I bought the unmanaged one. I don’t need their managment.If you don't know how to set up an endpoint, they will take care of it for you. The question is, whether its worth it coughing up the extra cash for white glove service.
Serious Discussion Harmony Endpoint by Check Point
- Thread starter Trident
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I bought the unmanaged one. I don’t need their managment.
How easy is it to set up the unmanaged one? Many endpoint software is complicated to set up, configure and manage. Can you just install the client and do the rest?
Oh it’s exceptionally easy, I will publish all related information soon.How easy is it to set up the unmanaged one? Many endpoint software is complicated to set up, configure and manage. Can you just install the client and do the rest?
The Threat Emulation blade is on par with VMRay. Really solid 
On par with CrowdStrike, Palo Alto and tools like Joe Sandbox. It’s amazing and extremely effective. Once you get your hands on it you will wonder how you’ve used products without such capabilities.The Threat Emulation blade is on par with VMRay. Really solid
so tempted to push that Harmony button... but think I'll wait a few more days, perhaps see how ZA/ESNG does in @Shadrowra's test.On par with CrowdStrike, Palo Alto and tools like Joe Sandbox. It’s amazing and extremely effective. Once you get your hands on it you will wonder how you’ve used products without such capabilities.
Switched one device more from ZA to Harmony Endpoint Advanced (HEA).
Policy configuration for maximum security (once you finish making all changes, click on "Install Policy"):
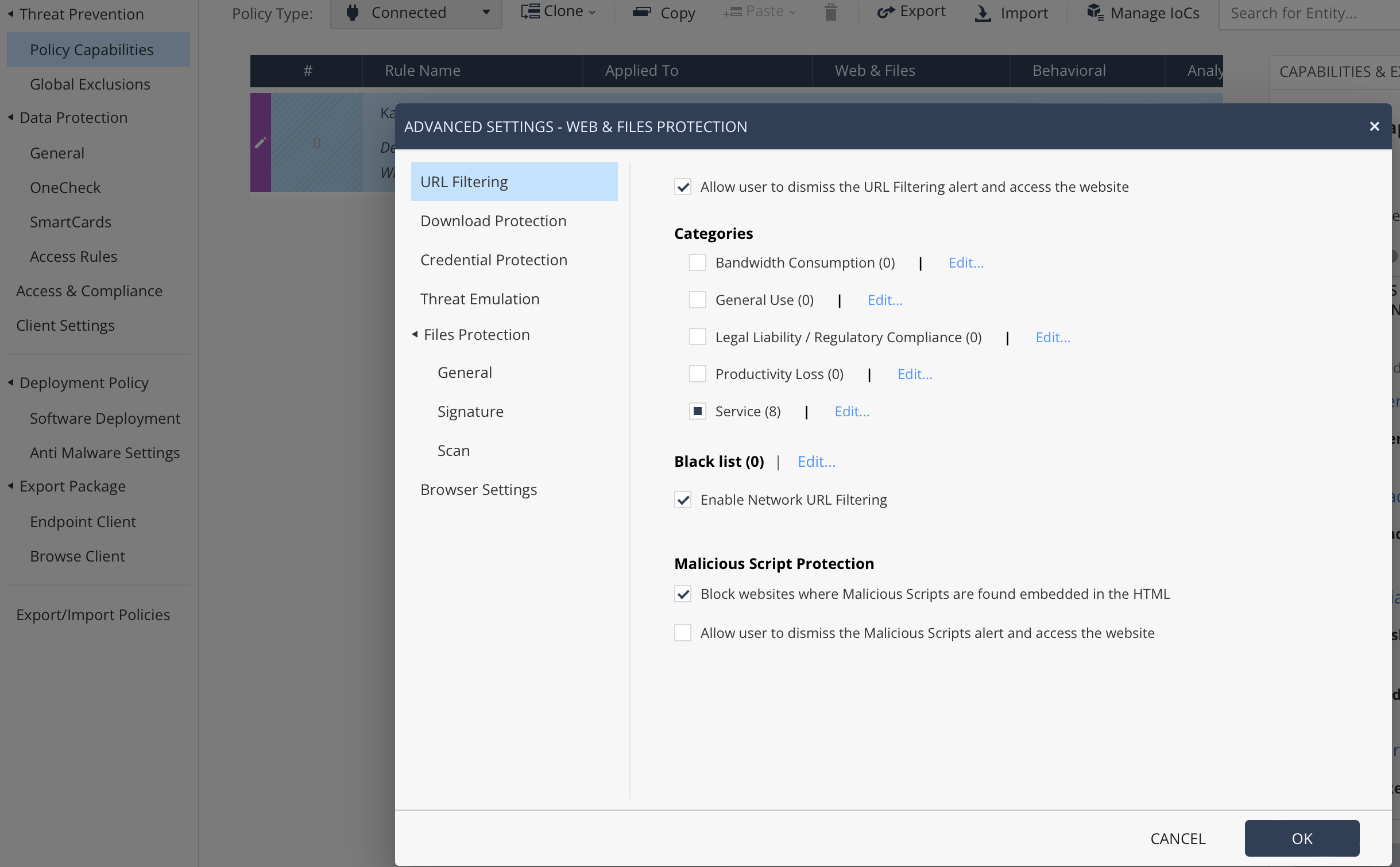
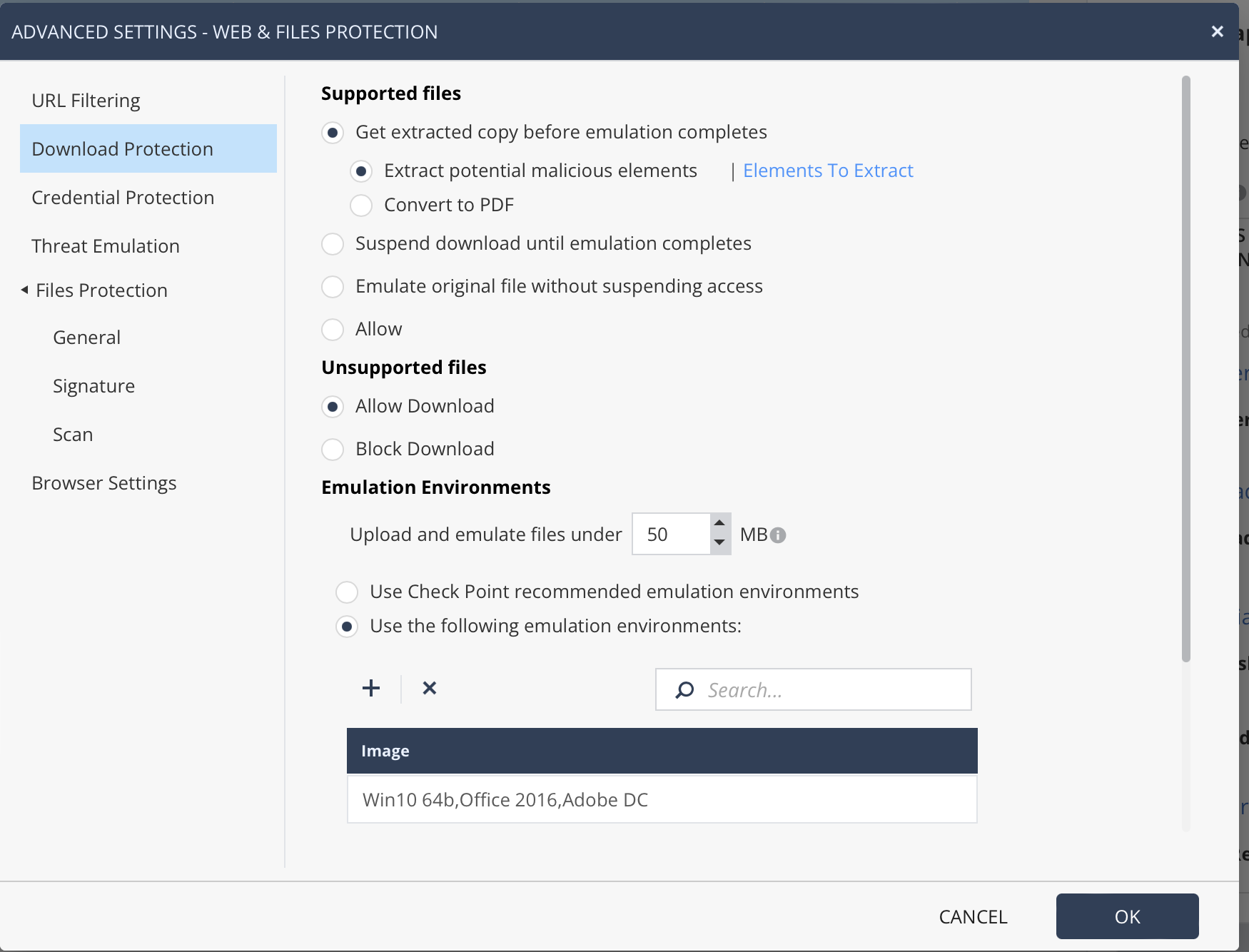
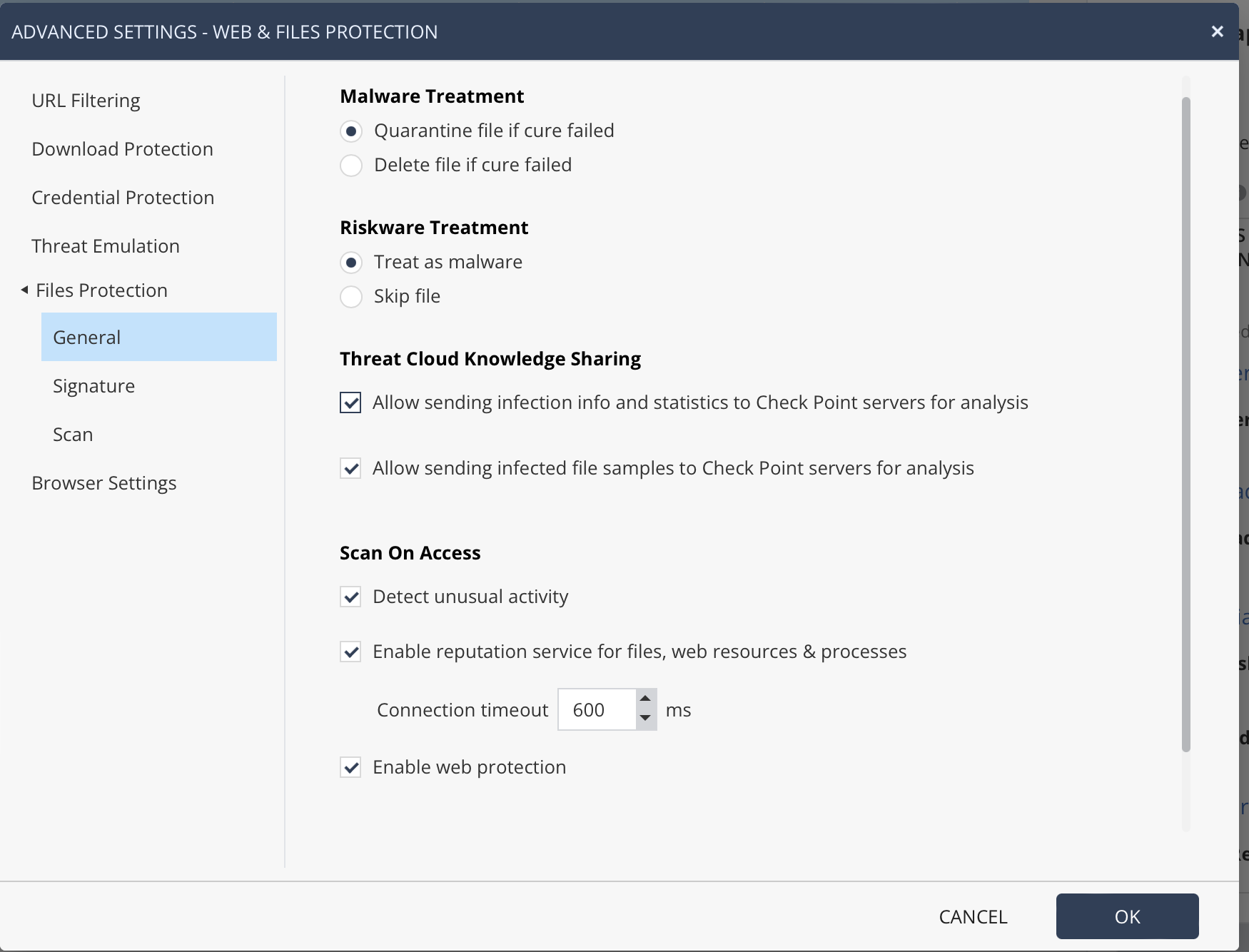
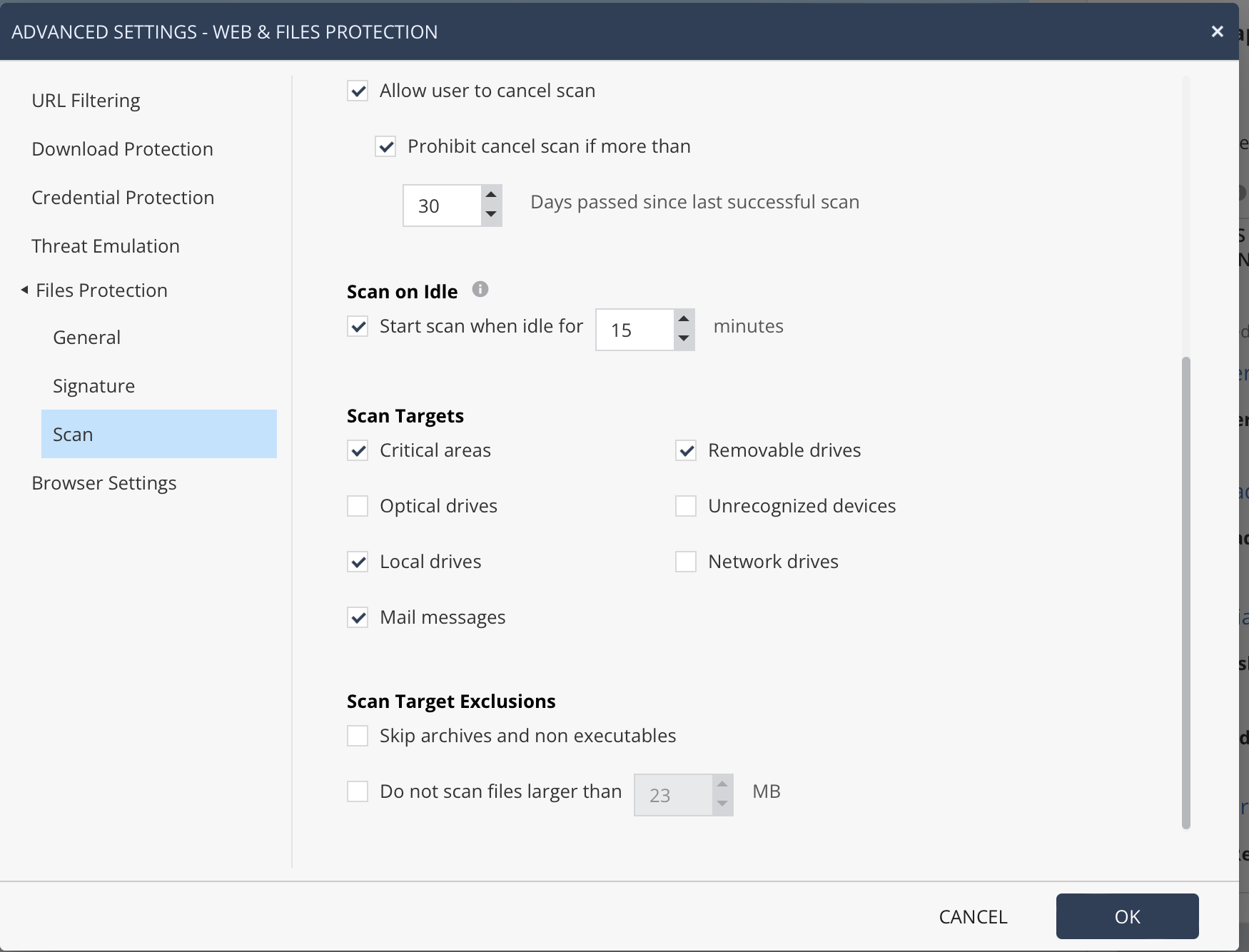
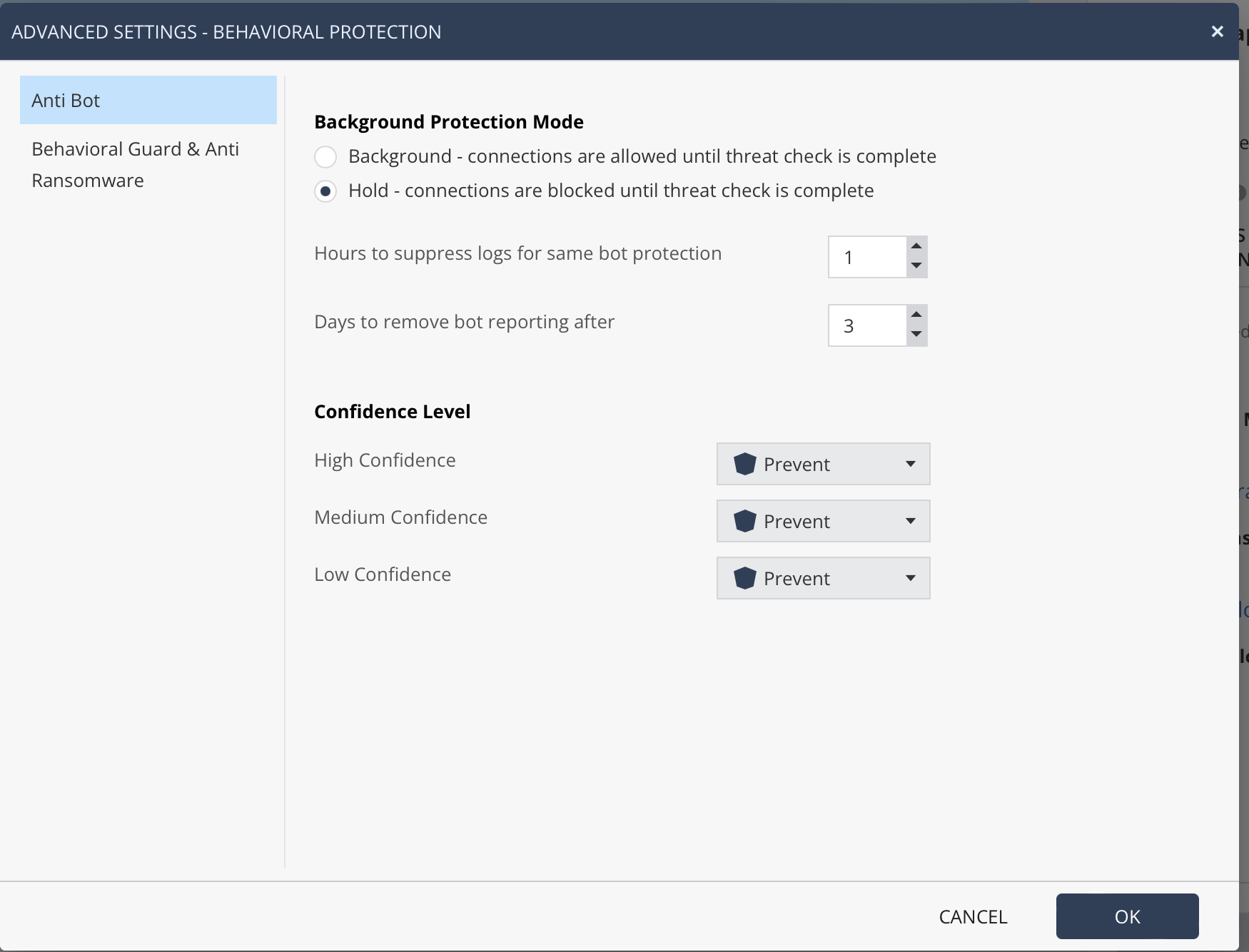
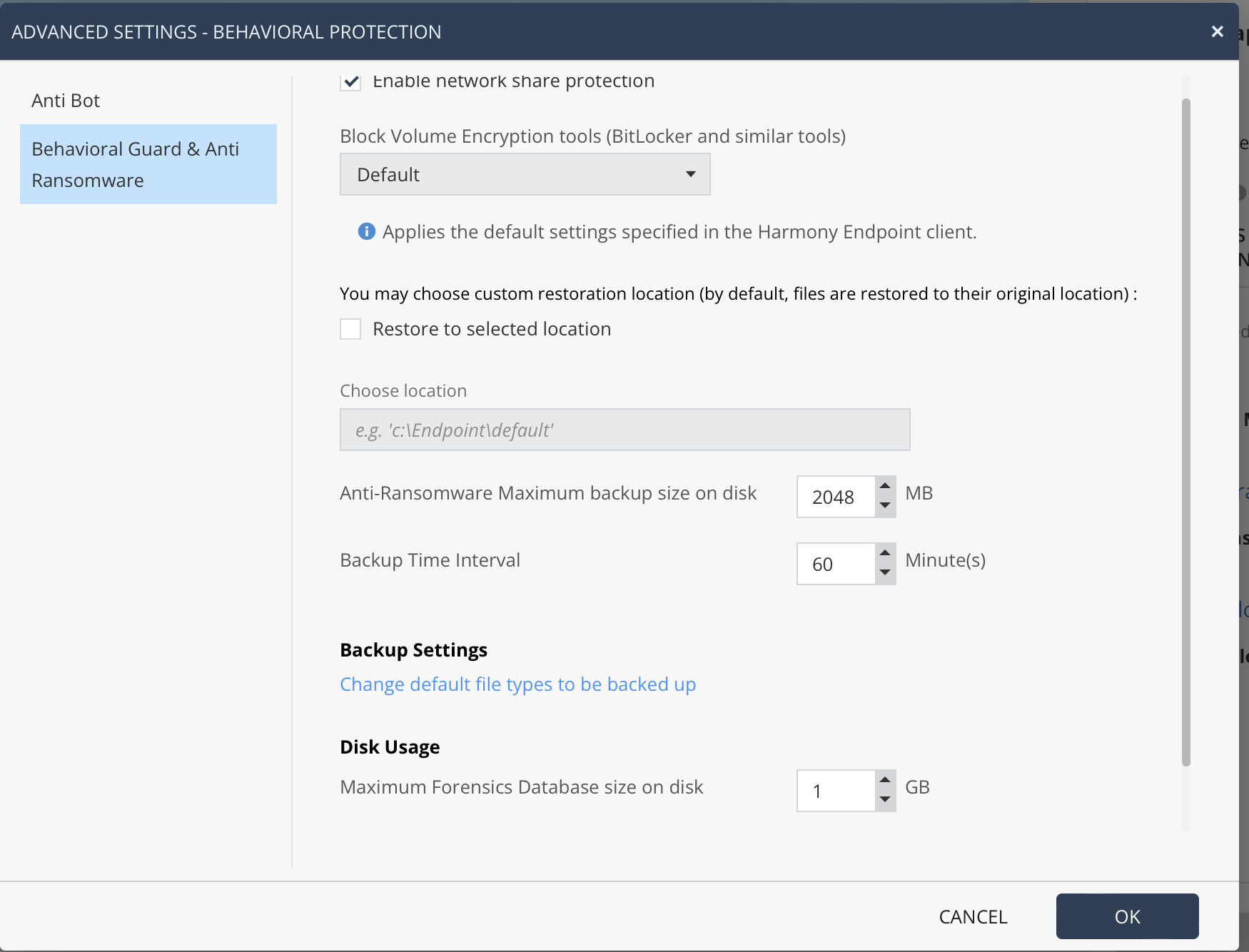
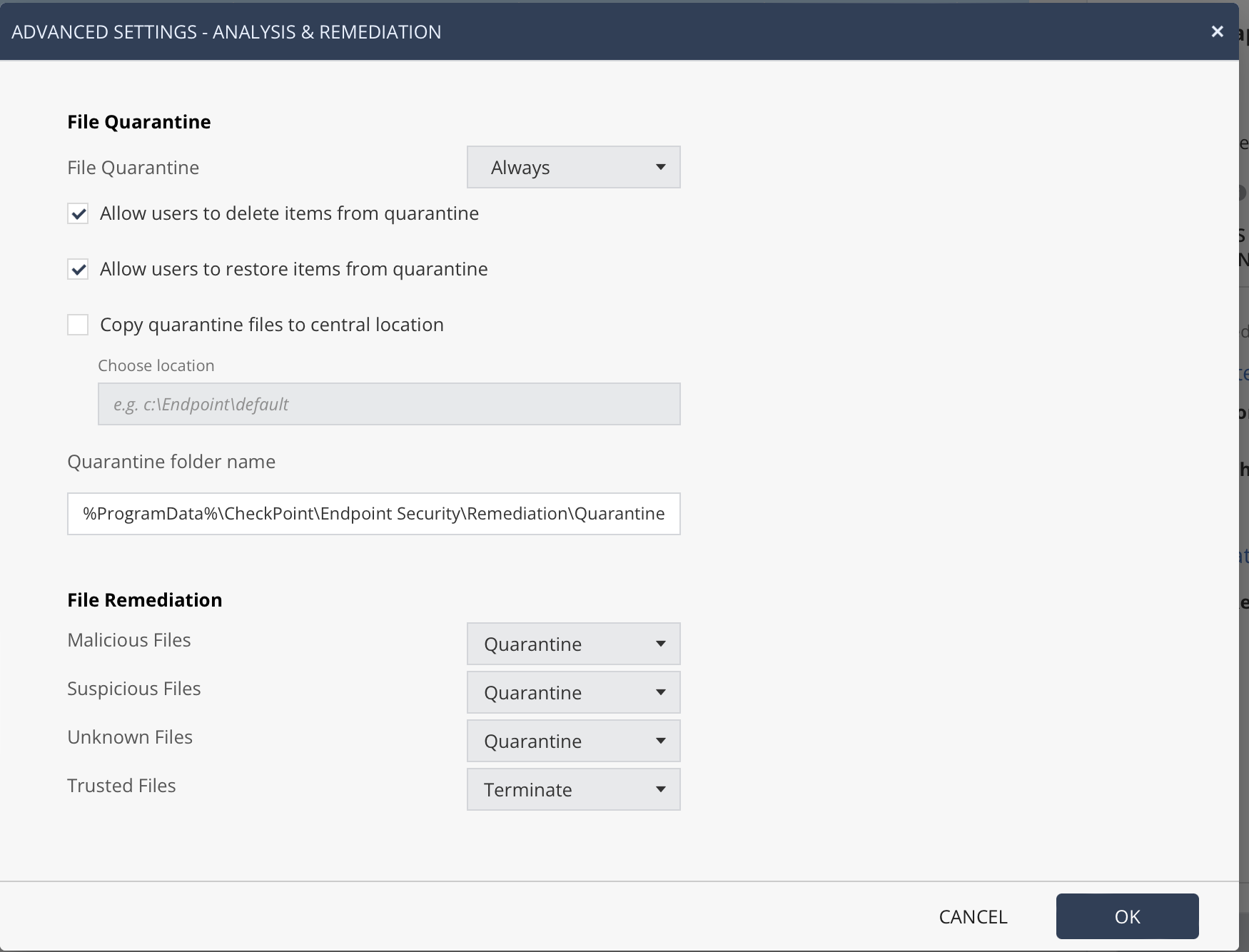 There is choice of engines as well - Kaspersky or Sophos. I choose Sophos because it's lighter and the updates are smarter with reduced disk activity. Users who need even more security can choose Kaspersky's full local engine. File reputation always uses Kaspersky feeds as well.
There is choice of engines as well - Kaspersky or Sophos. I choose Sophos because it's lighter and the updates are smarter with reduced disk activity. Users who need even more security can choose Kaspersky's full local engine. File reputation always uses Kaspersky feeds as well.
DHS-compliant is Sophos. Non-DHS-compliant is K.
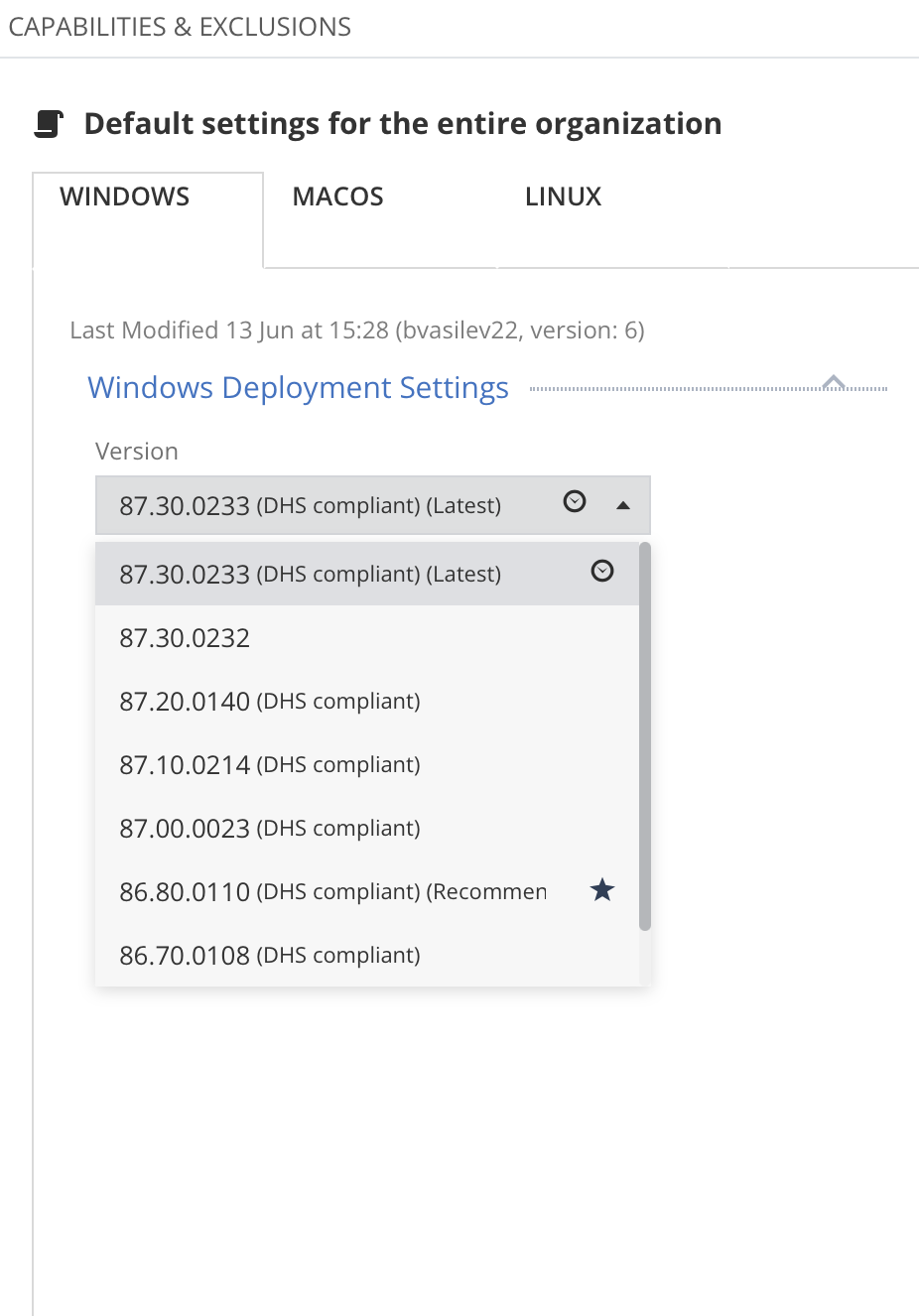
Before deploying the client, I recommend users who have had ZoneAlarm, to use software such as Revo to perform scan for any leftovers and delete them. @roger_m is very knowledgable of software uninstaller, he may suggest a better one. I type on Revo both Check Point and then ZoneAlarm (2 scans), perform advanced scan and delete everything.
Policy configuration for maximum security (once you finish making all changes, click on "Install Policy"):
DHS-compliant is Sophos. Non-DHS-compliant is K.
Before deploying the client, I recommend users who have had ZoneAlarm, to use software such as Revo to perform scan for any leftovers and delete them. @roger_m is very knowledgable of software uninstaller, he may suggest a better one. I type on Revo both Check Point and then ZoneAlarm (2 scans), perform advanced scan and delete everything.
There are 2 ways to deploy. Deployment settings can be configured here:
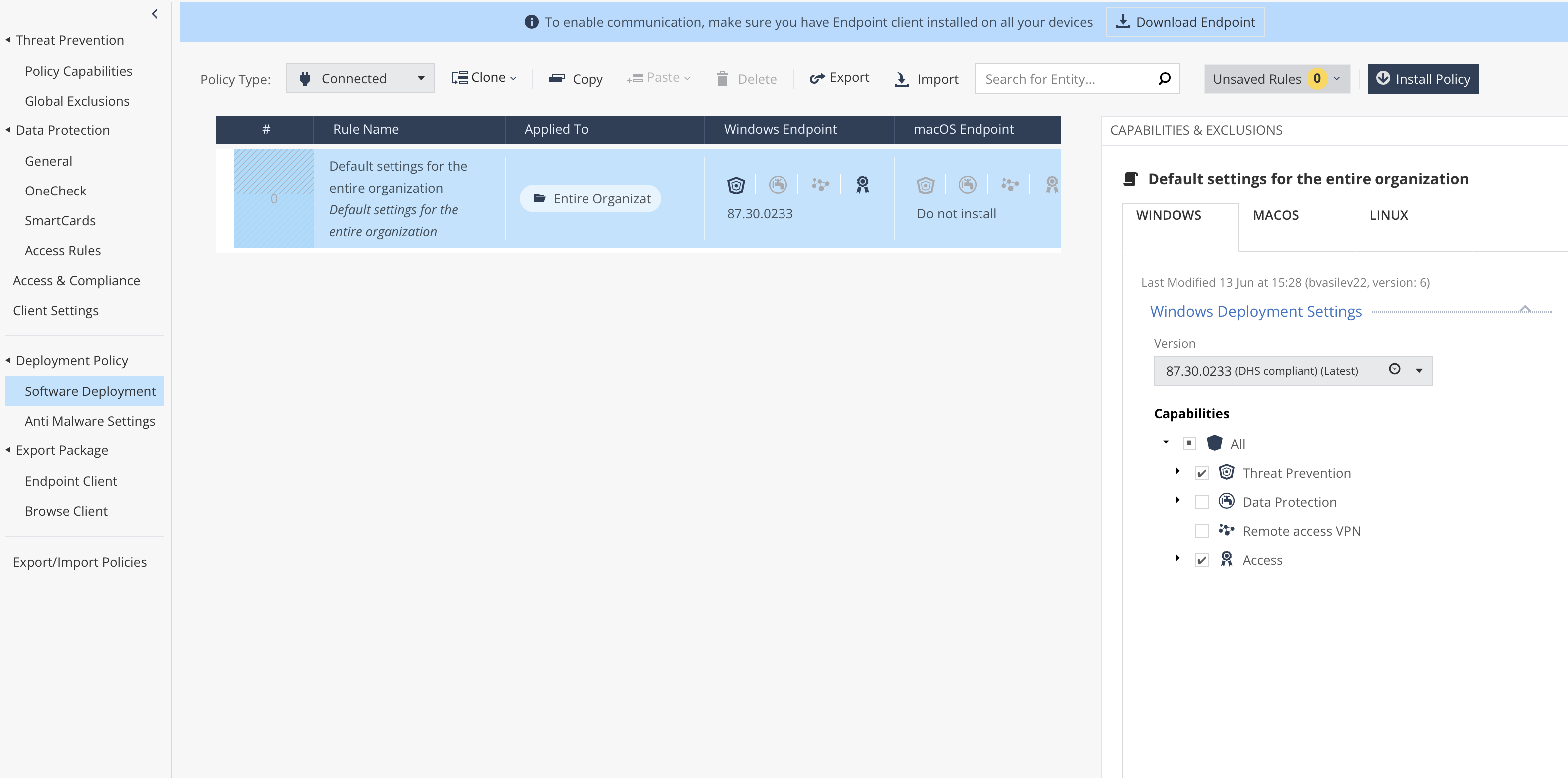
And then from the top bar that says "Download Endpoint" a very light client can be downloaded, which will deploy everything selected on the right hand side.
In addition, changing the deployment rules at any time causes all clients already installed to perform the changes.
E.g. You decide you no longer want Access control which includes firewall and compliance. You untick the component in question and install the policy. In a second, the client receives the changes and asks the user what time it is convenient to schedule the change for. At the specified time, the client removes Access Control.
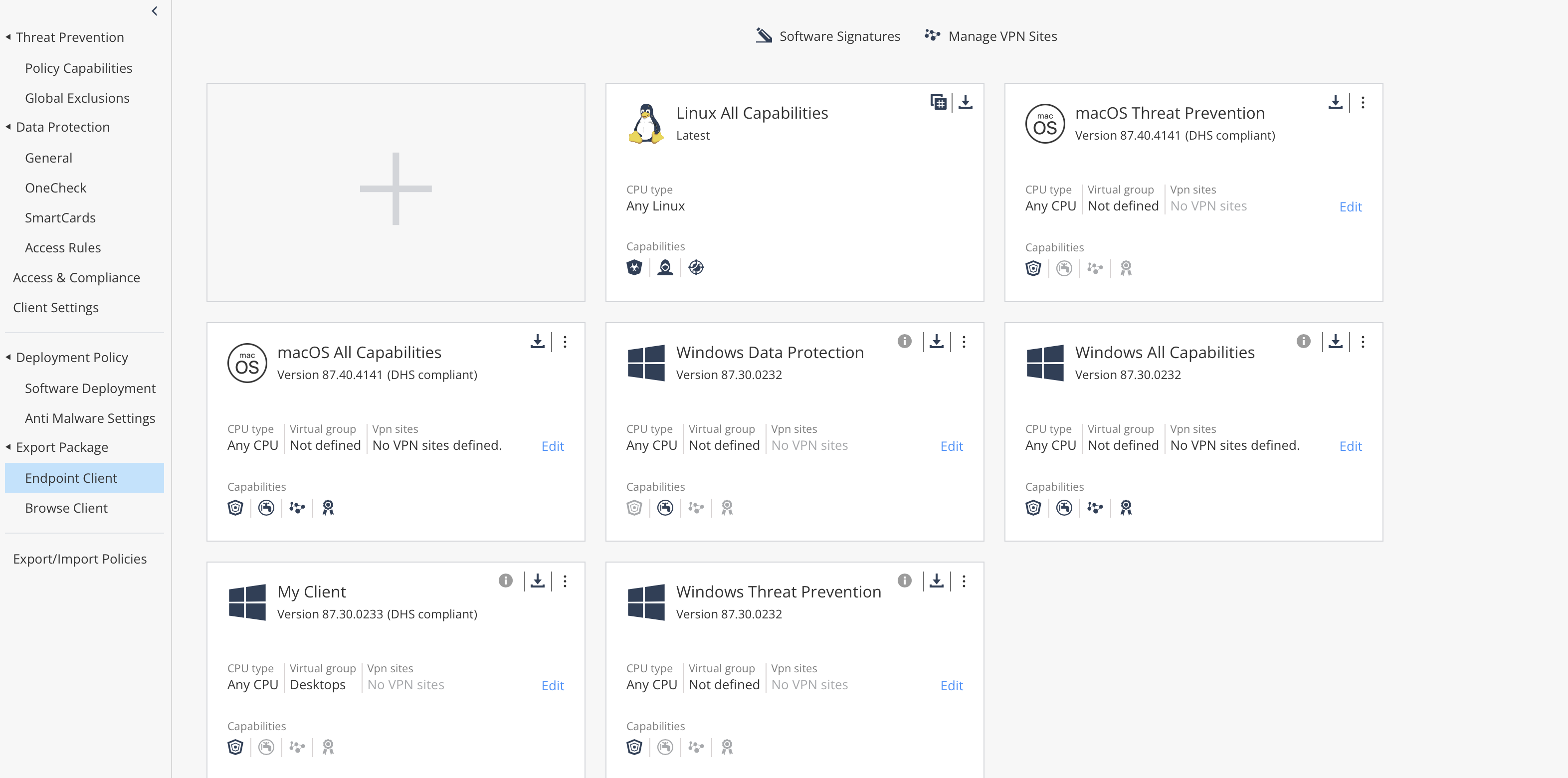
The second option is to go here (Export Package -> Endpoint Client) and press on the big Plus sign:
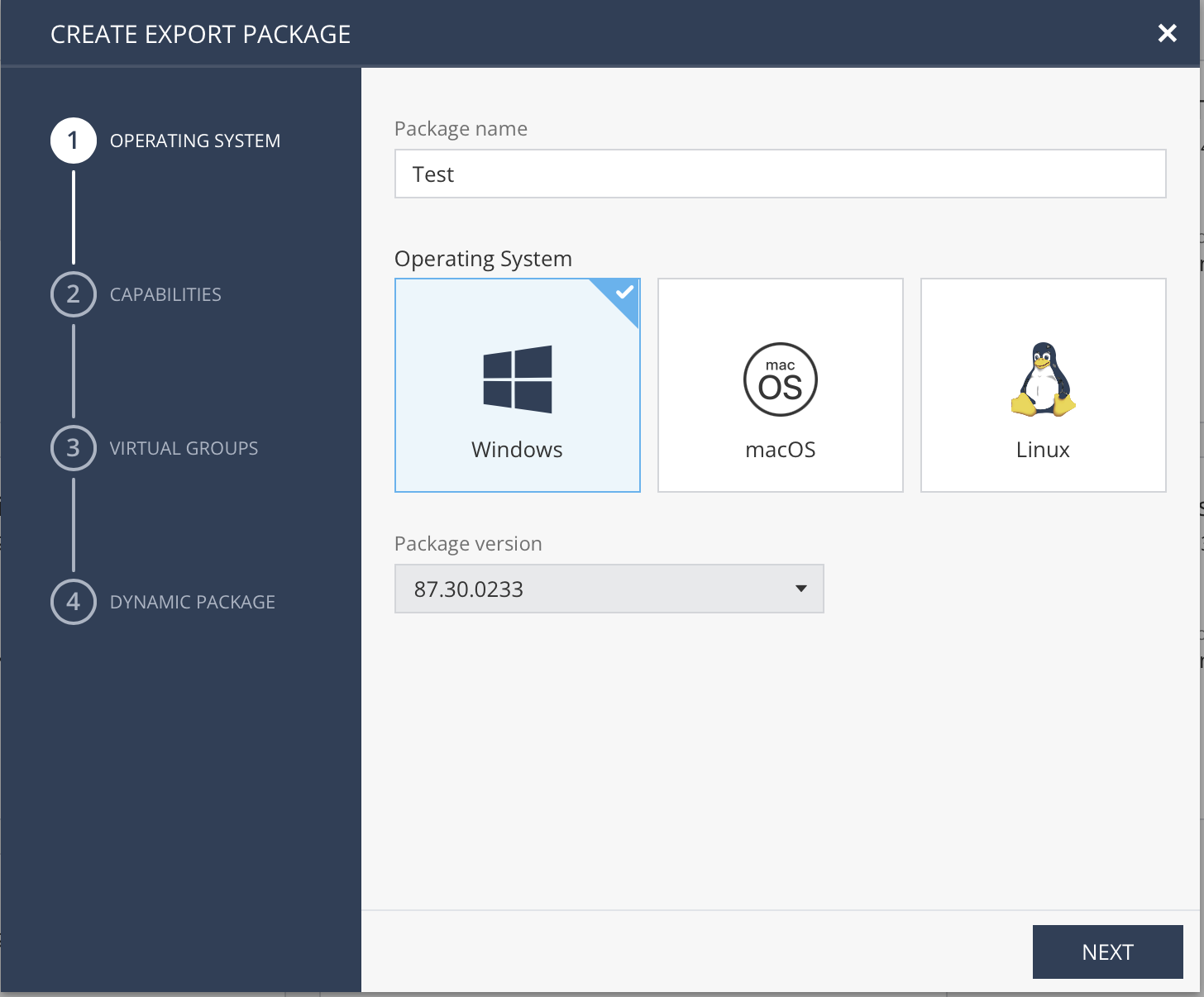
Select operating system, client version and enter package name so you will be able to identify it:
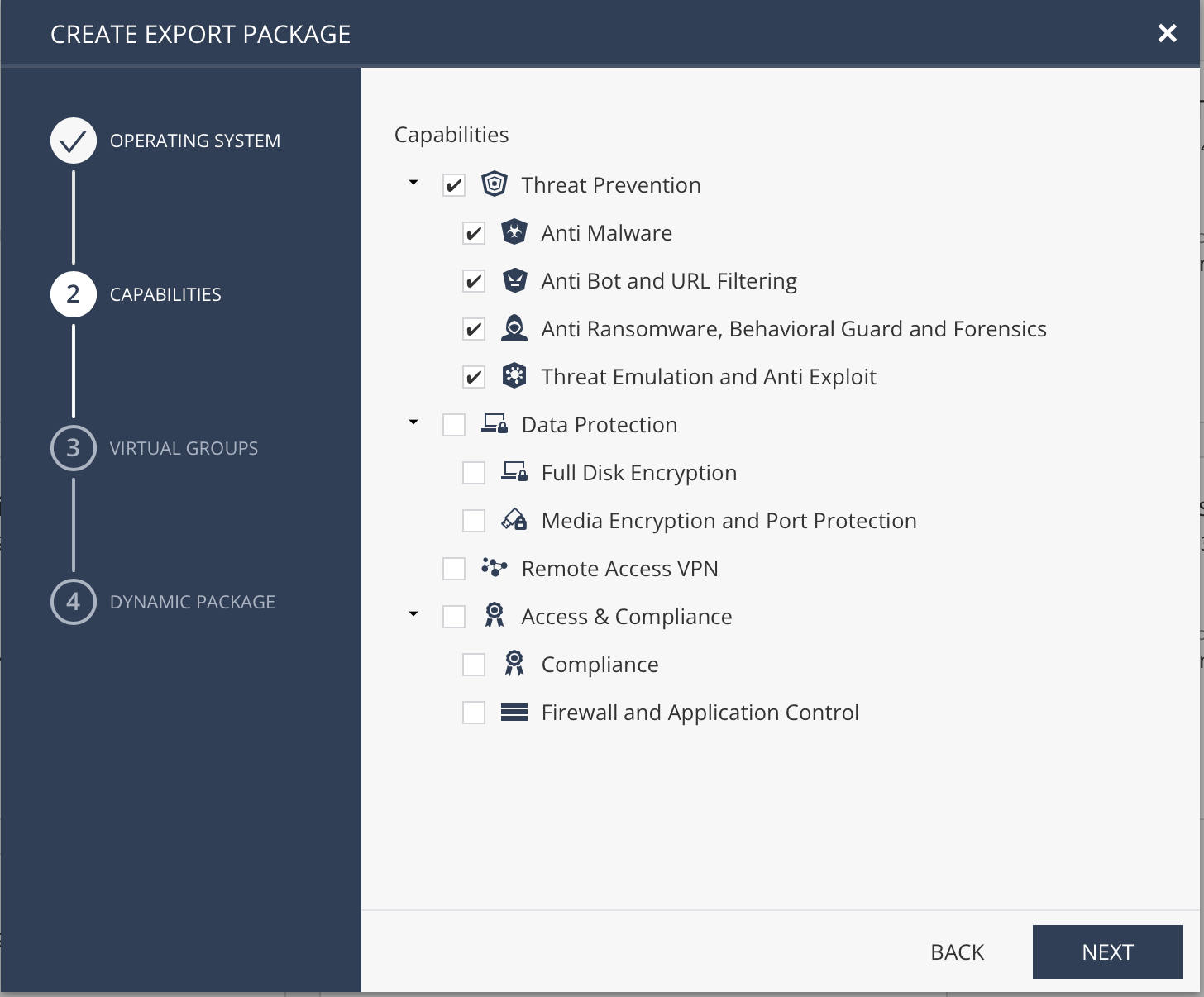
Next, select what you want this package to include:
Next, on virtual group, select what applies (desktop/laptop). This is for identification purposes.
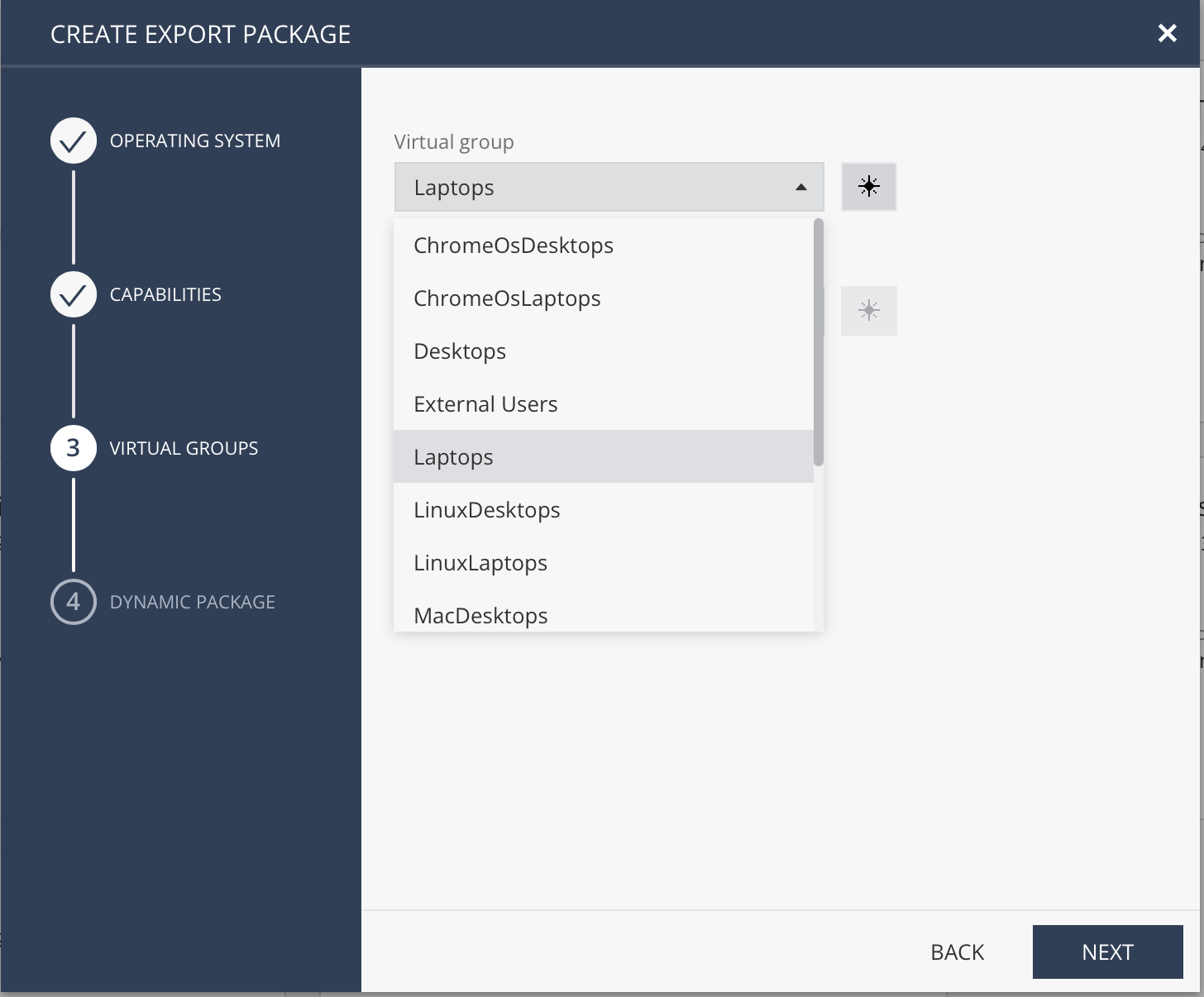
Next, I recommend leaving all settings as they are for slower download (package will be quite big) but the deployment process will be quicker.
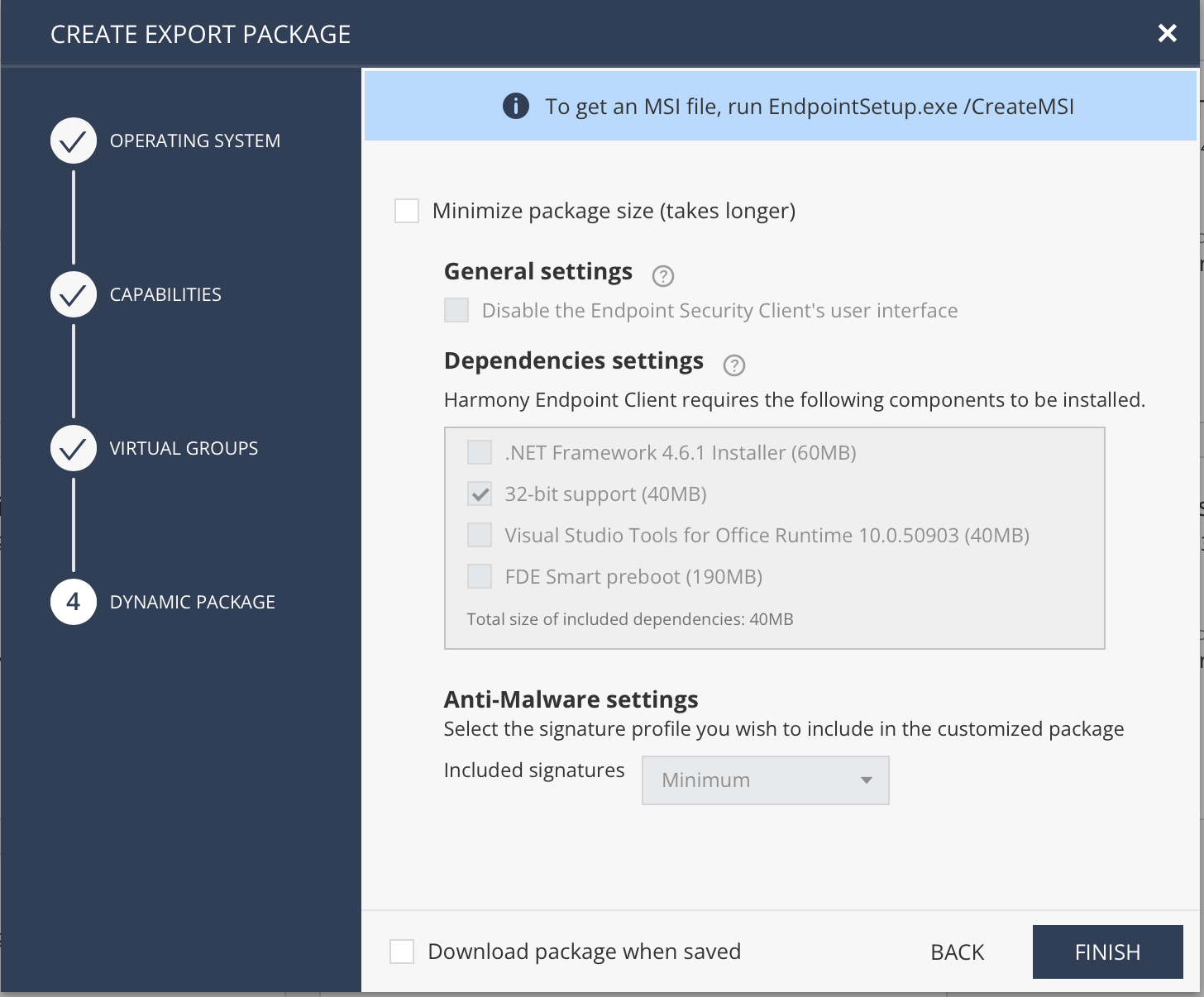
This window will automatically close when you press "Finish" and you will be returned to the clients list. Your client will shortly appear there. Click "Download" to start downloading.
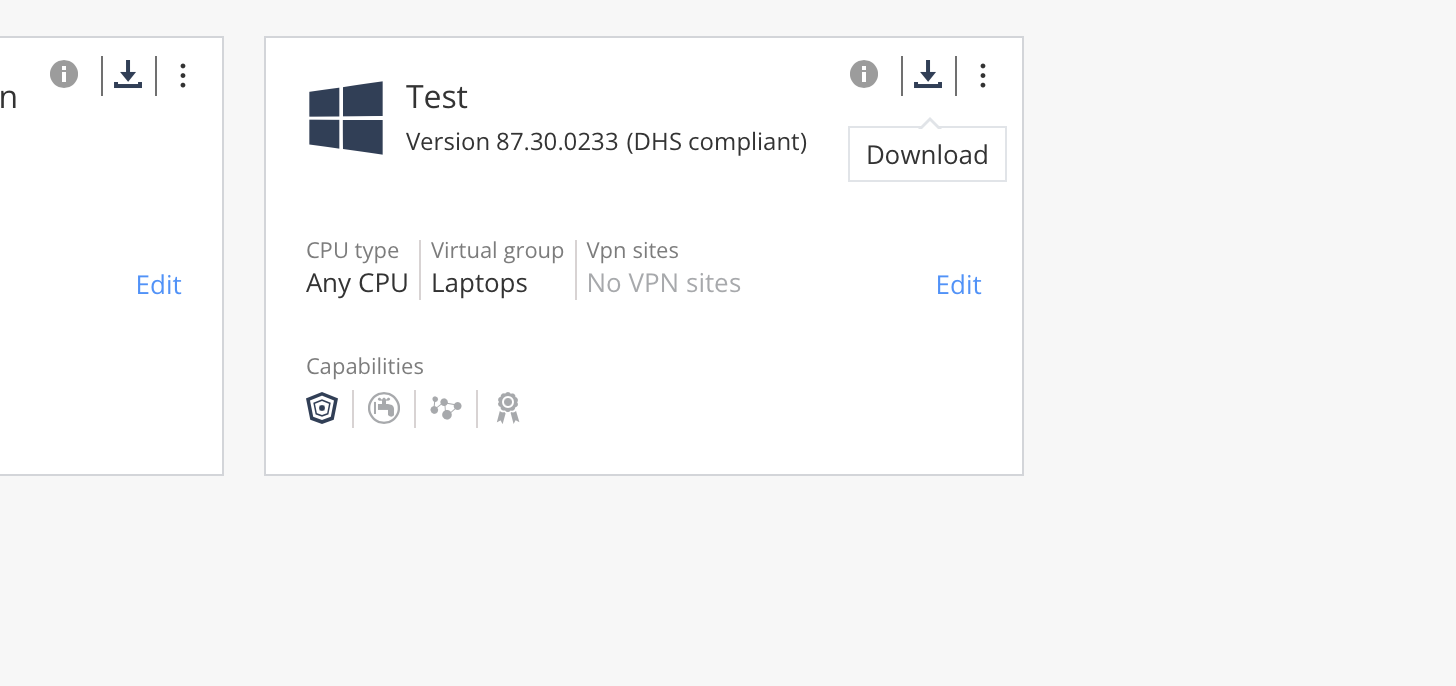
And then from the top bar that says "Download Endpoint" a very light client can be downloaded, which will deploy everything selected on the right hand side.
In addition, changing the deployment rules at any time causes all clients already installed to perform the changes.
E.g. You decide you no longer want Access control which includes firewall and compliance. You untick the component in question and install the policy. In a second, the client receives the changes and asks the user what time it is convenient to schedule the change for. At the specified time, the client removes Access Control.
The second option is to go here (Export Package -> Endpoint Client) and press on the big Plus sign:
Select operating system, client version and enter package name so you will be able to identify it:
Next, select what you want this package to include:
Next, on virtual group, select what applies (desktop/laptop). This is for identification purposes.
Next, I recommend leaving all settings as they are for slower download (package will be quite big) but the deployment process will be quicker.
This window will automatically close when you press "Finish" and you will be returned to the clients list. Your client will shortly appear there. Click "Download" to start downloading.
Last edited:
ZoneAlarm on Shadowra test is not important, Harmony Endpoint is a different product.so tempted to push that Harmony button... but think I'll wait a few more days, perhaps see how ZA/ESNG does in @Shadrowra's test.
@Trident, is it possible to have different setups for different computer? Like one for mine and another for my daughter?
It is possible to create as many policies as you want and move different devices to different policies. In the next few days we’ll explore reports, logs, changing policies and others.@Trident, is it possible to have different setups for different computer? Like one for mine and another for my daughter?
Last edited:
I almost don't want people to know about this hidden gem. LolIt is possible to create as many policies as you want and move different devices to different policies. In the next few days we’ll explore reports, logs, changing policies and others.
The question is why Checkpoint is using Kaspersky instead of its own in-house native AV engine.
They switched to it for their next-gen AV product.
Can the Harmony Endpoint be used with Windows Defender or do you have to install the AV package?
They switched to it for their next-gen AV product.
Can the Harmony Endpoint be used with Windows Defender or do you have to install the AV package?
Check Point uses both their engine and a third-party engine. Their engine is based on static analysis (next-gen AV) and they have full-blown emulations as well. Between the two, a gap (dynamic analysis) remains, which is filled by Kaspersky/Sophos. It’s actually a very smart design. It’s the same with ZoneAlarm but there you don’t have choice of engines, anti-malware is always Sophos.The question is why Checkpoint is using Kaspersky instead of its own in-house native AV engine.
They switched to it for their next-gen AV product.
Can the Harmony Endpoint be used with Windows Defender or do you have to install the AV package?
Harmony can be used with Defender but I am unsure why anyone would want to do that. You just need not to install anti-malware.
Check Point uses both their engine and a third-party engine. Their engine is based on static analysis (next-gen AV) and they have full-blown emulations as well. Between the two, a gap (dynamic analysis) remains, which is filled by Kaspersky/Sophos. It’s actually a very smart design. It’s the same with ZoneAlarm but there you don’t have choice of engines, anti-malware is always Sophos.
Harmony can be used with Defender but I am unsure why anyone would want to do that. You just need not to install anti-malware.
Harmony Endpoint Security installation is blocked because Smart App isn't supported. Since that's a Windows application control feature, the reason it must be disabled is because it conflicts with the Harmony Endpoint Security application control feature. You can't have both running at the same time. But Smart App in Windows 11 is in evaluation mode and isn't enabled.
So there's a possibility that this endpoint software can be infected with ransomeware because it has files rollback feature despite all other fantastic features just like other endpoints.
How about those files not monitored and not protected? How to rollback after a ransomware attack? Such files can be in the tens of thousands throughout the system since a ransomware is crafted to infect as many file extension types as possible
Just for comparison. Deep Instinct don't talk about remediation so I assume there's none. Trellix has a system remediation feature.
How about those files not monitored and not protected? How to rollback after a ransomware attack? Such files can be in the tens of thousands throughout the system since a ransomware is crafted to infect as many file extension types as possible
Just for comparison. Deep Instinct don't talk about remediation so I assume there's none. Trellix has a system remediation feature.
Last edited:
Ransomware Remediation is just one layer. Having it or not having it doesn’t mean anything. Trelix with Dynamic Application Containment and various policies has powerful prevention, but they still use anti-ransomware. Deep Instinct just hasn’t developed it.So there's a possibility that this endpoint software can be infected with ransomeware because it has files rollback feature despite all other fantastic features just like other endpoints.
How about those files not monitored and not protected? How to rollback after a ransomware attack? Such files can be in the tens of thousands throughout the system since a ransomware is crafted to infect as many file extension types as possible
Just for compariaon. Deep Instinct don't talk about remediation so I assume there's none. Trellix has a system remediation feature.
My point is that if after a ransomware attack how to deal with unmonitored and unprotected files which are encrypted?Ransomware Remediation is just one layer. Having it or not having it doesn’t mean anything. Trelix with Dynamic Application Containment and various policies has powerful prevention, but they still use anti-ransomware. Deep Instinct just hasn’t developed it.
What do you mean by 'Having it (remediation) or not having it doesn’t mean anything'
If an endpoint can confidently says no ransomware can bypass it then I agree that there's no need of remediation since it has so many other fantastic features to detect/block/remove ransomware. But can they?
On an Endpoint you can’t assume, produce statements and verdicts or take chances. You need to cover every vector, every corner in every way possible. To boost ransomware detection and protection, since the version 87.00 Check Point also supports Intel TDT (11th and 12th core Intel CPUs) to enhance ransomware behaviour detection. Something Deep Instinct still doesn’t do.My point is that if after a ransomware attack how to deal with unmonitored amd unprotected files which are encrypted?
If an endpoint can confidently says no ransomware can bypass it then there's no need of remediation since it has so many other fantastic features to detect/block/remove ransomware. But can they?
You will deal with unmonitored files by having the appropriate backup and disaster recovery policies in place.
Yes, you don't take chances against ransomware attack.On an Endpoint you can’t assume, produce statements and verdicts or take chances. You need to cover every vector, every corner in every way possible. To boost ransomware detection and protection, since the version 87.00 Check Point also supports Intel TDT (11th and 12th core Intel CPUs) to enhance ransomware behaviour detection. Something Deep Instinct still doesn’t do.
You will deal with unmonitored files by having the appropriate backup and disaster recovery policies in place.
As I mentioned endpoints do come with fantastic features to detect/block/remove ransomware, Bascially they have the same or similar features like deep AI/ML/BB/signature/sandbox and what not.
On your last statement. So you agree files rollback is not useful since there are other encrypted files which cannot be rollbacked because they are unmonitored and unprotected, right?
Last edited:
They do, yes. Not all of them are equal though. If anyone finds this feature not useful, they can disable it.As I mentioned endpoints do come with fantastic features to detect/block/remove ransomware, Bascially they have the same or similar features like deep AI/ML/BB/signature and what not.
You may also like...
-
New Update Announcing End of Life for Kaspersky Engine in Harmony Endpoint
- Started by Trident
- Replies: 14
-
Security News Kimwolf Botnet Lurking in Corporate, Govt. Networks
- Started by Miravi
- Replies: 1
-
App Review Huawei HiSec Endpoint Protection 2025
- Started by Shadowra
- Replies: 33
-
Serious Discussion [Extension]Checkpoint harmony web protection
- Started by Vitali Ortzi
- Replies: 29
-
App Review CheckPoint Harmony Endpoint Security 2024
- Started by Shadowra
- Replies: 40

