You are lucky! Windows Defender just corrupts the signature database on my computer and I have to disable it.... I'm still waiting for Microsoft to release a utility to reset Windows Defender.In case you're wondering if I'm using outdated WD, I'm not! I'm indeed running v1809's WD version
View attachment 201612
Advanced Plus Security DeepWeb's Security Config
- Thread starter DeepWeb
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Last updated
- Dec 17, 2018
- Windows Edition
- Enterprise
- Security updates
- Allow security updates and latest features
- User Access Control
- Always notify
- Real-time security
- Kaspersky Total Security (GDPR)
- Firewall security
- Periodic malware scanners
- Norton Power Eraser
Run PE Detector
VT Hash Checker
Root Certificate Check
- Malware sample testing
- I do not participate in malware testing
- Browser(s) and extensions
- Browsers:
Chrome
Firefox Nightly
Edge
Extensions:
Nano Adblocker & Defender
HTTPS Everywhere
Privacy Possum
Searchonymous
Temporary Container (FF)
- Maintenance tools
- None - They break more than they fix
- File and Photo backup
- Windows Backup using File History
- System recovery
- Macrium Reflect
-Emsisoft Anti-Malware
+Kaspersky Total Security
+Kaspersky Total Security
Last edited:
Having issues uninstalling Emsisoft Anti-Malware. It corrupts the entire boot process. Either that or installing Kaspersky. One of them is causing a major major headache.
E
Eddie Morra
[Redacted, must have misunderstood one of the posts, no way it meant what I thought it did lol]
I can now confirm it's Kaspersky Total Security. I'm not using both simultaneously. I uninstalled one, reboot tgen installed the other. But Kaspersky boots to Inaccessible Boot Device. It is specifically Kaspersky. I've already ruled out all other software. Something about it is not working for my setup. Reading through forums to see what might be the cause.[Redacted, must have misunderstood one of the posts, no way it meant what I thought it did lol]
I think my Group Policy is too strict with some of the drivers Kaspersky is loading during boot time. I am disabling the strict policy to only use Good Drivers at boot. For now Early Launch Anti-Malware is set to "Not configured". Before it was set to only "good drivers".
But this is a very confusing bug! Kaspersky Security Cloud works flawlessly. Kaspersky Anti-Virus has no issues either. But Kaspersky Total Security breaks? Hmm... I couldn't find any documentation on the Internet so if I find a fix for this I will post it here.
Last edited:
Kaspersky has always been good for protection. The free version looks splendid, excluding their web filter, prefer Forticlients.
~LDogg
~LDogg
Update: OK I FOUND THE ISSUE!!!! It was indeed my Group Policy. No reinstall of Windows necessary.
When you install Kaspersky Total Security make sure you leave
Computer Configuration > Administrative Templates > System > Early Launch Anti-Malware > Boot-Start Driver Initialization Policy > Not configured!!!
Windows does not recognize some of the drivers Kaspersky is using and it will block them from running at boot up and cancel the entire boot process. Also after installing Kaspersky, I highly highly recommend going to Powershell/Command Prompt as admin and run the command immediately after installing the AV:
"dism /online /cleanup-image /restorehealth"
That way even if installing Kaspersky or any other antivirus breaks your bootup process, Windows will repair it before you boot into a blue screen.
When you install Kaspersky Total Security make sure you leave
Computer Configuration > Administrative Templates > System > Early Launch Anti-Malware > Boot-Start Driver Initialization Policy > Not configured!!!
Windows does not recognize some of the drivers Kaspersky is using and it will block them from running at boot up and cancel the entire boot process. Also after installing Kaspersky, I highly highly recommend going to Powershell/Command Prompt as admin and run the command immediately after installing the AV:
"dism /online /cleanup-image /restorehealth"
That way even if installing Kaspersky or any other antivirus breaks your bootup process, Windows will repair it before you boot into a blue screen.
Last edited:
+Enabled hardware virtualization
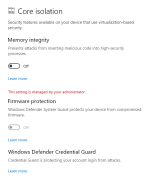
@Vasudev I ultimately enabled virtualization in BIOS again. But I disabled HVCI/Memory Integrity because it used too much CPU like you said and it breaks Kaspersky and every other AV and many kernel drivers like the Vmware Microcode Update Driver.
I noticed some sweet changes in the latest version of Windows 10 1809. You no longer have to enable Hyper-V Hypervisor for virtualization based security. If you enable virtualization in BIOS, Windows will automatically use some hidden hypervisor I guess. The result is
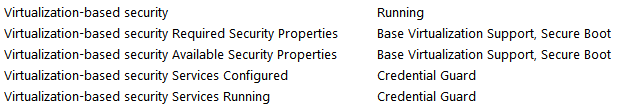
+Base Virtualization
+Secure Boot (whatever that means...)
+Credential Guard
-Kaspersky virtualized browsing
Apparently if I turn on one I cannot use the other. But the benefits of Microsoft's virtualization outweigh this one small feature in Kaspersky. And as long as Memory Integrity is off there's no performance impact and no conflict with programs and drivers. I am still trying to figure out what Firmware Protection is. I have tried every combination yesterday and nothing could enable it. If I ever get bored I will do a clean install and see if it enabled out of the box. I suspect it's something only newer hardware can utilize which raises the question, why display it for people with incompatible hardware and software. But they were smart enough to grey it out so that nobody breaks their computer.
But they were smart enough to grey it out so that nobody breaks their computer.
@Vasudev I ultimately enabled virtualization in BIOS again. But I disabled HVCI/Memory Integrity because it used too much CPU like you said and it breaks Kaspersky and every other AV and many kernel drivers like the Vmware Microcode Update Driver.
I noticed some sweet changes in the latest version of Windows 10 1809. You no longer have to enable Hyper-V Hypervisor for virtualization based security. If you enable virtualization in BIOS, Windows will automatically use some hidden hypervisor I guess. The result is
+Base Virtualization
+Secure Boot (whatever that means...)
+Credential Guard
-Kaspersky virtualized browsing
Apparently if I turn on one I cannot use the other. But the benefits of Microsoft's virtualization outweigh this one small feature in Kaspersky. And as long as Memory Integrity is off there's no performance impact and no conflict with programs and drivers. I am still trying to figure out what Firmware Protection is. I have tried every combination yesterday and nothing could enable it. If I ever get bored I will do a clean install and see if it enabled out of the box. I suspect it's something only newer hardware can utilize which raises the question, why display it for people with incompatible hardware and software.
Attachments
No I don't have it confused. I think there's a misunderstanding. There is most definitely a CPU overhead when HVCI is enabled in Windows and besides all AVs break when it is running. It kicks all of the kernel drivers out and that's problematic because it disabled self-protection for Kaspersky and other AVs. BIOS does not show HVCI. Only "Enable virtualization" but I had it disabled until now due to not having full granular control over which virtualization-based security features I can enable. Actually Group Policy is still broken and not properly enforcing the rules for virtualization based security which is frustrating. When will Microsoft learn.
Is it related to Hyper V to some extent?No I don't have it confused. I think there's a misunderstanding. There is most definitely a CPU overhead when HVCI is enabled in Windows and besides all AVs break when it is running. It kicks all of the kernel drivers out and that's problematic because it disabled self-protection for Kaspersky and other AVs. BIOS does not show HVCI. Only "Enable virtualization" but I had it disabled until now due to not having full granular control over which virtualization-based security features I can enable. Actually Group Policy is still broken and not properly enforcing the rules for virtualization based security which is frustrating. When will Microsoft learn.
Ret winaero to delete group policy and setup it once again.
Oh! You can use Kaspersky's Parental Control or Kaspersky Security Cloud's Data Leak tools to create a quasi Data Loss Prevention system. If you enable it, Kaspersky will monitor form fields and messages for the keywords that you provide.
Update: It works!
Attachments
Last edited:
You guys already know me. DeepWeb loves Group policy. I think the default configuration in Windows 10 could be dramatically better and improve security without anyone even noticing a difference on their computers. Many debug tools for example are exploited to extract passwords. 99% of Windows users will never even use those debug tools and you can easily turn them off. Anyway stopping my rant.
This nice security guidance by the GCHQ is easy enough to understand:
EUD Security Guidance: Windows 10 - 1803 - NCSC Site
Not every item is relevant but it's a good start. As a general rule, skip what you don't understand. That easy.
Another one: How to prevent Mimikatz (a tool to extract your Windows passwords)
Preventing Mimikatz Attacks – Blue Team – Medium
This nice security guidance by the GCHQ is easy enough to understand:
EUD Security Guidance: Windows 10 - 1803 - NCSC Site
Not every item is relevant but it's a good start. As a general rule, skip what you don't understand. That easy.
Another one: How to prevent Mimikatz (a tool to extract your Windows passwords)
Preventing Mimikatz Attacks – Blue Team – Medium
Last edited:
I'm growing increasingly tired of AOMEI Backupper. It keeps failing, the scheduled backups are no longer working and like sumtingwong I'm struggling with creating a bootable media. What has happened to this product? I'm going to reinstall. If reinstalling doesn't work I'll give Macrium Reflect a try tonight and see if it's more reliable.
-AOMEI Backupper
+Macrium Reflect
-AOMEI Backupper
+Macrium Reflect
Last edited:
Some BIOS options needs changing. For example BIOS rollback option which must be enabled for successfully BIOS recovery if bad BIOS bricks the mobo.You guys already know me. DeepWeb loves Group policy. I think the default configuration in Windows 10 could be dramatically better and improve security without anyone even noticing a difference on their computers. Many debug tools for example are exploited to extract passwords. 99% of Windows users will never even use those debug tools and you can easily turn them off. Anyway stopping my rant.
This nice security guidance by the GCHQ is easy enough to understand:
EUD Security Guidance: Windows 10 - 1803 - NCSC Site
Not every item is relevant but it's a good start. As a general rule, skip what you don't understand. That easy.
Another one: How to prevent Mimikatz (a tool to extract your Windows passwords)
Preventing Mimikatz Attacks – Blue Team – Medium
I personally think their guidelines are too strict so that people will feel secure and at the same the PCs the employees use are the ones with highest hidden malware since they think they're safe and install every known software in the world. I reckon we might see Trojan downloader or some ransomwares in their PCs.
Then again, thanks for linking that document.
Good Setup  I like Kaspersky
I like Kaspersky 
 Can I get the Wallpaper you use? It's awesome
Can I get the Wallpaper you use? It's awesome 
You may also like...
-
App Review Bitdefender Total Security 2026
- Started by Shadowra
- Replies: 60
-
Advanced Plus Security Divine_Barakah's PC Security Config 2026
- Started by Divine_Barakah
- Replies: 20
-
Advanced Plus Security Amnesia sec config 2025
- Started by Amnesia
- Replies: 11
-
Poll Paid vs Free Antivirus in 2026: What are you using, and is it worth paying for?
- Started by Bot
- Replies: 96
-
App Review Qihoo 360 Free Total Security 2025
- Started by Shadowra
- Replies: 28