- Apr 28, 2015
- 9,098
It seems scripts detections did not improve even hardening the settings...
Yeah ESET's advanced techniques (more static heuristics, possibly sandbox emulation on-device) do tend to be heavy. Both involve more analysis before the program is even allowed to run, which I think most users perceive as a slowdown. A behavior blocker traps and evaluates API calls which happen less often and most apps when they are doing CPU-intensive things are not calling out to Windows APIs constantly.I have felt a slight impact especially when launching a program with these more aggressive settings
That's too bad. Once again, "SM25.vbs" seems to have identically duplicated itself and then put that script into AutoRuns.... I can't imagine a behavior blocker would miss that. From the Huorong test:It seems scripts detections did not improve even hardening the settings...
SM25.vbs triggers wscript.exe and mshta.exe. Last named tries calling out, triggers Huorong Network Access Control (=Firewall) appears, default action is to auto-block after 45 seconds, so I chose "Deny". wscript.exe tries setting an AutoRun, flashing red Huorong HIPS alert (File protection) appears, whose default action is to auto-block after 45 seconds, so I chose "Deny". Next is a Huorong HIPS alert (Sensitive action) on Hidden PowerShell script executions. Default action is to auto-block after 45 seconds, so I chose "Deny". All services but mshta.exe autoterminate, broken mshta.exe window closed personally. No further malicious traces, no AutoRuns. Untouched source file deleted before firing off 2nd_opinion scans. HIT.
Nice!I already turned on that DNA hehe... see the pics in my previous post...
You are a champ. Thanks for satisfying our curiosity.A small test (to make ESET fans happy) performed today with a high detected sample but not detected by ESET at VT "apparently":
View attachment 256723
View attachment 256722
View attachment 256719
View attachment 256720
View attachment 256721
Thanks @upnorth for the sample...
I know, that's why I said "apparently"... this time was "right" since it was not detected on demand but was on dynamicThe fact a sample is not detected by an engine on VT does not mean it doesn't actually detect it. That is a well-known fact many people keep forgetting.
Why didn't you add my suggestions for rules to hips in addition to the settings recommended by the antivirus developers?Привет, ребята, до конца месяца я только что реализовал эту программу.:
[KB6119] Настройка правил HIPS для продуктов ESET business для защиты от вымогателей
[KB6132] Настройка правил брандмауэра для ESET Endpoint Security для защиты от программ-вымогателей
Также сохраняя прежние агрессивные ухищрения...
A very good question, it must take a really long time to download and it just isn't there yet...Where is ESET BB...?
A very good question, it must take a really long time to download and it just isn't there yet...

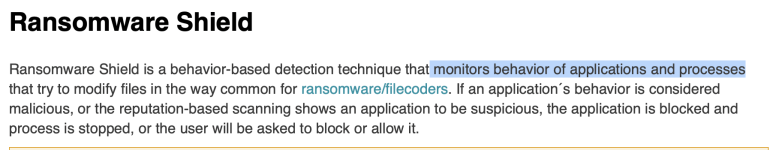
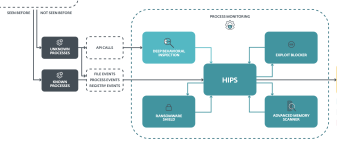
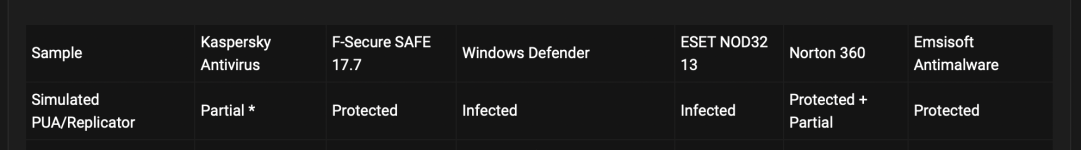
Yes I agree. For most users they might not be problematic but some software might be blocked. That's why I prefer to set them to Ask when creating them.Adding by default those HIPS rules can be problematic, because They can break also legit behavior ...
I still can't get my head around having to fiddle with HIPS settings in Eset.ESET could have many preset HIPS rules with a simple on/off switch. The rules could be even automatically turned on/off according to how paranoid you set it. As it is, the HIPS is basically useless for a basic user and demand some work for advanced users.