I also hate waking up in the morning but it doesn't mean i will sleep forever. You have to do what you have to do.@Lockdown correct me if I am wrong but you dislike Windows for security and then on your profile you have "From AppGuard", so a software which works on Windows OS...
Default Deny VS traditional AVs
- Thread starter JM Safe
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
L
Local Host
Is not as hard as you state, specially if you have knowledge.It's a double-edged sword. Default-deny integrated into AVs usually works off a massive whitelist so it makes it a lot more user friendly than something like VS or SAP. The problem is, if a malicious application triggers a block, the majority of the population would instantly allow the offending application to run and then be outraged when they got infected.
Happens with "advanced" users too. Drop a piece of malware called "GoogleUpdate.exe" onto an advanced user's system and watch them either allow it to execute because they assume it's legitimate or have a small panic attack while debating with themselves whether it's legitimate or not.
A malicious GoogleUpdate wouldn't have the Google Certificate, I don't let it run nor access the Internet anyway.
I update my Software manually, and only programs that really need the Internet have access to it (Browsers, Game Clients, etc.).
D
Deleted Member 3a5v73x
"Advanced" users who use default-deny don't make assumptions, they make sure in the first place that file they are about to execute is legitimate or not with other tools and manual inspection.Happens with "advanced" users too. Drop a piece of malware called "GoogleUpdate.exe" onto an advanced user's system and watch them either allow it to execute because they assume it's legitimate or have a small panic attack while debating with themselves whether it's legitimate or not.
Last edited by a moderator:
That's saferI update my Software manually, and only programs that really need the Internet have access to it (Browsers, Game Clients, etc.).
5
509322
@Lockdown correct me if I am wrong but you dislike Windows for security and then on your profile you have "From AppGuard", so a software which works on Windows OS...
So what ?
What does my dislike of Microsoft and Windows have to do with my job ?
And my dislikes are in-line and shared by many in the industry.
I short Microsoft because it is no one's friend.
Last edited by a moderator:
I agree hence the 'Not JUST for advanced users'It's a double-edged sword. Default-deny integrated into AVs usually works off a massive whitelist so it makes it a lot more user friendly than something like VS or SAP. The problem is, if a malicious application triggers a block, the majority of the population would instantly allow the offending application to run and then be outraged when they got infected.
Happens with "advanced" users too. Drop a piece of malware called "GoogleUpdate.exe" onto an advanced user's system and watch them either allow it to execute because they assume it's legitimate or have a small panic attack while debating with themselves whether it's legitimate or not.
You'd be surprised. I see it a lot with CF too; people complaining about how they don't know whether a file is safe or not when it's been put inside the sandbox. Happens less with default-deny but it's there if you look."Advanced" users who use default-deny don't make assumptions, they make sure in the first place that file they are about to execute is legitimate or not with other tools.
RoboMan
Level 38
Verified
Honorary Member
Top Poster
Content Creator
Well-known
High Reputation
Forum Veteran
This is turning into a war rather than an argument-based discussion... Remember guys, that Linux, Windows, antivirus or default deny, we all pursue the same goal of security and, on different levels, we all either achieve it or keep learning on our way to the top. Some may find, at this moment, AV more suitable for them, others may find default-deny solutions more suitable, and lastly some may find a combination of both as their best solution. There are no black or white, good or wrong here, it's more a matter of tastes. I switched to default deny not so long ago and I haven't had any trouble or infection with it. I used AV for years and I hadn't had any infection as well. Everything starts on our habits and our workspace, and what we do or aim to do. It's like, I don't know, secured hardware firewalls. There are great thousand of dollars routers that provide great security. Although, me as a home user would never spent so much money on them, because I don't need them nor will they actually make me "safer" on my condition as a home regular user. The best option varies on the kidn of user. 
Pers
I'm glad you said it lol. Many threads seems to cause a clash of ego lolThis is turning into a war rather than an argument-based discussion... Remember guys, that Linux, Windows, antivirus or default deny, we all pursue the same goal of security and, on different levels, we all either achieve it or keep learning on our way to the top. Some may find, at this moment, AV more suitable for them, others may find default-deny solutions more suitable, and lastly some may find a combination of both as their best solution. There are no black or white, good or wrong here, it's more a matter of tastes. I switched to default deny not so long ago and I haven't had any trouble or infection with it. I used AV for years and I hadn't had any infection as well. Everything starts on our habits and our workspace, and what we do or aim to do. It's like, I don't know, secured hardware firewalls. There are great thousand of dollars routers that provide great security. Although, me as a home user would never spent so much money on them, because I don't need them nor will they actually make me "safer" on my condition as a home regular user. The best option varies on the kidn of user.
D
Deleted Member 3a5v73x
I won't even bother asking why someone should continue to use CF if they can't differentiate if a sandboxed file is legitimate or not. CF as default-deny with auto-containment enabled is popular here, still, I don't see a purpose of using it for an "Advanced" user system.You'd be surprised. I see it a lot with CF too; people complaining about how they don't know whether a file is safe or not when it's been put inside the sandbox. Happens less with default-deny but it's there if you look.
CF is one of the best if not the best free software but sadly is also the most buggy software out there with the worse support and atmosphere.I won't even bother asking why someone should continue to use CF if they can't differentiate if a sandboxed file is legitimate or not. CF as default-deny with auto-containment enabled is popular here, still, I don't see a purpose of using it for an "Advanced" user system.
Yes, more a software is sophisticated and then more is the possibility to have it buggy.CF is one of the best if not the best free software but sadly is also the most buggy software out there with the worse support and atmosphere.
L
Local Host
Let is die as it's a waste of time to argue about it unless both persons are open minded, plus it's off topic.This is turning into a war rather than an argument-based discussion... Remember guys, that Linux, Windows, antivirus or default deny, we all pursue the same goal of security and, on different levels, we all either achieve it or keep learning on our way to the top. Some may find, at this moment, AV more suitable for them, others may find default-deny solutions more suitable, and lastly some may find a combination of both as their best solution. There are no black or white, good or wrong here, it's more a matter of tastes. I switched to default deny not so long ago and I haven't had any trouble or infection with it. I used AV for years and I hadn't had any infection as well. Everything starts on our habits and our workspace, and what we do or aim to do. It's like, I don't know, secured hardware firewalls. There are great thousand of dollars routers that provide great security. Although, me as a home user would never spent so much money on them, because I don't need them nor will they actually make me "safer" on my condition as a home regular user. The best option varies on the kidn of user.
I sure ain't going to waste my time explaining and talking to a person who would never be open minded, they stuck with their way of thinking.
That is right, but at the same time is not the reason why CF is so buggy, there's software way more sophisticated that has no problems, it goes down to the programmers being lazy or lacking knowledge.Yes, more a software is sophisticated and then more is the possibility to have it buggy.
Also by ignorance from the Publishers (Comodo).
+1Let is die as it's a waste of time to argue about it unless both persons are open minded, plus it's off topic.
I sure ain't going to waste my time explaining and talking to a person who would never be open minded, they stuck with their way of thinking.
You'd be surprised. I see it a lot with CF too; people complaining about how they don't know whether a file is safe or not when it's been put inside the sandbox. Happens less with default-deny but it's there if you look.
+1. I had issues with the blocked files, some of them Windows processes, not the sanboxed files. Happened often enough that I said "Bye bye Comodo!" Not exactly home user-friendly.
Last edited:
5
509322
People should use what they like. They should use what works best for them on their specific system(s).
The drama that happens on the forums is largely a result of communications via posts that can be interpreted many different ways. In virtually 99 % of the cases, the intent and intended meaning of the post is lost or misinterpreted by the reader. People twist things within the context of a thread for a whole range of reasons.
When I post something, its intent and meaning is what I say it is... not how others interpret it. That's how written communications have worked since ape man started painting pictures on cave walls.
The drama that happens on the forums is largely a result of communications via posts that can be interpreted many different ways. In virtually 99 % of the cases, the intent and intended meaning of the post is lost or misinterpreted by the reader. People twist things within the context of a thread for a whole range of reasons.
When I post something, its intent and meaning is what I say it is... not how others interpret it. That's how written communications have worked since ape man started painting pictures on cave walls.
No issues with updates  with my double deny (AppLocker & ACL) with different users for different uses (programs) approach
with my double deny (AppLocker & ACL) with different users for different uses (programs) approach 
Don't think Microsoft intended it to use it that way Every folder in Program Files has a deny with exception for its own signature. It is not as tight as hash based whitelist, but a lot easier to maintain (zero maintenance problems, everything updates fine).
Every folder in Program Files has a deny with exception for its own signature. It is not as tight as hash based whitelist, but a lot easier to maintain (zero maintenance problems, everything updates fine).
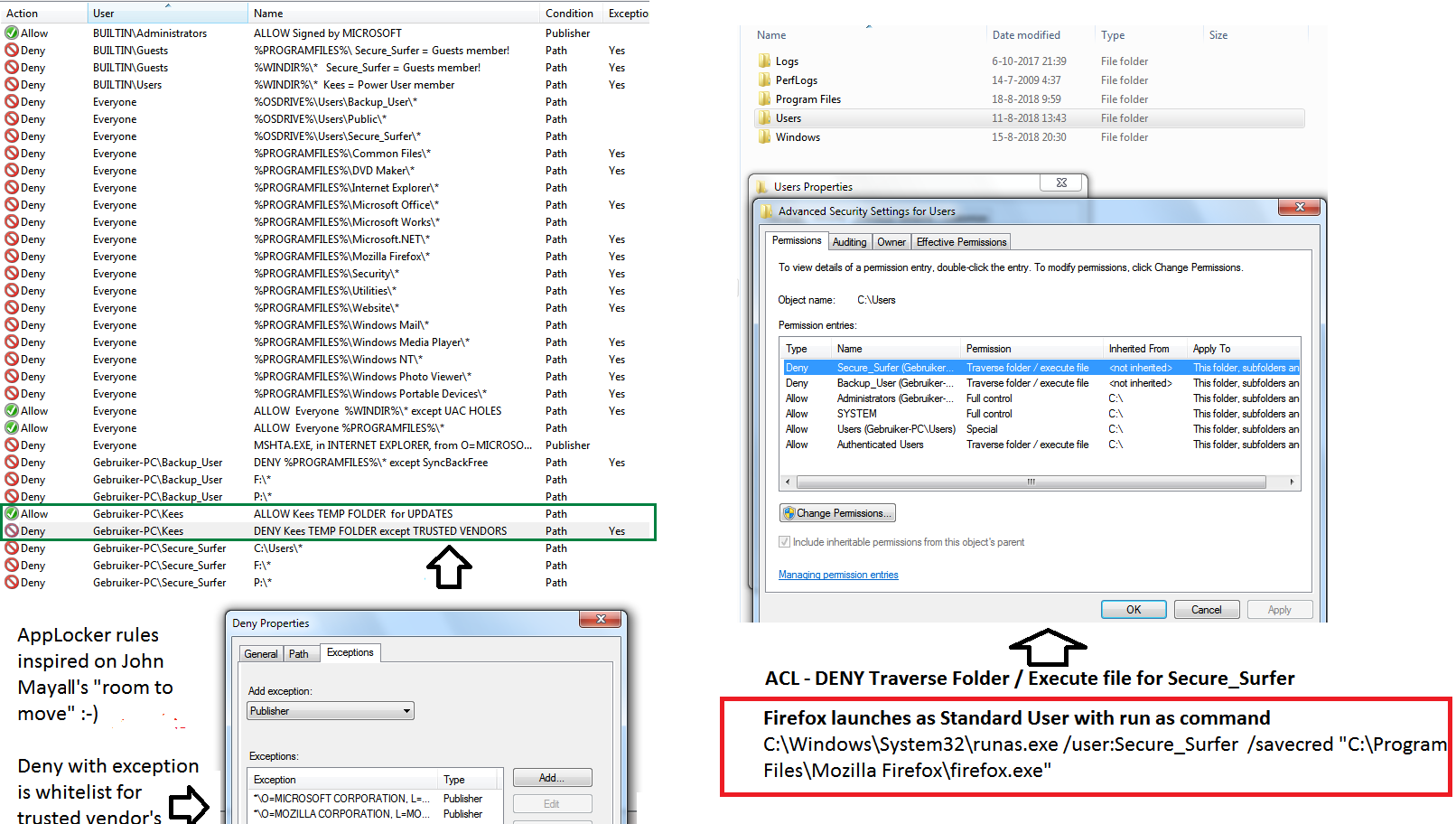
Don't think Microsoft intended it to use it that way
Last edited:
How should we define the following; Ae they "Default-Deny"?
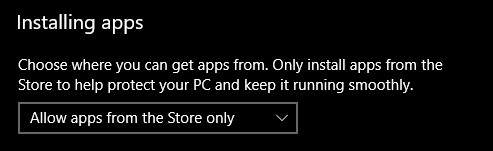
- Browser blocks a malicious download
- Extension prevents access to a phishing website
- Unable to install program due to account permissions (or see image).
Most readers will not understand the idea. But this is simple. The picture on the right is related to making the light 'on demand sandbox' for the Firefox web browser and the shortcut to run it. This sandbox is simply another account for the user named Secure_Surfer (standard user type of account). When Firefox is running in that sandbox and has been exploited, then the payload is usually dropped somewhere in the %UserProfile% and cannot be executed due to ACL permissions for Secure_Surfer's account.No issues with updateswith my double deny (AppLocker & ACL) with different users for different uses (programs) approach
Don't think Microsoft intended it to use it that wayEvery folder in Program Files has a deny with exception for its own signature. It is not as tight as hash based whitelist, but a lot easier to maintain (zero maintenance problems, everything updates fine).
View attachment 196357
The next logical step would be adding some other restrictions for Secure_Surfer's account (via ACL or local policies) , like blocking: CMD shell, script interpreters (powershell.exe, powershell_ise.exe, wscript.exe, cscript.exe, mshta.exe, hh.exe) and some other vulnerable tools.
Similar 'on demand sandboxes' can be made for securing other vulnerable applications like MS Office, PDF viewers, etc. In fact, the similar idea was adopted in ReHIPS.
Last edited:
D
Deleted member 178
Exact, which make sandboxing very tight and stable without requiring much maintenance or updates, opposed to other sandboxing mechanisms.Similar 'on demand sandboxes' can be made for securing other vulnerable applications like MS Office, PDF viewers, etc. In fact, the similar idea was adopted in ReHIPS.
You may also like...
-
Serious Discussion AI-Powered Antivirus: The Future of Cybersecurity or Just Hype?
- Started by Bot
- Replies: 10
-
Question What does Kaspersky's default deny/zero trust mode do and how to set it properly?
- Started by nonamebob567
- Replies: 1
-
Poll Paid vs Free Antivirus in 2026: What are you using, and is it worth paying for?
- Started by Bot
- Replies: 96
-
Poll The Trifecta Threat. Comodo vs. ESET vs. McAfee - Which Security Suite Wears the Crown?
- Started by Divergent
- Replies: 31


