This makes a great case for runbysmartscreen. Not a catch all solution, but helpful in many situations!Any SmartScreen settings in WSC or ConfigureDefender (except Disabled setting) have no influence to SmartScreen check.
The "Warn" setting simply allows the user to run the application.
The "Block" setting does not allow the user to run the application.
The "User" setting in ConfigureDefender applies the setting from WSC
The "Warn" and "Block" settings in ConfigureDefender forces WSC to apply these settings and they cannot be changed by the user from WSC.
If you do not see the SmartScreen alert then there are some possibilities, for example:
It is easy to check (before execution) if the file has MOTW:
- SmartScreen is Disabled.
- The file extension is ignored by design - SmartScreen is triggered only for some executables, like EXE, MSI, COM, SCR, BAT, JSE, VBE, etc.
- The file has not MOTW attached.
View attachment 225491
Without MOTW, the Unblock option is absent. The MOTW is skipped for files stored on flash drives or unpacked by many unpackers.
ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I see. In case of testing malwares on the hub, we download a password protected zip file then extract that file and execute anything that was not detected by signatures. Will SmartScreen work for these exe malwares when I set it to "Warn" via Configure Defender?Any SmartScreen settings in WSC or ConfigureDefender (except Disabled setting) have no influence to SmartScreen check.
The "Warn" setting simply allows the user to run the application.
The "Block" setting does not allow the user to run the application.
The "User" setting in ConfigureDefender applies the setting from WSC
The "Warn" and "Block" settings in ConfigureDefender forces WSC to apply these settings and they cannot be changed by the user from WSC.
I see. In case of testing malwares on the hub, we download a password protected zip file then extract that file and execute anything that was not detected by signatures. Will SmartScreen work for these exe malwares when I set it to "Warn" via Configure Defender?
If your question is in reference to my request, I changed my profile post request to use Max with no SS because I realized this could interfere with your normal testing routine.
No. The "Warn" setting (in WSC or ConfigureDefender) can only allow choosing the available option after the SmartScreen alert is already seen. This setting has no influence on showing this alert or not - it cannot add the MOTW to the file.I see. In case of testing malwares on the hub, we download a password protected zip file then extract that file and execute anything that was not detected by signatures. Will SmartScreen work for these exe malwares when I set it to "Warn" via Configure Defender?
You will see the SmartScreen alert only if the executable supported by SmartScreen technology has MOTW attached (assuming that SmartScreen is enabled).
Ok, thanks for clarifyingNo. The "Warn" setting (in WSC or ConfigureDefender) can only allow choosing the available option after the SmartScreen alert is already seen. This setting has no influence on showing this alert or not - it cannot add the MOTW to the file.
You will see the SmartScreen alert only if the executable supported by SmartScreen technology has MOTW attached (assuming that SmartScreen is enabled).
The SmartScreen can be Disabled in the test. This will not influence other WD settings.If your question is in reference to my request, I changed my profile post request to use Max with no SS because I realized this could interfere with your normal testing routine.
This script was already being detected by WD but the execution wasn't blocked in my test. Same happened with another script in another test. My internet connection didn't drop. What could be the reason?
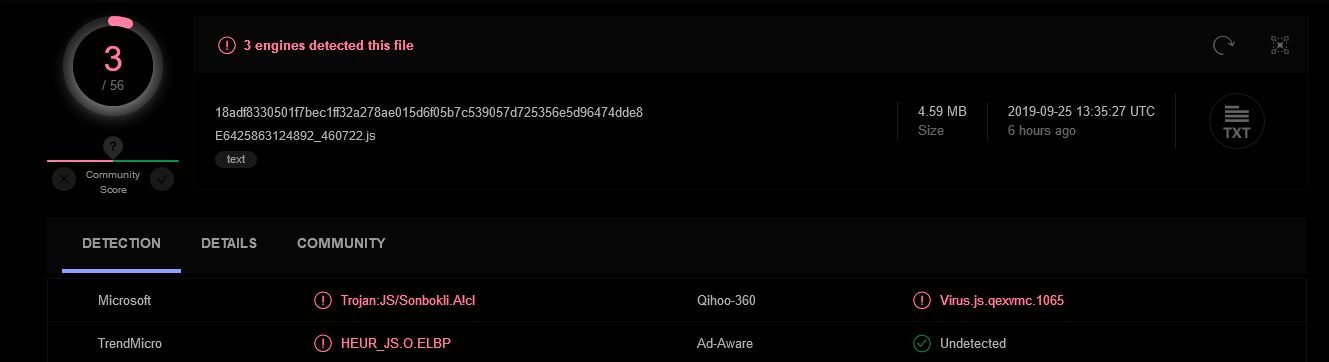
What is a source of this image?This script was already being detected by WD but the execution wasn't blocked in my test. Same happened with another script in another test. My internet connection didn't drop. What could be the reason?
View attachment 225818
Edit.
OK - @blackice is right, this was VT.
Last edited:
Looks like dark mode VT. Kinda slick looking.What is a source of this image?
It seems that VT used more recent signatures or the sample was tested (on VT) with MOTW.This script was already being detected by WD but the execution wasn't blocked in my test. Same happened with another script in another test. My internet connection didn't drop. What could be the reason?
View attachment 225818
The difference might happen also when Windows E5 was used.
Post edited.
Last edited:
Yes, it isLooks like dark mode VT. Kinda slick looking.
Hmm ok, let's see what happens in the next test.It seems that VT used more recent signatures or the sample was tested with MOTW.
The difference might happen also when Windows E5 was used.
When using ShadowDefender on boot and for some reason, there was a problem with updating the signatures, then you use pretty old signatures. So before the test, it is good to look at WSC if the signatures are freshly updated.Hmm ok, let's see what happens in the next test.
Anyway, If the sample has a standard signature (but not fast signature related to BAFS), then it should be also detected dynamically by signatures in the cloud.
Last edited:
I always update before running shadow defender and it's being detected by a fast signature not the standard one. All the .exe files samples on the dynamic test were also detected by fast signatures but for some reason this .js file wasn't.When using ShadowDefender on boot and for some reason, there was a problem with updating the signatures, then you use pretty old signatures. So before the test, it is good to look at WSC if the signatures are freshly updated.
Anyway, If the sample has a standard signature (but not fast signature related to BAFS), then it should be also detected dynamically by signatures in the cloud.
I always update before running shadow defender and it's being detected by a fast signature not the standard one. All the .exe files samples on the dynamic test were also detected by fast signatures but for some reason this .js file wasn't.
By fast signatures, I mean the signatures in the WD Cloud related to BAFS. If your samples are unpacked by Winrar or 7-ZIP, then they are ignored by BASF. So, they are not detected by fast signatures. In this case, only standard signatures in the cloud and behavior-based Machine Learning models are used. It is often hard to see the difference between them, because behavior-based ML models can classify some samples as malicious in milliseconds.
If WD detection of .js script on VT is related to BASF, then it will not be detected in the static part of your tests, but rather in dynamic part. In some cases, WD on Windows Home or Pro will not detect such samples (but they can be detected on Windows E5).
Edit.
There is also a possibility that VT has access to most recent signatures in the WD Cloud. Who knows?
Last edited:
I am curious on something, Serioushoax did a sample test today with WD at Max settings ,and static only detected 3 samples but WD got 13 others on demand (dynamic), without the max settings of configure defender would these samples have infected computer?
I am curious on something, Serioushoax did a sample test today with WD at Max settings ,and static only detected 3 samples but WD got 13 others on demand (dynamic), without the max settings of configure defender would these samples have infected computer?
Weak local signatures are the reason for the low static detection. The real time detection uses the cloud which is WD's strong point. The main detection difference between High and Max settings are the the blocking level and the number of ASR rules enabled. One sample
"E6425863124892_460722.js opens wscript.exe and the payload is blocked by two ASR rule". One of these ASR rules "Block executables unless they meet a prevalence, age or trusted criteria" would not have been enabled in High setting. I am not sure whether it would have been a block, partial block, etc. with only the one rule "Use advanced protection against ransomware" instead of two.
Remember, you can enable all of these using High and manually select the additional ASR rules, blocking level, cloud timeout, etc. unless you encounter an ASR rule incompatibility with your system that does not allow exclusions.
Edited: last sentence.
Last edited:
Maybe "slow signatures" would be a slightly better term. WD has good local (offline) signatures for several days old malware.Weak local signatures are the reason for the low static detection.
...
- Aug 17, 2014
- 12,745
- 123,912
- 8,399
Just to inform you,I am curious on something, Serioushoax did a sample test today with WD at Max settings ,and static only detected 3 samples but WD got 13 others on demand (dynamic), without the max settings of configure defender would these samples have infected computer?
static = on-demand scan
dynamic = on-execution detection
In the test made by SeriousHoax, the ConfigureDefender "MAX Protection level" settings cannot change the results of the static (on-demand scan) detection. These settings have an impact on dynamic (on-execution) detection.
The situation is more complicated when the samples have MOTW attached. Such samples can be treated by WD as they were executed, even when the user just opens the folder with samples. The testers usually count such detections as static but then, ConfigureDefender MAX Protection level can have an important impact on static detection results.
The situation is more complicated when the samples have MOTW attached. Such samples can be treated by WD as they were executed, even when the user just opens the folder with samples. The testers usually count such detections as static but then, ConfigureDefender MAX Protection level can have an important impact on static detection results.
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0