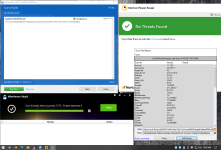
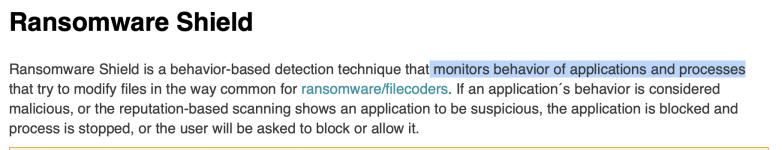
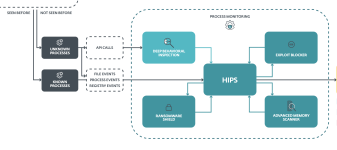
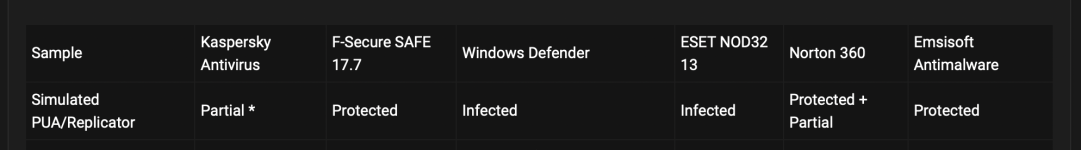
SM25.vbs triggers wscript.exe and mshta.exe. Last named tries calling out, triggers Huorong Network Access Control (=Firewall) appears, default action is to auto-block after 45 seconds, so I chose "Deny". wscript.exe tries setting an AutoRun, flashing red Huorong HIPS alert (File protection) appears, whose default action is to auto-block after 45 seconds, so I chose "Deny". Next is a Huorong HIPS alert (Sensitive action) on Hidden PowerShell script executions. Default action is to auto-block after 45 seconds, so I chose "Deny". All services but mshta.exe autoterminate, broken mshta.exe window closed personally. No further malicious traces, no AutoRuns. Untouched source file deleted before firing off 2nd_opinion scans. HIT.