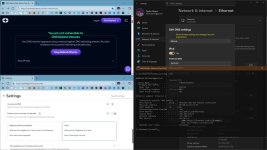
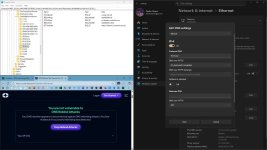
Go to the test site again, disable ad blocker and any other content blocker you have installed. Then open the DevTools, switch to
Networking tab. Now run the test once with DNS resolvers that fail the test, screenshot and repeat the test with NextDNS. At the end, post the screenshots here. This will give us at least some ide what is happening and why.
Also, visit
dnscheck.tools with ControlD, take a screenshot, then visit it with NextDNS and take the screenshot again. Just make sure to hide your IP address.
That is... if you want to test it. Because as of now, you didn't show any desire to find the answer to what is happening.