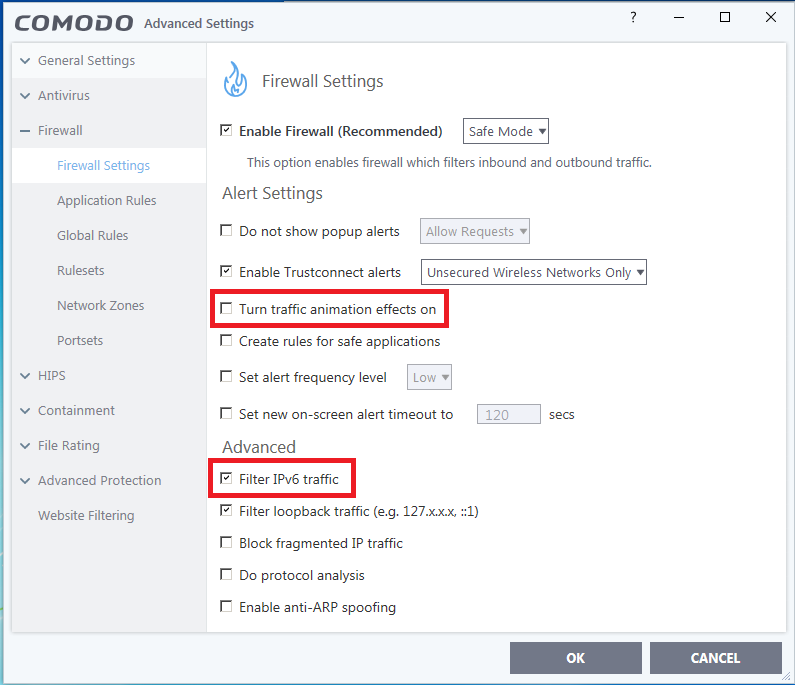
Hey. I was using CF with cruel settings but wanted to make another config, that's not as secure as cruel comodo but i think it has less hassle and is more suitable for inexperienced users. CF works only as a companion app at those settings so I would recommend that one use an AV along with it.

-Summary-
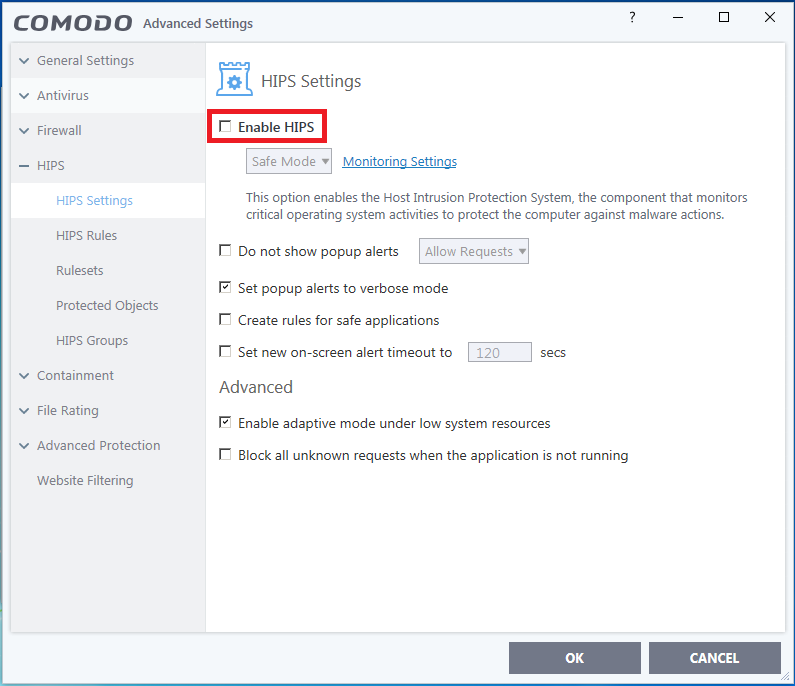
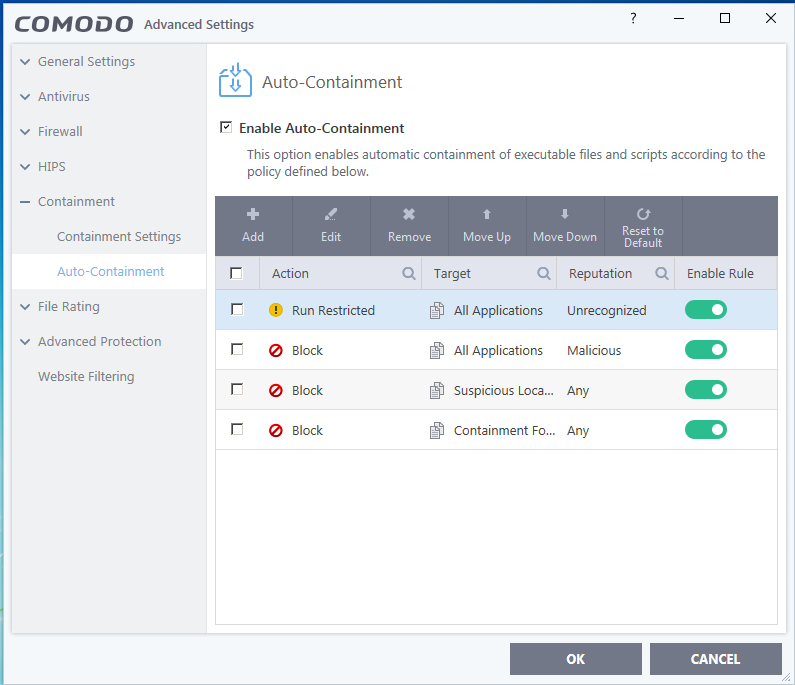
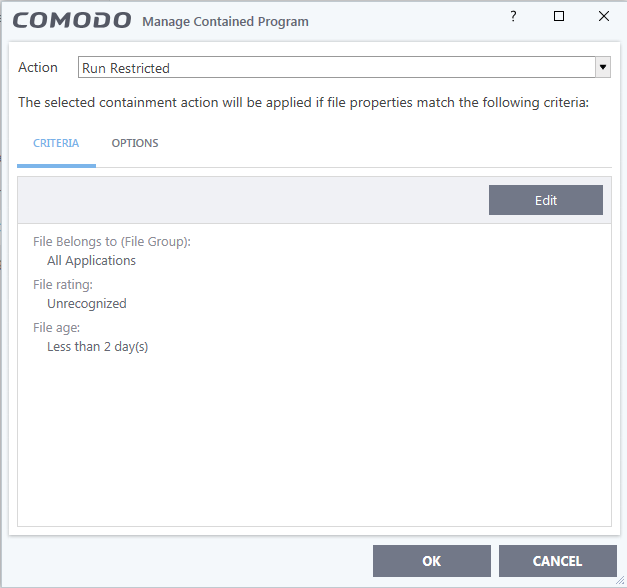
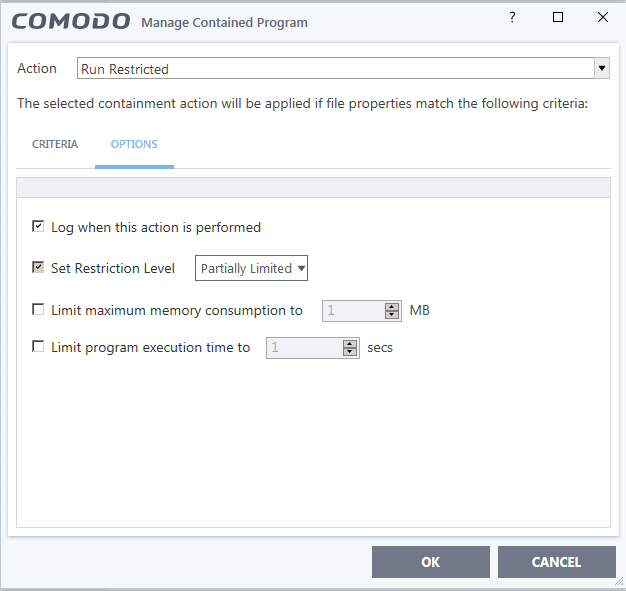
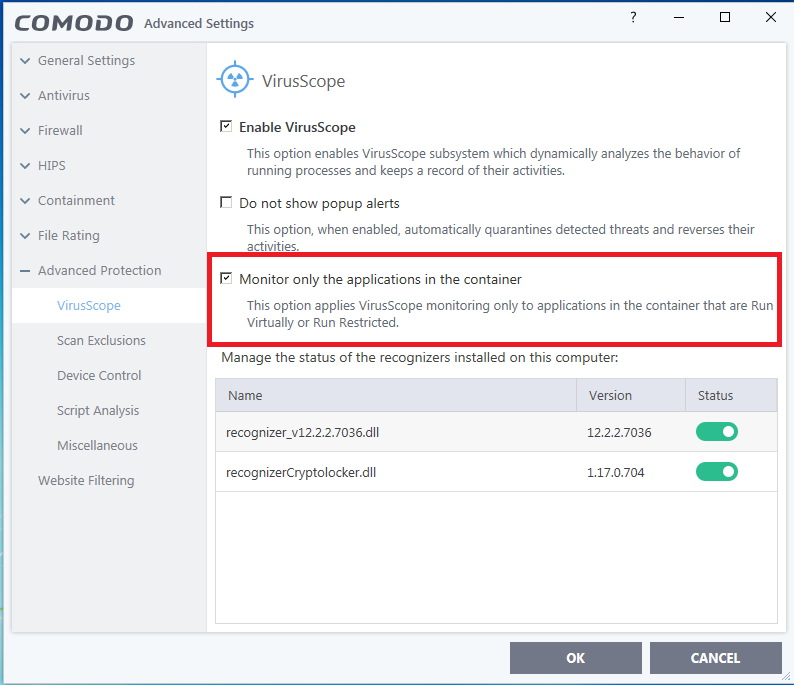
HIPS disabled. Auto-Containment only blocks known malicious files and runs specific programs (unrecognized; less than 2 days old) under partial restriction. I thought that virtualization is a big hit on usability. You can't save nor edit any documents easily. File rating and auto-containment automatically quarantines known threats. File rating doesn't automatically trust files originated from trusted(user interaction) installers (I guess user may whitelist a malware by mistake). VirusScope only detects files in containment (unrecognized; less than 2 days old), so it can't create false positives on known trusted files.
-Summary-
HIPS disabled. Auto-Containment only blocks known malicious files and runs specific programs (unrecognized; less than 2 days old) under partial restriction. I thought that virtualization is a big hit on usability. You can't save nor edit any documents easily. File rating and auto-containment automatically quarantines known threats. File rating doesn't automatically trust files originated from trusted(user interaction) installers (I guess user may whitelist a malware by mistake). VirusScope only detects files in containment (unrecognized; less than 2 days old), so it can't create false positives on known trusted files.
- Partially Limited - The application is allowed to access all operating system files and resources like the clipboard. Modification of protected files/registry keys is not allowed. Privileged operations like loading drivers or debugging other applications are also not allowed. (Default)
Last edited:
