And even if you customize the Svchost (as you did in your post), at Comodo it can only be done in a generic way, for example, a simple “allow” “port: 53” (necessary for DNS) opens all comms for any malware.
Respectively, the rules for it can be more restrictive than this, as in my DNS rule I also restricted svchost to remote IP addresses cloudflare (1.1.1.1, 1.0.0.1).
I could have done the same, for example, for Windows time to remote port 123, and/or remote HTTP (port 80), but I chose not to. It is actually a lot of work to create rules like this for all running applications requiring network comms in any application firewall, including Windows firewall, but with a better interface, this work can be reduced. Windows firewall has the serious limitation of not supporting wildcards in path rules, and I seem to remember Comodo has a similar limitation - not quite the same - one that I posted elsewhere some time ago in another forum here:
The HIPS feature is only overkill if it's set up to be that way. That's true I guess, but I remember that old versions of Comodo gave me dumb alerts...

www.wilderssecurity.com
Keep in mind also with Comodo, that all settings once configured can be backed up and restored at any time if necessary.
Btw, even though in Comodo, svchost rules can not be tied to specific services it hosts, I believe this is not a security issue. That's because any svchost rule in comodo will affect
all services it is hosting. Windows firewall w/Advanced security has the option to tie svchost rules to specific services it hosts, but one can also create rules that affect all services:
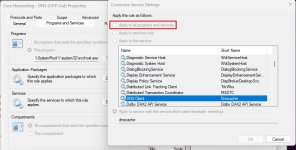
Therefore the rule created this way would apply to all running svchost processes in Windows.
Not defending Comodo and those in charge of its development, just trying to state facts as I understand them. As for malicious processes harnessing svchost or any other Windows process for comms, well it should be contained in the sandbox with the Cruel setup or similar, thereby mitigating or eliminating that threat.
Assuming Melih is in charge, I would like to see him either:
- Spearhead an initiative to investigate and fix all reported bugs and shortcomings and provide a free version, or
- Spearhead an initiative to investigate and fix all reported bugs and charge a fee (freemium) for it, or
- Announce and discontinue the development of the free version and post a disclaimer to "use at your own risk"





