Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,118
"One of the most active ransomware groups, Egregor is part of the Sekhmet malware family that has been active since mid-September 2020. Like most other Ransomware groups, it targets organizations across the world. The ransomware operates by hacking into organizations, stealing sensitive user documents, encrypting data, and finally demanding ransom in exchange of decrypted documents."
....
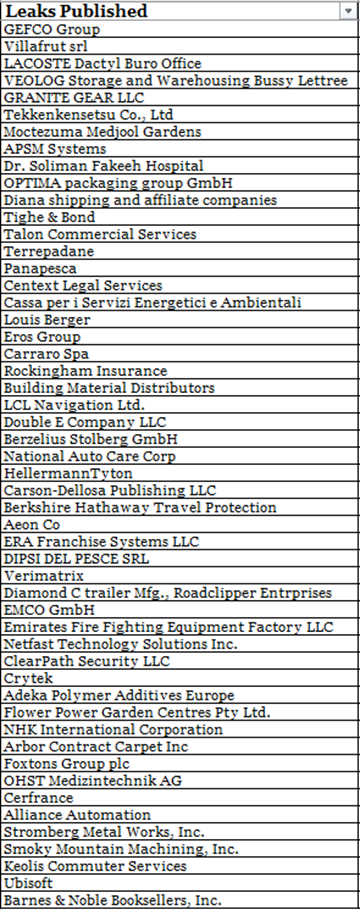
"Allegedly, 52 companies have been breached by the threat actor till today (as of October 30, 2020), from GEFCO group being among the first ones to the more recently affected organizations such as Crytek, Ubisoft, Foxtons Group, and Barnes & Noble."
....
...
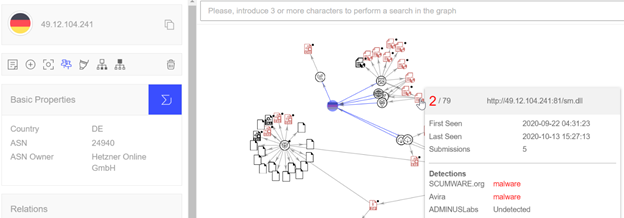
"The Egregor Ransomware family shares functionalities of other ransomware actors like Clop Ransomware. As per the intelligence analysis, the threat actor has a possible link to TinyMet Payload v0.2 which was used by Clop Ransomware as a precursor for the TA505 Post-Exploitation Operation. The malware hosting server has been traced back and identified to the server with IP 49.12.104[.]241 and located in Germany, as shown in the figure below.
The ransomware possesses multiple anti-analysis techniques such as code obfuscation and packed payloads."
...
"Unfortunately, there are no third-party tools that can decrypt files encrypted by this threat actor considering that the user needs a private key from the hacker server to decrypt the files. The cyber criminals behind this ransomware are the only ones with the decryption software and key."
Look at the below article for more details:
....
"Allegedly, 52 companies have been breached by the threat actor till today (as of October 30, 2020), from GEFCO group being among the first ones to the more recently affected organizations such as Crytek, Ubisoft, Foxtons Group, and Barnes & Noble."
....
...
"The Egregor Ransomware family shares functionalities of other ransomware actors like Clop Ransomware. As per the intelligence analysis, the threat actor has a possible link to TinyMet Payload v0.2 which was used by Clop Ransomware as a precursor for the TA505 Post-Exploitation Operation. The malware hosting server has been traced back and identified to the server with IP 49.12.104[.]241 and located in Germany, as shown in the figure below.
The ransomware possesses multiple anti-analysis techniques such as code obfuscation and packed payloads."
...
"Unfortunately, there are no third-party tools that can decrypt files encrypted by this threat actor considering that the user needs a private key from the hacker server to decrypt the files. The cyber criminals behind this ransomware are the only ones with the decryption software and key."
Look at the below article for more details:
