- Jul 29, 2018
- 566
Thankyou for doing this. You really inspired me with the post.
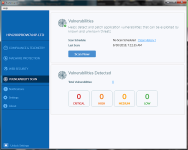
I ran this on a barely patched W7 installation and came up with this after running the vulnerability scanner in FortiClient:
View attachment 196870
View attachment 196868
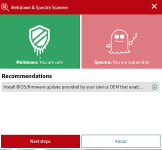
I noticed next to the updates in the list view, there was a number at the end of each listed OS vulnerability:
View attachment 196869
Maybe this is the number of updates to install. So, for "Critical" in this case, OS vulnerabilities, maybe the number of updates to install is the number of vulnerabilities. I will have to see. I have this almost fresh installation (a few updates/IE 11) imaged, so I am going to "Fix Now" to see the results. There are only OS vulnerabilities showing here.
This seems to be a VERY cutting type of application, and I like that very much from an a-v. Simple (REALLY simple) and very clinical protection from an endpoint specialist. A few good and straightforward modules that appear to function reliably and on a lighter than air base platform. On detection, real-time a-v scanning is finding keyfinders that everyone finds and that I should remove and will. All my PCs have stickers anyway.
Many very good elements to this approach by Fortinet. It must speak highly for their overall endpoint product. The web filter is the best web control set I have seen available for general use to date. Really like the filter is an understatement. I really like all of the modules and pulled together this way too.
How about this:
AppGuard
FortiClient
SysHardener
?
I'll rerun the scan after the "Fix Now" is over. It's running and downloading on the PC now. Should be interesting to see how it functions, but it looks mostly like another way to get Windows Updates so far.
AppGuard, if I'm not wrong, it's based on default-deny, so it should be as good as Comodo FW.You need bb with forticlient. I thing only with Comodo FW you are secure enough.
Other nice free alternatives could be OSArmor, ExeRadarPro or ReHIPS