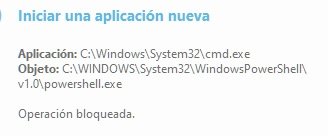
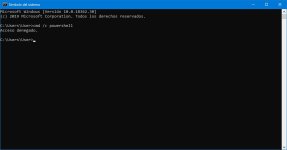
ESET HIPS should prevent cmd from launching powershell if the rules are configured correctly. In my case it does block cmd from launching powershell.Eset does not prevent cmd.exe from spawning powershell.exe
Configure ESET as default-deny (bye ransomware!)
- Thread starter RoboMan
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
ESET HIPS should prevent cmd from launching powershell if the rules are configured correctly. In my case it does block cmd from launching powershell.
It worked for me also when I tried @Andy Ful ’s tests, just had other issues to solve. On that note my image restore got messed up so I’m doing a fresh install of Win 10. Should be no issues now with powershell trying to open from svchost.exe every 25 minutes (no clue what was causing it). But, I haven’t reinstalled ESET with the old settings yet since I haven’t had time.
You can configure Eset to prevent any EXE file you like, from launching another EXE file you want. Yet, there are many possibilities - some are not obvious, like executing via COM objects and LOLBins.ESET HIPS should prevent cmd from launching powershell if the rules are configured correctly. In my case it does block cmd from launching powershell.
COM objects are accessible via most of the scripting engines. So, generally configuring HIPS via child processes is not easy.
You can configure Eset to prevent any EXE file you like, from launching another EXE file you want. Yet, there are many possibilities - some are not obvious, like executing via COM objects and LOLBins.
COM objects are accessible via most of the scripting engines. So, generally configuring HIPS via child processes is not easy.
It seems as though fully locking things down concerning powershell with HIPS is an arduous task of trial and error, not to mention there always being something you missed. Only the most diligent will not get security fatigue. As fun as it is to play with it it is pushing me towards ‘configuring’ something else to ‘defend’ my device and call it a day, but that’s for another thread.
I do not have time now to check it, but devjit2018 showed already how to prevent all applications from executing powershell.exe.It seems as though fully locking things down concerning powershell with HIPS is an arduous task of trial and error, not to mention there always being something you missed. Only the most diligent will not get security fatigue. As fun as it is to play with it it is pushing me towards ‘configuring’ something else to ‘defend’ my device and call it a day, but that’s for another thread.
https://malwaretips.com/threads/configure-eset-as-default-deny-bye-ransomware.91105/post-803860
If you will block in this way all scripting engines (wscript.exe, cscript.exe, mshta.exe, hh.exe, wmic.exe, scrcons.exe, etc.), then the access to COM objects will be very restricted. So finally, it will be hard for the attacker to execute the scripting code.
I do not have time now to check it, but devjit2018 showed already how to prevent all applications from executing powershell.exe.
https://malwaretips.com/threads/configure-eset-as-default-deny-bye-ransomware.91105/post-803860
If you will block in this way all scripting engines, then (wscript.exe, cscript.exe, mshta.exe, hh.exe, wmic.exe, scrcons.exe, etc.), then the access to COM objects will be very restricted.
Ah, I misunderstood your comment. I actually had tried his rules and they seemed to work. I thought you were implying that there were ways around those rules. My mistake. Thank you for the clarification.
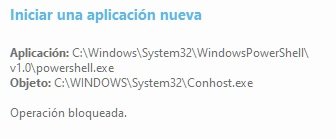
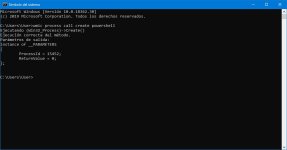
There are two simple ways:View attachment 212803View attachment 212804
Before creating these rules I used Macrium. Now the question is, how can I run the cmd for example to make an sfc? Excuse me I'm a novice user. Thank you.
- Do not block cmd.exe in Eset.
- Unblock temporarily cmd.exe in Eset.
This method is probably quite effective, but I cannot say that it is bullet-proof.Ah, I misunderstood your comment. I actually had tried his rules and they seemed to work. I thought you were implying that there were ways around those rules. My mistake. Thank you for the clarification.
Well, this is my last intervention on this topic as it is for experienced users.
View attachment 212805View attachment 212806View attachment 212807
You can disable a rule temporarily when you need to use cmd.exe and then re-enable it when you’re done. I’m not at my computer right now to provide screenshots. Just uncheck the rule and save and then recheck it and save when you’re done.
Yes precisely. Creating HIPS rules needs time and patience since every machine is unique. You may have software that requires powershell or wscript. Setting ESET to block powershell/wscript will render that software useless that requires any of them to operate properly. That's why it's recommended that only advanced users should tinker with the HIPS. Casual users should just use the HIPS in Smart Mode.It seems as though fully locking things down concerning powershell with HIPS is an arduous task of trial and error, not to mention there always being something you missed. Only the most diligent will not get security fatigue. As fun as it is to play with it it is pushing me towards ‘configuring’ something else to ‘defend’ my device and call it a day, but that’s for another thread.
Yes precisely. Creating HIPS rules needs time and patience since every machine is unique. You may have software that requires powershell or wscript. Setting ESET to block powershell/wscript will render that software useless that requires any of them to operate properly. That's why it's recommended that only advanced users should tinker with the HIPS. Casual users should just use the HIPS in Smart Mode.
With a fresh install and most everything loaded I’m having no issues with the hips rules.
Last edited:
RoboMan
Level 38
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
High Reputation
Forum Veteran
Would you think VoodooShield would be a good addition to this setup? Or is it too much? Looking forward to hear your opinions.
Would you think VoodooShield would be a good addition to this setup? Or is it too much? Looking forward to hear your opinions.
I think VS would be a great addition for extra scripting protection. I was using NVT OSArmor with it to cover blind spots. I’m not sure about the system impact of VS, OSA is virtually a feather.
It largely depends on you my friend. If you want an anti executable that has VT integrated then VS will be your only option. Else if you just want good protection against scripts then OSArmor will suffice. For those who have lifetime licenses, AppGuard is an excellent tool to use alongside ESET/KIS.Would you think VoodooShield would be a good addition to this setup? Or is it too much? Looking forward to hear your opinions.
RoboMan
Level 38
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
High Reputation
Forum Veteran
The only issue I always had with VS is the delay to execute programs, I guess because it has to compare it with VirusTotal. I would very much like to use OSA, if you would share with me your configuration file for it, that would cover the best script protection and basic features, I would very much appreciate it.It largely depends on you my friend. If you want an anti executable that has VT integrated then VS will be your only option. Else if you just want good protection against scripts then OSArmor will suffice. For those who have lifetime licenses, AppGuard is an excellent tool to use alongside ESET/KIS.
Or if anybody could share with me their OSA configuration file with good script protection, I'd be very thankful.
The only issue I always had with VS is the delay to execute programs, I guess because it has to compare it with VirusTotal. I would very much like to use OSA, if you would share with me your configuration file for it, that would cover the best script protection and basic features, I would very much appreciate it.
Or if anybody could share with me their OSA configuration file with good script protection, I'd be very thankful.
I can share it when I get back to my pc. I basically looked at the video CruelSister did on it and clicked on some other optional boxes. It’s pretty easy to play with since you can untick anything that gives you issues, and set exception. Default is good for most scripts. I block Powershell and CMD and just disable OSA when I need those since I rarely use them. I think my file has some exceptions you may or may not want for ConfigureDefender.
So the config file isn't an allowed file type for posting. If you PM me I can get it to you somehow. However I would say start with default, CS has a couple recommended options and then experiment from there. Either way, let me know.
VS shouldn't delay the execution of programs which are started from the root directories of the C drive(system space) like windows, program files. It normally checks the user space like program data, appears, desktop, downloads,documents. I've never had the delay while running VS with ESET except when executing from the downloads folder. OSArmor you won't even notice is there. It just sits there quietly doing it's job. I used to have it with ESET but since tweaking the HIPS, running SysHardener and ditching MS Office I don't require it anymore.The only issue I always had with VS is the delay to execute programs, I guess because it has to compare it with VirusTotal
You may also like...
-
App Review Shadowra's Big Comparative : Episode 2 - Paid Antivirus
- Started by Shadowra
- Replies: 198