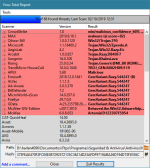
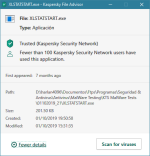
It looks like a crack for XLSTAT (AddinSoft) for Excel.@Andy Ful: what about XLSTATSTART.exe? I got final verdict from KVirusDesk is clean, also appears as Trusted in KSN...
I've also tested with KTS2020d (defaults) and :
I've tested and triggers cmd.exe -> conhost.exe for about 1 second and auto terminates, it only left a 0 KB file... false positive??
ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Is there any entry in the Log for blocking via ASR rules (search for 1121 in the Log)? You can also post the Log, I am curious how this malware was mitigated.I checked log, there wasn't anything in the log about this sample.
The payload should be blocked when spawning by WmiPrvSE.exe.
Last edited:
- Apr 28, 2015
- 9,400
- 1
- 84,830
- 8,389
Kaspersky usually does not add cracks to detections unless they can harm clearly the system... so We can consider it's a FP 
@SeriousHoax In your testing with Max settings I guess you haven't had any ransomware make it far enough to be blocked by Controlled Folder Access? 
Got a (hopfully) simple question, why are there ?????? here?
What is this suppose to be?
Could be a Unicode error due to Region & Language settings.
Could be a Unicode error due to Region & Language settings.
The below links can probably help:
https://en.wikipedia.org/wiki/Quantcast

Quantcast
The Quantcast Platform simplifies digital advertising by connecting brands to their audiences using real-time data from over 100M web & mobile destinations.
Agreed!Kaspersky usually does not add cracks to detections unless they can harm clearly the system
What's it suppose to be, what do those options say for others?Could be a Unicode error due to Region & Language settings.
Guys, please PM to each other about this. It is completely off topic here - nothing to do with ConfigureDefender.:emoji_pray:What's it suppose to be, what do those options say for others?
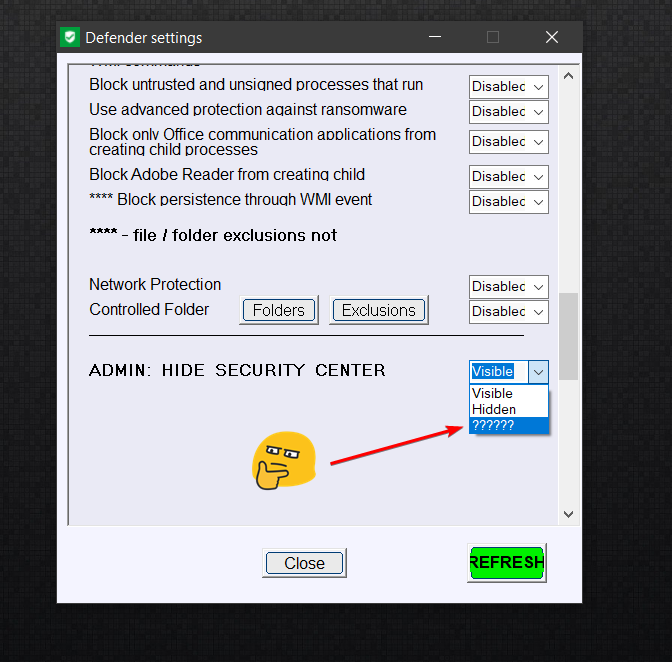
How is it offtopic, there is an option in your program and it's labeled ??????, I'm wondering what it does/means/do/supposed to say, etc. just answer the question and this will move on.
Please be kind. Your post :How is it offtopic, there is an option in your program and its labled ??????, I'm wondering what it does/means/do/suspose to say, etc. just answer the damned question and this will move on.
https://malwaretips.com/threads/configuredefender-utility-for-windows-10.79039/post-837296
is probably displayed improperly. Here what I can see on my computer:
That is why some members completely did not understand what it should mean.
There is one setting ??????? in ConfigureDefender, and it means that the user hid only some features in Windows Security Center by using reg tweaks, GPO, or other software.
Attachments
Last edited:
+1Please be kind.
Some notes related to the latest test:
https://malwaretips.com/threads/malware-samples-14-2-10-2019.95369/post-837733
4.bat was analyzed here:
https://app.any.run/tasks/310bde9b-a55c-4525-815c-5c0e6566197e/
If successful then it writes autorun entry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
msptermsizes = "C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe"
DH_695294_7957766861156.vbs was analyzed here:
https://app.any.run/tasks/65743ea0-6e3c-409c-a617-cfdf189501a7/
If successful then it writes autorun entry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
wdukuigy = "C:\Users\admin\AppData\Roaming\Microsoft\Zulycjadyc\ytfovlym.exe"
Chrome.Update.cfbe05.js was analyzed here:
https://app.any.run/tasks/79b53a41-6f20-42dd-875f-b8291ab51715/
It is probably a part of some more complex attack - it does not try to do anything dangerous. It can be also that the CnC server is already down.
https://malwaretips.com/threads/malware-samples-14-2-10-2019.95369/post-837733
4.bat was analyzed here:
https://app.any.run/tasks/310bde9b-a55c-4525-815c-5c0e6566197e/
If successful then it writes autorun entry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
msptermsizes = "C:\Users\admin\AppData\Local\msptermsizes\msptermsizes.exe"
DH_695294_7957766861156.vbs was analyzed here:
https://app.any.run/tasks/65743ea0-6e3c-409c-a617-cfdf189501a7/
If successful then it writes autorun entry:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
wdukuigy = "C:\Users\admin\AppData\Roaming\Microsoft\Zulycjadyc\ytfovlym.exe"
Chrome.Update.cfbe05.js was analyzed here:
https://app.any.run/tasks/79b53a41-6f20-42dd-875f-b8291ab51715/
It is probably a part of some more complex attack - it does not try to do anything dangerous. It can be also that the CnC server is already down.
Last edited:
Sorry, but I was getting fusterated with all the non-answers. I have no idea why you are seeing what you see, this is what I posted, and this is the link to said pictures (maybe this'll work)...
Sorry, but I was getting fusterated with all the non-answers. I have no idea why you are seeing what you see, this is what I posted, and this is the link to said pictures (maybe this'll work)...View attachment 226636View attachment 226637
This was @Andy Ful's reply earlier today:
There is one setting ??????? in ConfigureDefender, and it means that the user hid only some features in Windows Security Center by using reg tweaks, GPO, or other software.
There wasn't any. Even in the last malware pack test for the 3 script there wasn't any entry related to those.Is there any entry in the Log for blocking via ASR rules (search for 1121 in the Log)? You can also post the Log, I am curious how this malware was mitigated.
The payload should be blocked when spawning by WmiPrvSE.exe.
So far, no. All the ransomwares have been blocked by signatures.@SeriousHoax In your testing with Max settings I guess you haven't had any ransomware make it far enough to be blocked by Controlled Folder Access?
The two samples from the last test add autorun entries, so I am sure that they were neutralized on your testing system or were already dead. It is also possible that they were stopped by WIndows 10 mitigations. Anyway, we do not know if WD could mitigate/block them.There wasn't any. Even in the last malware pack test for the 3 script there wasn't any entry related to those.
Network Protection not working. Opera&Edge // host&vm
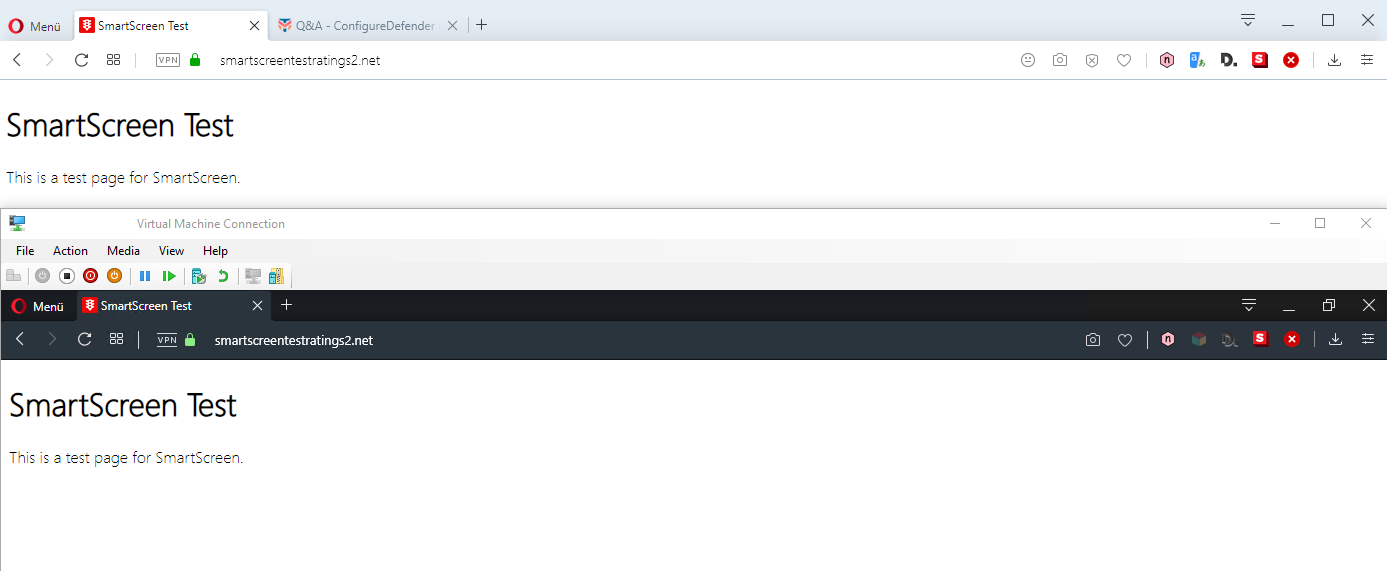
You have the same issue as me. Not to worry. You still have Smartscreen on Edge and you can use what you like for the others.
The Demo link SmartScreen Test does not work for me too. That happened several times in the past. But, Network Protection still works for the real phishing links. I have just tried this on the one-year-old link and NP works well. If someone wants to check it, then please PM to me.
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0