Rising automatically cleared the detection without reporting.
Or maybe someone reported to them.
Or maybe someone reported to them.
This happens when the backend fails silently.
Uploading to MS proactively was a great thing to do, no warning when downloading through Edge and no detection by MS Defender anymoreNew version has been pushed and it has been uploaded to MS proactively.
In this new version there are minimal changes to the application, the changes are mainly to the cloud backend.
Reputation-based detections have now been integrated.
Example: Helios:Malware!Rep1, Rep2 and Rep3.
These deterministic detections have been implemented to reduce false positives and allow certain heuristics to be less aggressive.
Due to the updated cloud backend, older versions of the application will fall back to local heuristics but won't be able to use the AI or reputation lookup.
This is probably a detection of the malicious LOLBin control feature.Uploading to MS proactively was a great thing to do, no warning when downloading through Edge and no detection by MS Defender anymore
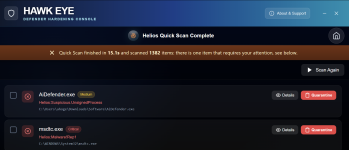
The Helios Quick Scan has a false positive, msdtc.exe:
View attachment 294599
Could you please retry the scan?Uploading to MS proactively was a great thing to do, no warning when downloading through Edge and no detection by MS Defender anymore
The Helios Quick Scan has a false positive, msdtc.exe:
View attachment 294599
Didn't work. It's still stuck.Please install the VS C++ redistributable from this website and try again.
https://aka.ms/vc14/vc_redist.x64.exe
Is it the same if you execute as admin? It seems some people have this issue, I am unable to reproduce on my side.Didn't work. It's still stuck.
New executable is now blocked by Smart App ControlNew version has been pushed and it has been uploaded to Microsoft. It may take a bit of time for them to process.
Huorong and Rising promised to clear the detection and it looks like they have created a stable exclusion.
McAfee responded that they will clear the detection and it's been done. Microsoft exclusion is unstable and linked to the version info. When I change the version info strings, the detection reappears. I've not yet received response from ClamAV/Cisco.
-Refined user interface, fixed an issue where it appeared cropped on lower resolution screens
-Added EULA
-Added scan profiles
-Removed the initial loading state. Now even on machines where the Defender State can't be pulled, the application loads and allows scan to be ran.
-Exclusion analysis now local
No idea, on the submission portal, the progress of the detection moved like this:New executable is now blocked by Smart App Control
MSHTA appears as an infected file not a victimThis is one of the cases where Helios will help.
Example: malicious HTA file is not detected by Defender.
Hash: 24ef77b150ff7ebc30d8cb7234fd2cec8a15a58128e8e2441e259b7d3de1e66c
Defender alone would not handle this malware.
Protections: MSHTA is blocked from accessing the web anyway, through Deep Firewall Control.
The script sets persistence.
Response:
View attachment 294617
Remediation terminates the process, deletes the persistence and the initial script (I will update the UI so it doesn't display "Quarantine" but "Process" and displays information what will happen on remediation.
Helios combines expertise in fileless and evasive malware detection with reputation from different providers on executables.
Yes, there is room for UI improvement.MSHTA appears as an infected file not a victim