Advice Request CleanBrowsing DNS vs NextDNS vs ControlD DNS
- Thread starter SohanRay
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
I am not saying that you are wrong, but based on which tests are you stating that?But if you compare just the blocking malicious domains part, yeah Quad9 is definitely better.
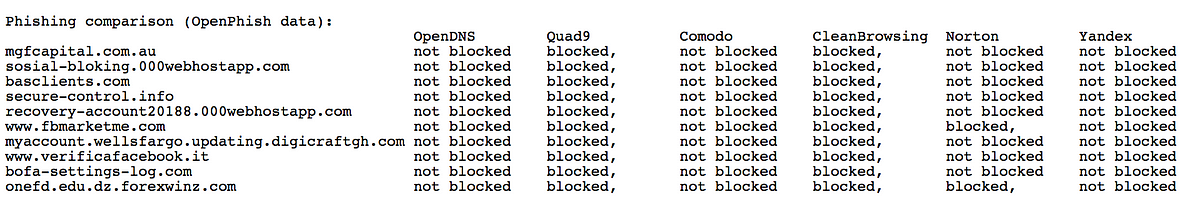
I have seen many test results over the Internet. Sometimes NextDns does well, sometimes CleanBrowsing does well. But Quad9 always does well no matter which test results you look at. Now you may say do your own testing and see. But the test results depends a lot on the sources you use to gather the malicious domains. What normal users can gather would be from public lists. Now NextDns uses public lists, so its more likely to shine. But lists from say cybersecurity firms would never be available to general people, if you had tested on their lists NextDns most probably would have done bad. Public lists have a lot of false positives. You'll find opendns not blocking most domains mentioned in Openphish (public list) which they themselves back and is a part of their own company initiative. Why? Its because they don't trust their own initiated source completely. Even Quad9 doesn't block a lot of domains from Openphish. Same reason. But if you see NextDns, it would probably block almost all of it if not all. So the thing is all NextDns has are those free public lists in their arsenal. And these lists are literally accessible by anyone. But the premium private ones are the ones accessible by only authorized entities. So all services using such premium private services, can easily use all or any of those public lists. Its pretty obvious. So now which one is bound to perform better? The answer is obvious right... Quad9 uses threat intel from so many leading cybersecurity companies on near real time basis. And also any vetted domains from public lists.I am not saying that you are wrong, but based on which tests are you stating that?
N
Not much really. They have been mostly inactive since quite some time I think. And all they have is those public blacklists which you can choose from like you can in nextdns in case of privacy, ads and trackers. They don't have any other added feature. So pretty lame basically. Their speeds were good though in my case. They have or had an email to contact them. But they never replied when I mailed them. So I have investigated them before and well, they didn't make it to this list of comparison at all. Its far behind.What you guys think about RethinkDNS?
Quad9 and NextDNS are really great I have tried both for long term testing as well. However I always go back to Cloudflare because they are consistently faster
at my specific location.
So depending on your location one DNS provider can be better than another.
This tool can be useful for checking which DNS providers are the best for your specific location.
at my specific location.
So depending on your location one DNS provider can be better than another.
This tool can be useful for checking which DNS providers are the best for your specific location.
If you don't mind, can you post some links to those tests?I have seen many test results over the Internet. Sometimes NextDns does well, sometimes CleanBrowsing does well. But Quad9 always does well no matter which test results you look at.
At least to get a clear idea of the differences.
Thats cool and all but just like @cryogent I would really like to see those tests results. Been trying to find stuff for a long time but never was able to find much more than Youtube tests about NextDNS.I have seen many test results over the Internet. Sometimes NextDns does well, sometimes CleanBrowsing does well. But Quad9 always does well no matter which test results you look at. Now you may say do your own testing and see. But the test results depends a lot on the sources you use to gather the malicious domains. What normal users can gather would be from public lists. Now NextDns uses public lists, so its more likely to shine. But lists from say cybersecurity firms would never be available to general people, if you had tested on their lists NextDns most probably would have done bad. Public lists have a lot of false positives. You'll find opendns not blocking most domains mentioned in Openphish (public list) which they themselves back and is a part of their own company initiative. Why? Its because they don't trust their own initiated source completely. Even Quad9 doesn't block a lot of domains from Openphish. Same reason. But if you see NextDns, it would probably block almost all of it if not all. So the thing is all NextDns has are those free public lists in their arsenal. And these lists are literally accessible by anyone. But the premium private ones are the ones accessible by only authorized entities. So all services using such premium private services, can easily use all or any of those public lists. Its pretty obvious. So now which one is bound to perform better? The answer is obvious right... Quad9 uses threat intel from so many leading cybersecurity companies on near real time basis. And also any vetted domains from public lists.
Well I don't think I can find all of them again. But lets see which ones I can.If you don't mind, can you post some links to those tests?
At least to get a clear idea of the differences.
(you'll have to scroll down in this one)
Phishing Protection — Comparing DNS Security Filters
I was reading an article from Brian Krebs about the Real Jokers Stash and the crazy stuff that goes into the darkweb / cybercrime forums…
 medium.com
medium.com

Quad9 - Wikipedia

This New Free Service Helps Keep Malware Off Your Computer
Keeping all your devices malware-free isn't always easy. Fortunately, there's a new tool that can help... and it's totally free.
 www.forbes.com
www.forbes.com
There are others too, but I can't find them now. Would require much time.
There it was properly explained that when we do tests for these filtering services the results entirely depend on the sources we use. The more close sources a service uses, the better its results are. So things can't be compared really based on such individual tests to that extent. You'll have to investigate the other aspects to be sure.
Last edited:
Well I don't think I can find all of them again. But lets see which ones I can.
(you'll have to scroll down in this one)

Phishing Protection — Comparing DNS Security Filters
I was reading an article from Brian Krebs about the Real Jokers Stash and the crazy stuff that goes into the darkweb / cybercrime forums…medium.com
(here it mentions about Quad9 being 97 percent effective)
Quad9 - Wikipedia
en.wikipedia.org

This New Free Service Helps Keep Malware Off Your Computer
Keeping all your devices malware-free isn't always easy. Fortunately, there's a new tool that can help... and it's totally free.www.forbes.com
There are others too, but I can't find them now. Would require much time.
There it was properly explained that when we do tests for these filtering services the results entirely depend on the sources we use. The more close sources a service uses, the better its results are. So things can't be compared really based on such individual tests to that extent. You'll have to investigate the other aspects to be sure.
Thanks for sharing. In the end none of those sources are stating that NextDNS is weaker in malware and phishing protection than Quad9 except in this twitter post from another DNS provider. In the Youtube video it even performed a little better than Quad9. I like Quad9 and NextDNS but just think that there are not enough trustworthy tests about NextDNS to judge its efficiency. Considering that most people would also add external blocklists like oisd or Energized it's hard to rate NextDNS anyway.
The main reason behind NextDns shining in most people's individual tests is that it entirely uses and depends on public free lists. And almost all individuals use the public free lists to test the filtering, because that is essentially what they can acquire without paying for a subscription fee.
So, its obvious that NextDns would shine in those tests. But that isn't the whole picture at all. So it doesn't prove NextDns is as good as it says or as some others say who did such tests of their own.
So, its obvious that NextDns would shine in those tests. But that isn't the whole picture at all. So it doesn't prove NextDns is as good as it says or as some others say who did such tests of their own.
You said that multiple times. But you are only talking about the Threat Intelligence Feeds of NextDNS. It has more than that.The main reason behind NextDns shining in most people's individual tests is that it entirely uses and depends on public free lists. And almost all individuals use the public free lists to test the filtering, because that is essentially what they can acquire without paying for a subscription fee.
So, its obvious that NextDns would shine in those tests. But that isn't the whole picture at all. So it doesn't prove NextDns is as good as it says or as some others say who did such tests of their own.
Yeah i know, NextDns isn't compared by its filtering much. It isn't that popular yet. Its shouldn't be hard to compare actually. There shouldn't be any lists added in the privacy section and all the other security features should be turned on and then tested.Thanks for sharing. In the end none of those sources are stating that NextDNS is weaker in malware and phishing protection than Quad9 except in this twitter post from another DNS provider. In the Youtube video it even performed a little better than Quad9. I like Quad9 and NextDNS but just think that there are not enough trustworthy tests about NextDNS to judge its efficiency. Considering that most people would also add external blocklists like oisd or Energized it's hard to rate NextDNS anyway.
By the way, there were 2 youtube videos. In one quad9 performed much better. And that one is the more reliable one.
Well except for 2 or 3 of other security features like dns rebinding protection, all other security features are also just based on some public blocklists only. If you investigate their Github repository, you'll know.You said that multiple times. But you are only talking about the Threat Intelligence Feeds of NextDNS. It has more than that.
And if you're talking about finding newly registered domains and AI... Well Quad9's partners have that too. Infact Quad9 is like using a dozen of such AI engines all combined effectively.
I did note that in one of the tests where NextDNS came out on top that they used OISD and it blocked 2 extra items that Quad9 didn't. Which was the difference in the test.Yeah i know, NextDns isn't compared by its filtering much. It isn't that popular yet. Its shouldn't be hard to compare actually. There shouldn't be any lists added in the privacy section and all the other security features should be turned on and then tested.
By the way, there were 2 youtube videos. In one quad9 performed much better. And that one is the more reliable one.
Yeah. And the other test was by lawrence systems.I did note that in one of the tests where NextDNS came out on top that they used OISD and it blocked 2 extra items that Quad9 didn't. Which was the difference in the test.
For me an adblocking DNS is more important because my AV and if required a reputable browser extension can help with blocking malicious domains. Blocking ad related domains via DNS also reduces bandwidth and improves browsing speed. So NextDNS is an easier choice for me with its adblocking and malicious domain blocking ability.
There's also Adguard DNS, which can block ads as well as malicious sites, but the later part isn't as effective.
There's also Adguard DNS, which can block ads as well as malicious sites, but the later part isn't as effective.
True, adblocking is really important for me too for the same reasons and also that I am too used to a clean experience . But instead of paying for that, I am using the controld free dns with malware and ad blocking alongside Bitdefender antivirus which has the web protection feature and scam alert security features.For me an adblocking DNS is more important because my AV and if required a reputable browser extension can help with blocking malicious domains. Blocking ad related domains via DNS also reduces bandwidth and improves browsing speed. So NextDNS is an easier choice for me with its adblocking and malicious domain blocking ability.
There's also Adguard DNS, which can block ads as well as malicious sites, but the later part isn't as effective.
Why ControlD? Well you can see this post:

ControlD doesn't seem to have an efficient system · Control D Feedback
Check this post–> https://help.nextdns.io/t/p8h54n9/nextdns-vs-controld-controld-has-a-problem
Well except for 2 or 3 of other security features like dns rebinding protection, all other security features are also just based on some public blocklists only. If you investigate their Github repository, you'll know.
And if you're talking about finding newly registered domains and AI... Well Quad9's partners have that too. Infact Quad9 is like using a dozen of such AI engines all combined effectively.
Thats a quote from the Quad9 website. They don't say who their TI partners are and they don't say anything about their AI driven threat detection. Wish they would be more transparent in that matter.Sources of Blocking Data
Quad9 partners with many threat intelligence (TI) sources, both commercial and public. These partners provide threat data to Quad9 as part of their missions to help reduce risk and cybercrime on the Internet and also because their partnership with Quad9 may help them improve their own ability to detect these risks. The combination of philanthropic sponsorship coupled with a virtuous feedback loop of detection improvement creates conditions in which Quad9 users benefit as the usage of the platform increases – more blocks mean increased improvement of blocking feedback.
TI partners supply Quad9 with information about domains or hosts that they believe should be blocked, and in turn the partners receive near-real-time feedback from Quad9 on the volumetric rates of the threats they list. This volumetric data allows them to understand the rising or falling status of various threatening campaigns and allows them to improve the lists of risky domains they provide to Quad9. Quad9 is exclusively a distribution tool for the threat data generated by partners – we do not generate our own set of domain-based Indicators of Compromise (IOCs) and, therefore, do not compete with our TI partners.
Typically Quad9 obtains malicious domains from around twenty difference TI sources. Many of these sources have broad malware detection capabilities and provide wide coverage against newly emerging domain threats. Some are more specific – they may, for example, target niche markets such as financial fraud, homoglyphs, network IDS past behaviors, phishing detectable by visual object recognition, optical character recognition (OCR), structure and linkages to other sites, or app-based spyware. This combination of extremely diverse TI provider expertise allows Quad9 to be more effective than any other DNS blocking system that relies upon only its own source of malware or fraud domain detection.
This model of donated data and cooperative improvement exists because Quad9 is a not-for-profit organization whose goals are specifically aligned with the security and privacy of our end users and not with the extraction of money from customers. Quad9 continually adds to and modifies the set of threat providers to extend more accurate and rapid threat-blocking abilities to our user community.
Thats what I said earlier. But why disabling such a feature when it's basically one of the advantages of NextDNS?I did note that in one of the tests where NextDNS came out on top that they used OISD and it blocked 2 extra items that Quad9 didn't. Which was the difference in the test.
Thats a quote from the Quad9 website. They don't say who their TI partners are and they don't say anything about their AI driven threat detection. Wish they would be more transparent in that matter.
Quad9 | A public and free DNS service for a better security and privacy
A public and free DNS service for a better security and privacy
You can find the partners here. Not all are listed. As they say, partners from sensitive industry like finance or Health aren't listed. You can go to the partners mentioned individual websites to find out more about them.
You may also like...
-
Battle How Adguard compares to NextDns and ControlD regarding blocking malicious domains?
- Started by Parkinsond
- Replies: 9
-
Poll Paid vs Free Antivirus in 2026: What are you using, and is it worth paying for?
- Started by Bot
- Replies: 96
-
Battle Chrome vs. Firefox vs. Edge in 2026 — Which Browser Should Home Users Trust?
- Started by Bot
- Replies: 275
-