Problem solved. Microsoft simply removed these detections from PowerShell with the security intelligence update version 1.341.296.0.

ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Do you think completely removing the detection is a good decision considering how often malware author tries to disable protection (or parts of it) or create exclusions?Problem solved. Microsoft simply removed these detections from PowerShell with the security intelligence update version 1.341.296.0.

Hi just wanted to ask ,I got a clean install done of win10 pro and I am running WD for a test run ,just didn't want to install a third part av .I use this computer 1-2 times a week an older machine.Is WD enough with simplewall or should I add something like Wisevector or Voodooshield?THks
You have to open a thread about your config. Like for example:Hi just wanted to ask ,I got a clean install done of win10 pro and I am running WD for a test run ,just didn't want to install a third part av .I use this computer 1-2 times a week an older machine.Is WD enough with simplewall or should I add something like Wisevector or Voodooshield?THks

SECURITY: Complete - SecurityNightmares's Security Config 2021
New version of my previous one. My setup focuses on a minimal attack surface. I also rely on the following rule from the Hard_Configurator manual (SETUP OVERKILL part): Adding more advanced features is usually not necessary and often ends with overkill, incompatibilities, and disappointment...
 malwaretips.com
malwaretips.com
It is good for Administrators. A similar problem is for other AVs in Enterprises. Many of them have an option to enable external AV management, for example:Do you think completely removing the detection is a good decision considering how often malware author tries to disable protection (or parts of it) or create exclusions?
Starting and stopping Kaspersky Endpoint Security
For Home users, it would be better to block these changes when Tamper Protection is enabled.
In such a case, the ConfigureDefender could be run only when Tamper Protection has been disabled (no problem). Anyway, there are not many Home users who use ASR rules.
Last edited:
I missed this reply. I agree with what you say. I have seen Microsoft adding, removing and adding signatures again in the past for some not so dangerous samples. So I won't be surprised if Microsoft changes their decision again regarding this in the future.It is good for Administrators. A similar problem is for other AVs in Enterprises. Many of them have an option to enable external AV management, for example:
Starting and stopping Kaspersky Endpoint Security
support.kaspersky.com
For Home users, it would be better to block these changes when Tamper Protection is enabled.
In such a case, the ConfigureDefender could be run only when Tamper Protection has been disabled (no problem). Anyway, there are not many Home users who use ASR rules.
F
ForgottenSeer 85179
After/ with new AMD graphic driver update installation and Windows reboot i got that in Defender:
anything i should do? Installation was successful and i can open AMD center.
Blocked APP or process: svchost.exe
Blocked by: Reducing the attack surface
Rule: Block executable files unless they meet the criteria for
frequency, age or trustworthiness
Affected items: C:\Program Files\AMD\CNext\CNext\cpumetricsserver.exe
Blocked APP or process: AUEPMaster.exe
Blocked by: Reducing the attack surface
Rule: Stealing credentials from the local Windows
security subsystem (Isass.exe).
Affected items: C:\Windows\System32\lsass.exe
Blocked APP or process: atieclxx.exe
Blocked by: Reducing the attack surface
Rule: Stealing credentials from the local Windows
security subsystem (Isass.exe).
Affected items: C:\Windows\System32\lsass.exe
Blocked APP or process: atiesrxx.exe
Blocked by: Reducing the attack surface
Rule: Stealing credentials from the local Windows
security subsystem (Isass.exe).
Affected items: C:\Windows\System32\lsass.exe
anything i should do? Installation was successful and i can open AMD center.
The first will not be blocked after a few days. It can be related to CPU optimization or overclocking (I am not sure).
The second is AMD telemetry (not important):
The last two are the parts of ATI External Events Utility.
https://www.file.net/process/atieclxx.exe.html
https://www.file.net/process/atiesrxx.exe.html
It can have an impact on FreeSync.
"AMD External Events Utility" service allows FreeSync to run for only borderless windowed games for new AMD drivers. Without this service FreeSync will work for fullscreen games."
ASR LASS rule does not prevent these executables from running, but only blocks access to LSASS. I do not know if it can have an impact on FreeSync.
The second is AMD telemetry (not important):
The last two are the parts of ATI External Events Utility.
https://www.file.net/process/atieclxx.exe.html
https://www.file.net/process/atiesrxx.exe.html
It can have an impact on FreeSync.
"AMD External Events Utility" service allows FreeSync to run for only borderless windowed games for new AMD drivers. Without this service FreeSync will work for fullscreen games."
ASR LASS rule does not prevent these executables from running, but only blocks access to LSASS. I do not know if it can have an impact on FreeSync.
Last edited:
In a few weeks, I plan to push the beta version.Hello, when is the new version coming out?
Defender's ASR rules in action. As an example, I have chosen the spam campaign delivering banking trojans (IcedID and Qbot). The scenario of the attack is very common in the wild.

 securelist.com
securelist.com
The malware delivery starts as usual via email attachment or the link to the hacked website. In both cases, the ZIP archive with an Excel document is downloaded to disk. When the user opens the document and allows macros (Excel 4.0), the malware loader is downloaded and executed by Excel (directly or via LolBin) - in both cases, the child process is created. So, the infection chain is stopped by the ASR rule "Block Office applications from creating child processes".

Malicious spam campaigns delivering banking Trojans
In mid-March 2021, we observed two new spam campaigns delivering banking Trojans. The payload in most cases was IcedID, but we have also seen a few QBot (aka QakBot) samples.
The malware delivery starts as usual via email attachment or the link to the hacked website. In both cases, the ZIP archive with an Excel document is downloaded to disk. When the user opens the document and allows macros (Excel 4.0), the malware loader is downloaded and executed by Excel (directly or via LolBin) - in both cases, the child process is created. So, the infection chain is stopped by the ASR rule "Block Office applications from creating child processes".
Last edited:
Defender's ASR rules in action.

The ASR rule mentioned in the article is a new one (will be added to HIGH, INTERACTIVE, and MAX presets in the ConfigureDefender soon). Network Protection can be enabled via ConfigureDefender.
About the malware:

Protecting customers from a private-sector offensive actor using 0-day exploits and DevilsTongue malware | Microsoft Security Blog
The Microsoft Threat Intelligence Center (MSTIC) alongside the Microsoft Security Response Center (MSRC) has uncovered a private-sector offensive actor, or PSOA, that we are calling SOURGUM in possession of now-patched, Windows 0-day exploits (CVE-2021-31979 and CVE-2021-33771).
www.microsoft.com
Enabling the attack surface reduction rule “Block abuse of exploited vulnerable signed drivers” in Microsoft Defender for Endpoint blocks the driver that DevilsTongue uses. Network protection blocks known SOURGUM domains.
The ASR rule mentioned in the article is a new one (will be added to HIGH, INTERACTIVE, and MAX presets in the ConfigureDefender soon). Network Protection can be enabled via ConfigureDefender.
About the malware:
As we shared in the Microsoft on the Issues blog, Microsoft and Citizen Lab have worked together to disable the malware being used by SOURGUM that targeted more than 100 victims around the world including politicians, human rights activists, journalists, academics, embassy workers, and political dissidents. To limit these attacks, Microsoft has created and built protections into our products against this unique malware, which we are calling DevilsTongue.
There are many good places.other good place is sordum.org
Anyway, this particular thread is specifically devoted to the development, capabilities, and issues related to ConfigureDefender. I do not plan to move to sordum.org .
Last edited:
Hi Andy!
I learned a couple of months ago that it's possible to make Microsoft Defender log hash of files detected by its real-time protection. You may not or may know this already.
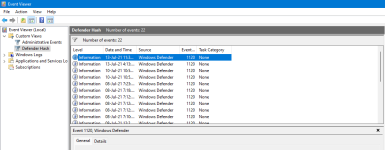
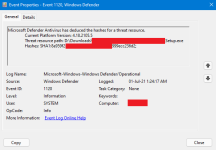
Now can you make the next version of Configure Defender's log to also show/log event id 1120 for those who have it enabled.
I'm someone who finds logging of hash in any AV very useful especially when it detects something false positive so that I can verify it on sites like VirusTotal. Unfortunately, most AVs don't log hashes of detected threats. Some exceptions are ESET, Kaspersky, and maybe one or two other.
Anyway, I think many users will find this info helpful.
I learned a couple of months ago that it's possible to make Microsoft Defender log hash of files detected by its real-time protection. You may not or may know this already.
After this, restart the system and from now on when Defender's real-time protection detects something a log containing the file's sha-1 hash will be created in the system log.On Windows 10 and up, create the following registry subkey:
Registry location: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender
DWORD name: ThreatFileHashLogging
DWORD value: 1
I have created my own custom log to find it quickly.EventID 1120 is recorded in the System log. (Microsoft-Windows-Windows Defender/Operational)


Now can you make the next version of Configure Defender's log to also show/log event id 1120 for those who have it enabled.
I'm someone who finds logging of hash in any AV very useful especially when it detects something false positive so that I can verify it on sites like VirusTotal. Unfortunately, most AVs don't log hashes of detected threats. Some exceptions are ESET, Kaspersky, and maybe one or two other.
Anyway, I think many users will find this info helpful.
Last edited:
I will look at this. The hashes can be useful when inspecting several files. The cons will be more events in the log. For a single file, I simply upload it to VirusTotal and look at the hash in the report.Hi Andy!
I learned a couple of months ago that it's possible to make Microsoft Defender log hash of files detected by its real-time protection. You may not or may know this already.
Yeah but the problem is, when you restore something from Defender's quarantine it automatically gets added into temporary exclusions and there's no simple way to delete or even see that. I can only see those exclusions in the registry. As long as the file is not moved or deleted from that folder the exclusions remain there. I don't like this behavior. So when the hash is logged I can simply copy and paste it in Virustotal without restoring it from the quarantine.I will look at this. The hashes can be useful when inspecting several files. The cons will be more events in the log. For a single file, I simply upload it to VirusTotal and look at the hash in the report.
Good point. This also solves another problem. The PUA, HackTool, and some other malware types are not logged (severe and high-ranked malware are usually logged). But, PUA (and others) are not quarantined.Yeah but the problem is, when you restore something from Defender's quarantine it automatically gets added into temporary exclusions and there's no simple way to delete or even see that.
OK, I will think about it.
Last edited:
Helping the people on other forums, I would like to recall that Defender with ConfigureDefender settings is already tested by professional AV Labs:
MRG Effitas tests are made specifically for or Enterprises (include a special Fileless Malware test). So, the strength of ASR rules is tested, too. I made the cumulative results for several tests, here:

 malwaretips.com
malwaretips.com
AV-Comparatives settings in these tests are similar to ConfigureDefender HIGH settings but with disabled ASR rules (HIGH settings are stronger, especially in Enterprises). I made the cumulative results for several tests, here:

 malwaretips.com
malwaretips.com
Edit1
Changed the link to the recent scorings of AV-Comparatives Business Security tests.
Edit2
Simple conclusion. In AV-Comparatives tests, the protection of Defender on HIGH settings is comparable to KIS on default settings. I think, that a similar comparison is probably true in the daily life of Home users.
- MRG Effitas in 360 Degree Assessment & Certification tests (ConfigureDefender MAX settings)
- AV-Comparatives in Business Security tests (Cloud Protection Level set to High, no ASR rules, WDBP extension installed in Chrome).
MRG Effitas tests are made specifically for or Enterprises (include a special Fileless Malware test). So, the strength of ASR rules is tested, too. I made the cumulative results for several tests, here:

MRG Effitas - MRG Effitas 360 Degree Assessment & Certification – Q3 2020
This Programme is called “360 Assessment & Certification” since it tests the security applications capabilities with a full spectrum of attack vectors. In the 360 Assessment, trojans, backdoors, spyware, financial malware, ransomware and “other” malicious applications are all used. Along side...
 malwaretips.com
malwaretips.com
AV-Comparatives settings in these tests are similar to ConfigureDefender HIGH settings but with disabled ASR rules (HIGH settings are stronger, especially in Enterprises). I made the cumulative results for several tests, here:

AV-Comparatives - Business Security Test 2021 (March – June)
Introduction his is the first half-year report of our Business Main-Test Series of 2021, containing the results of the Business Real-World Protection Test (March-June), Business Malware Protection Test (March), Business Performance Test (June), as well as the Product Reviews. Please note that...
 malwaretips.com
malwaretips.com
Edit1
Changed the link to the recent scorings of AV-Comparatives Business Security tests.
Edit2
Simple conclusion. In AV-Comparatives tests, the protection of Defender on HIGH settings is comparable to KIS on default settings. I think, that a similar comparison is probably true in the daily life of Home users.
Last edited:
ConfigureDefender 3.0.1.0 beta 2
Download location ( x64 and x86):
Updated help:
The file is accepted by SmartScreen and has been whitelisted by Microsoft Defender and Avast. The submission to Norton and Bitdefender is not finished, yet.
The changelog (version 3.0.1.0 beta 2):


Download location ( x64 and x86):
Updated help:
The file is accepted by SmartScreen and has been whitelisted by Microsoft Defender and Avast. The submission to Norton and Bitdefender is not finished, yet.
The changelog (version 3.0.1.0 beta 2):
- Added some useful information to the Help and manual.
- Added "Send All" setting to Automatic Sample Submission.
- Updated ASR rules (1 new rule added).
- Added the Warn mode to ASR rules.
- Added INTERACTIVE Protection Level which uses ASR rules set to Warn.
- Added the <Info> button next to the Protection Levels buttons. It displays information about which settings are enabled in DEFAULT, HIGH, INTERACTIVE, and MAX Protection Levels.
- Redesigned slightly the layout of the Exploit Guard section.
- Added support for Windows 11.
- Added support for Id=1120 to Defender Security Log. If this event is logged by Windows Event Log, then it will be also included in ConfigureDefender.
- Added CFA setting BDMO = Block Disk Modifications Only - folders will not be protected, but some important disk sectors will be still protected (Id = 1127).
Last edited:
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0