I don't know about the exclusion part but if you're 100% certain of a program being safe, in this case Brave browser then turn off WD Real time protection before installing Brave and turn on after. It happened to me a lot too while updating apps because of this ASR rule. As you can see from the name of the rule, it's obvious to face this issue while installing brand new version of a program.I've had some trouble auto-updating Brave Browser and I have this ASR block in the log:
View attachment 228755
I have added this ASR exclusion (folder): Windows/C:/Program Files (86)/Brave Software/Update/Install
Is this correct?
ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
You can do it, but in most cases, it would not work because some executables will be unpacked and run from the user temporary folder. Furthermore, it is not necessary. The new updater will be allowed by Microsoft tomorrow when it will gain more prevalence.I've had some trouble auto-updating Brave Browser and I have this ASR block in the log:
View attachment 228755
I have added this ASR exclusion (folder): Windows/C:/Program Files (86)/Brave Software/Update/Install
Is this correct?
Yes, this ASR rule is activated in MAX Protection Level.:emoji_ok_hand:I think its because your on Max settings ? with ConfigureDefender..... with High settings probably no problem.
Disable WD, run the updater, enable WD, restart Windows.I don't know about the exclusion part but if you're 100% certain of a program being safe, in this case Brave browser then turn off WD Real time protection before installing Brave and turn on after. It happened to me a lot too while updating apps because of this ASR rule. As you can see from the name of the rule, it's obvious to face this issue while installing brand new version of a program.
Restarting Windows is necessary to make ASR rules work properly.
@Andy Ful BTW I tested some phishing links with Brave recently and network protection blocked some of them so it is definitely working. 
That is good.@Andy Ful BTW I tested some phishing links with Brave recently and network protection blocked some of them so it is definitely working.
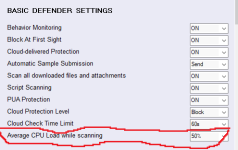
I have no idea and I do not know how Microsoft defines "average CPU load factor". Is it a time average or another average? Who knows?Hi Andy Ful, Windows Defender doesn't seem to respect this setting
Yes another weird thing from MicrosoftI have no idea and I do not know how Microsoft defines "average CPU load factor". Is it a time average or another average? Who knows?
Finally, something bypassed the WD on ConfigureDefender MAX Protection Level. As it could be guessed, this was a script (poy.js):
 app.any.run
app.any.run
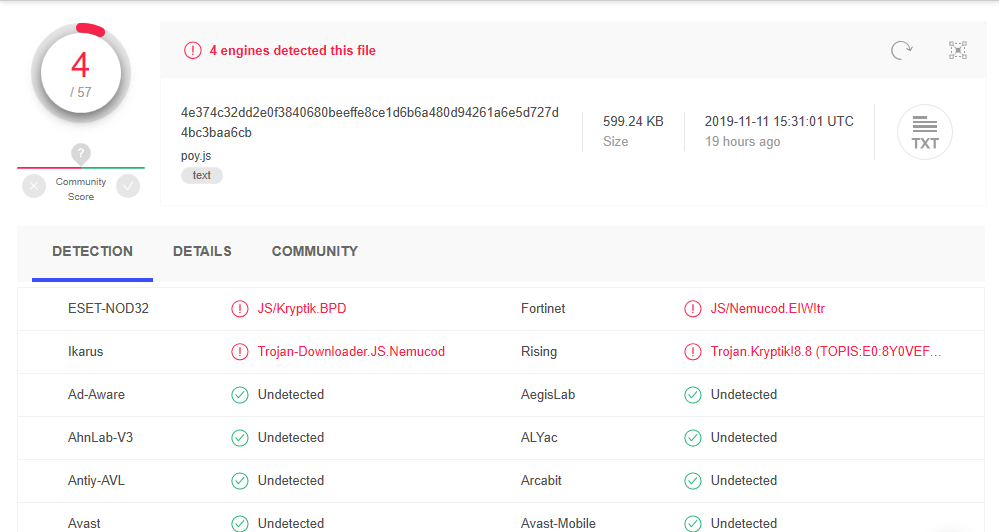
The persistence was done in a standard way by dropping the shortcut sideb.lnk to the start folder. The shortcut can start JScript payload with a fake file extension (.dat) dropped to the user Temp folder. The malware also created the autorun registry key that can execute the shortcut with Windows start. It probably behaved as an info-stealer and did not run any payload during the test. If the poy.js malware did directly run the payload (dropped to the start folder), then it could be blocked by ASR rules. Congrats to Eset for the quick signature of poy.js malware.
Edit.
Thank SeriousHoax, WD can detect this malware by signatures, now (WD deleted the malware after it has been unpacked):
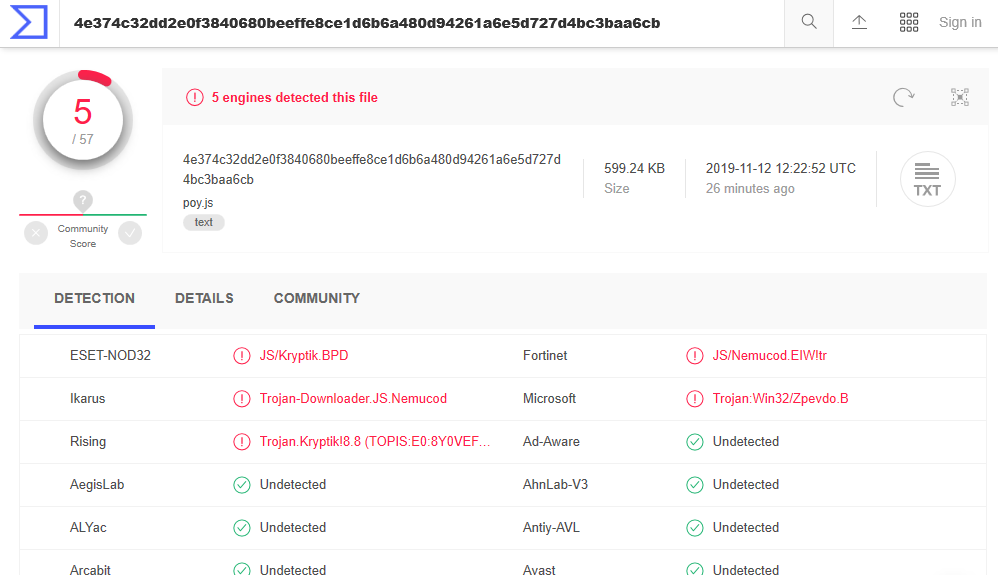

Analysis poy.js (MD5: 73646B9F16674BAB327AF8E66A21207A) Malicious activity - Interactive analysis ANY.RUN
Interactive malware hunting service. Live testing of most type of threats in any environments. No installation and no waiting necessary.
The persistence was done in a standard way by dropping the shortcut sideb.lnk to the start folder. The shortcut can start JScript payload with a fake file extension (.dat) dropped to the user Temp folder. The malware also created the autorun registry key that can execute the shortcut with Windows start. It probably behaved as an info-stealer and did not run any payload during the test. If the poy.js malware did directly run the payload (dropped to the start folder), then it could be blocked by ASR rules. Congrats to Eset for the quick signature of poy.js malware.
Edit.
Thank SeriousHoax, WD can detect this malware by signatures, now (WD deleted the malware after it has been unpacked):
Last edited:
- Apr 28, 2015
- 9,400
- 1
- 84,830
- 8,389
Congrats to Kaspersky, too.
Leave it to M$! Edge Chromium update blocked by its own ASR rules. In this case "Block credential stealing ... "
This ASR rule should not block the updates. It blocks access only to LSASS which is usually unimportant for installing/running/updating applications.Leave it to M$! Edge Chromium update blocked by its own ASR rules. In this case "Block credential stealing ... "
Anyway, I do not use this rule because it produces so many false positives, that you cannot see anything else in ConfigureDefernder Log.
Btw, everything that is blocked by this ASR rule "Block credential stealing from the Windows local security authority subsystem (lsass.exe)" is also blocked by ESET HIPS. I found that in ESET HIPS log. ESET usually blocks even more related to this lass.exe so maybe not false positives?This ASR rule should not block the updates. It blocks access only to LSASS which is usually unimportant for installing/running/updating applications.
Anyway, I do not use this rule because it produces so many false positives, that you cannot see anything else in ConfigureDefernder Log.
HIPS cannot recognize if something is malicious or not. ESET HIPS is not smarter than ASR.Btw, everything that is blocked by this ASR rule "Block credential stealing from the Windows local security authority subsystem (lsass.exe)" is also blocked by ESET HIPS. I found that in ESET HIPS log. ESET usually blocks even more related to this lass.exe so maybe not false positives?
It does not mean that it will be always false positive, but only in 99 % (or more).
Some notes about the last WD test made by @SeriousHoax:
1. AL_5014513395824.vbs
The malware uses WMI to run payload. This should be blocked by ASR if it did not auto terminate (ASR rule "Block process creations originating from PSExec and WMI commands").
https://app.any.run/tasks/a8184aa1-1892-4434-82a7-93bbba1364fa/
2.JD.vbe
The malware was prevented from using ADOB.Stream to download something and the script execution was interrupted with error (probably by ASR).
https://app.any.run/tasks/cd3a5e8a-9725-41aa-b3a1-9c554ee198a8/
3. JVC_21555.vbs
The malware (QBOT) is going to download and run a payload. This should be prevented by ASR rule "Impede JavaScript and VBScript to launch executables" (the name of this rule was changed by MS to "Block JavaScript or VBScript from launching downloaded executable content").
https://app.any.run/tasks/0e65507e-685a-4b68-9358-7dc619c8b4c2/
4.ps.ps1
This malicious script is going to download and run the EMOTET trojan. Blocked probably by ASR.
https://app.any.run/tasks/7e5fab0a-d591-4dde-b33f-2fe1501a3941/
5. Order_2718032693_Proforma_invoice.jar
This is Adwind RAT.
WD has allowed the malware on the initial stage, but it seems that the malicious actions were neutralized.
"This initial process executed js script which in turn ran one more js script and another .jar file. JS script also used Task Scheduler to run itself later. Jar file started a series of malicious activities such as using attrib.exe to mark files or folders as hidden, running VBS script files, changing the autorun value in the registry and more. It has been noted that sometimes Jar file runs a series of taskkill commands to shutdown processes by their names based on a list that contains names of system processes, names of common Anti-virus programs and analyzing programs, such as wireshark.exe, procexp.exe, processhacker.exe and so on."
https://any.run/malware-trends/adwin
Thanks to @SeriousHoax and other testers for their excellent job.
1. AL_5014513395824.vbs
The malware uses WMI to run payload. This should be blocked by ASR if it did not auto terminate (ASR rule "Block process creations originating from PSExec and WMI commands").
https://app.any.run/tasks/a8184aa1-1892-4434-82a7-93bbba1364fa/
2.JD.vbe
The malware was prevented from using ADOB.Stream to download something and the script execution was interrupted with error (probably by ASR).
https://app.any.run/tasks/cd3a5e8a-9725-41aa-b3a1-9c554ee198a8/
3. JVC_21555.vbs
The malware (QBOT) is going to download and run a payload. This should be prevented by ASR rule "Impede JavaScript and VBScript to launch executables" (the name of this rule was changed by MS to "Block JavaScript or VBScript from launching downloaded executable content").
https://app.any.run/tasks/0e65507e-685a-4b68-9358-7dc619c8b4c2/
4.ps.ps1
This malicious script is going to download and run the EMOTET trojan. Blocked probably by ASR.
https://app.any.run/tasks/7e5fab0a-d591-4dde-b33f-2fe1501a3941/
5. Order_2718032693_Proforma_invoice.jar
This is Adwind RAT.
WD has allowed the malware on the initial stage, but it seems that the malicious actions were neutralized.
"This initial process executed js script which in turn ran one more js script and another .jar file. JS script also used Task Scheduler to run itself later. Jar file started a series of malicious activities such as using attrib.exe to mark files or folders as hidden, running VBS script files, changing the autorun value in the registry and more. It has been noted that sometimes Jar file runs a series of taskkill commands to shutdown processes by their names based on a list that contains names of system processes, names of common Anti-virus programs and analyzing programs, such as wireshark.exe, procexp.exe, processhacker.exe and so on."
https://any.run/malware-trends/adwin
Thanks to @SeriousHoax and other testers for their excellent job.
WoW this is nice. While testing I do what I can with the tools I have to check for malicious activities. Since you know a lot more about WD, ASR etc, this thorough analysis of your is highly appreciated. Keep it upSome notes about the last WD test made by @SeriousHoax:
1. AL_5014513395824.vbs
The malware uses WMI to run payload. This should be blocked by ASR if it did not auto terminate (ASR rule "Block process creations originating from PSExec and WMI commands").
https://app.any.run/tasks/a8184aa1-1892-4434-82a7-93bbba1364fa/
2.JD.vbe
The malware was prevented from using ADOB.Stream to download something and the script execution was interrupted with error (probably by ASR).
https://app.any.run/tasks/cd3a5e8a-9725-41aa-b3a1-9c554ee198a8/
3. JVC_21555.vbs
The malware (QBOT) is going to download and run a payload. This should be prevented by ASR rule "Impede JavaScript and VBScript to launch executables" (the name of this rule was changed by MS to "Block JavaScript or VBScript from launching downloaded executable content").
https://app.any.run/tasks/0e65507e-685a-4b68-9358-7dc619c8b4c2/
4.ps.ps1
This malicious script is going to download and run the EMOTET trojan. Blocked probably by ASR.
https://app.any.run/tasks/7e5fab0a-d591-4dde-b33f-2fe1501a3941/
5. Order_2718032693_Proforma_invoice.jar
This is Adwind RAT.
WD has allowed the malware on the initial stage, but it seems that the malicious actions were neutralized.
"This initial process executed js script which in turn ran one more js script and another .jar file. JS script also used Task Scheduler to run itself later. Jar file started a series of malicious activities such as using attrib.exe to mark files or folders as hidden, running VBS script files, changing the autorun value in the registry and more. It has been noted that sometimes Jar file runs a series of taskkill commands to shutdown processes by their names based on a list that contains names of system processes, names of common Anti-virus programs and analyzing programs, such as wireshark.exe, procexp.exe, processhacker.exe and so on."
https://any.run/malware-trends/adwin
Thanks to @SeriousHoax and other testers for their excellent job.
I will try, but I do not think that it is necessary to understand the tests on Malware Hub. I was just curious about what these malware samples could do.WoW this is nice. While testing I do what I can with the tools I have to check for malicious activities. Since you know a lot more about WD, ASR etc, this thorough analysis of your is highly appreciated. Keep it up
They've been crazy crazy good at this especially since v13. Most of the zero days I analyze are dynamically generated Mac malware and I've found dozens in the last week where VT detection rates are 2 or 3 out of 69 and ESET is always amongst the 2 that detect it, and it detects whatever you feed at it. They somehow manage to detect zero-day variations of existing malware using generic signatures but they don't suffer from frequent false positives which is usually what happens with other vendors' AI-based engines (like Symantec's AdvML.x signatures, which seem to nab corporate Powershell scripts once a month or two if you crawl back on their forums)Congrats to Eset for the quick signature of poy.js malware.
I was not sure where to mention this, while testing Windows Defender in Shadow Defender, its Cloud protection is not working. That's why I was not able to test the last malware pack. Tried again today and same result. I had this problem before and was fixed automatically. So, I won't be able to test WD until that and might test other AVs in the meantime.
Last edited:
This issue with ShadowDefender should be solved by leaving the ShadowMode, setting WD with ConfigureDefender, checking/correcting the settings in WD Security Center, restarting the computer, and entering the ShadowMode again.I was not sure where to mention this, while testing Windows Defender in Shadow Defender, its Cloud protection is not working. That's why I was not able to test the last malware pack. Tried again today and same result. I had this problem before and was fixed automatically. So, I won't be able to test WD until that and might test other AVs in the meantime.
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0