F
ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Finally, I could find out what happened. For an unknown reason, WD flagged all ConfigureDefender repository on GitHub as malicious (false positive), despite the fact that all files in the repository (including ConfigureDefender installers) are detected as clean. This situation could probably happen when the files were uploaded to GitHub and next whitelisted in Microsoft via the Developer channel. If one of them was flagged in the beginning as malicious (false positive) then also was all zipped repository (ConfigureDefender-master.zip). This file has independent detection and whitelisting all files in the repository in Microsoft does not remove the false positive.
I have just submitted this repository to Microsoft for whitelisting - the false positive will be removed soon.
I have just submitted this repository to Microsoft for whitelisting - the false positive will be removed soon.
Last edited:
The submission looks now as follows:
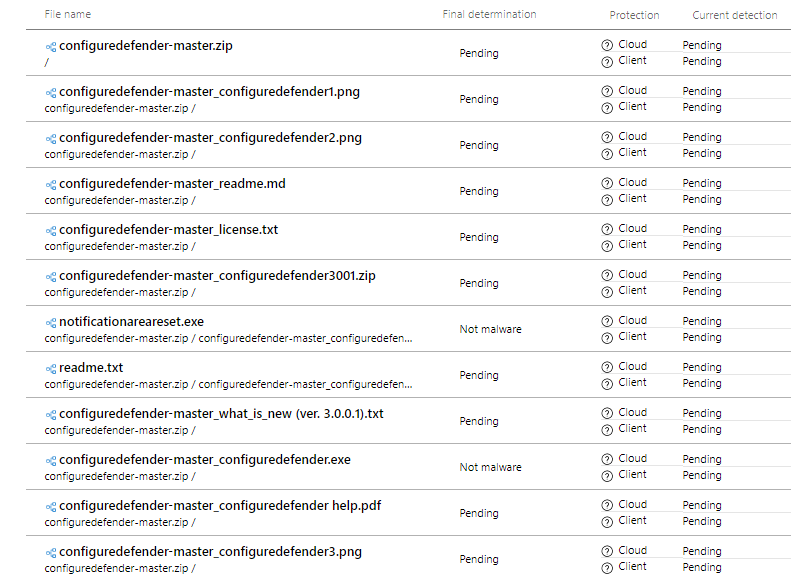
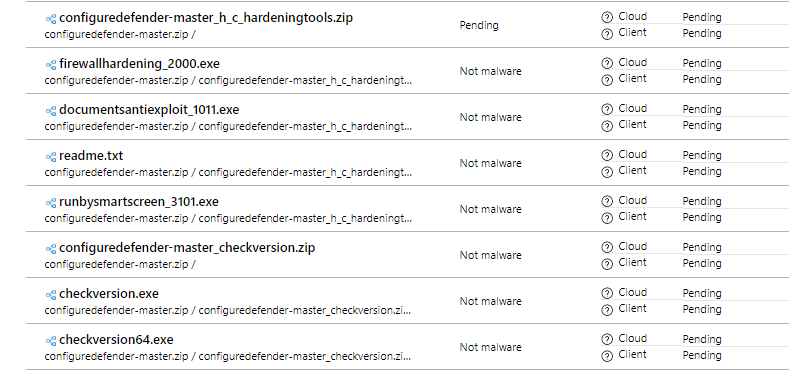
The entries with "Not malware" were already whitelisted in Microsoft (several months ago). Others were not whitelisted, yet.
The entries with "Not malware" were already whitelisted in Microsoft (several months ago). Others were not whitelisted, yet.
Wow, that was quick.
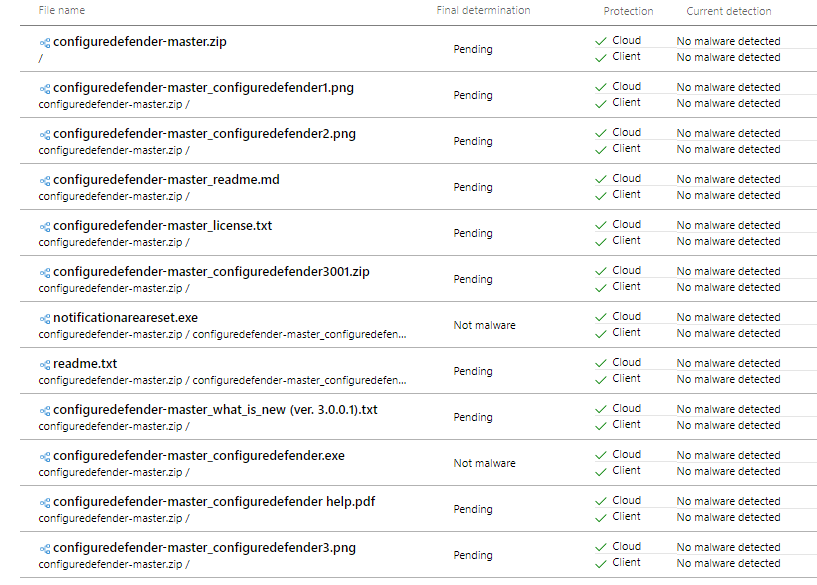
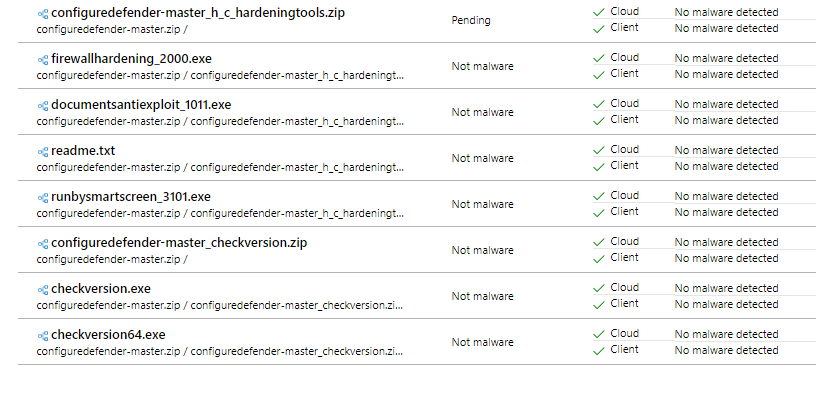
All files in the repository are clean in the cloud and client. Let's wait for the final determination.
All files in the repository are clean in the cloud and client. Let's wait for the final determination.
I have just checked the submission. False-positive removed. I can download the repository without a Microsoft Defender alert with AntivirusSignatureVersion: 1.329.2695.0
Thanks guys (from MT and Wilderssecurity) for helping me to solve this strange issue.
I never saw a false positive (ZIP archive) which was allowed by SmartScreen + PUA protection in Edge and contained only clean files, but anyway was flagged by Defender as malicious.

The positive is a quick reaction of Microsoft to remove the false positive (only a few hours).
Thanks guys (from MT and Wilderssecurity) for helping me to solve this strange issue.
I never saw a false positive (ZIP archive) which was allowed by SmartScreen + PUA protection in Edge and contained only clean files, but anyway was flagged by Defender as malicious.
The positive is a quick reaction of Microsoft to remove the false positive (only a few hours).
Anyway, adding malware exclusions like in the case of the DeroHE ransomware payload (iobit.dll), can have an impact on malware persistence.The idea of adding Defender exclusions can be dangerous in targeted attacks. It seems rather stupid in the wide-spread attacks:
In the targeted attacks, this method can be used for lateral movement and can increase the time of penetrating the Enterprise network until finally it will be detected by Defender.
- The computer is already highly compromised, because malware has got high privileges.
- Adding exclusions by the malware do not stop the behavior monitoring (protected by Tamper Protection), so the malware can be still detected in the cloud.
- Adding exclusions increases the chances of the proper detection in the cloud.
In the case of the IOBIT malware, the attacker did not get any gain of adding exclusions.
In most cases, the post-execution behavior-based detections in Microsoft cloud can detect the malware after some minutes. If the malware is not excluded, then the infection chain will be killed and the encryption will be often interrupted. If the malware is excluded in the meantime, then it will survive and the encryption will continue.
In the case of ransomware in the home environment, this is not so important because the user's files are often encrypted before post-execution detection will work. But in businesses, this difference can be crucial because there are much more data and the full encryption can last several hours.
So, adding malware exclusions can have two opposite causes:
- Negative for the attacker:
Exclusions are suspicious and can increase the malware detection on the pre-execution stage. This can be an important disadvantage especially when advanced WD settings are enabled (like higher Cloud Protection Level or ASR rule "Use advanced protection against ransomware"). - Positive for the attacker: exclusions can increase the malware persistence.
Last edited:
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
ConfigureDefender and its options reviewed:

 www.computerworld.com
www.computerworld.com
Decoding Microsoft Defender’s hidden settings
Though many Windows 10 users opt for third-party antivirus protection, those who use Microsoft Defender may not be getting all of the protection they could. Here’s how to check your settings and what to change.
As you scroll through the tool, you’ll notice a section that covers control for Microsoft’s Attack Surface Reduction (ASR) rules. You’ll also note that many of them are disabled. These are among the most overlooked settings in Microsoft Defender. While you will need an Enterprise license to fully expose monitoring across your network, even standalone computers and small businesses can take advantage of these settings and protections. As noted in a recent document, Microsoft Defender Attack Surface Reduction recommendations, there are several settings that should be safe for most environments.
The recommended settings to enable include:
Turning these settings “on” — meaning they block the action — usually won’t adversely impact even standalone computers. You can use the tool to set these values and review any impact on your system. Most likely you won’t even realize they’re better protecting you.
- Block untrusted and unsigned processes that run from USB.
- Block Adobe Reader from creating child processes.
- Block executable content from email client and webmail.
- Block JavaScript or VBScript from launching downloaded executable content.
- Block credential stealing from the Windows local security authority subsystem (lsass.exe).
- Block Office applications from creating executable content.
Next, there are settings that should be reviewed for your environment to ensure they don’t interfere with your business or computing needs. These settings are:
In particular, in an environment that includes Outlook and Teams a great number of events were registered if the setting of “Block all office applications from creating child processes” was turned on. Again, you can try these and see if you are affected.
- Block Office applications from injecting code into other processes.
- Block Win32 API calls from Office Macros.
- Block all Office applications from creating child processes.
- Block execution of potentially obfuscated scripts.
The settings to watch out for include these:
These settings should be reviewed to make sure they don’t hinder line-of-business apps and business processes. For example, while “Use advanced protection against ransomware” sounds like a setting everyone would want, in one business where a team had developed internal-use software, it created issues with developer workflows. (This setting specifically scans executable files entering the system to determine whether they are trustworthy. If the files resemble ransomware, this rule blocks them from running.)
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion.
- Use advanced protection against ransomware.
- Block process creations originating from PSExec and WMI-commands.
- Block all Office communication applications from creating child processes.
The setting, “Block process creations originating from PSExec and WMI-commands,” was especially troublesome, according to the authors. Not only did the setting lead to a large number of events in the audit log, it is incompatible with Microsoft Endpoint Configuration Manager, as the configuration manager client needs WMI commands to function properly.
Thanks.
In the article is included an interesting link about ASR rules after using them for two years in the business environment:
Microsoft Defender Attack Surface Reduction recommendations | Palantir Blog (medium.com)
In the article is included an interesting link about ASR rules after using them for two years in the business environment:
Microsoft Defender Attack Surface Reduction recommendations | Palantir Blog (medium.com)
F
ForgottenSeer 85179
Sounds like "Block process creations originating from PSExec and WMI commands" is only problematic in enterprise environments.Thanks.
In the article is included an interesting link about ASR rules after using them for two years in the business environment:
Microsoft Defender Attack Surface Reduction recommendations | Palantir Blog (medium.com)
I enable this rule and will test it some days
One of the users who tested ConfigureDefender reported that this rule had significantly increased the boot time of his laptop without any record in the Log. I suspect that also the laptop firmware can use sometimes WMI.Sounds like "Block process creations originating from PSExec and WMI commands" is only problematic in enterprise environments.
I enable this rule and will test it some days
If these issues are absent, then enabling this rule is recommended.
Last edited:
F
ForgottenSeer 85179
I don't compare time before and now but looks like boot time is equal.One of the users who tested ConfigureDefender reported that this rule had significantly increased the boot time of his laptop without any record in the Log. I suspect that also the laptop firmware can use sometimes WMI.
If these issues are absent, then enabling this rule is recommended.
But of course, this may differ for weaker PCs.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Those settings are a little bit different from your high profile.Thanks.
In the article is included an interesting link about ASR rules after using them for two years in the business environment:
Microsoft Defender Attack Surface Reduction recommendations | Palantir Blog (medium.com)
Especially: not enabling use advanced protection against ransomware and enabling block credential stealing from the Windows local security authority subsystem (lsass.exe).
Are you planning to change those settings on the high profile?
F
ForgottenSeer 85179
These settings are from companie side of view, so they have different use caseThose settings are a little bit different from your high profile.
Especially: not enabling use advanced protection against ransomware and enabling block credential stealing from the Windows local security authority subsystem (lsass.exe).
Are you planning to change those settings on the high profile?
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Yes, I know that, but I had for example a block from the advanced ransomware protection on my son's computer when updating an application.These settings are from companie side of view, so they have different use case
So, is that setting still needed/recommended for a computer from a normal/home user?
I'm interested in Andy's opinion.
He chose those settings for a reason.
The HIGH Protection Level is optimal for the home environment as a starting point. Some users will have to use exclusions or disable one or more rules (like you), and others will be able to enable additional rules (like @SecurityNightmares). This can depend on the software installed on the computer.Yes, I know that, but I had for example a block from the advanced ransomware protection on my son's computer when updating an application.
So, is that setting still needed/recommended for a computer from a normal/home user?
I'm interested in Andy's opinion.
He chose those settings for a reason.
By the way, what was this application?
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
It was Elgato Stream Deck Software.The HIGH Protection Level is optimal for the home environment as a starting point. Some users will have to use exclusions or disable one or more rules (like you), and others will be able to enable additional rules (like @SecurityNightmares). This can depend on the software installed on the computer.
By the way, what was this application?

Elgato Stream Deck Software Release Notes
======================================================================= Source: https://help.elgato.com/admin/content-management/articles/2793637-elgato-stream-deck-software-release-notes/...
 help.elgato.com
help.elgato.com
Could you make an exclusion?It was Elgato Stream Deck Software.

Elgato Stream Deck Software Release Notes
======================================================================= Source: https://help.elgato.com/admin/content-management/articles/2793637-elgato-stream-deck-software-release-notes/...help.elgato.com
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
The software is now up to date. It was just the internal updater that triggered that rule.Could you make an exclusion?
Maybe next time setting it on audit for the update and back to enabled afterwards creates an automatic exclusion?
The blocked updater executable should be in the ConfogireDefender Log. You can search the log via the "ransomware" string. If the blocked entry is in the application folder, then you may exclude it. But, if the updates are rare, then you can turn this rule to Audit temporarily and make the update without exclusions as well.The software is now up to date. It was just the internal updater that triggered that rule.
Maybe next time setting it on audit for the update and back to enabled afterwards creates an automatic exclusion?
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
There was a question about ConfigureDefender at Wilders:

 www.wilderssecurity.com
My answer was:
www.wilderssecurity.com
My answer was:

 www.wilderssecurity.com
Is there a possibility (in a future version perhaps) to highlight the set protection level?
www.wilderssecurity.com
Is there a possibility (in a future version perhaps) to highlight the set protection level?
The same request could be made for Hard_Configurator.
Is it on recommended, one of the profiles or custom settings?
(EDIT: typo)
Recently installed Configure Defender on Windows 10 (Windows Defender fully operating) and I think I have set it on High setting by following the instructions in the folder ie High Button, then Refresh Button then Reboot
When I then open Config Defender there is no way I can determine which level Config Defender is set to ie Default, High, Max. I would have expected at least the High Button to be highlighted.
The image I have enclosed shows Basic Defender Settings underneath the three Buttons.
My question is:- How do I know which Protection Level has been set?
Is there something I am not doing?
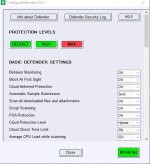
ConfigureDefender - for configuring Windows built-in Defender settings
Hi @ Wilders Recently installed Configure Defender on Windows 10 (Windows Defender fully operating) and I think I have set it on High setting by...
It's on High.
Click on Default, look at the values show. Then click on High and look again at the values shown.
ConfigureDefender - for configuring Windows built-in Defender settings
Hi @ Wilders Recently installed Configure Defender on Windows 10 (Windows Defender fully operating) and I think I have set it on High setting by...
The same request could be made for Hard_Configurator.
Is it on recommended, one of the profiles or custom settings?
(EDIT: typo)
Last edited:
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0