@hacheafleur
First of all thanks for the logs, i have taken a good look and so far everything seems reasonable clean.
I did found some spyware & adware traces (But nothing special) and a bunch of traces of old software and bad removal.
Other then that your pc is fine.
However i did see you are running:
ESET-IS, MBAM, Windows defender while ok. ESET and MBAM both like to scan every single thing my program does, which is ok.
But it also does dramatically increase the time my program needs to scan everything.
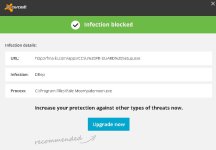
And as such some scans where blocked by ESET and my program kept trying. Just for the record our program does work fine next to AV programs and Internet Security solutions, but usually its a better thing to white-list it so that functions within my program get not scanned continuously, some functions run a command PER exe file or PER dll. Which means that a process which should take less then a 2 seconds might take much more as every time the process gets scanned.
That said the logs are far from complete and this is also the reason why it took so long. Some functions where blocked or denied.
I hope this helps, your logs are being deleted from our system.
If you require more information contact me anytime.
Kind Regards
Nico