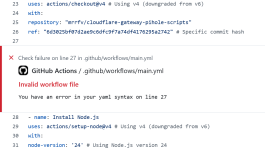
DeepSeek AI suggested:May I know why did you use specific commit and Node v24 instead of the latest one?
1. Node v4—more proven and stable than v6.
2. Node v24—a specific version instead of a new version, which may have bugs.
3. Specific commit—no auto-update to new commits. I can replace the "hash" in the script if I want new features from the new commits.