No, Machine Learning models are also a part of WD default protection. The local ML models are updated via WD updates. From Microsoft documentation, it follows that it should be the same for Windows Home, Pro, and E3. The E5 edition has some additional AI protection ("Advanced machine learning and AI based protection for apex level viruses and malware threats"). Furthermore, E5 editions can use "Behavioral-based detection for advanced and targeted attacks (post-breach)".Isn't machine learning part of ATP only ?
ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Microsoft's foggy technical literature make it difficult to determine exactly which features of ATP make it into WD. @Nightwalker posted this @ Wilders: Out of sight but not invisible: Defeating fileless malware with behavior monitoring, AMSI, and next-gen AV - Microsoft Security
Thanks, this was actually a very interesting read. It almost sounds like enterprise grade WD is almost as good with fileless as consumer antimalware are with normal/non-fileless malware. It's just that these techniques haven't yet percolated down to consumer-grade products and remains in enterprise realm, even the article near the bottom for consumer suggests Windows-S is the way to go, with only microsoft (counter)signed binaries, no scripting engines etc.
Oh well, in a few years time consumer products will have these techniques too and then fileless will be less scary than it is today.
No, Machine Learning models are also a part of WD default protection. The local ML models are updated via WD updates. From Microsoft documentation, it follows that it should be the same for Windows Home, Pro, and E3. The E5 edition has some additional AI protection ("Advanced machine learning and AI based protection for apex level viruses and malware threats"). Furthermore, E5 editions can use "Behavioral-based detection for advanced and targeted attacks (post-breach)".
And Enterprise has cloud or sandbox detonation of suspicious files,
Last edited:
No, Machine Learning models are also a part of WD default protection. The local ML models are updated via WD updates. From Microsoft documentation, it follows that it should be the same for Windows Home, Pro, and E3. The E5 edition has some additional AI protection ("Advanced machine learning and AI based protection for apex level viruses and malware threats"). Furthermore, E5 editions can use "Behavioral-based detection for advanced and targeted attacks (post-breach)".
Thanks @Andy Ful ! That's actually great, though it's not clear from MS' document if the models for home/pro are sufficient to stop most fileless or the "advanced ML" is what's needed. Still good news, I guess a few days after something hits enterprises home uses receive a trained model to catch it, so as long as it's not innovative 0day malware, home users should be ok.
This one and many more articles are related to the full WD ATP used in Windows E5 editions. Some features like AMSI ML models are included in default WD protection.Microsoft's foggy technical literature make it difficult to determine exactly which features of ATP make it into WD. @Nightwalker posted this @ Wilders: Out of sight but not invisible: Defeating fileless malware with behavior monitoring, AMSI, and next-gen AV - Microsoft Security
It is available for Windows E5.And Enterprise has cloud or sandbox detonation of suspicious files,not mentioned in that reference, if I remember correctly.
Post edited.
The ML models + ASR are available for Windows Home. They are sufficient to stop most fileless malware based on Windows scripts (PowerShell, Windows Scripts Host, VBA macros).Thanks @Andy Ful ! That's actually great, though it's not clear from MS' document if the models for home/pro are sufficient to stop most fileless or the "advanced ML" is what's needed.
...
It is mentioned and available for Windows E5.
Shame that E5 costs so much, even E3 which effectively just an MDM service is not reasonably priced for personal use. The biggest hole in MS' defender at the moment is probably the lack of a web dashboard to manage all family computers at group policy level
The ML models + ASR are available for Windows Home. They are sufficient to stop most fileless malware based on Windows scripts (PowerShell, Windows Scripts Host, VBA macros).
To put a benchmark on how effective the models are for home users, do you know if the ML models for home would had blocked Astaroth when it was fresh ( ie before models had been trained with Astharoth in their training set )
I really love the notes at the end of the text listing all the optional features. Like buying optional features for a new car. 
I edited my post when I saw that I initially missed scrolling down to see much of the chart.
It is mentioned and available for Windows E5.
I edited my post when I saw that I initially missed scrolling down to see much of the chart.
@Andy Ful Does WD ML also cover leveraging functions in-process from COM interfaces or .net objects - or it just tracks the process tree?
From the below infection chain it follows that it should be detected by behavior-based and AMSI ML models. These models are trained and optimized on the very large sample of malware before they are included in WD. Many malware samples use similar infection chains.To put a benchmark on how effective the models are for home users, do you know if the ML models for home would had blocked Astaroth when it was fresh ( ie before models had been trained with Astharoth in their training set )
Please note, that the above picture is related to preventing the infection - not to detecting the final Astaroth payload, which is reflectively injected as DLL.
Last edited:
- May 26, 2014
- 1,378
- 9,319
- 2,288
@oldschool @Andy Ful
I really dont know why Windows Defender is a target of so much hate and biased remarks:

 www.wilderssecurity.com
www.wilderssecurity.com
I guess some people need to justify their financial and emotional efforts in third party security solutions.
I really dont know why Windows Defender is a target of so much hate and biased remarks:
Windows Defender Is Becoming the Powerful Antivirus That Windows 10 Needs
I'm afraid you're misunderstanding. I'm talking about a scenario where you allow the malware to run because you trust it, and AV keeps quit. If you...
I guess some people need to justify their financial and emotional efforts in third party security solutions.
From the below infection chain it follows that it should be detected by behavior-based and AMSI ML models. These models are trained and optimized on the very large sample of malware before they are included in WD. Many malware samples use similar infection chains.
View attachment 225219
Please note, that the above picture is related to preventing the infection - not to detecting the final Astaroth payload, which is reflectively injected as DLL.
But were these the ML models for home/pro (*) or the "advanced ML" ones which are used in E5.
(*) referring to the time when Astaroth was a 0day, a few days later I'd expect home/pro to detect it as well
Who knows? ASR rules can cover some attacks related to COM interfaces or .NET objects.@Andy Ful Does WD ML also cover leveraging functions in-process from COM interfaces or .net objects - or it just tracks the process tree?
@oldschool @Andy Ful
I really dont know why Windows Defender is a target of so much hate and biased remarks:

Windows Defender Is Becoming the Powerful Antivirus That Windows 10 Needs
I'm afraid you're misunderstanding. I'm talking about a scenario where you allow the malware to run because you trust it, and AV keeps quit. If you...www.wilderssecurity.com
I guess some people need to justify their financial and emotional efforts in third party security solutions.
+people love dissing Microsoft, even after 20 years since it was the old powerful Borg empire and massive org changes, people still hold a grudge
Edit: it doesn't look like Exploit Guard was used on that test, to be fair with the Wilders poster, the WD result would had been worrying if Exploit Guard was on though.
Last edited:
People just like to theorize but do not bother to read carefully the test methodology.@oldschool @Andy Ful
I really dont know why Windows Defender is a target of so much hate and biased remarks:

Windows Defender Is Becoming the Powerful Antivirus That Windows 10 Needs
I'm afraid you're misunderstanding. I'm talking about a scenario where you allow the malware to run because you trust it, and AV keeps quit. If you...www.wilderssecurity.com
I guess some people need to justify their financial and emotional efforts in third party security solutions.
I do not think that the Astaroth infection chain (points 1-4) is an apex malware infection chain (these points are pretty common).But were these the ML models for home/pro (*) or the "advanced ML" ones which are used in E5.
(*) referring to the time when Astaroth was a 0day, a few days later I'd expect home/pro to detect it as well
So, yes - these ML models should be included in Windows Home, Pro, and E3.
There is no doubt that WD uses pre-execution behavior monitoring/blocking. It can be seen when WD blocks execution for 10s (up to 60s, depending on settings) and analyses the file in the cloud. After this, the file execution can be:
- blocked,
- allowed,
- allowed and blocked after several seconds/minutes.
Here are some examples of ML behavior-based detections on Windows Pro (default, high or max ConfigureDefender settings):
Last edited:
What's the difference between selecting "Warn" for SmartScreen from WSC and from Configure Defender? I haven't seen SmartScreen in action when "Warn" is selected from WSC.
What's the difference between selecting "Warn" for SmartScreen from WSC and from Configure Defender? I haven't seen SmartScreen in action when "Warn" is selected from WSC.
Are your samples downloaded from the web or imported via USB ? The later don't have Mark of the web Mark of the Web (Internet Explorer)
Any SmartScreen settings in WSC or ConfigureDefender (except Disabled setting) have no influence to SmartScreen check.What's the difference between selecting "Warn" for SmartScreen from WSC and from Configure Defender? I haven't seen SmartScreen in action when "Warn" is selected from WSC.
The "Warn" setting simply allows the user to run the application.
The "Block" setting does not allow the user to run the application.
The "User" setting in ConfigureDefender applies the setting from WSC
The "Warn" and "Block" settings in ConfigureDefender forces WSC to apply these settings and they cannot be changed by the user from WSC.
If you do not see the SmartScreen alert then there are some possibilities, for example:
- SmartScreen is Disabled.
- The file extension is ignored by design - SmartScreen is triggered only for some executables, like EXE, MSI, COM, SCR, BAT, JSE, VBE, etc.
- The file has not MOTW attached.
Without MOTW, the Unblock option is absent. The MOTW is skipped for files stored on flash drives or unpacked by many unpackers.
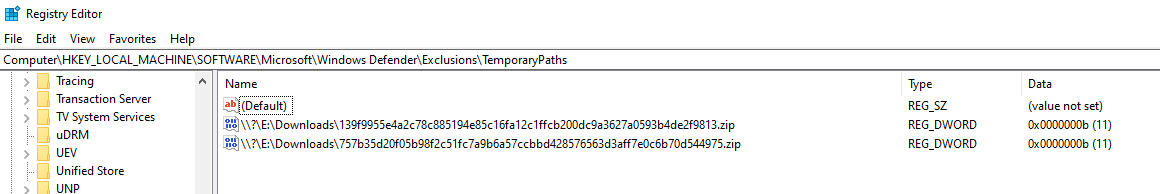
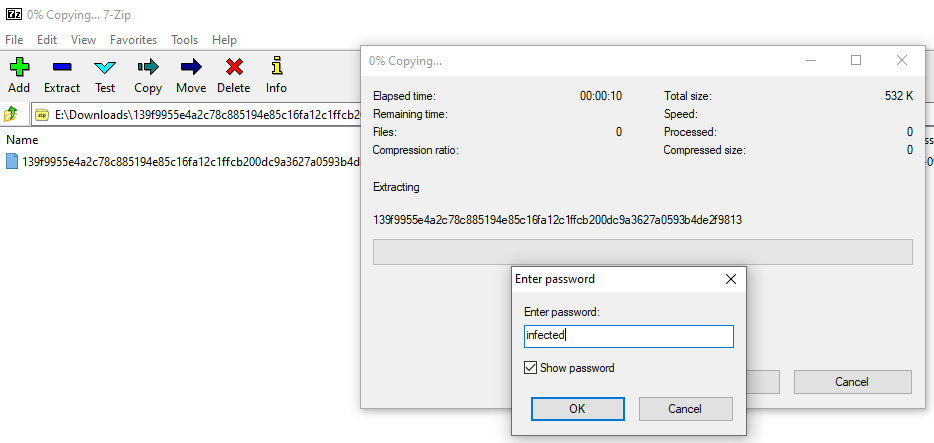
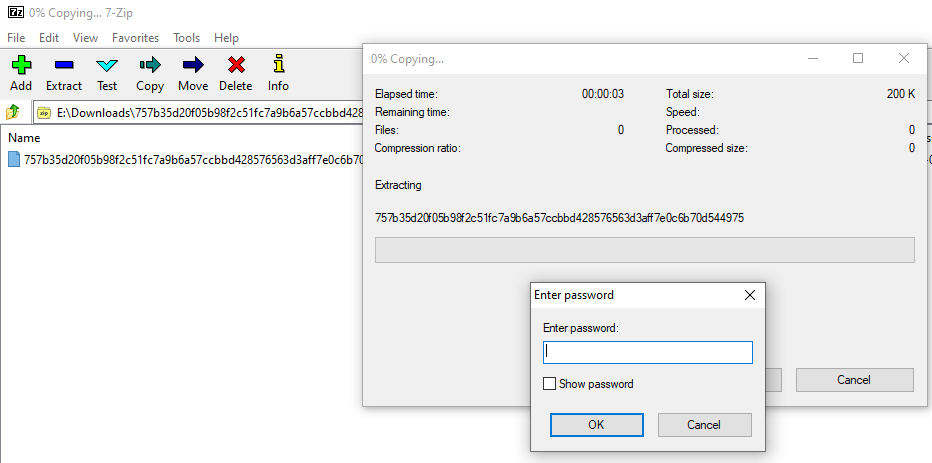
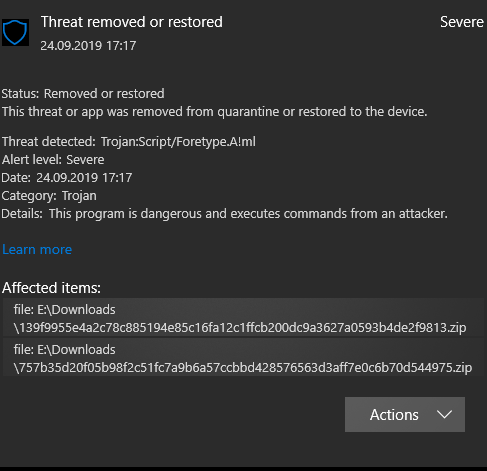
How can i clear temporary exclusions? I download some samples from Cape Sandbox, and very interesting, every ZIP archive have password (infected) and WD detect malware before extract.
***
***
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0