New:
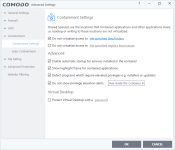
- We now have a new tab "Advanced Protection" under "Advanced Settings" where:
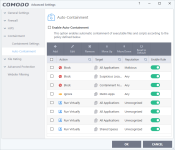
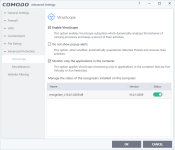
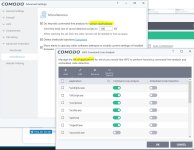
a - "Virus Scope" and "Secure Shopping": These used to be separate tabs are now part of this "Advanced Protection" section.
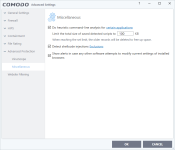
b - "Miscellaneous": From HIPS Settings, we have moved 4 settings and made part of this section. "Heuristic Command Line Analysis" and "Embedded Code Detection" are integrated under one interface as "Do Heurristic Command Line Analysis". So embedded code detection is expanded in that interface and connected with related parsers. Also we have moved "shell code injection detection" and "browser configuration modification" settings under this section.
- Comodo Secure DNS is back in installation offering now
Changes:
- You will see word "Sandbox" is now replaced with word "Containment" across whole GUI as that is easier to understand by layman while Sandbox has been more technical.
Improved:
Support of Python interpreter in heuristic command line analysis
Fixed:
- All GUI issues experienced with upcoming Windows 10 RedStone-2 / Creators Update are fixed in this release.
Main focus of CIS v10 has been to make it more stable and bug free and as part of that aim, hundreds of bugs are fixed, below are few particular fixes:
- BSOD after launched Opera in Sandbox
- Critical bypasses of Sanbdox
- Keyboard can be intercepted in Virtual Desktop
- Several apps crash caused by guard32/64.dll
- PowerShell scripts are not sandboxed
- Missed fileless malware cases
We are working on next features on CIS, mainly robust web filtering, which will provide solid protection against phishing and malicious URLs.
Thank you all for your feedback and support.
- We now have a new tab "Advanced Protection" under "Advanced Settings" where:
a - "Virus Scope" and "Secure Shopping": These used to be separate tabs are now part of this "Advanced Protection" section.
b - "Miscellaneous": From HIPS Settings, we have moved 4 settings and made part of this section. "Heuristic Command Line Analysis" and "Embedded Code Detection" are integrated under one interface as "Do Heurristic Command Line Analysis". So embedded code detection is expanded in that interface and connected with related parsers. Also we have moved "shell code injection detection" and "browser configuration modification" settings under this section.
- Comodo Secure DNS is back in installation offering now
Changes:
- You will see word "Sandbox" is now replaced with word "Containment" across whole GUI as that is easier to understand by layman while Sandbox has been more technical.
Improved:
Support of Python interpreter in heuristic command line analysis
Fixed:
- All GUI issues experienced with upcoming Windows 10 RedStone-2 / Creators Update are fixed in this release.
Main focus of CIS v10 has been to make it more stable and bug free and as part of that aim, hundreds of bugs are fixed, below are few particular fixes:
- BSOD after launched Opera in Sandbox
- Critical bypasses of Sanbdox
- Keyboard can be intercepted in Virtual Desktop
- Several apps crash caused by guard32/64.dll
- PowerShell scripts are not sandboxed
- Missed fileless malware cases
We are working on next features on CIS, mainly robust web filtering, which will provide solid protection against phishing and malicious URLs.
Thank you all for your feedback and support.