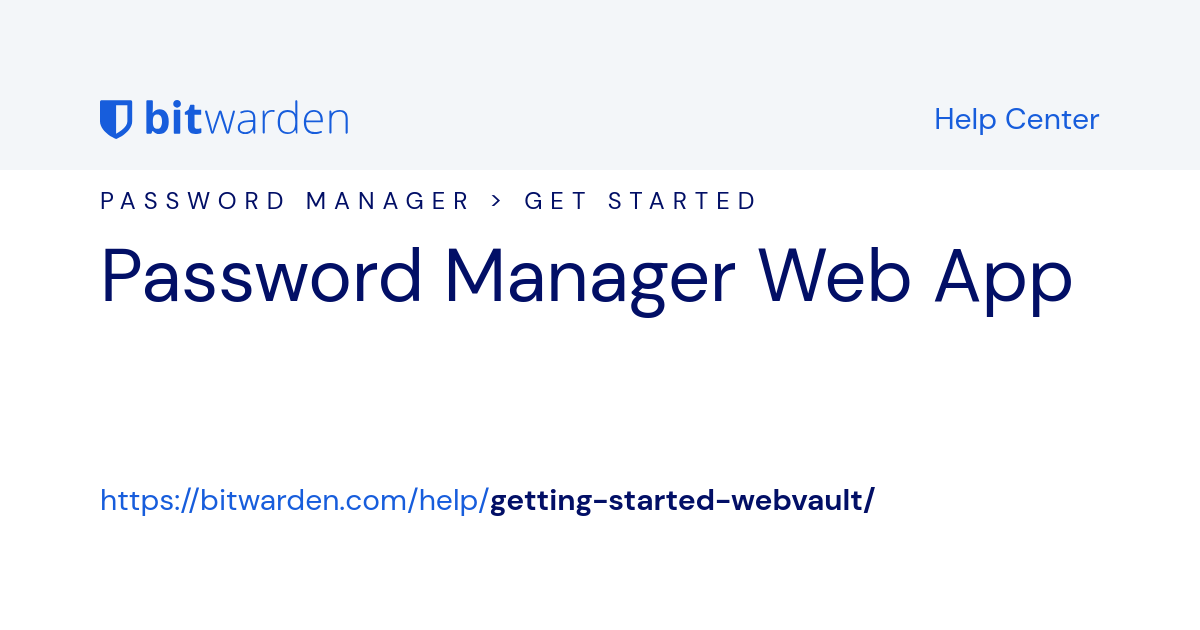
Changed my master password into a four random word passphrase.
2FA was already enabled.
~LDogg