This has wandered so far off from what the OP was asking 
Completely securing a computer without using programs
- Thread starter TheMalwareMaster
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
W
Wave
Best disable AutoRun and not plug-in devices you don't know where they came from, because scanning with an AV it can already be too late by then. Better be safe than sorryVery true my friend.
Thats why i recommend scanning all USB drives with an AV on a regular basis.
Well if browser extensions are allowed you could even disable( in browser settings ) js/ flash/ auto- download.. Stop keep on downloading in the background if you close chrome .. Well block pop up . And maybe other things I don't remember .
Browsers have many settings
Recently I voluntary tried to open in my browser a phishing website with https and Firefox blocked it .
Browsers have many settings
Recently I voluntary tried to open in my browser a phishing website with https and Firefox blocked it .
I had most of these done already, they are good settings, and stuff like this is what the OP was looking for (I believe)Enable PUA detection in Windows Defender:
Code:Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\MpEngine] "MpEnablePus"=dword:00000001
Enable UAC password prompt:
Code:Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System] "ConsentPromptBehaviorAdmin"=dword:00000001
Disable elevation for a unsigned applications:
Code:Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System] "ValidateAdminCodeSignatures"=dword:00000001
It has no impact on security but you can also disable modern UAC prompt:
Code:Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\TestHooks] "XamlCredUIAvailable"=dword:00000000
This has got me thinking, I have EmsiSoft AM collecting dust. So what about those reg settings with Defender on periodic
scan, with EmsiSoft AM at the helm ?
No other software at all not even WFC, but windows firewall set so that I have to manually add rules ?
would that be as tight as I think it is ?
5
509322
-Web exploit attacks
Protecting against these is beyond the realm of registry hacks.
In keeping with the Microsoft-only theme of this thread, use EMET.
Last edited by a moderator:
There is no security that can survive sophisticated, targeted attacks. Even the best commercial security suites can be exploited - you can buy an exploit in the Dark Web if you are from Rockefeller family. Software Restriction Policies (SRP) and reg tweaks can be very effective against most malware files in the wild (even 0-day) only because such protection is uncommon in home computers, and no one bothers to fight it - there are so many home computers badly secured. The most you can get from Windows built-in security (in Windows Home) is to lock Standard User Account with SRP + silent UAC, and use Windows Store Apps for tasks related to Internet, documents and media. This setup is very secure without any third party security programs, and everything (non desktop) is updated through Windows Updates. You can install new programs on SUA only from Windows Store, and there is no possibility to run/install new desktop programs on this account. Desktop program updates and installations are possible only on Administrator account. You can next harden the system disabling remote assistance and remote access, etc. Many people can live with such setup, but for most MalwareTips members it will be impractical.
Last edited:
First Mac Malware Of 2017 DetectedJust use MacBook and you will not think about viruses anymore
(Mac) Security is just illusionNamed Quimitchin by Malwarebytes and called Fruitfly by Apple, the ‘new’ back door may actually have been lurking in the background of macOS for years, taking advantage of vulnerabilities in code that hasn’t been updated since the late 1990s, according to the antivirus software publisher’s blog post.
A masterclass in simplicity, the malware contains just two files designed to open a backdoor into the Macs it infects, letting it receive instructions from the hacker’s computer, known in the cybersecurity world as a command and control server (C&C)
Two part answer to the question. I'm assuming you mean Windows not Linux or MacOS.
1) You can use Windows in built security tools to make a attack and exploitation more difficult. You can use Group Policy to harden Windows, You can disable unneeded services, You can block open ports and risky apps through the firewall, You can tweak the registry, You can use Windows 10 in built security features like Device Guard & Credential Guard, You can delete Adobe Flash/OneDrive/Telemetry permanently. Honestly you need to practice defense in depth, layered security, and default deny to have any chance of protecting yourself.
2) There is no way you can protect a Windows system with just the in built tools Microsoft offers. Advanced malware will find a way in either through zero day exploits, social engineering, phishing or user error. Even with the best next generation security software there are always bugs to exploit. Best you can do and hope for is to make it more expensive, time consuming and difficult for would be attackers.
1) You can use Windows in built security tools to make a attack and exploitation more difficult. You can use Group Policy to harden Windows, You can disable unneeded services, You can block open ports and risky apps through the firewall, You can tweak the registry, You can use Windows 10 in built security features like Device Guard & Credential Guard, You can delete Adobe Flash/OneDrive/Telemetry permanently. Honestly you need to practice defense in depth, layered security, and default deny to have any chance of protecting yourself.
2) There is no way you can protect a Windows system with just the in built tools Microsoft offers. Advanced malware will find a way in either through zero day exploits, social engineering, phishing or user error. Even with the best next generation security software there are always bugs to exploit. Best you can do and hope for is to make it more expensive, time consuming and difficult for would be attackers.
Yes, especially kernel mode rootkits (32bit) are less common.PE Infectors, advanced kernel-mode (or even user-mode rootkits) aren't as common in the wild anymore
They exploit the poor security of the System Service Descriptor Table (SSDT) of the NT kernel by using the most trivial technique now easily detected by anti rootkit systems.
(For those interested SSDT is the addressing table used to direct the application working at ring 3 (User mode) to the native API, and it is in a structure called KeServiceDescriptorTable. The native API are provided by the kernel to allow the API of the sub-systems (win32) to perform certain operations which are only possible in kernel mode.
In this table we find an array of pointers that point to these API.
So, in theory, it could not use the native API because it would be like to operate in kernel mode and, in fact, the kernel provides the working system of an application is: Application/Subsystem API/Native API/NT Kernel.
So 32bit rootkits use the SSDT table to interface directly with the kernel, using another working system: Application/Native API/NT Kernel).
Sure, under 64bit technology it is not so easy to develop a rootkit that works by using SSDT Hooking, because Microsoft has patched the kernel, but it is still vulnerable.
SSDT consist of an array of pointers obtained from the operation: the Address of the Native Function/Address of KiServiceTable.
This "protection" is bypassable with a driver where it is implemented an algorithm for the analysis of the KeSystemServiceStart.
All this to say that the inherent Windows vulnerabilities make the operating system extremely insecure and you can work on the registry or security policy but without monitoring of the events is very difficult to predict all of the infection vectors and attack surfaces.
A lot of the Military sites use a 'black box' scenario with extremely limited access to the internet and usb and other ports disabled to secure machines. I dont really have an understanding of it though.
I would say that you can leave WD as your main AV, ditch EAM and implement Common Sense 2017 (if you weren't already)I had most of these done already, they are good settings, and stuff like this is what the OP was looking for (I believe)
This has got me thinking, I have EmsiSoft AM collecting dust. So what about those reg settings with Defender on periodic
scan, with EmsiSoft AM at the helm ?
No other software at all not even WFC, but windows firewall set so that I have to manually add rules ?
would that be as tight as I think it is ?
W
Wave
The System Service Dispatch Table is essentially a table containing pointer addresses which reside to areas in memory where the function stubs are, therefore when you lookup NtTerminateProcess in the SSDT you can find the pointer address for redirection to that function. The way SSDT hooking works is that these pointer addresses will be modified to the pointer address of your own function from within your own device driver, causing execution flow to redirect to your own function. Since it's system-wide, this means any code that calls NtTerminateProcess normally will end up leading to the SSDT to follow the pointer address, but it'll really lead to your own code. This means that SSDT hooking will affect kernel-mode code execution as well as user-mode programs - if you hook NtOpenProcess via the SSDT and then call NtOpenProcess from kernel-mode, your hook will still be triggered.(For those interested SSDT is the addressing table used to direct the application working at ring 3 (User mode) to the native API, and it is in a structure called KeServiceDescriptorTable. The native API are provided by the kernel to allow the API of the sub-systems (win32) to perform certain operations which are only possible in kernel mode.
In this table we find an array of pointers that point to these API.
So, in theory, it could not use the native API because it would be like to operate in kernel mode and, in fact, the kernel provides the working system of an application is: Application/Subsystem API/Native API/NT Kernel.
In user-mode there is a module called ntdll.dll (under System32), and ntdll.dll is the Native API system-call wrapper - it works differently depending on the process architecture and OS version. It is responsible for making the actual system call and transitioning execution to the kernel via syscall instruction. However, the system ID for the function being called is moved into EAX at the start. Therefore, if you hook a Ki function which is called in trail to intercept multiple API calls from one single hook in a process, you should be able to filter it out via the system ID for that function (e.g. KiFastSystemCall which isn't even used anymore on newer OS versions of Windows).
Phishing counts as social engineering, and phishing is completely unrelated to securing a Windows system in the sense the OP is referring too. Phishing attacks are malicious however they won't "harm" the system, they are there for the purpose of obtaining information through unethical means (social engineering, tricking you into believing you are giving information to a trusted service for example).social engineering, phishing
I assume the OP is referring to actual harmful malware and protection against this, based on registry tweaks... Which is not possible.
Every piece of software can be exploited because nothing is full-proof, as long as it's made by a human then it's vulnerable to human error which is only natural.Even with the best next generation security software there are always bugs to exploit.
You can patch an exploit however in some scenarios it can be a very tricky process because the last thing you want to do is open up another gap which was even worse than the first one which can be exploited by an attacker. If it is very tricky to exploit (time consuming or lack of internal details) then this will put many attackers off the job and will lead to them giving up eventually, however if an attacker is determined enough then the chances are they will not stop until they achieve their goal.Best you can do and hope for is to make it more expensive, time consuming and difficult for would be attackers.
One of the best things you can do is not bothering to focus on protecting the source code with things like packing, obfuscation, etc. and just focus on providing great software to the loyal user-base who are not trying to attack you. Of course in terms of security software this may be the best option, but at the end of the day... Nothing is full-proof, and that is just how things are.
That's not true at all. The only thing you need to do to protect yourself is make sure you make good decisions - this opens a whole sub-set of good security practices and can include anything from only visiting trusted websites, not opening e-mails from untrusted senders, not aimlessly clicking unknown links, not handling attachments you are unsure of, doing proper research before running new programs, etc.Honestly you need to practice defense in depth, layered security, and default deny to have any chance of protecting yourself.
No matter how much security you have, even if you have a Default Deny configuration, the first line of defense is yourself and if you make bad decisions then you'll become infected; for example, execution of a new program may be automatically blocked since it's not a white-listed object, but if you were trying to run it yourself then you can just make a dumb decision by white-listing it, and then run it, boom... Now you're infected. The same applies to AV software, when it detects a threat and then the non-knowledgeable user just removes it from the quarantine and runs it anyway, then complain about the product not keeping them protected.
I found the approach you described in your post to be quite interesting, good idea.This setup is very secure without any third party security programs, and everything (non desktop) is updated through Windows Updates. You can install new programs on SUA only from Windows Store, and there is no possibility to run/install new desktop programs on this account.
on windows 10, you can use the default metro apps such as edge and photos and groove music. They go a long way toward protecting you from exploits, because of appcontainer isolation.
Alternatively, in chrome you can enable the flag for appcontainer lockdown.
For further protection, you can delete (or rename) the script interpreters that you probably don't need, such as powershell, powershell ISE, cscript, wscript. They are the main offenders. If you do need them sometimes, so keep a copy somewhere that the malware won't look for it.
(After a major windows update, you might have to delete or rename some of them again.)
As mentioned by others, you can do your main computer tasks in a standard user account, and crank up the user account control, and leave smartscreen enabled, and always update OS and software.
In short, on windows 10 you can actually make your system pretty safe. Some forms of ransomware can still attack, but the last laugh is yours if you keep an up-to-date offline backup.
If you format your hard disk with GPT, instead of MBR, you can easily recover from MBR attacks with the help of a good boot repair tool on CD or USB.
Alternatively, in chrome you can enable the flag for appcontainer lockdown.
For further protection, you can delete (or rename) the script interpreters that you probably don't need, such as powershell, powershell ISE, cscript, wscript. They are the main offenders. If you do need them sometimes, so keep a copy somewhere that the malware won't look for it.
(After a major windows update, you might have to delete or rename some of them again.)
As mentioned by others, you can do your main computer tasks in a standard user account, and crank up the user account control, and leave smartscreen enabled, and always update OS and software.
In short, on windows 10 you can actually make your system pretty safe. Some forms of ransomware can still attack, but the last laugh is yours if you keep an up-to-date offline backup.
If you format your hard disk with GPT, instead of MBR, you can easily recover from MBR attacks with the help of a good boot repair tool on CD or USB.
You can use one program for all Microsoft security thing (Hard_Configurator):
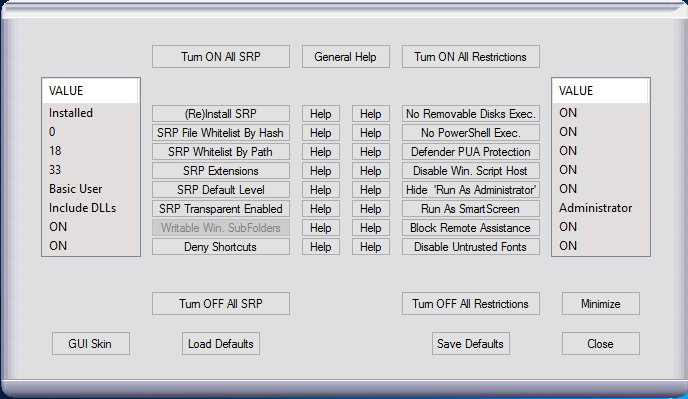
W
Wave
You can repair MBR easily as well with a boot disk/usbIf you format your hard disk with GPT, instead of MBR, you can easily recover from MBR attacks with the help of a good boot repair tool on CD or USB.
You can use one program for all Microsoft security thing (Hard_Configurator):
View attachment 135399
Thanks for mentioning Hard_Configurator. The new version will be uploaded to GitHub soon.
It can be useful for people, who do not like messing with Windows Registry.
Common Sence 2017 is pretty good but have you looked at Common Sense Pre Alpha 2018 ?I would say that you can leave WD as your main AV, ditch EAM and implement Common Sense 2017 (if you weren't already)
Last edited:
Finally I had a little time to take a look at your softwareThanks for mentioning Hard_Configurator. The new version will be uploaded to GitHub soon.
It can be useful for people, who do not like messing with Windows Registry.
Congrats Andy Ful, great job and really comprehensive pdf help
Thanks for that!
I downloaded it and I liked it, but one little thing: I couldn't get it to block powershell, although it blocked wscript just fine. What did I do wrong?You are welcome. Thanks for testing.
windows 10 x64
You may also like...
-
App Review Webroot SecureAnywhere Complete 2025
- Started by Shadowra
- Replies: 16
-
App Review DrWeb Security Space BETA
- Started by Shadowra
- Replies: 11
-
App Review Bitdefender Total Security 2026
- Started by Shadowra
- Replies: 60
-
App Review Qihoo 360 Free Total Security 2025
- Started by Shadowra
- Replies: 28
-
Serious Discussion A Habit-Based Guide to Internet Security
- Started by Divergent
- Replies: 2