- May 29, 2018
- 2,754
I test it at malcode database
Well atleast its working with opera, maybe just fails to block those threats youre visiting to
I test it at malcode database
You probably only need to enable ATP+ web filter + antivirus during installing
ATP = sandbox + dynamic threat protection, you can disable sandbox since youre using comodo firewall if you want to
Also anti-exploit becomes redundant, so you may disable it aswell since youre running OSA
Application firewall and single sign on are useful only if you use it in managed mode (connected to FortiGate)
yes my friend. For chrome is the best web filter. At Opera not working well. I have the same problem with K9 at Opera. Malwarebytes extension at opera works perfect. I stay with extensions at opera@AtlBo forticlient av is worth installing, if you want to have light performance + signature based av. Since youre using cf, you probably dont have hips on..so you will be lacking behaviour blocker against new threats?
Well if youre advanced user, you will know your needs but i would be using as you
-comodo firewall
- any av with behaviour blocker; avast, AVG,kaspersky( systemawatcher) , bitdefender, qihoo , maybe tweaked windows defender etc.
- fortinet web filter
- OSA
But if you replace forticlient av with any other antivirus opinion the web filter of forticlient will become bit redundant because most antiviruses can block malware sites well and netcraft will do enough for phishing,
@stefanos might be conflicting with your existing software?
@AtlBo forticlient av is worth installing, if you want to have light performance + signature based av. Since youre using cf, you probably dont have hips on..so you will be lacking behaviour blocker against new threats?
Great thanks. Very helpful.
Thanks for the images. Just what I was wanting to know.
Couple of questions:
1. If I don't use the Forticlient sandbox, anti-exploit, is the a-v worth installing just for signatures?
2. How is Fortinet with just anyone using Forticlient? Looks like it's meant to be complimentary to their other products, so this is why I ask.
Thanks for this help, and I may have a question about the configuration changes @ForgottenSeer 58943 recommended...
I have the HIPs on in Safe Mode. Even then, the system watcher element of things is a lacking, but I don't think I need more. OSArmor is so good at cutting malware off before BB becomes an issue, so maybe I will try this:
1. Comodo
-Firewall
-HIPs (Safe Mode)
-Sandbox
2. FortiClient
-A-V
*Sigs
-Web-Filter
3. NVT OSArmor
-All Options (plan to back off some, since don't want to see location blocks in the logs when I can see activity/behavior blocks instead)
4. AppCheck Anti R/W
-Had it for a while now
5. NVT ERP
-I use it like HIPs basically for the chance to whitelist command-line.
Sounds crowded, but it's my main "esperiment", so I don't mind. It's also the PC I use the most. All the apps are super light-weight, so it's not using RAM or processor as far as I can see.
This is really overkill
My suggestion:
- FortiClient (my modules) + Comodo FW (cruelsister's settings)
- FortiClient (my modules) + OSA (or ERP) + AppCheck + WFC (or W10FC or Simplewall)
1. No problemIt is, I agree. I only run all of this "for science and knowledge" sake. I gather alot of useful knowledge on the protection scopes of various security programs. I wouldn't recommend it for most individuals. Also, I don't install hoards of software.
OSA and ERP work very differently, although there is a of course overlap, many times. This is one reason I plan to trim back the settings in OSA over time. The problem with that is that the information that some executable is dropping and running something in AppData or whatever is something I would like to see for now. Well, when the Comodo HIPs are added I know this sounds crazy, but for now it's what I will use.
I have a few questions about FortiClient GUI and settings, but I like the application so far:
1. How do I change the settings mentioned by @ForgottenSeer 58943? EDIT I see your answer in the previous post thanks @imuade
2. Under the Malware Protection settings (top right)->A-V module->Block malicious websites all of the check boxes are green. Then, on Web Security main page the same, but in the Web Security settings they are green but can be changed. It says the green indicates allow the sites. The options are Allow, Block, Warn, Monitor. Does this indicate that they are allowed by default? OK, but unexpected, and I see the options there I have for changing if I need to so no problem. Wondering is there is a better way than all block. Also, what is monitor just out of curiosity?
3. Is grayware worth monitoring for?
OK, the vulnerability scan is very good. For laughs, has anyone run this on an unpatched system? I would love to find out how FortiClient would handle that situation. It could be a very interesting way to see how to get a limited number of patches that will do the job from a security perspective...or at least in Fortinet's opinion "do the job". In some cases, I could understand why someone might go for this kind of thing if it existed and if the concept was safe to trust.
The program seems very smooth and clean, and it's more what I have been looking for from an a-v than anything else I have seen to date...all things considered. Thanks for all the helpful information and tips.
Forti sandbox is not like Comodo or Sandboxie.its a malware analysis cloud sandbox.Forticlient sandbox
I was angry and nervous about these installations and uninstallations. But I found the solution. I am back to my lovely 360TSOK, the vulnerability scan is very good. For laughs, has anyone run this on an unpatched system? I would love to find out how FortiClient would handle that situation. It could be a very interesting way to see how to get a limited number of patches that will do the job from a security perspective...or at least in Fortinet's opinion "do the job". In some cases, I could understand why someone might go for this kind of thing if it existed and if the concept was safe to trust.
The program seems very smooth and clean, and it's more what I have been looking for from an a-v than anything else I have seen to date...all things considered. Thanks for all the helpful information and tips.
I was angry and nervous about these installations and uninstallations. But I found the solution. I am back to my lovely 360TS
It seems, that the scan shows the number of vulnerabilities rather than the number of missing updates. Still pretty informative (links, etc).OK, the vulnerability scan is very good. For laughs, has anyone run this on an unpatched system?
And is light. Extremely light. Comodo on my system slow down the applications and the boot time.And block many times safe thingsI can understand why. The BB in 360 brings good information to the user. For me, Comodo covers also with HIPs. HIPs covers the same areas and also some others. However, 360 logs are great and better than Comodo imo. Sandbox is still a hole in my life when it comes to MS Office sadl y for me. I still like this setup better for now.
360 is very good no boubt, especially the smoothness of the run-time execution of the program...
It seems, that the scan shows the number of vulnerabilities rather than the number of missing updates. Still pretty informative (links, etc).
You need bb with forticlient. I thing only with Comodo FW you are secure enough.Thankyou for doing this. You really inspired me with the post.
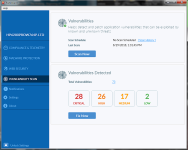
I ran this on a barely patched W7 installation and came up with this after running the vulnerability scanner in FortiClient:
View attachment 196870
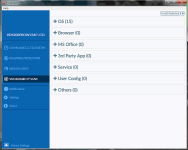
View attachment 196868
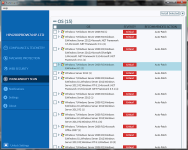
I noticed next to the updates in the list view, there was a number at the end of each listed OS vulnerability:
View attachment 196869
Maybe this is the number of updates to install. So, for "Critical" in this case, OS vulnerabilities, maybe the number of updates to install is the number of vulnerabilities. I will have to see. I have this almost fresh installation (a few updates/IE 11) imaged, so I am going to "Fix Now" to see the results. There are only OS vulnerabilities showing here.
This seems to be a VERY cutting type of application, and I like that very much from an a-v. Simple (REALLY simple) and very clinical protection from an endpoint specialist. A few good and straightforward modules that appear to function reliably and on a lighter than air base platform. On detection, real-time a-v scanning is finding keyfinders that everyone finds and that I should remove and will. All my PCs have stickers anyway.
Many very good elements to this approach by Fortinet. It must speak highly for their overall endpoint product. The web filter is the best web control set I have seen available for general use to date. Really like the filter is an understatement. I really like all of the modules and pulled together this way too.
How about this:
AppGuard
FortiClient
SysHardener
?
I'll rerun the scan after the "Fix Now" is over. It's running and downloading on the PC now. Should be interesting to see how it functions, but it looks mostly like another way to get Windows Updates so far.