Browser autofill profiles are a reliable phishing vector that allow attackers to collect information from users via hidden fields, which the browser automatically fills with preset personal information and which the user unknowingly sends to the attacker when he submits a form.
Autofill profiles are a recent addition to modern-day browsers. This feature works by allowing the user to create a profile that holds different details about himself that he usually enters inside web forms.
When the user has to fill in a form in the future, he can simply select an autofill profile and his browser will enter the preset information in all form fields, sparing the user the time he would have needed to type in 10, 20 or more fields.
Browser autofill profiles should not be confused with form field autofilling behavior, which allows a user to fill in one form field at a time with data he previously entered in those fields. Autofill profiles allow users to fill in entire forms with one click.
Autofill profiles facilitate phishing and reconnaissance attacks
Finnish web developer Viljami Kuosmanen has published yesterday a demo on GitHub that shows how an attacker could take advantage of browsers that support autofill profiles.
His demo, available here, is a simple web form. A user looking at this page will only see a Name and Email input field, along with a Submit button.
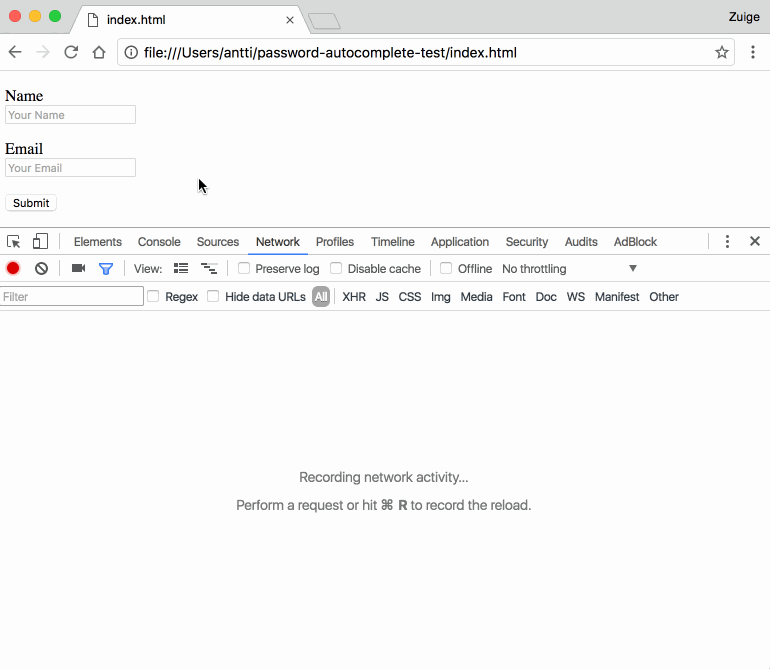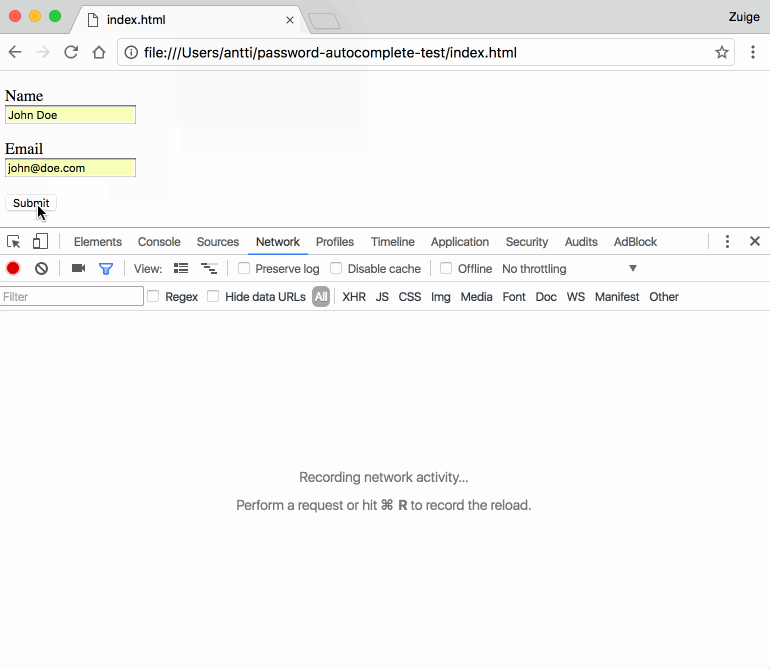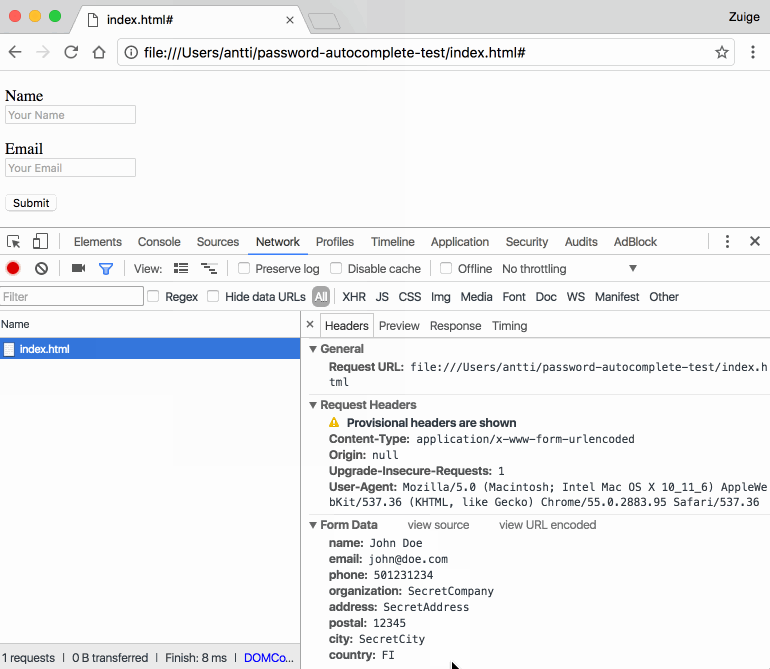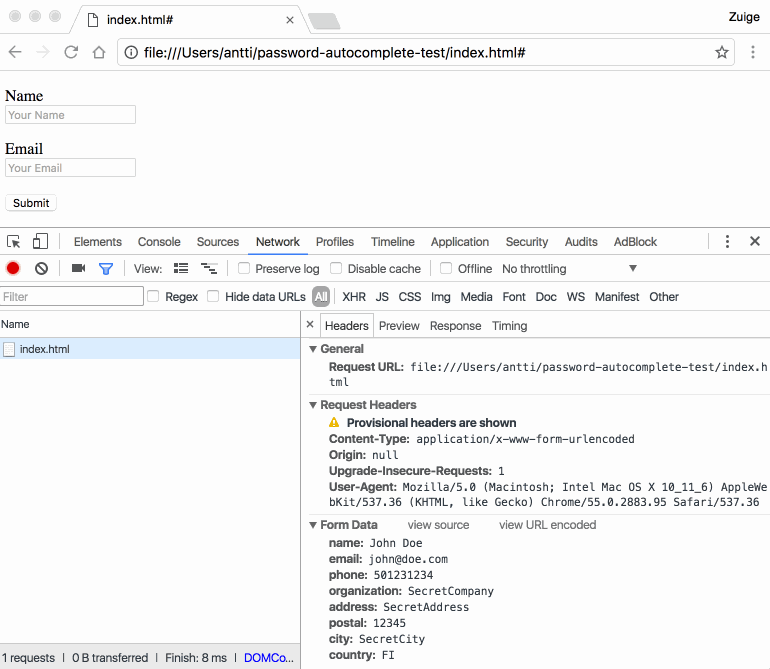
Unless the user looks at the page's source code, he won't know that the form also contains six more fields named Phone, Organization, Address, Postal Code, City, and Country.
If the user has an autofill profile set up in his browser, if he decides to autofill the two visible fields, the six hidden fields will be filled in as well, since they're part of the same form, even if invisible to the user's eye.
As you can imagine yourself, this presents a simple method that threat actors can use to collect all sorts of personal information about users, ranging from home addresses to phone numbers, and even credit card information, if the user saves this type of data in his autofill profile.
A dodgy form autofill has led the researcher down this rabbit hole
"I had known about this issue for a long time," Kuosmanen told Bleeping Computer today via email. "A similar thing (honeypots) is used to trap bots in forms to avoid spam. This is the same idea, just trap real browser users instead of bots."
"The idea for the demo came after I was annoyed about Chrome autofilling wrong fields on an ecommerce site. I then went on to see which details Chrome had saved for autofill about me and was surprised about how much information is available," Kuosmanen added.
Intrigued by Chrome's behavior, the developer says that he then experimented to see what was the range of form fields Chrome would fill in, and he eventually got the idea of testing hidden form fields.
"I thought it would be a good idea to demonstrate this issue as a gif and shared it on Twitter," Kuosmanen said.
During his tests, the developer discovered that Chrome had UI elements in place when a username or password was filled in, even inside a hidden field, but these didn't appear for the other fields.
Read more: Browser Autofill Profiles Can Be Abused for Phishing Attacks
Autofill profiles are a recent addition to modern-day browsers. This feature works by allowing the user to create a profile that holds different details about himself that he usually enters inside web forms.
When the user has to fill in a form in the future, he can simply select an autofill profile and his browser will enter the preset information in all form fields, sparing the user the time he would have needed to type in 10, 20 or more fields.
Browser autofill profiles should not be confused with form field autofilling behavior, which allows a user to fill in one form field at a time with data he previously entered in those fields. Autofill profiles allow users to fill in entire forms with one click.
Autofill profiles facilitate phishing and reconnaissance attacks
Finnish web developer Viljami Kuosmanen has published yesterday a demo on GitHub that shows how an attacker could take advantage of browsers that support autofill profiles.
His demo, available here, is a simple web form. A user looking at this page will only see a Name and Email input field, along with a Submit button.
Unless the user looks at the page's source code, he won't know that the form also contains six more fields named Phone, Organization, Address, Postal Code, City, and Country.
If the user has an autofill profile set up in his browser, if he decides to autofill the two visible fields, the six hidden fields will be filled in as well, since they're part of the same form, even if invisible to the user's eye.
As you can imagine yourself, this presents a simple method that threat actors can use to collect all sorts of personal information about users, ranging from home addresses to phone numbers, and even credit card information, if the user saves this type of data in his autofill profile.
A dodgy form autofill has led the researcher down this rabbit hole
"I had known about this issue for a long time," Kuosmanen told Bleeping Computer today via email. "A similar thing (honeypots) is used to trap bots in forms to avoid spam. This is the same idea, just trap real browser users instead of bots."
"The idea for the demo came after I was annoyed about Chrome autofilling wrong fields on an ecommerce site. I then went on to see which details Chrome had saved for autofill about me and was surprised about how much information is available," Kuosmanen added.
Intrigued by Chrome's behavior, the developer says that he then experimented to see what was the range of form fields Chrome would fill in, and he eventually got the idea of testing hidden form fields.
"I thought it would be a good idea to demonstrate this issue as a gif and shared it on Twitter," Kuosmanen said.

During his tests, the developer discovered that Chrome had UI elements in place when a username or password was filled in, even inside a hidden field, but these didn't appear for the other fields.
Read more: Browser Autofill Profiles Can Be Abused for Phishing Attacks