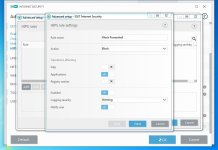
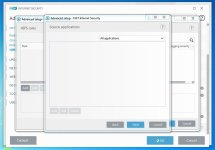
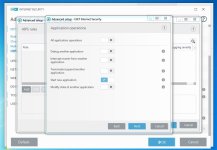
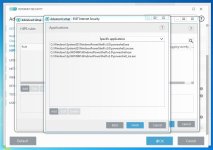
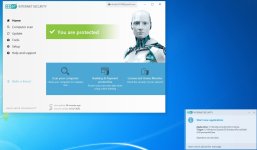
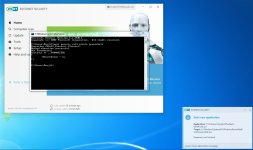
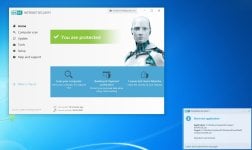
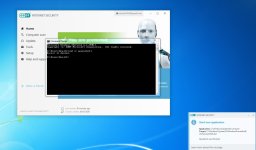
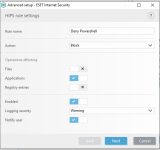
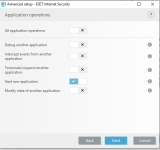
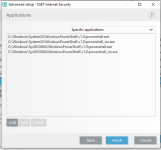
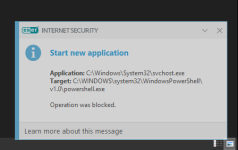
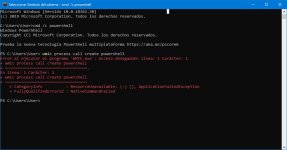
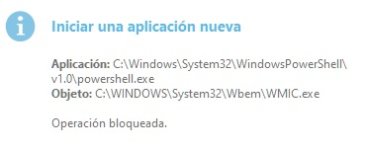
Are you sure? The HIPS settings from RoboMan post, do not disable the execution of wscript.exe, cscript.exe, etc., but only prevent starting them from Explorer. This will not stop some other ways of executing them (often used by malware), for example, via cmd.exe or WMI.As always another great post from @RoboMan. I use ESET with these HIPS rules but I have modified some of the rules. I have HIPS configured to disable execution of wscript, cscript, powershell, mshta, ask if anything tries to modify the hosts file, ask for changes in startup applications. I think it's also a good option to set rules in the firewall to ask for outgoing connections from command prompt and regsvr32.
You can try the below command to be sure:
cmd /c wscript