- Apr 5, 2014
- 6,008
Doctor Web specialists have examined 1C.Drop.1, a Trojan that spreads itself (software used by more than 1,000,000 companies) via email. It infects computers on which 1C accounting applications are installed and runs a dangerous ransomware program. It is one of those rare cases when attackers create a malicious applications using new techniques or uncommon programming languages.
It is no doubt that 1C.Drop.1 is the first Trojan analyzed by our specialists that is written in Russian—to be more precise, in an incorporated 1C language that uses Cyrillic characters for command writing. It is noteworthy that malicious files for 1C products that could modify or infect other external data processors have already been known to Doctor Web security researchers since 2005. However, this time, they detected a fully-featured dropper Trojan containing a ransomware program.
The Trojan is distributed as an attachment to the following email message titled “Our BIC code has been changed”:
Greetings!
Our BIC code has been changed.
Please update your bank classifier.
The classifier can be updated automatically in 1C Enterprise 8.
File – Open classifier update processor from the attachment.
Click YES to update the classifier automatically.
Within 1-2 minutes if there is Internet connection.
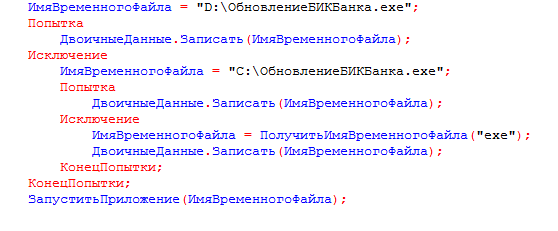
The email message contains an external data processor for “1C: Enterprise” namedПроверкаАктуальностиКлассификатораБанков.epf. The body of this module is password-protected—thus, standard methods cannot be used to view its source code. If the user runs this file in the 1C:Enterprise mode, the following window is displayed:
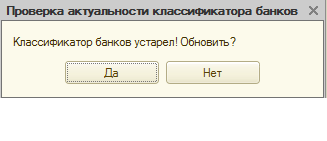
Clicking on any button of this window will launch 1C.Drop.1. In addition, in the 1C:Enterprise program, the user will see the following picture:

Meanwhile, the Trojan starts its malicious activity on the computer. First, it searches the 1C database for contractors with known email addresses and then sends the above-mentioned text message with its own copy attached. The Trojan uses the email address specified in the victim’s 1C user account as the sender’s address. If the user has not specified their email, the Trojan substitutes it with 1cport@mail.ru and attaches the ОбновитьБИКБанка.epf external data processor that contains the Trojan’s copy. If the file is run in the 1C software, the ransomware Trojan will affect the computer as well; yet, this copy of1C.Drop.1 will send contractors a corrupted EPF file that cannot be opened with “1C:Enterprise”. 1C.Drop.1 supports the following 1C databases:
It is no doubt that 1C.Drop.1 is the first Trojan analyzed by our specialists that is written in Russian—to be more precise, in an incorporated 1C language that uses Cyrillic characters for command writing. It is noteworthy that malicious files for 1C products that could modify or infect other external data processors have already been known to Doctor Web security researchers since 2005. However, this time, they detected a fully-featured dropper Trojan containing a ransomware program.

The Trojan is distributed as an attachment to the following email message titled “Our BIC code has been changed”:
Greetings!
Our BIC code has been changed.
Please update your bank classifier.
The classifier can be updated automatically in 1C Enterprise 8.
File – Open classifier update processor from the attachment.
Click YES to update the classifier automatically.
Within 1-2 minutes if there is Internet connection.
The email message contains an external data processor for “1C: Enterprise” namedПроверкаАктуальностиКлассификатораБанков.epf. The body of this module is password-protected—thus, standard methods cannot be used to view its source code. If the user runs this file in the 1C:Enterprise mode, the following window is displayed:

Clicking on any button of this window will launch 1C.Drop.1. In addition, in the 1C:Enterprise program, the user will see the following picture:

Meanwhile, the Trojan starts its malicious activity on the computer. First, it searches the 1C database for contractors with known email addresses and then sends the above-mentioned text message with its own copy attached. The Trojan uses the email address specified in the victim’s 1C user account as the sender’s address. If the user has not specified their email, the Trojan substitutes it with 1cport@mail.ru and attaches the ОбновитьБИКБанка.epf external data processor that contains the Trojan’s copy. If the file is run in the 1C software, the ransomware Trojan will affect the computer as well; yet, this copy of1C.Drop.1 will send contractors a corrupted EPF file that cannot be opened with “1C:Enterprise”. 1C.Drop.1 supports the following 1C databases:
- Trade Management 11.1
- Trade Management (basic) 11.1
- Trade Management 11.2
- Trade Management (basic) 11.2
- Accounting 3.0
- Accounting (basic) 3.0
- 1C:Comprehensive Automation 2.0
