Are you using WindowsSimpleHardening or Hard_Configurator along with CD? Try right clicking the icon and see if a Install By Smartscreen option is there or run as administrator. There are lots of browser options out there and if your using Microsoft Defender anyway, that's best accompanied with Chromium-Edge.You think I didn't try running the installer outside the browser immediately after?
If it's not MpEngine, then it's something from Windows 10, outside Defender.
ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Yes, this might happen when you have several executables in the folder. When you open the folder (first time after starting Windows session) these executables are checked by Defender. Some of them (not checked yet) can be suspended.You think I didn't try running the installer outside the browser immediately after?
It was probably MAPS, block at first sight, MpEngine... I think it's not being blocked, but it maybe it's being suspended to be analyzed, but something doesn't work right and immediately gives the error "installer cold not launch".
None. I manually changed group policies, following a video, because I wanted to learn exactly what I was changing. I did this: and this:Are you using WindowsSimpleHardening or Hard_Configurator along with CD? Try right clicking the icon and see if a Install By Smartscreen option is there or run as administrator. There are lots of browser options out there and if your using Microsoft Defender anyway, that's best accompanied with Chromium-Edge.
Running as administrator didn't work, I tried.
There were no executables, only a few documents and video files.Yes, this might happen when you have several executables in the folder. When you open the folder (first time after starting Windows session) these executables are checked by Defender. Some of them (not checked yet) can be suspended.
OK. You solved your problem. Let's go back to the ConfigureDefender topic.
Why wasting so much time while it could be so easy hardening Windows/Defender with Andy's tools in which he puts so much effort? 
Because I wanted to know what I was changing. I found it doesn't really explain what is doing, group policies have better explanation, and there aren't many policies to change, it's a quick thing to do.Why wasting so much time while it could be so easy hardening Windows/Defender with Andy's tools in which he puts so much effort?
I can assure you that Simple Windows Hardening does it's job perfectly fine, thats why so many people are using it here. Same with Configure Defender... And if you face any issues, you can revert the changes easily.Because I wanted to know what I was changing. I found it doesn't really explain what is doing, group policies have better explanation, and there aren't many policies to change, it's a quick thing to do.
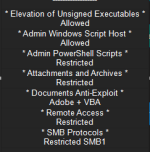
I also think that the information that is provided within the tool, is enough for people to understand what it's doing:
Last edited:
The more detailed info about SWH options is included in the manual:
https://github.com/AndyFul/Hard_Con...rdening/Simple Windows Hardening - Manual.pdf
The comprehensive info about SRP and Registry changes related to hardening can be found in the H_C documentation:
https://github.com/AndyFul/Hard_Configurator/tree/master/Documentation
The info about Defender ASR rules can be found in articles (included on the ConfigureDefender GitHub webpage):

 medium.com
medium.com

 techcommunity.microsoft.com
techcommunity.microsoft.com
https://github.com/AndyFul/Hard_Con...rdening/Simple Windows Hardening - Manual.pdf
The comprehensive info about SRP and Registry changes related to hardening can be found in the H_C documentation:
https://github.com/AndyFul/Hard_Configurator/tree/master/Documentation
The info about Defender ASR rules can be found in articles (included on the ConfigureDefender GitHub webpage):

Microsoft Defender Attack Surface Reduction Recommendations
Palantir’s Infosec team shares their tips and best practices
 medium.com
medium.com

Use attack surface reduction rules to prevent malware infection - Microsoft Defender for Endpoint
Attack surface reduction rules can help prevent exploits from using apps and scripts to infect devices with malware.
docs.microsoft.com
Microsoft Defender for Endpoint Blog | Microsoft Community Hub
Microsoft Defender for Endpoint disrupts ransomware with industry-leading endpoint security, providing comprehensive protection across all platforms and...
Last edited:
Could someone of you guys check, if the disabling of telemetry of windows will cause defender to prevent that?
I guess the adguard desktop caused to run that commandline and md prevented it from running , right?
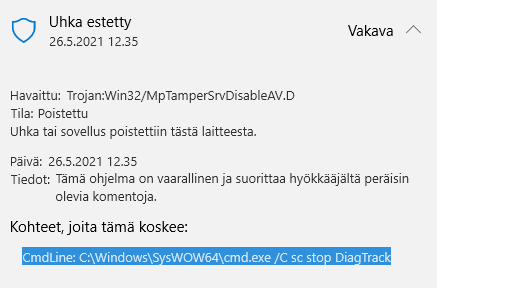
I guess the adguard desktop caused to run that commandline and md prevented it from running , right?
On my system it didn't flag it like 2 weeks ago...Could someone of you guys check, if the disabling of telemetry of windows will cause defender to prevent that?
I guess the adguard desktop caused to run that commandline and md prevented it from running , right?
View attachment 258443
This CmdLine is also blocked by Defender on my computer.Could someone of you guys check, if the disabling of telemetry of windows will cause defender to prevent that?
I guess the adguard desktop caused to run that commandline and md prevented it from running , right?
View attachment 258443
New ASR rule:
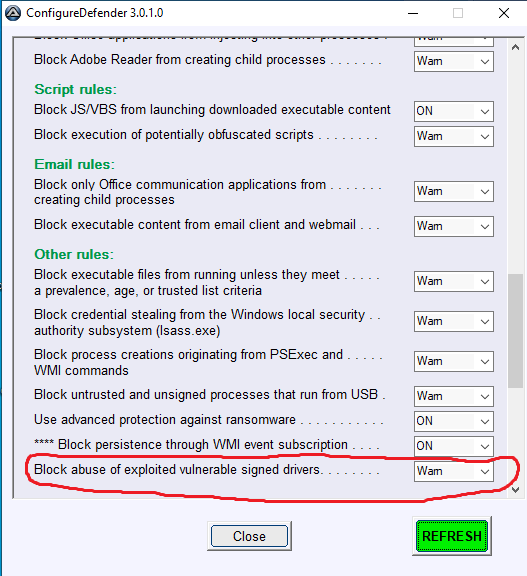
This rule will be set as follows:
DEFAULT -------------> Disabled
HIGH -------------------> Audit
INTERACTIVE -----> Warn
MAX -------------------> ON
This rule will be set as follows:
DEFAULT -------------> Disabled
HIGH -------------------> Audit
INTERACTIVE -----> Warn
MAX -------------------> ON
Where do we find version 3.0.1.0? I'm still running 3.0.0.1. Thanks.
I plan to publish the new version in June.Where do we find version 3.0.1.0? I'm still running 3.0.0.1. Thanks.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Thanks AndyI plan to publish the new version in June.
How does the new warn option work?
Do you get a popup or something like that where you can decide if you allow or deny something or just info that a rule is triggered?
It works like most ASR rules. If it is set to Warn, then the driver is initially blocked and you can see the alert, that allows unblocking. The next time the driver will be allowed. One can also use ASR exclusions. The blocked driver can be submitted for analysis to Microsoft.Thanks Andy
How does the new warn option work?
Do you get a popup or something like that where you can decide if you allow or deny something or just info that a rule is triggered?
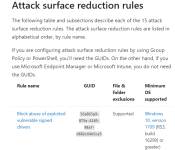


Use attack surface reduction rules to prevent malware infection - Microsoft Defender for Endpoint
Attack surface reduction rules can help prevent exploits from using apps and scripts to infect devices with malware.
docs.microsoft.com
Last edited by a moderator:
I have overlooked that this rule does not block the drivers already installed on the system. So, maybe it will be better to set it to ON in the HIGH preset....
This rule will be set as follows:
DEFAULT -------------> Disabled
HIGH -------------------> Audit
INTERACTIVE -----> Warn
MAX -------------------> ON
DEFAULT -------------> Disabled
HIGH -------------------> ON
INTERACTIVE -----> Warn
MAX -------------------> ON
Last edited:
F
ForgottenSeer 85179
makes sense to me but an enforcement would be nice.I have overlooked that this rule does not block the drivers already installed on the system. So, maybe it will be better to set it to ON in the HIGH preset.
Looks like i need to start from scratch soon...
Microsoft disabled its own PowerShell cmdlets for managing ASR rules (Disabled, AuditMode) when Tamper Protection is enabled. When the user opens PowerShell console and tries to set any ASR rule to Disabled or Audit Mode, then Defender blocks the cmdlet and Logs the event as :
Trojan:Win32/MpTamperASRRule.PSA (for AuditMode attempt)
Trojan:Win32/MpTamperASRRule.PSD (for disabling attempt)
This does not affect the PowerShell cmdlets when the user wants to enable ASR rules.
For now, these changes do not affect the functionality of <DEFAULT>, <HIGH>, <INTERACTIVE>, <MAX> options in ConfigureDefender. They work as usual. Anyway, when the user wants to set a particular ASR rule manually to Disabled or Audit, Defender will block the attempt with an alert. It is still possible to do it when Tamper Protection is temporarily disabled.
I will try to negotiate with Microsoft to whitelist ConfigureDefender in Tamper Protection, but the chances for that are not great.
Furthermore, I think that Microsoft is doing the right thing, except labeling the action as Trojan.
Trojan:Win32/MpTamperASRRule.PSA (for AuditMode attempt)
Trojan:Win32/MpTamperASRRule.PSD (for disabling attempt)
This does not affect the PowerShell cmdlets when the user wants to enable ASR rules.
For now, these changes do not affect the functionality of <DEFAULT>, <HIGH>, <INTERACTIVE>, <MAX> options in ConfigureDefender. They work as usual. Anyway, when the user wants to set a particular ASR rule manually to Disabled or Audit, Defender will block the attempt with an alert. It is still possible to do it when Tamper Protection is temporarily disabled.
I will try to negotiate with Microsoft to whitelist ConfigureDefender in Tamper Protection, but the chances for that are not great.
Furthermore, I think that Microsoft is doing the right thing, except labeling the action as Trojan.
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0