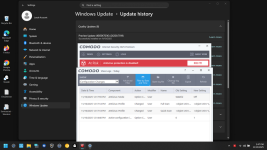
Finally, the issue has been identified. It was not Firewall but AV. I ran the test twice with the same result (Install error - 0x80070005).
The reported tests show that enabling/disabling other modules (HIPS, Auto-containment, VirusScope, Firewall, Script Analysis, Website Filtering) did not cause the KB5067036 update error. But whenever one of the disabled modules was the Antivirus module, the update failed.
In fact, the issue is quite similar to that from the OP (the same update KB5067036 and the same error). In my case (last two tests), I used CIS Proactive config with disabled HIPS and AV modules, which is almost the same setup as the Comodo Firewall config in the OP. However, I did not use the silent setup, and all tests were run on the default Admin account.
I also ran two additional tests with the installed Comodo Firewall application (Proactive config with disabled HIPS), and the KB5067036 failed as in the OP.
It is strange, but all of this suggests that the active AV component's absence may be the cause of the issue in both CIS and Comodo Firewall.